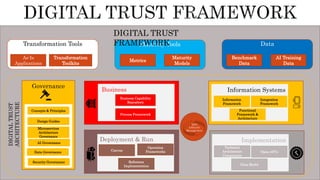
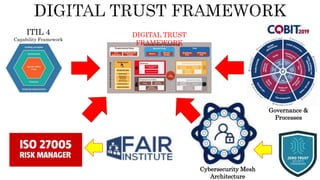
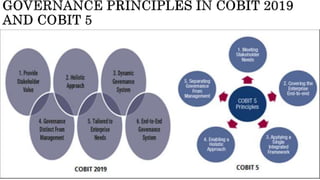
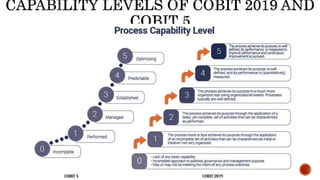
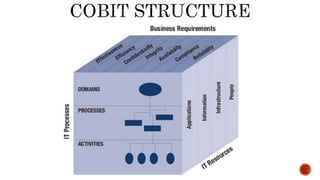
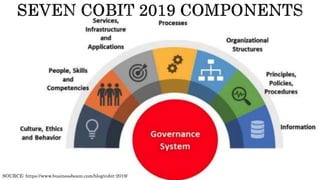
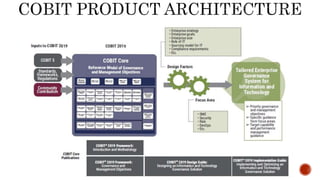
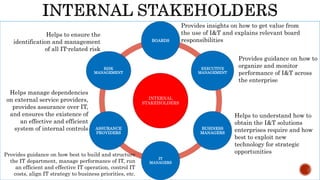
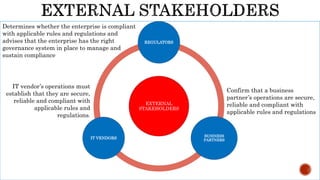
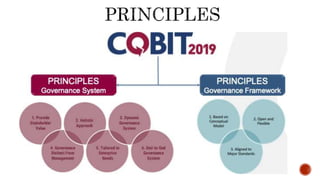
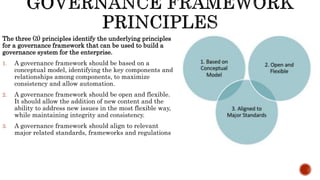
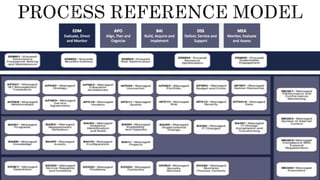
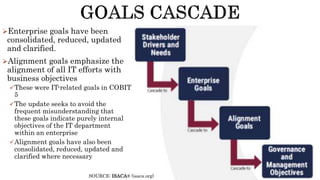
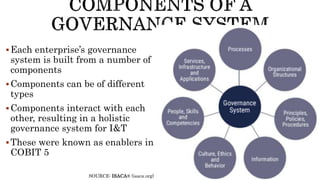
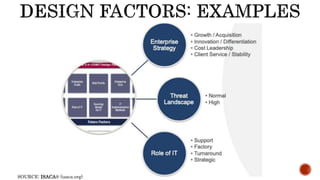
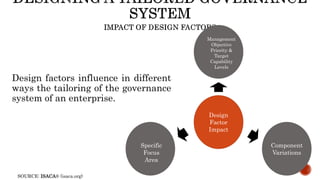
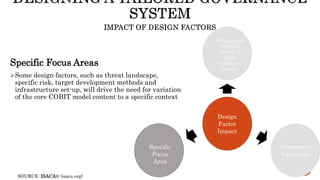
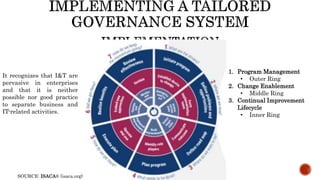
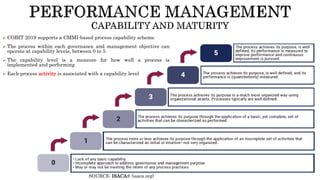
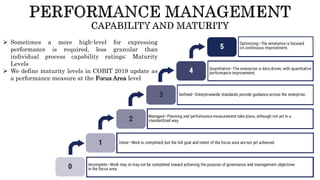
The document provides an overview of the Digital Trust Framework (DTF) and how it will integrate several frameworks including ODA, COBIT 2019, ITIL 4, and ISO 27005 to provide an overall approach for digital trust. The DTF will be a modular, cloud-based, open digital platform that can be orchestrated using AI. It will use the TMForum's Open Digital Architecture as a cornerstone and was developed for a 4IR environment.