Embed presentation
Download as PDF, PPTX





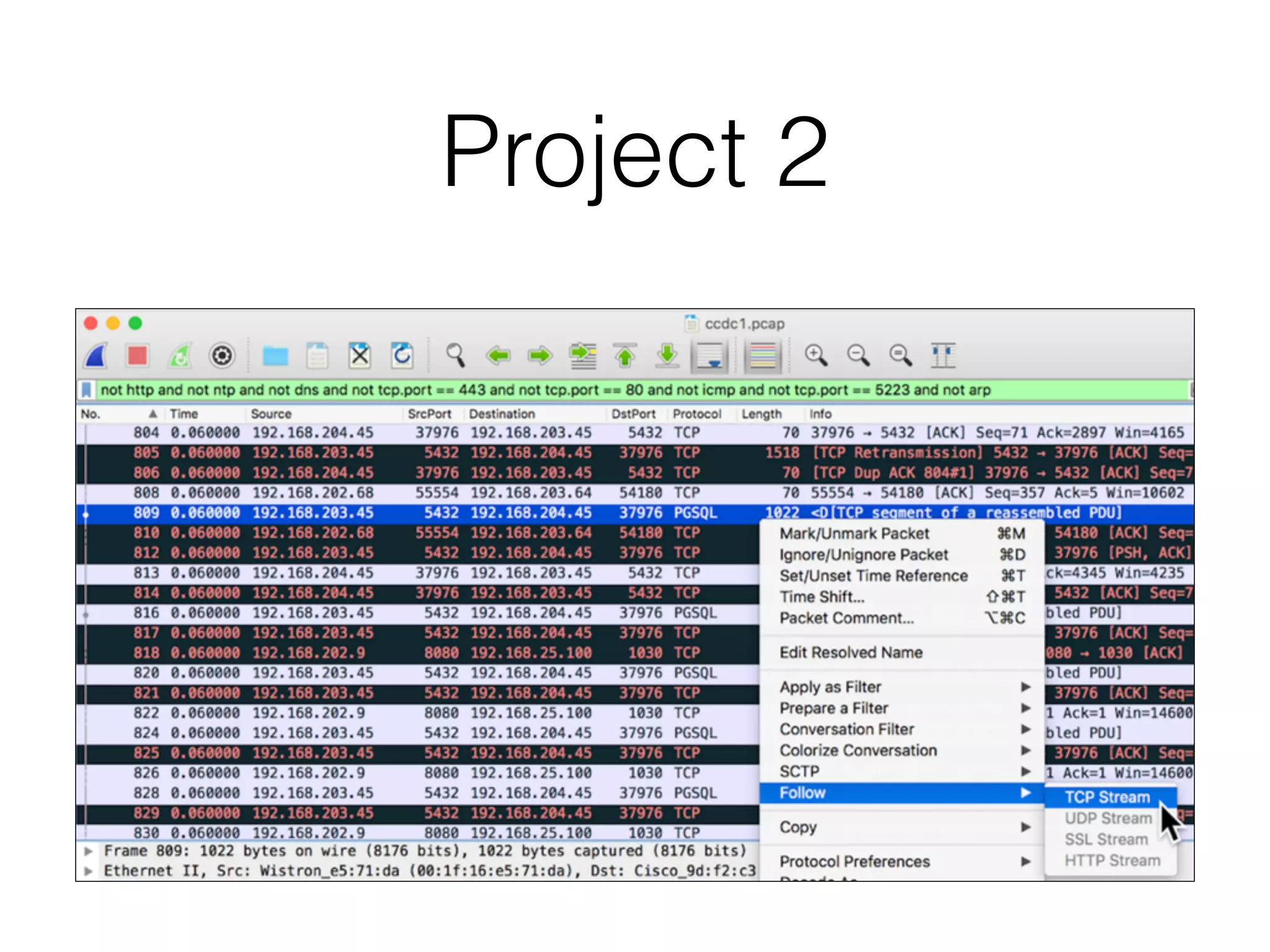


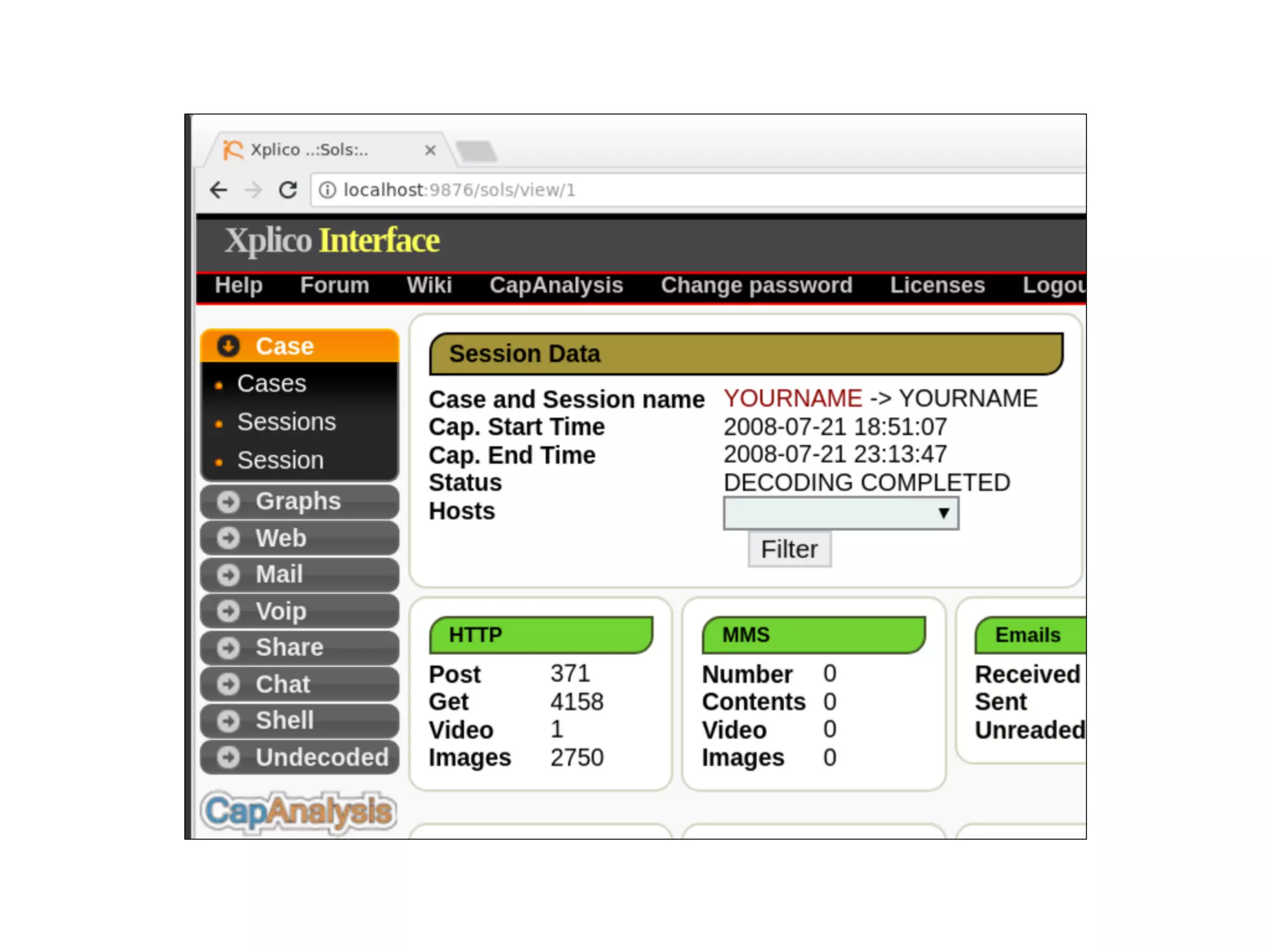
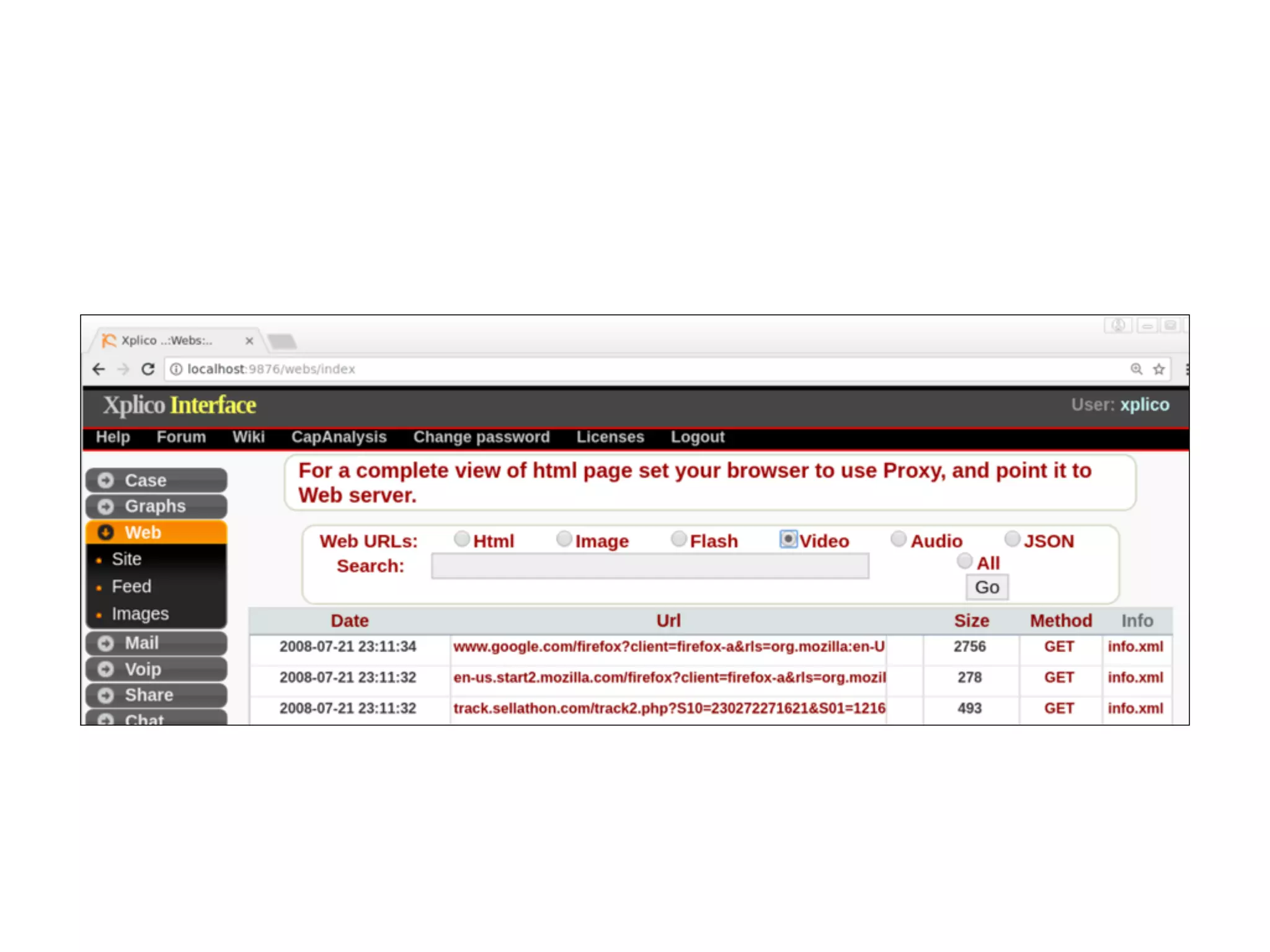
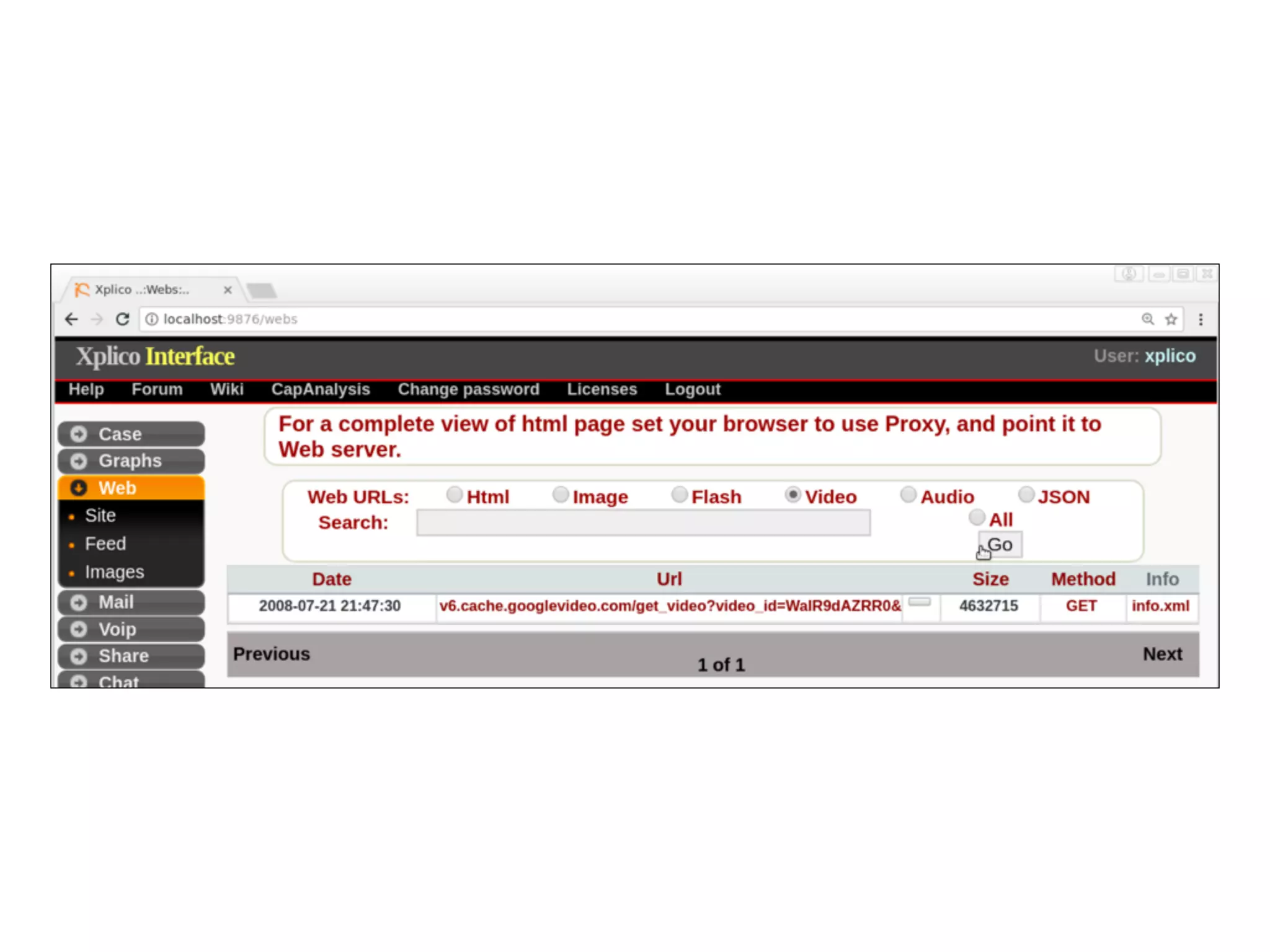

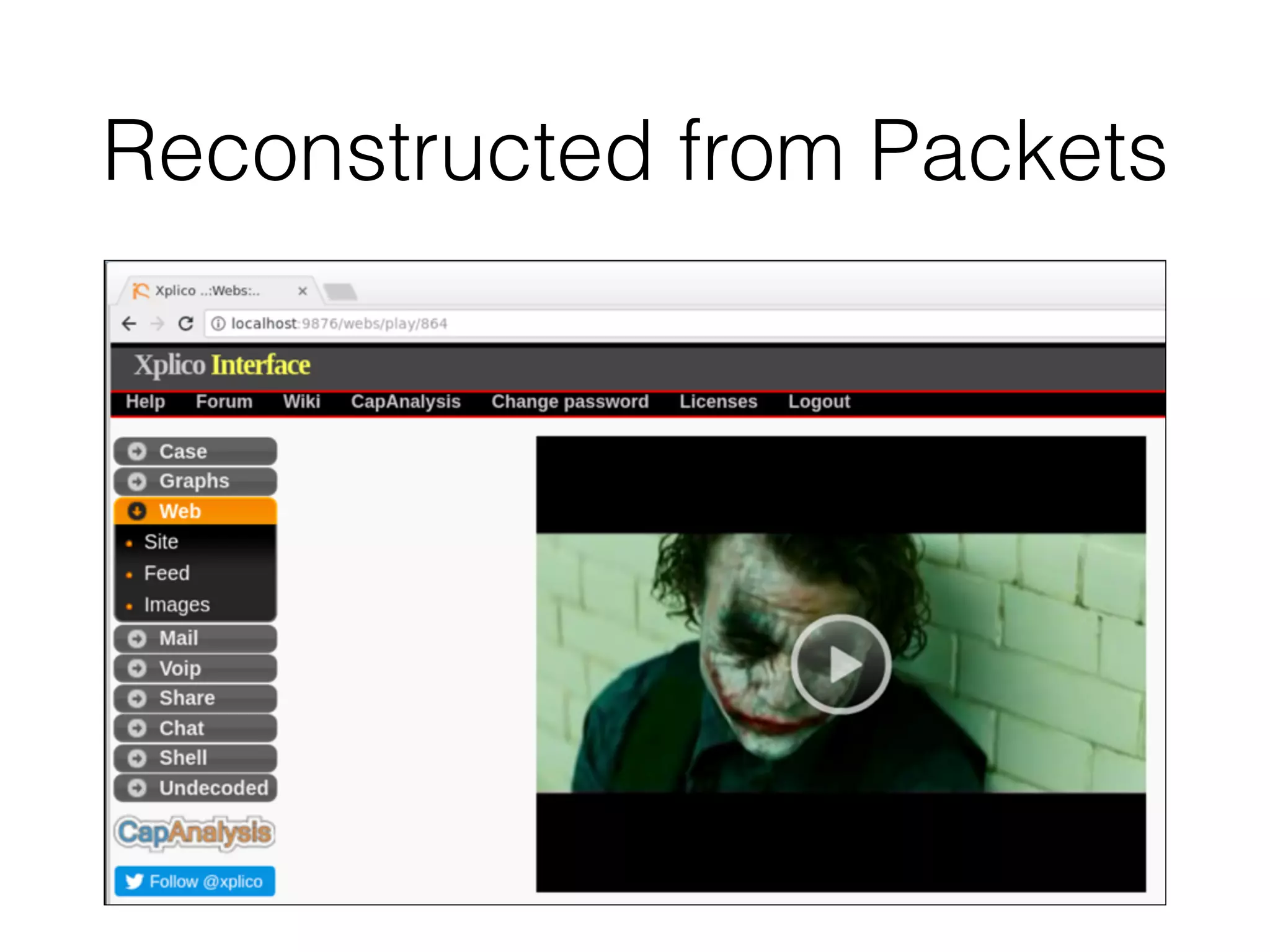



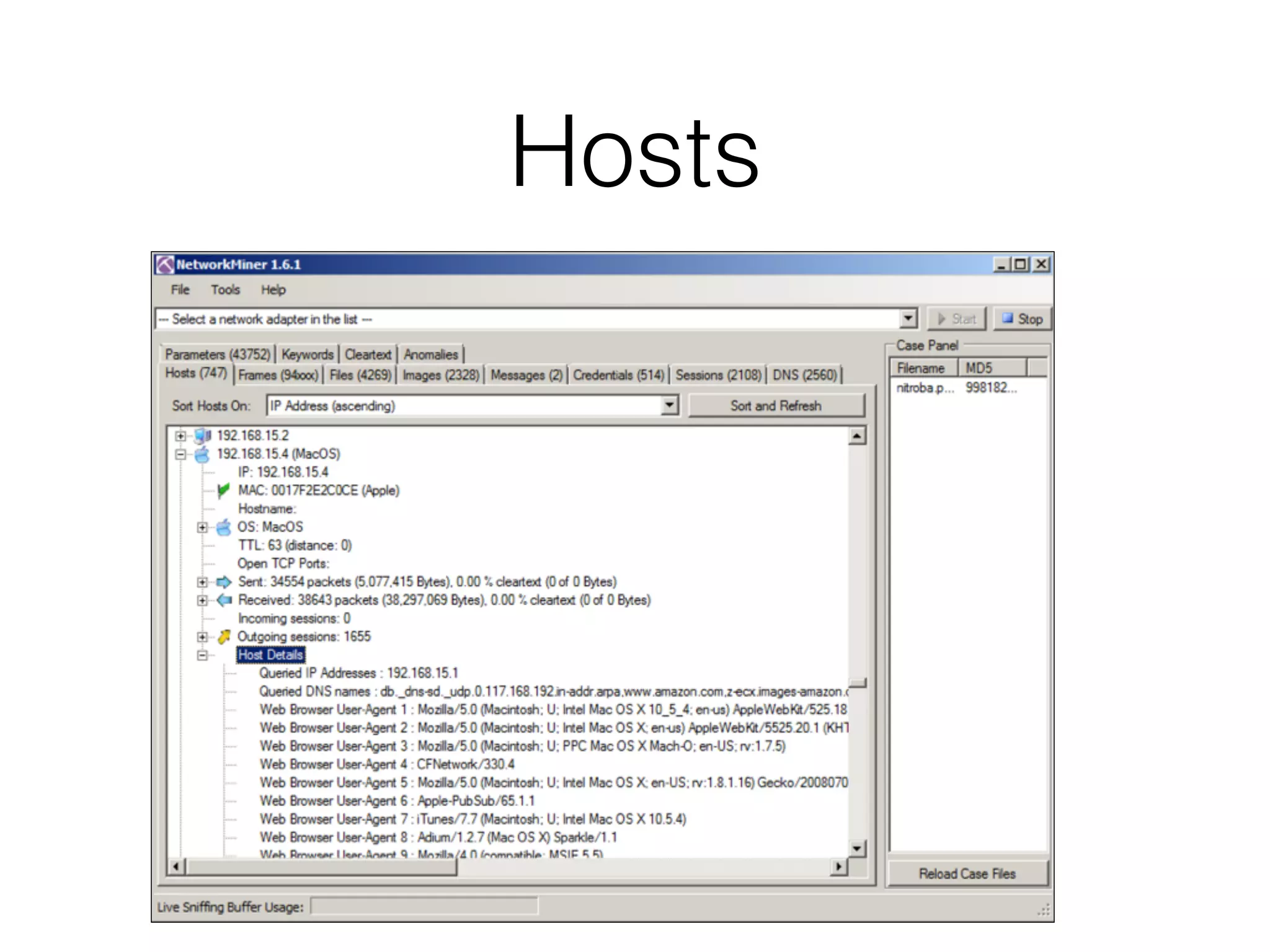
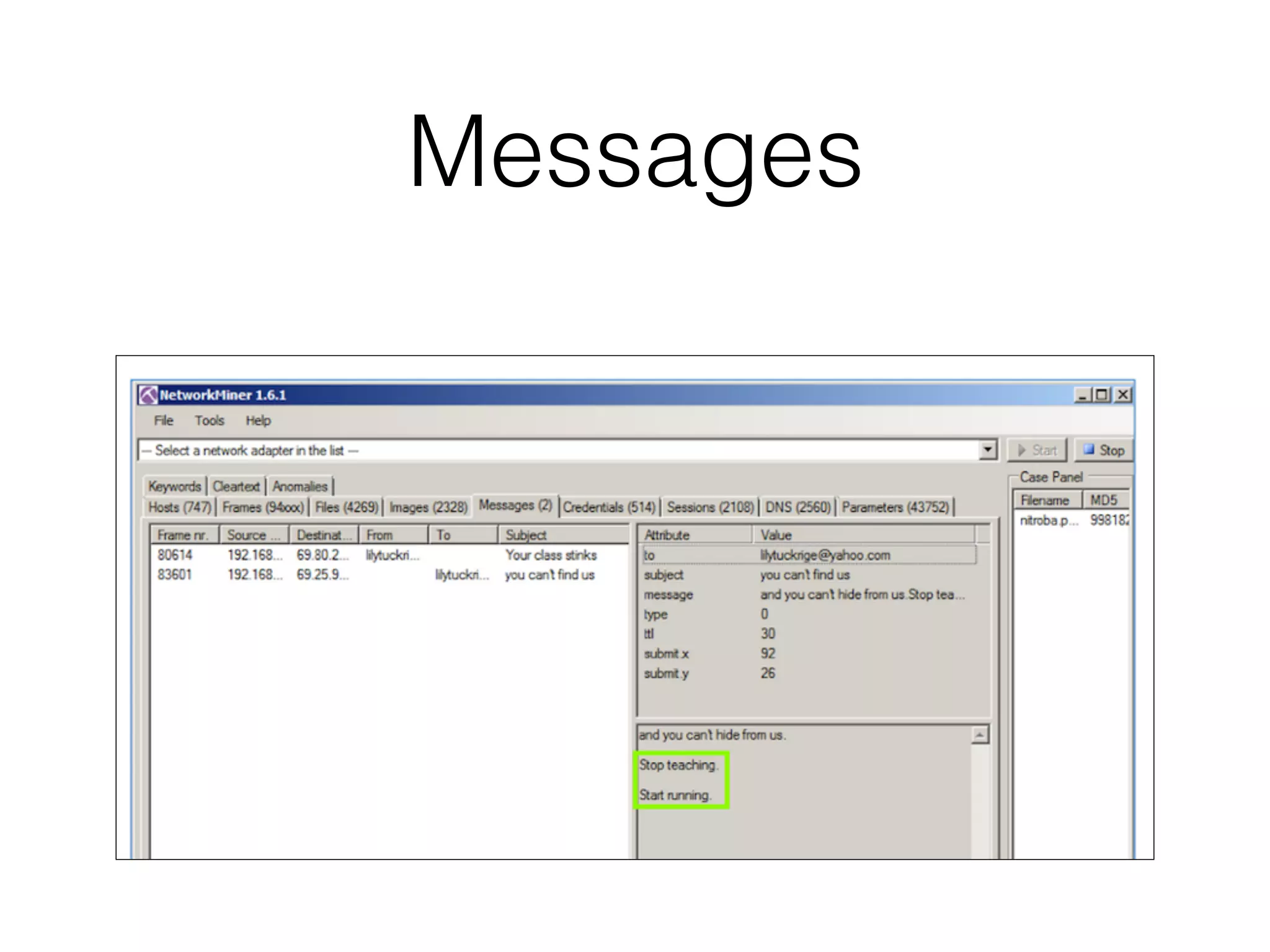




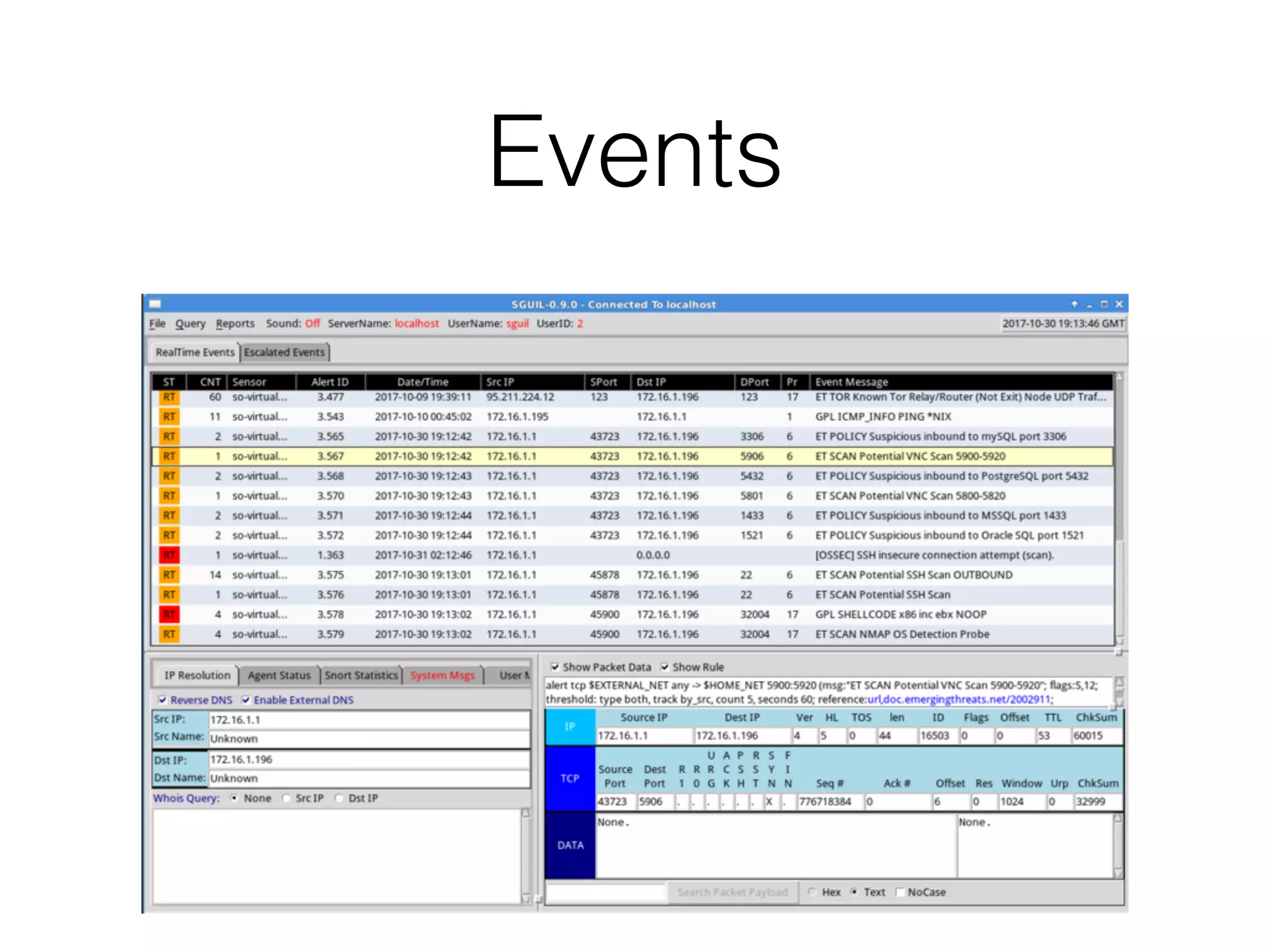
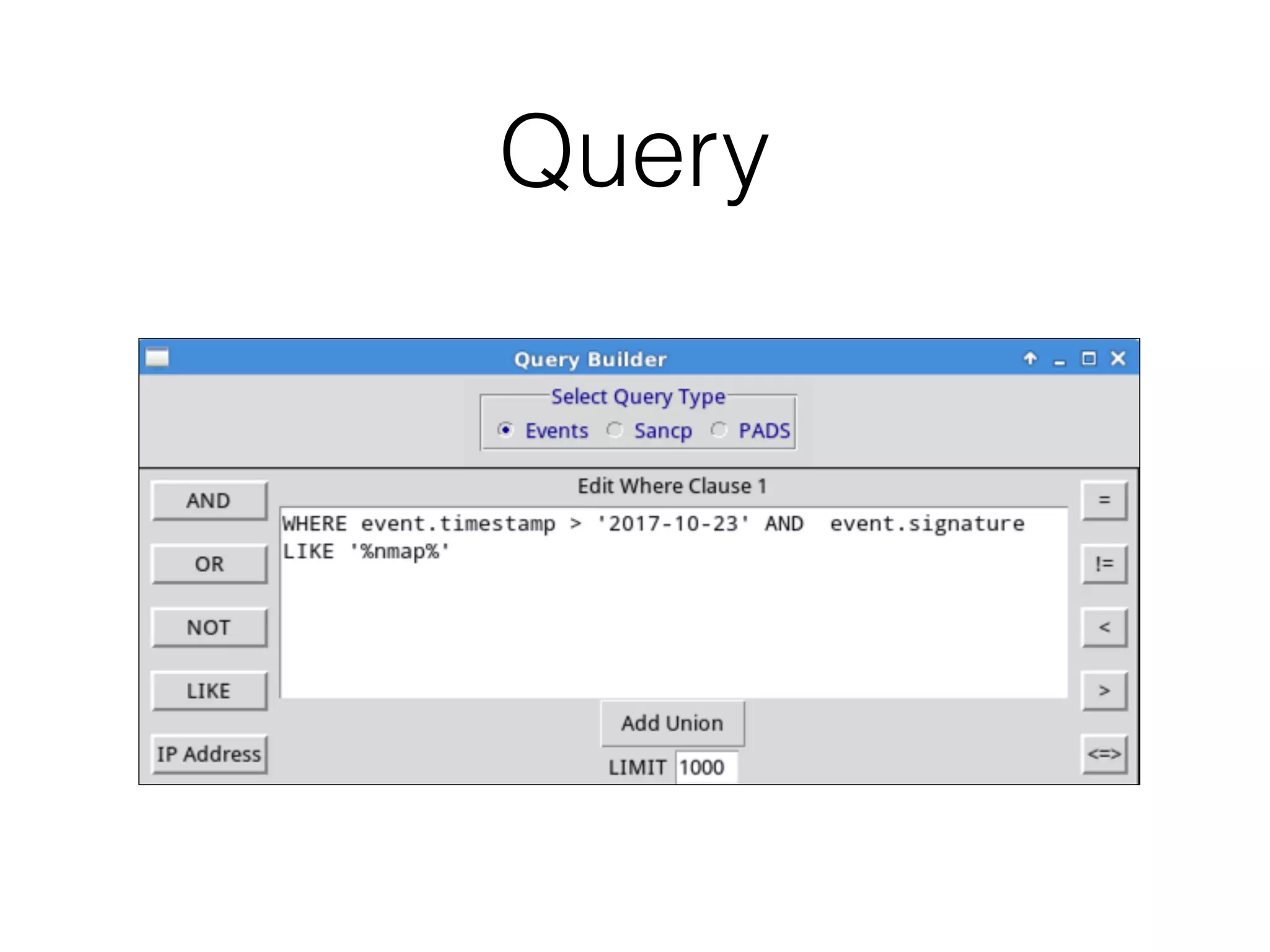
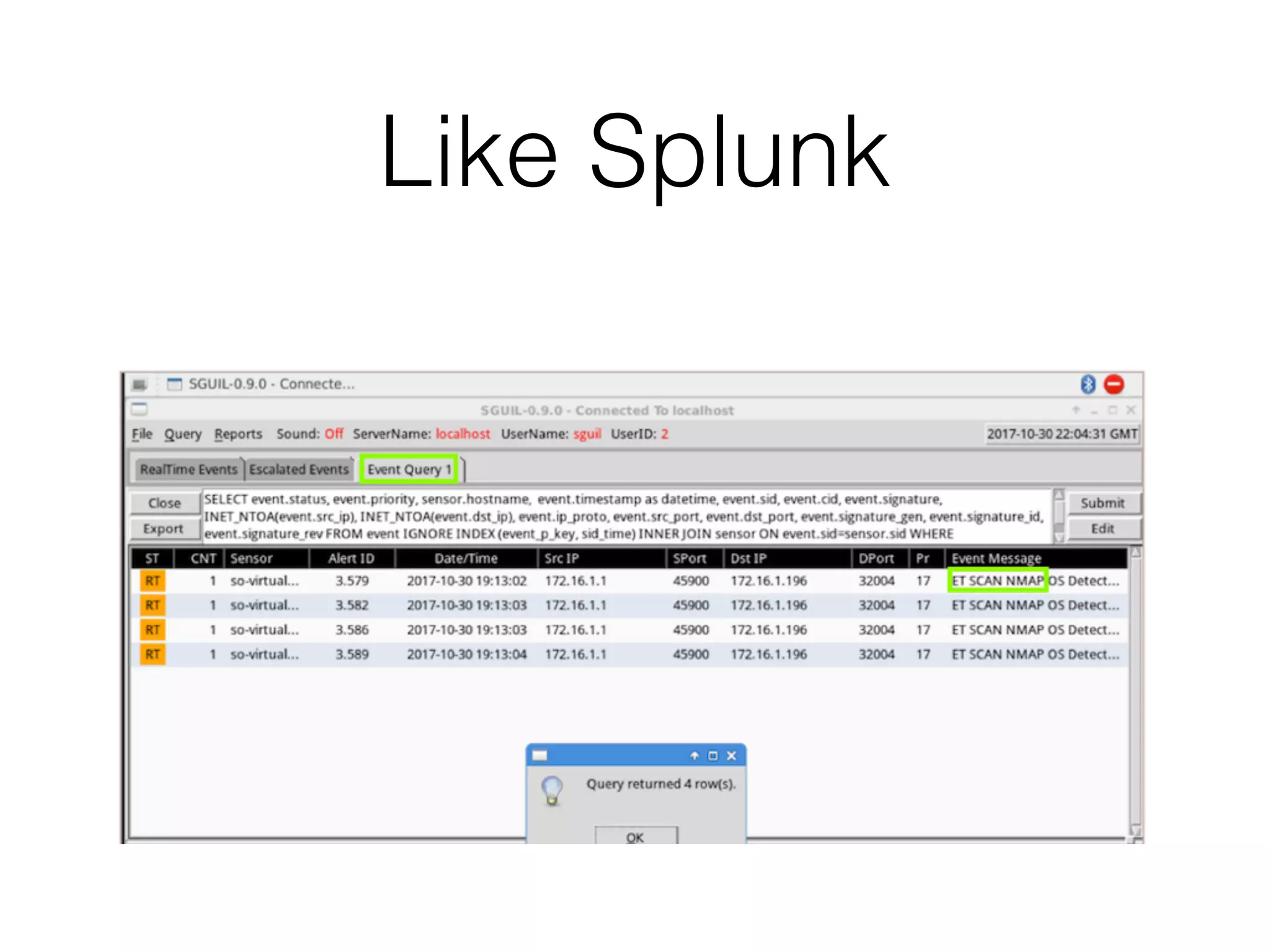
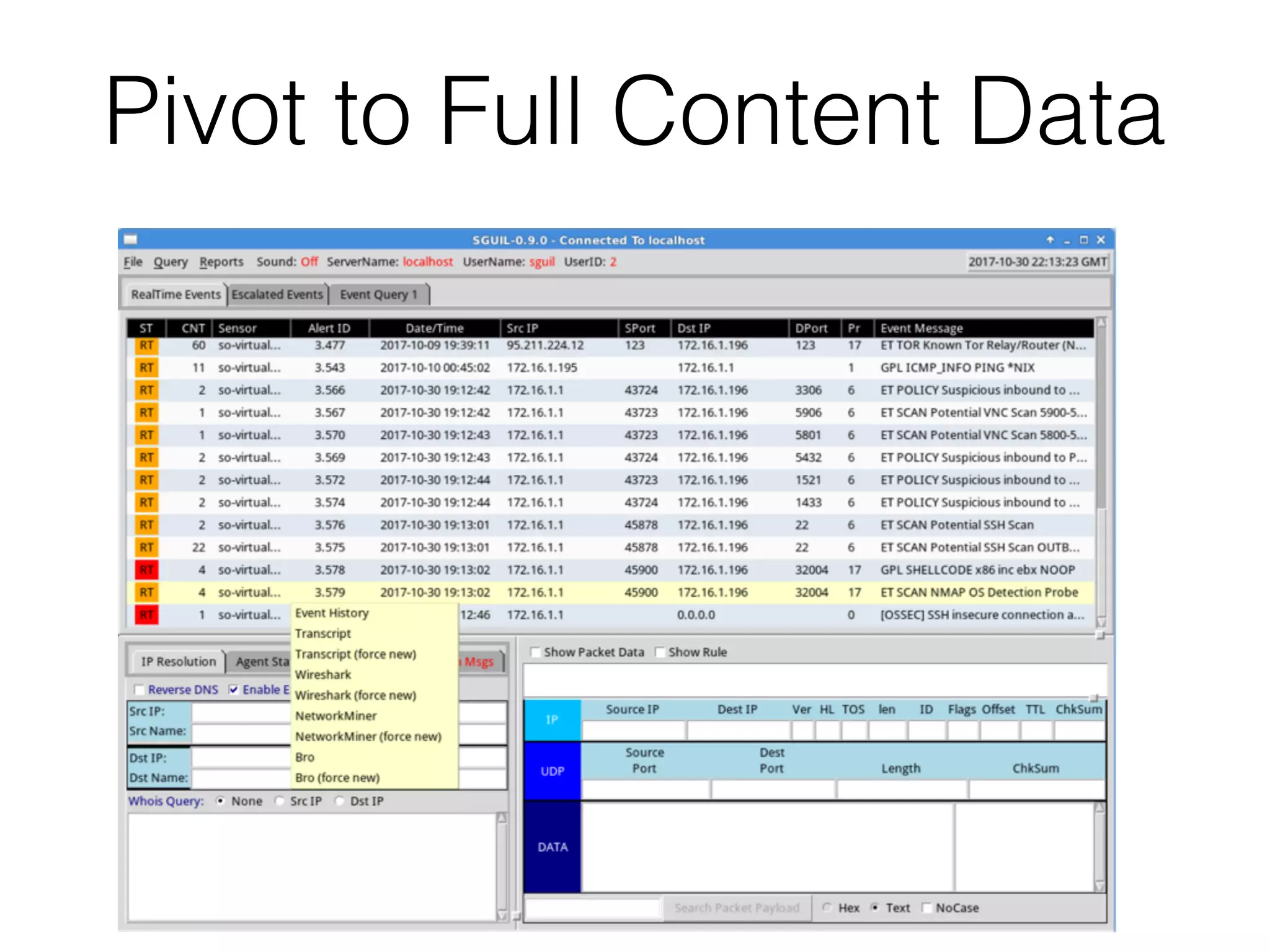
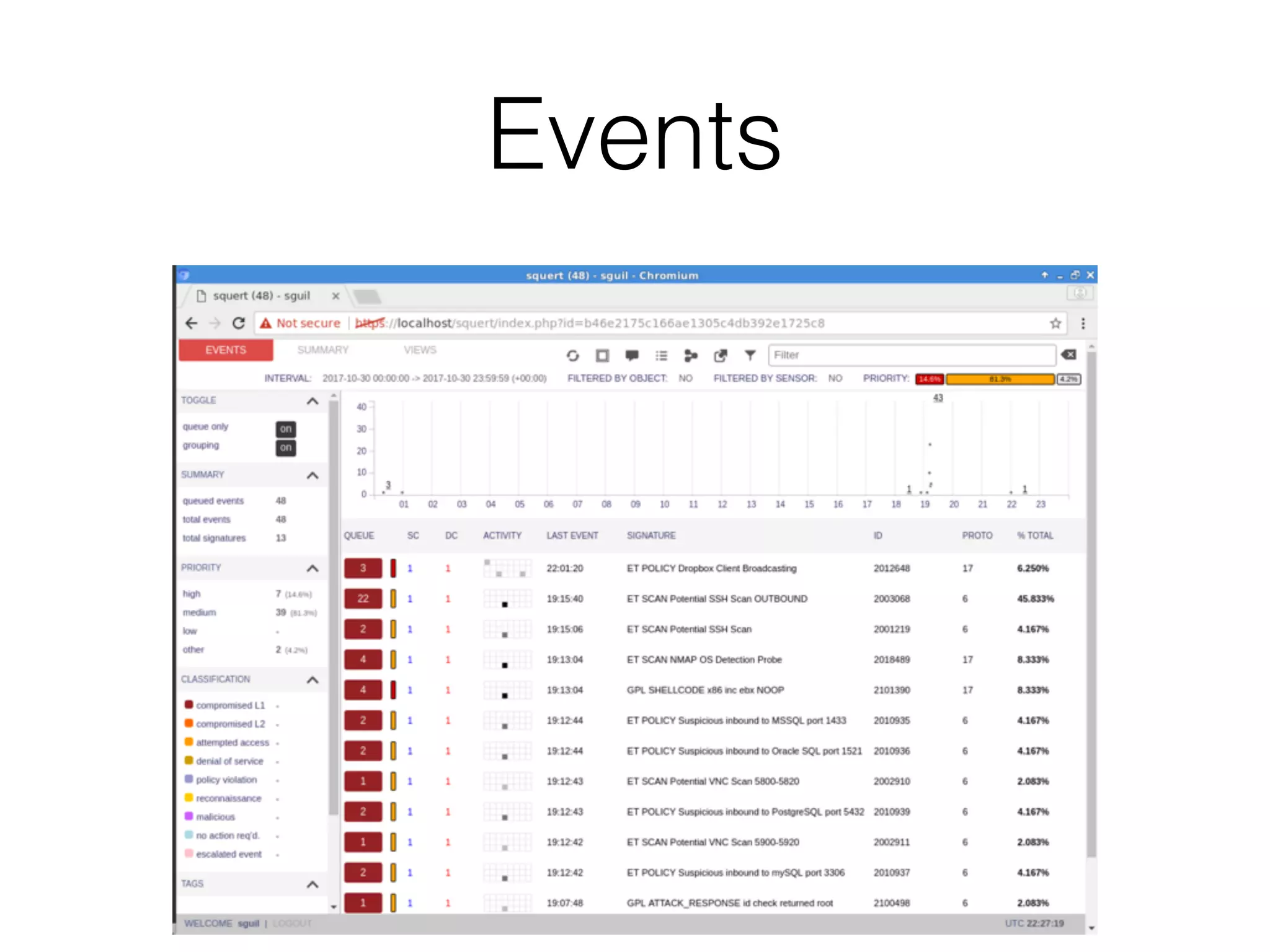







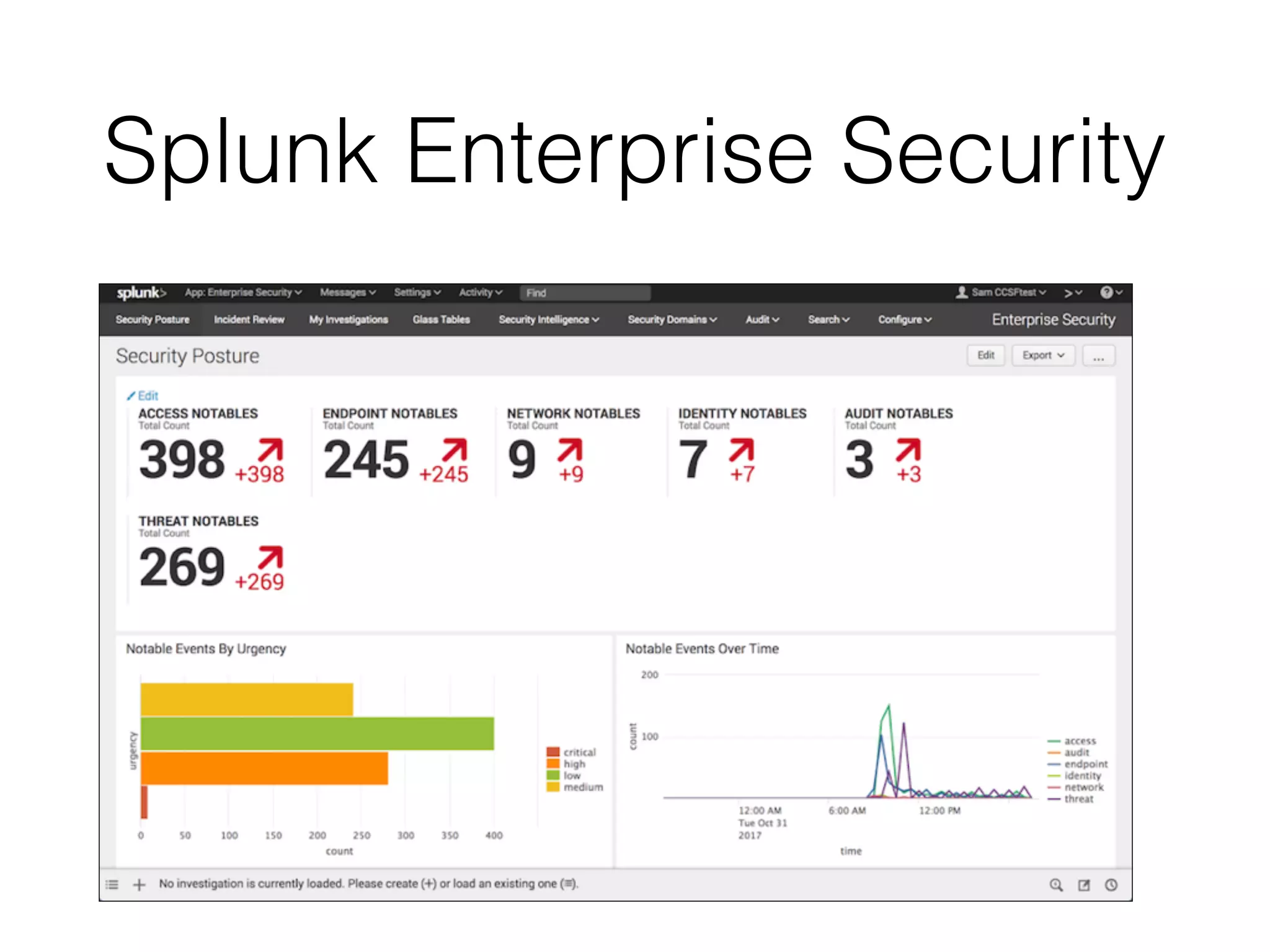


The document discusses various tools and methods for network security monitoring, focusing on graphical packet analysis tools like Wireshark, Xplico, and NetworkMiner. It highlights the limitations and features of each tool, as well as their specific use cases for analyzing network traffic and saved packet captures. Additionally, it reviews different NSM consoles like Sguil, Squert, Snorby, and Elsa for querying and visualizing network data.






































