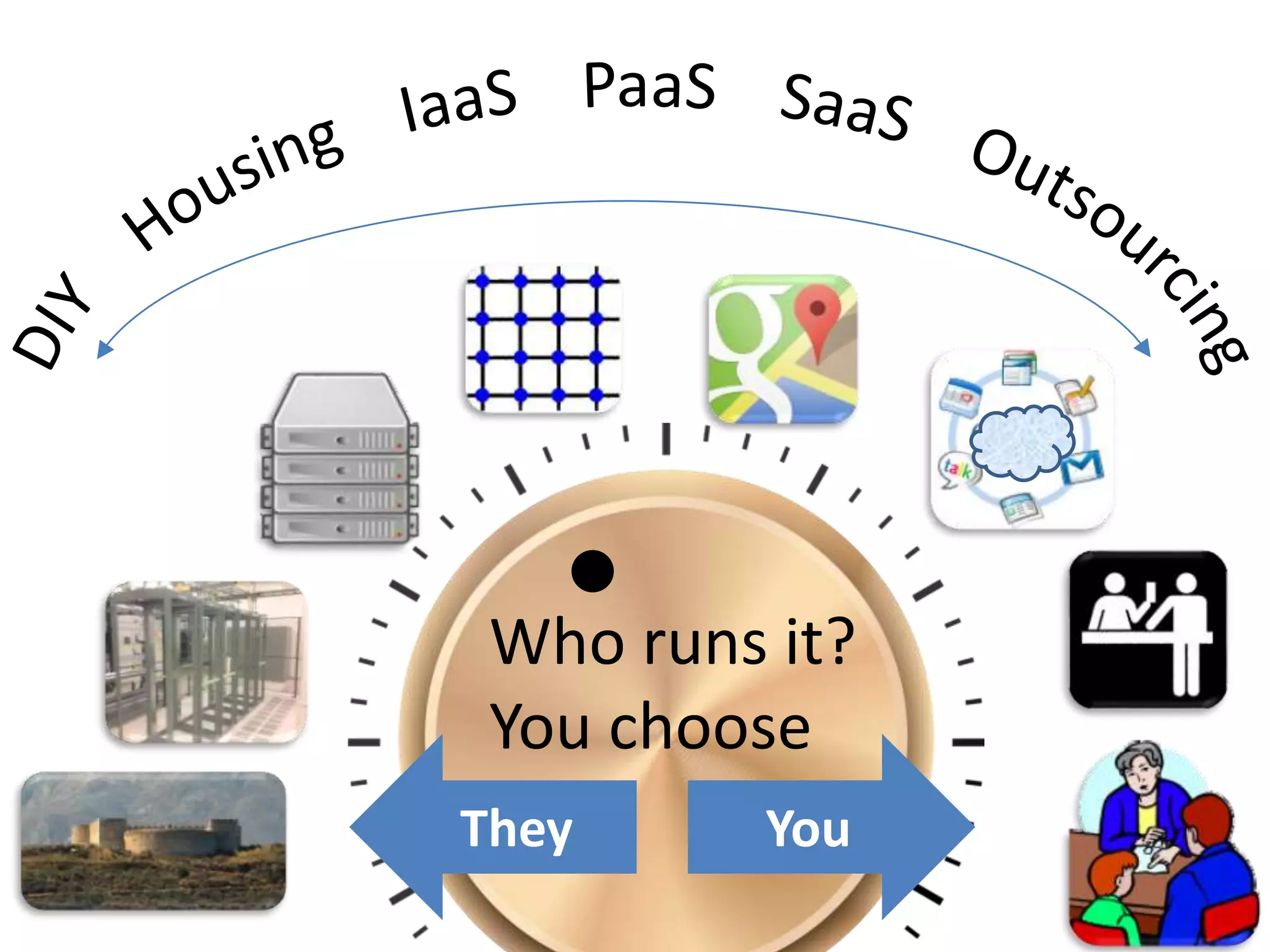
The document provides an overview of the Certificate of Cloud Security Knowledge (CCSK) certification. It discusses the history and purpose of the CCSK, which was created by the Cloud Security Alliance to promote best practices for security in cloud computing. The CCSK certification tests knowledge across 15 domains related to cloud security and is intended to help both consumers and vendors discuss security risks and assurances. To become certified, candidates must pass an online multiple choice exam that covers all domains and must be completed within 90 minutes with a score of 80% or higher.