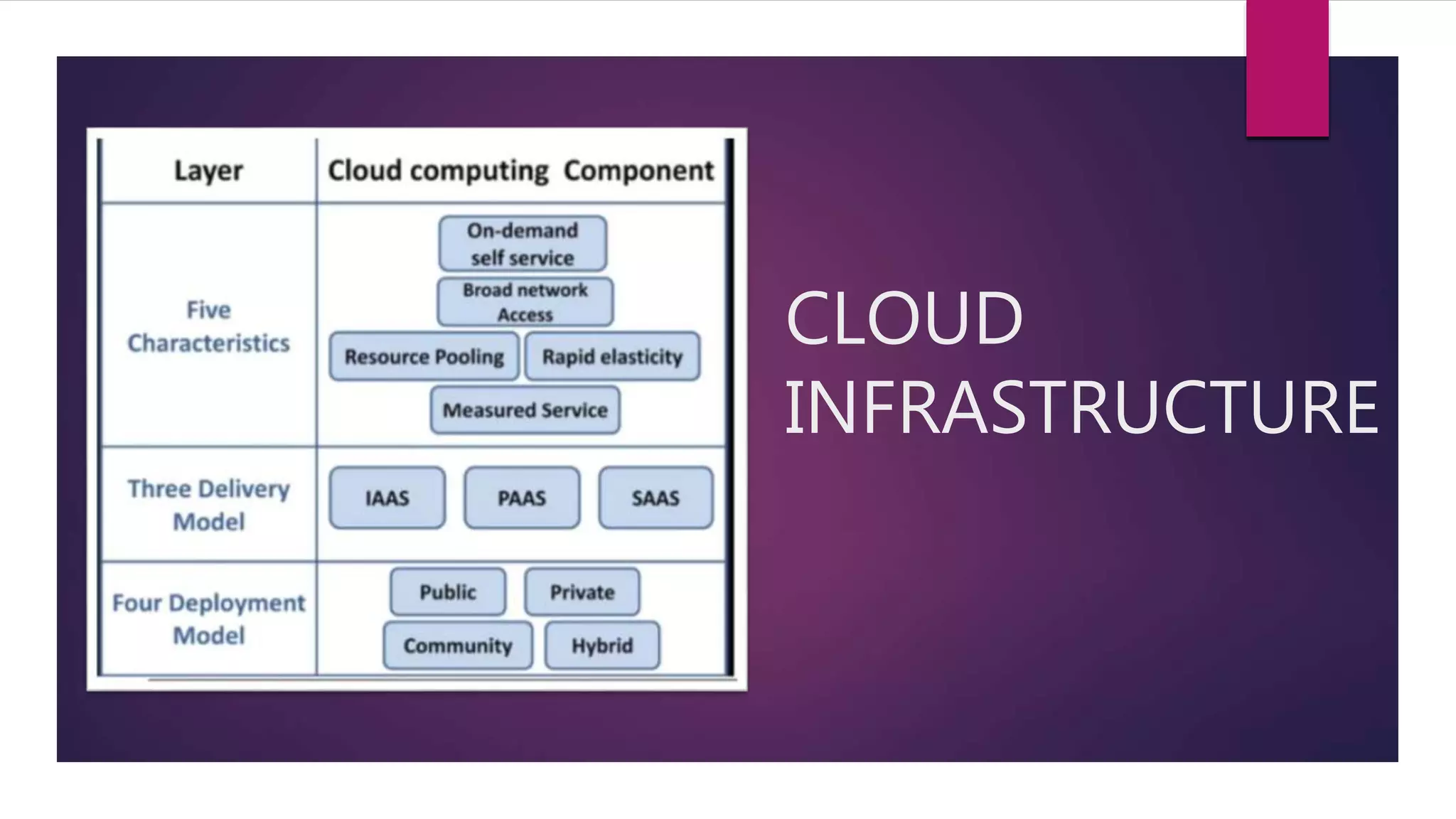
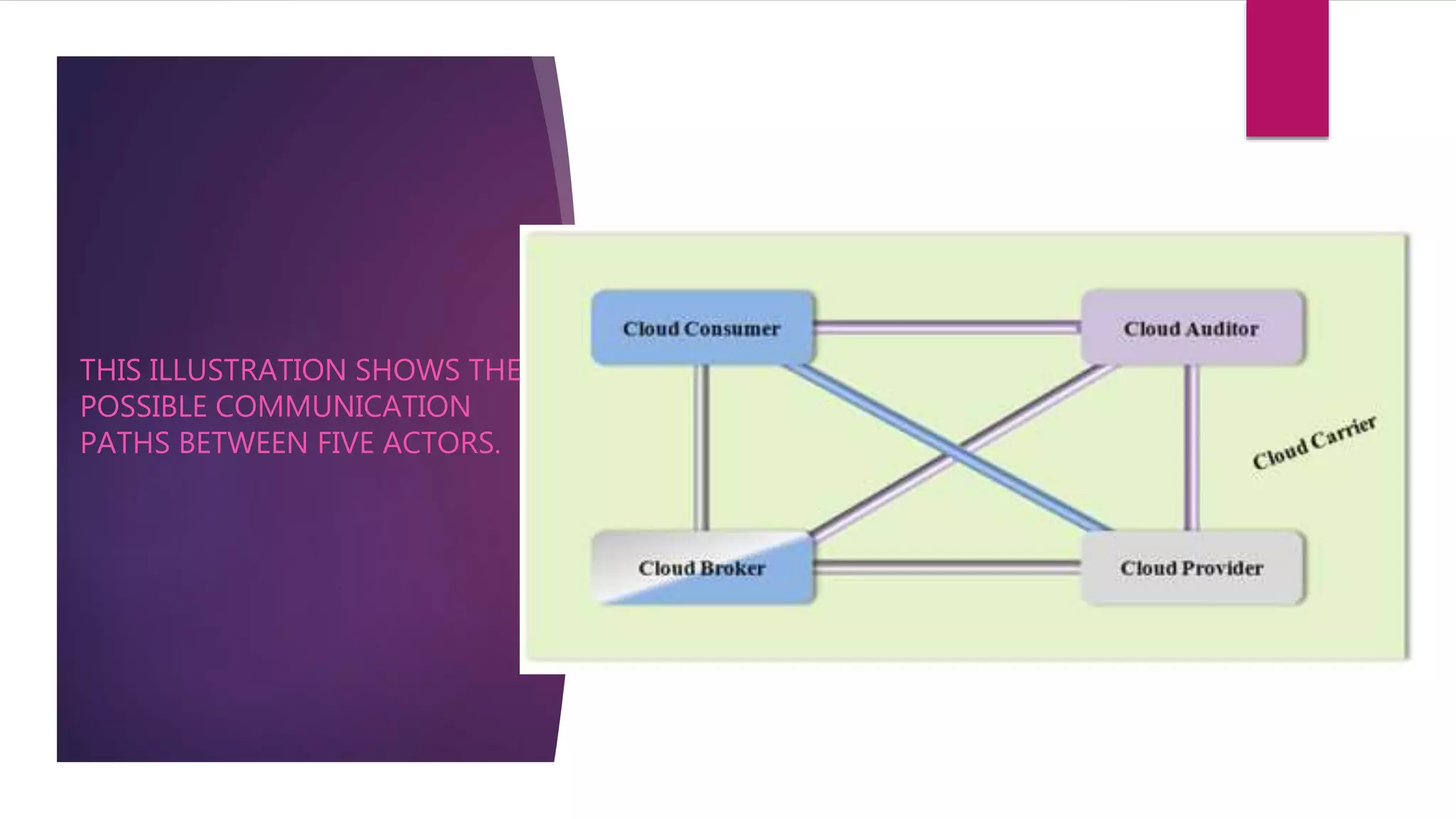
This document discusses security risks and recommendations for cloud computing. The top threats to cloud security are data breaches, data loss, account hijacking, insecure interfaces and APIs, denial of service attacks, malicious insiders, insufficient due diligence, abuse of cloud services, and shared technology vulnerabilities. Virtual machines (VMs) are also vulnerable via VM attacks between VMs on the same physical server, increased attack surface from multitenancy, and hypervisor attacks that can control all VMs and systems. The document recommends security measures like security information and event management (SIEM), identity and access management (IAM), data dispersion, data leakage prevention (DLP), bit splitting, cloud monitoring, load balancing, effective exit processes, and