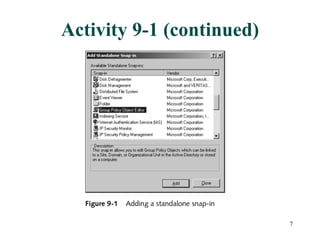
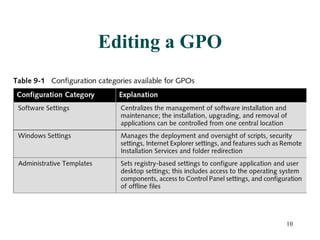
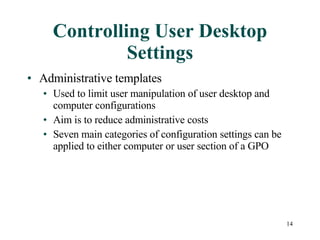
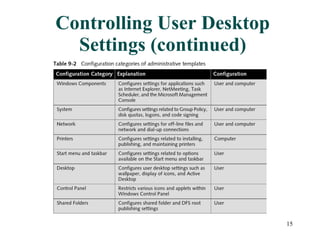
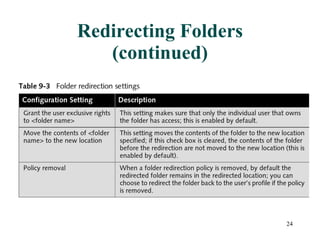
Group Policy Objects (GPOs) can be used to centrally manage user and computer settings across a Windows network. GPOs are created and linked to sites, domains, and organizational units to apply policies to all computers and users within those containers. Common uses of GPOs include controlling user desktop settings and security, deploying login and startup scripts, redirecting user folders, and installing or removing software applications. Troubleshooting tools like GPRESULT and Resultant Set of Policy can help determine which policies are in effect for a given user or computer.