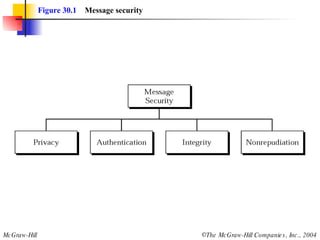
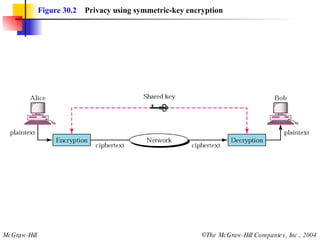
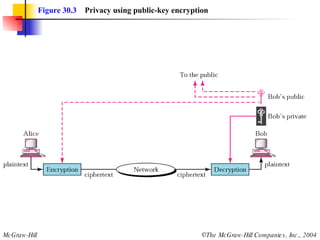
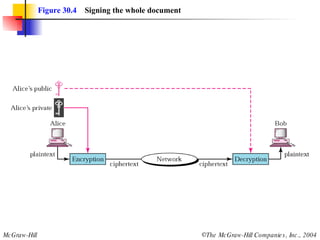
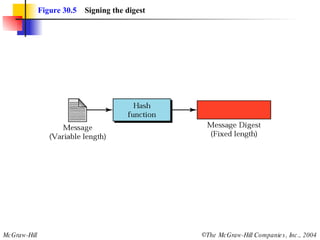
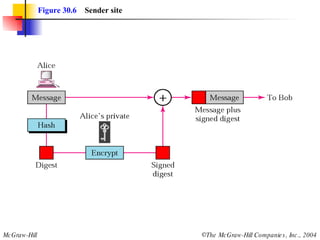
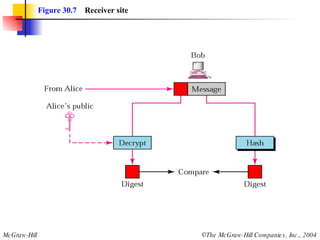
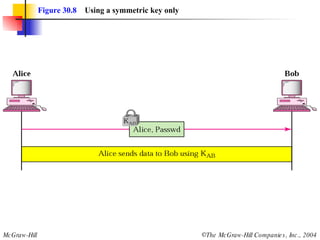
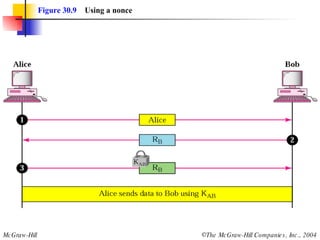
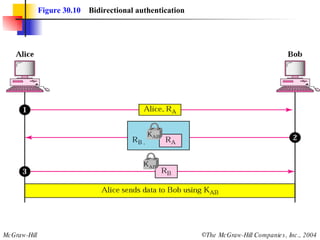
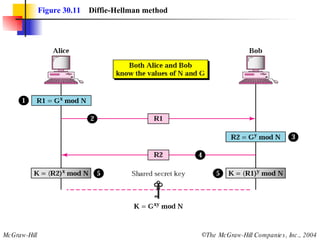
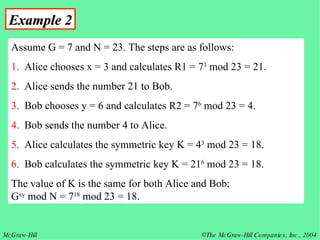
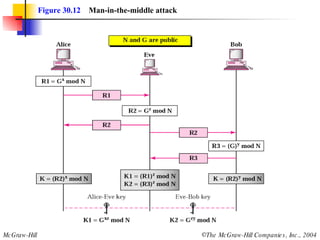
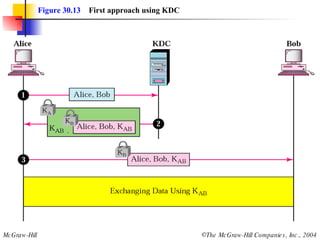
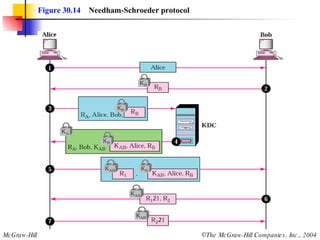
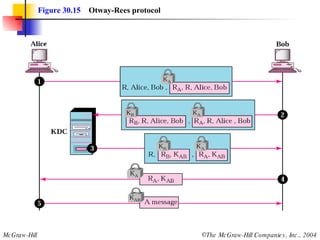
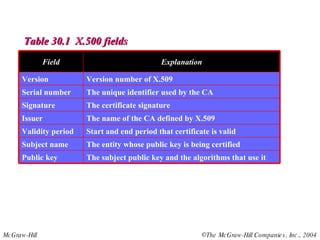
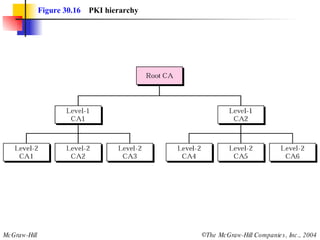
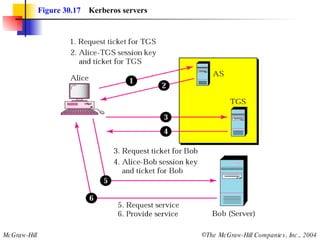
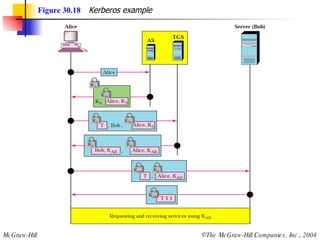
This document discusses message security, user authentication, and key management. It covers digital signatures, symmetric and asymmetric encryption, authentication using keys or nonces, key distribution methods like Diffie-Hellman, and public key infrastructure including the X.500 standard and certificate fields. Kerberos is introduced as a network authentication system using ticket-granting servers. Diagrams illustrate privacy, signatures, authentication approaches, man-in-the-middle attacks, key distribution centers, and the Kerberos process.