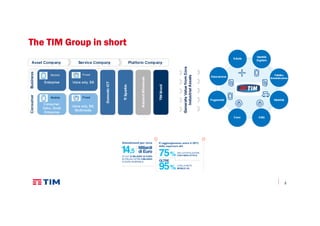
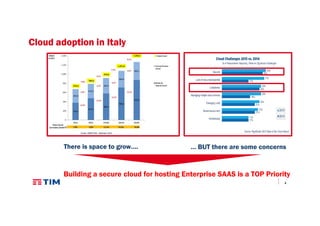
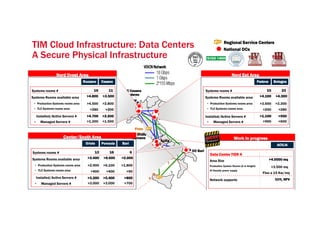
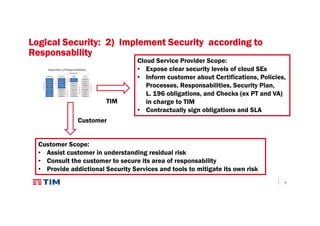
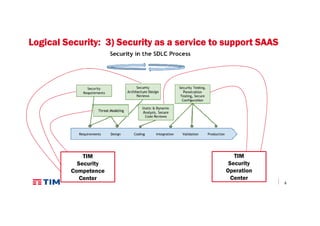
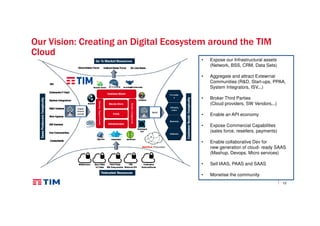
The document discusses TIM Group's cloud security strategies, highlighting their unique offerings compared to OTT players, such as compliance, quality experience, and local presence. It outlines current practices and future challenges in building a secure cloud environment, detailing the infrastructure and logical security measures employed. The text concludes by emphasizing the need for advancements in security technologies and collaborative environments within the cloud ecosystem.