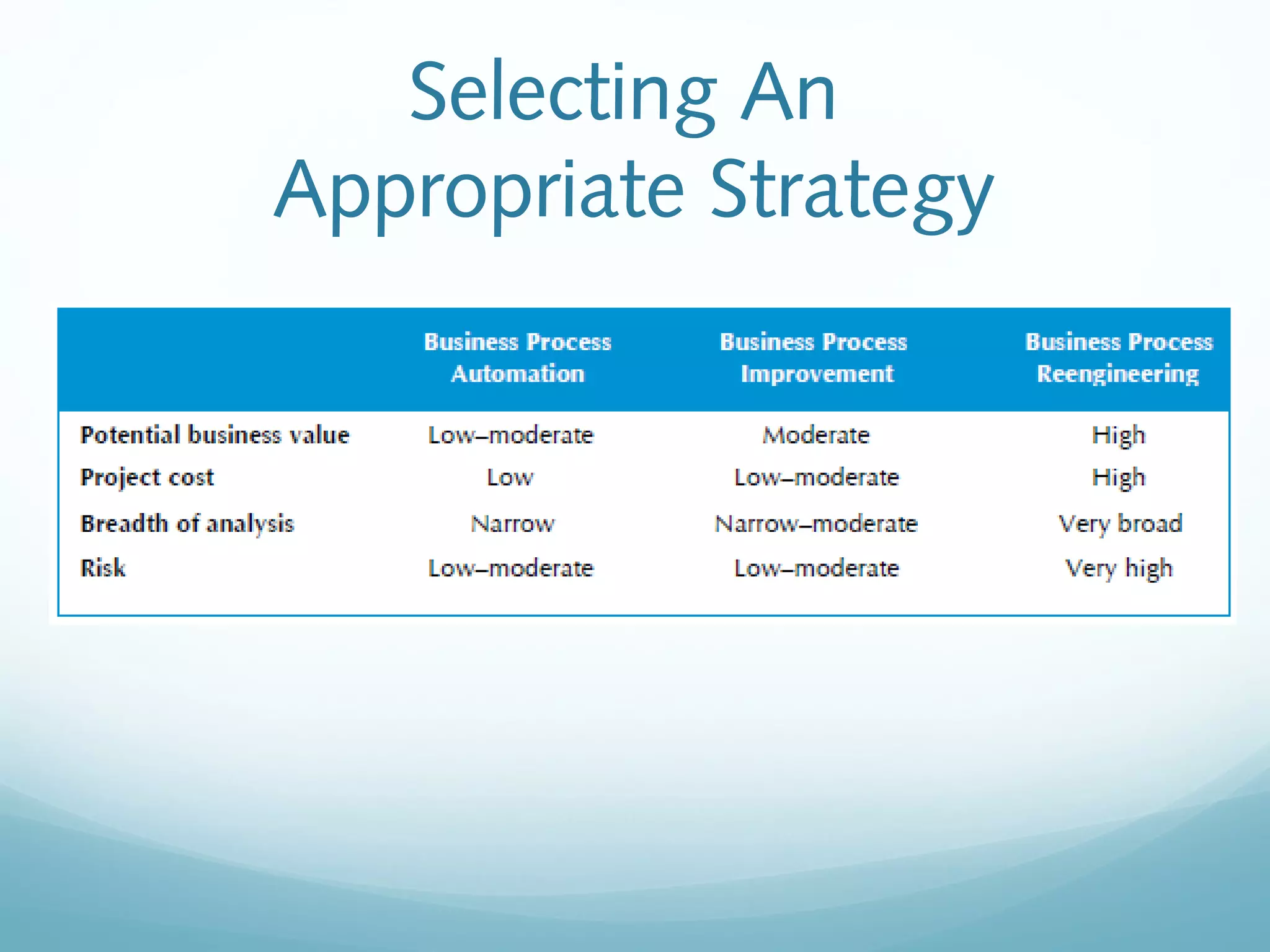
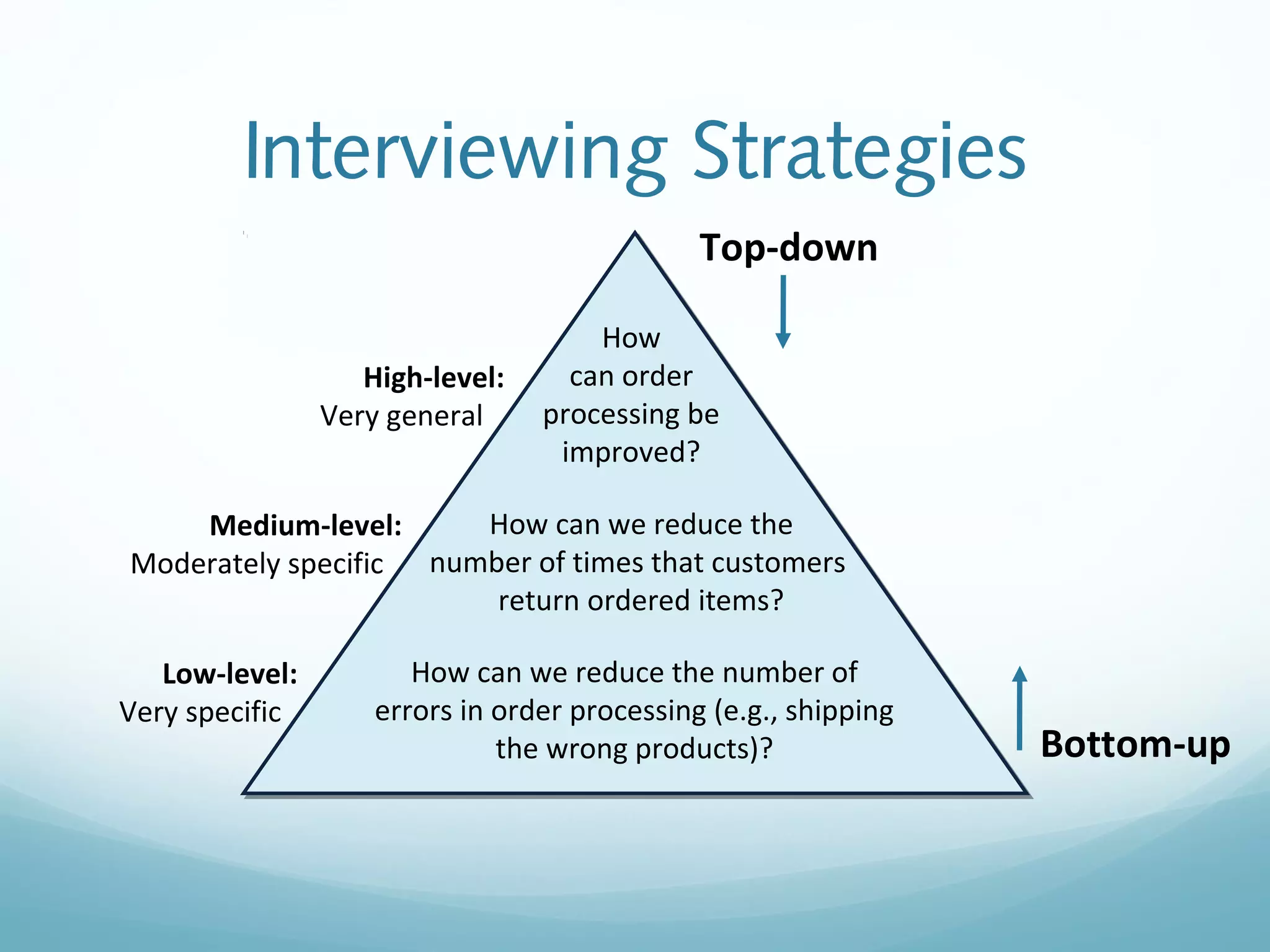
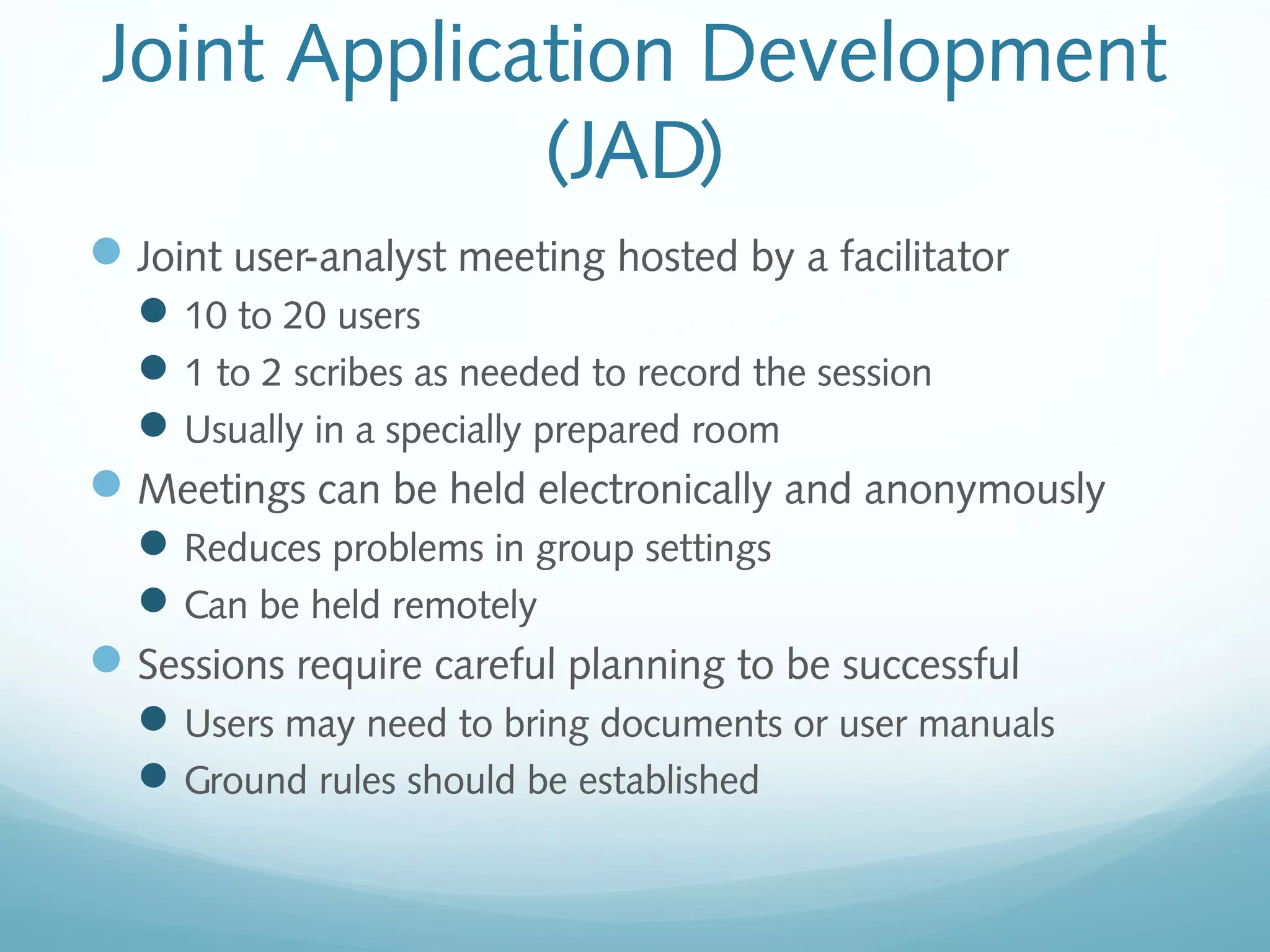
The document discusses requirements determination, which aims to convert high-level business needs into detailed requirements. It covers requirements analysis strategies like business process automation, improvement, and reengineering. Techniques for gathering requirements are described, including interviews, questionnaires, joint application development sessions, document analysis, and observation. Alternative documentation methods like concept maps and story cards are also presented. The chapter concludes with an overview of the contents of a system proposal document.