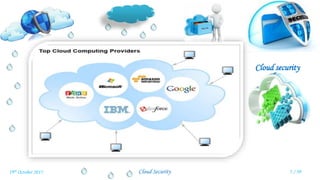
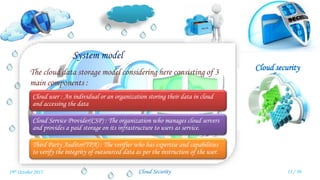
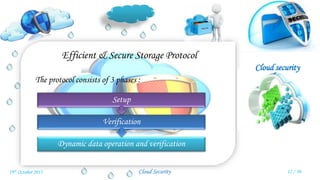
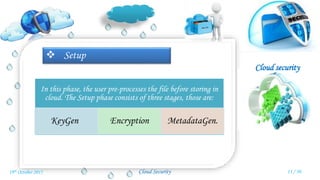
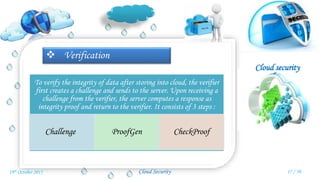
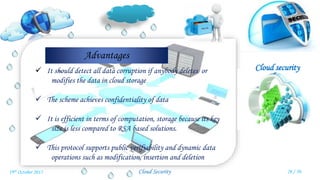
Veena Venugopal presented on cloud security and proposed an efficient and secure protocol for data storage in cloud computing. The protocol has three phases - setup, verification, and dynamic operations and verification. In the setup phase, the user encrypts and generates metadata for the file. A third party auditor verifies the integrity of the stored data by generating challenges and checking proofs from the cloud server. The protocol also supports dynamic operations like modification, insertion, and deletion of blocks while maintaining security. It provides confidentiality, public verifiability, and supports efficient dynamic operations on outsourced data in the cloud.