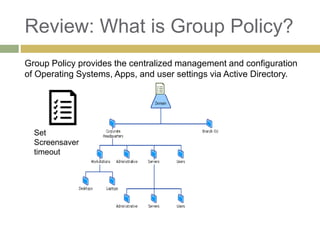
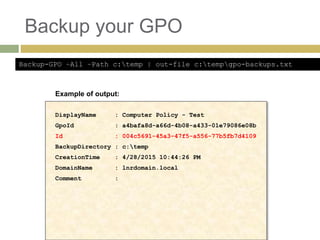
The document provides an overview of Group Policy, its management, and useful tips for configuring settings via Active Directory. It covers various aspects including Group Policy Objects (GPOs), their application order, software restriction policies, and the use of PowerShell for managing GPOs. Additionally, it discusses the importance of Group Policy Preferences and loopback processing for terminal services, emphasizing best practices for security and management.