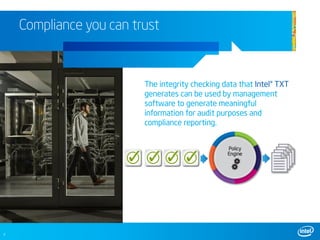
The document discusses cloud security and compliance. It notes that security compliance has become more complex with growing threats and virtualization. It emphasizes the need to trust hardware, resources, and verification processes used. Intel Trusted Execution Technology is highlighted as a way to determine if a system can be trusted and establish a pool of known good resources. Compliance reporting and added protection are also benefits. Downloading a security planning guide is recommended to learn how to protect data from device to data center.