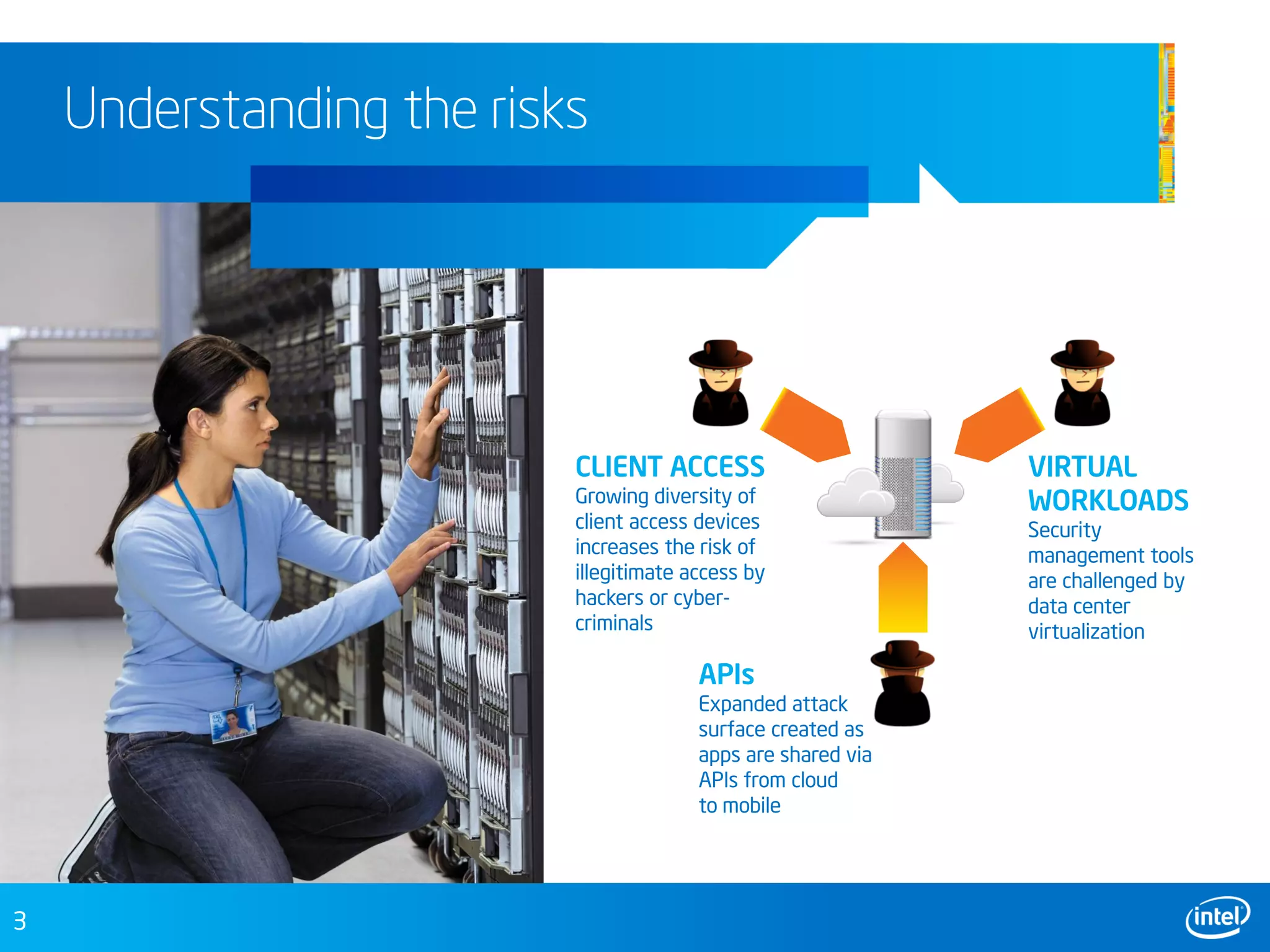
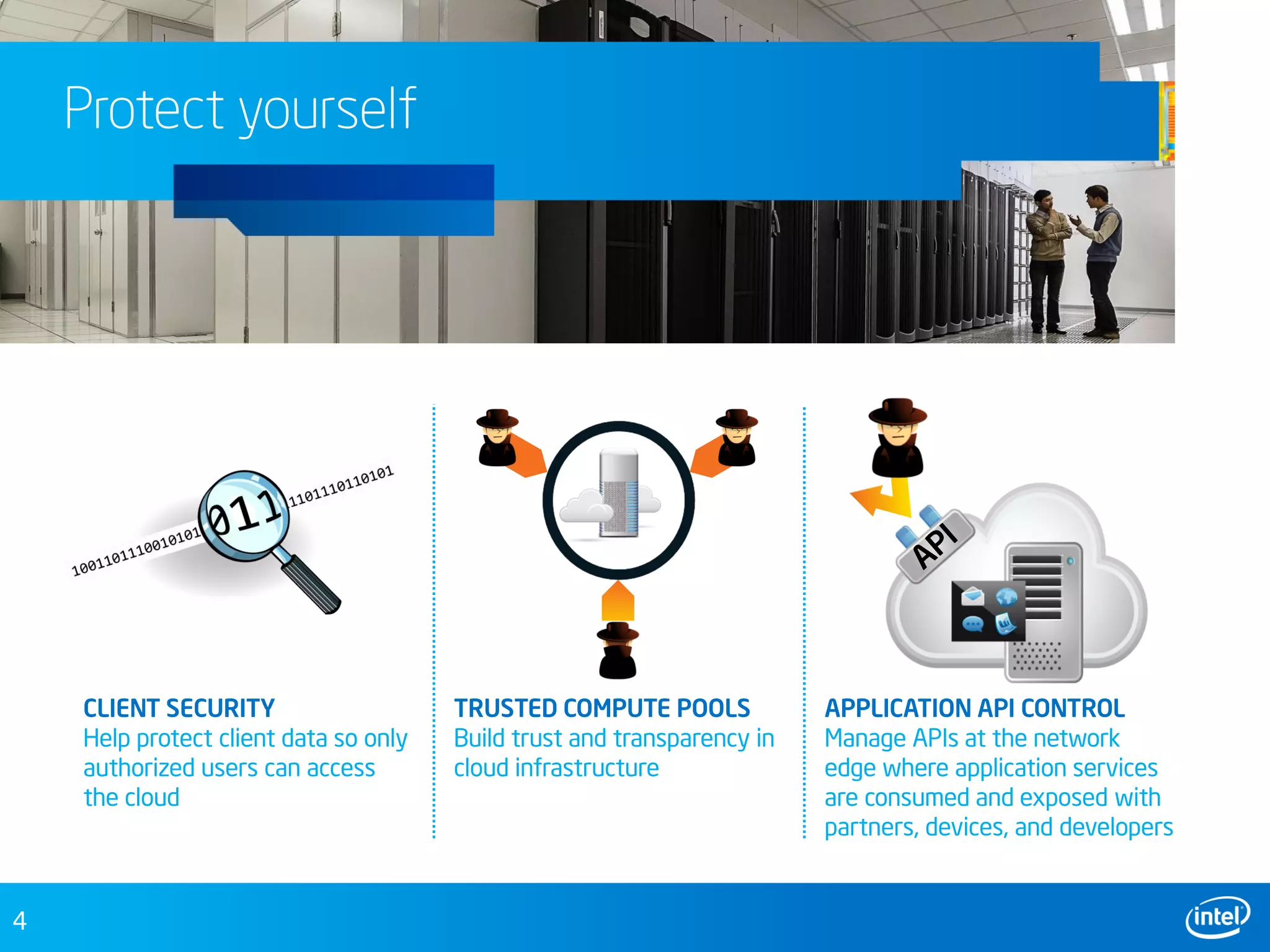
This document discusses security challenges in cloud computing environments and provides recommendations for securing infrastructure and data. It outlines growing risks from a diversity of client access devices, virtualized workloads, and expanded APIs. The document recommends establishing trusted compute pools using Intel Trusted Execution Technology to provide a foundation of trust. It also suggests controlling APIs at network edges and providing more secure client access through technologies like Intel Identity Protection and McAfee solutions. The overall goal is to help users move to the cloud with confidence by protecting infrastructure and data.