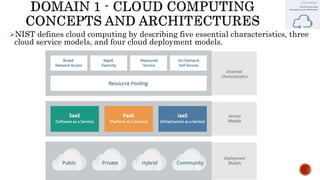
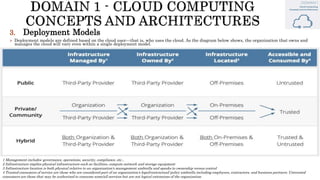
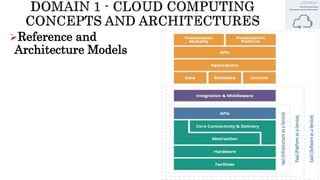
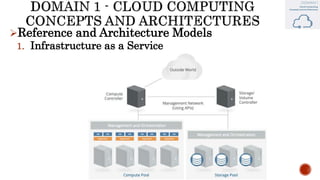
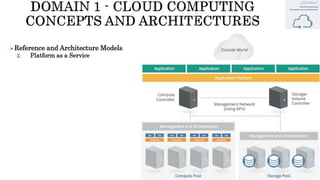
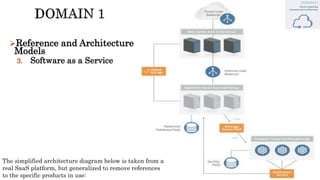
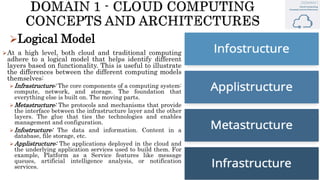
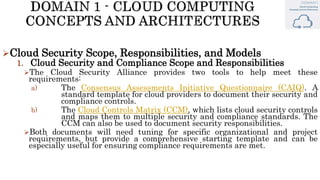
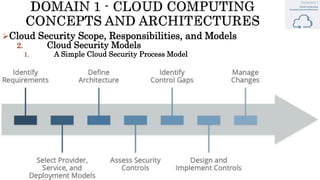
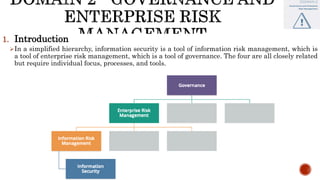
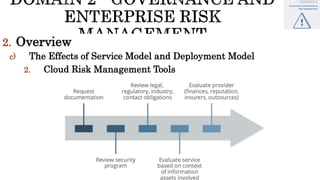
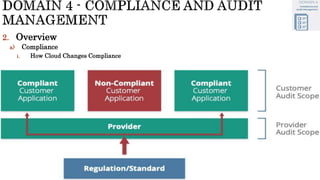
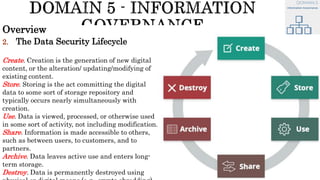
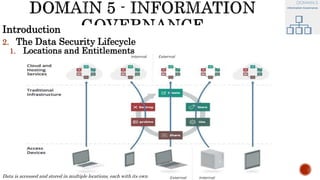
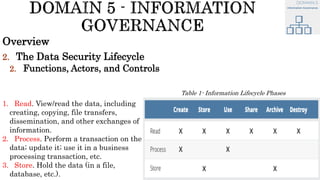
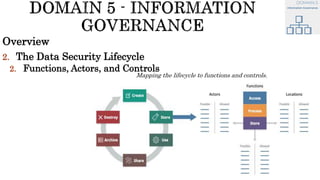
The document discusses key concepts in cloud computing, including definitions, models, and architectures. It defines cloud computing using NIST and ISO/IEC definitions, noting essential characteristics like on-demand self-service, broad network access, resource pooling, rapid elasticity, and measured service. It describes cloud service models including Software as a Service (SaaS), Platform as a Service (PaaS), and Infrastructure as a Service (IaaS), as well as deployment models like public, private, community, and hybrid clouds. The document also provides reference architectural models for IaaS, PaaS and SaaS and discusses logical models and security scope in cloud computing.