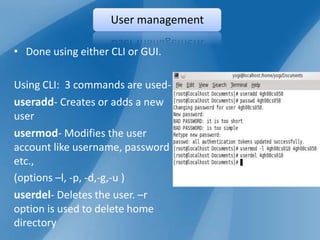
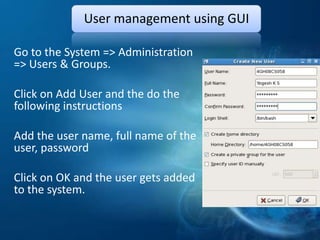
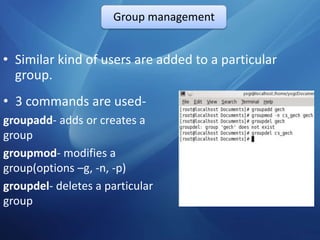
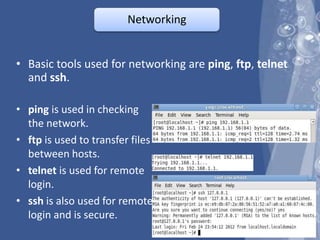
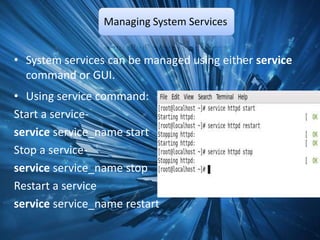
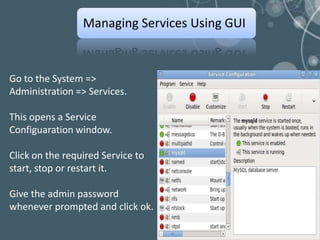
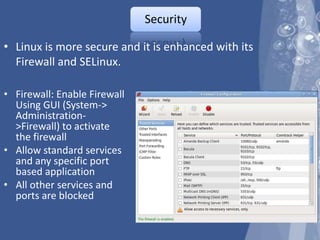
The document outlines a technical seminar on Linux administration presented by Yogesh K S. It discusses key topics like installing Linux, user and group management, security features like firewalls and SELinux, managing services, backups, and package management. The seminar covered essential admin tasks, tools, and commands for system installation, configuration, maintenance and security.





![Communicating with Users
• The admin should
communicate with the users
to intimate about the changes.
• Commands used-
wall- addresses all users
simultaneously who are
currently logged in.
Syntax: wall msg
write-addresses a single user
Syntax: write username [tty] msg](https://image.slidesharecdn.com/linuxadministration-120613145938-phpapp01/85/Linux-administration-12-320.jpg)




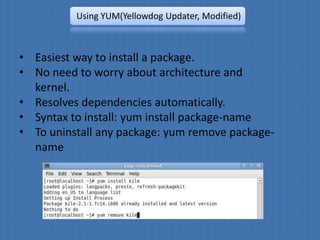
![Using RPM(Redhat Package Manager)
• Be aware of Architecture and type of kernel.
• Syntax: rpm [options] file.rpm(-i=install, -U= upgrade,
-e= erase)
• To install a package: rpm –i pkg.rpm
• To remove a package: rpm –e pkg](https://image.slidesharecdn.com/linuxadministration-120613145938-phpapp01/85/Linux-administration-20-320.jpg)