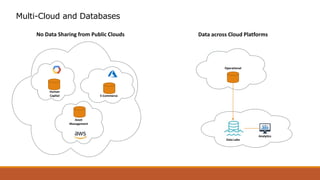
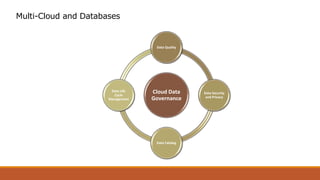
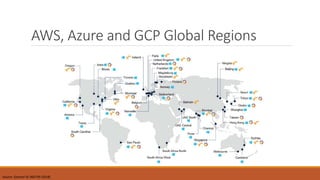
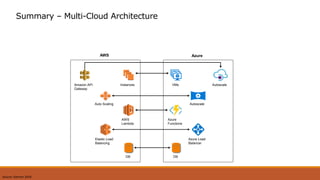
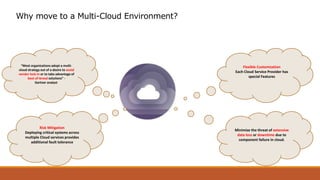
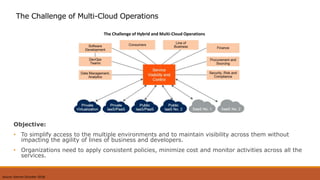
The document discusses the challenges of transitioning to a multi-cloud environment and proposes solutions across six architecture domains: 1) provisioning infrastructure as code while enforcing policies, 2) implementing a zero-trust security model with secrets management and encryption, 3) using a service registry and service mesh for networking, 4) delivering both modern and legacy applications via flexible orchestration, 5) addressing issues of databases across cloud platforms, and 6) establishing multi-cloud governance and policy management. The goal is to simplify management of resources distributed across multiple cloud providers while maintaining visibility, consistency, and cost optimization.











![Multi-Cloud Security
SaaS PaaS IaaS
Any User
Any Device
Any Network
Identity and Access Management [Identity as a Service (IDaaS)]
• Single Sign-On
• Universal Directory
• Multi Factor Authentication
• Life Cycle Management
• Mobility Management
• API Access Management
• Developer Platform](https://image.slidesharecdn.com/multi-cloudarchitectureapproach-191108143853/85/Multi-Cloud-Architecture-Approach-14-320.jpg)