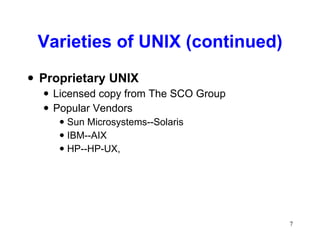
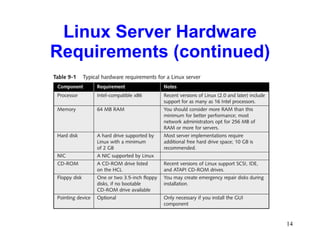
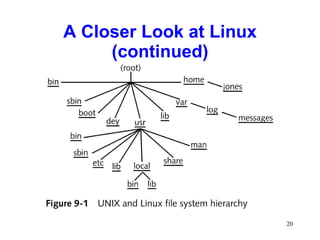
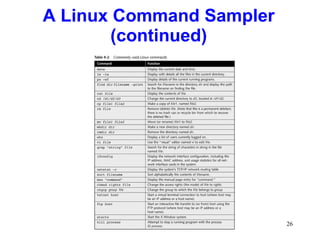
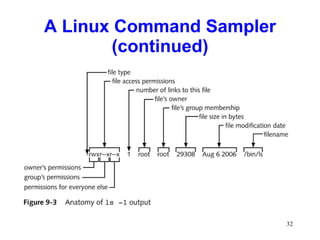
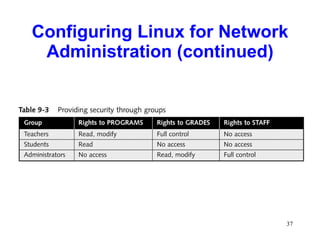
This chapter discusses the history and varieties of UNIX and Linux operating systems. It describes how to install Linux, configure users and permissions, and interconnect Linux with other network operating systems using tools like Samba, WINE, VMware and Telnet. The chapter also provides examples of basic Linux commands and how to set up a Linux server with the required hardware specifications.