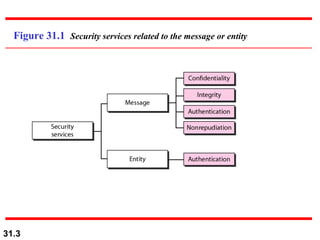
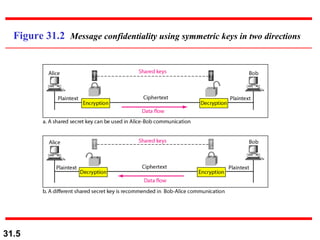
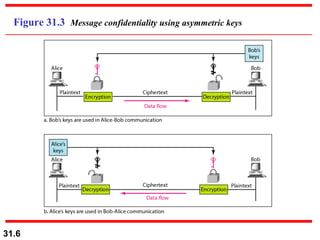
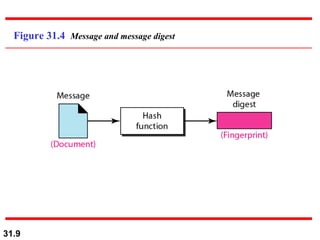
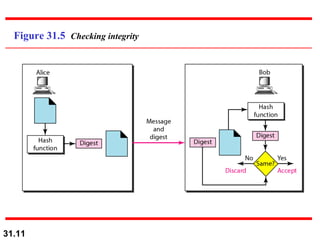
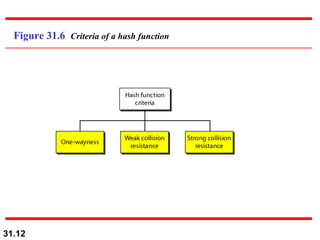
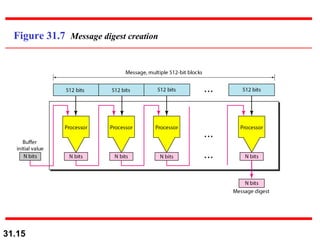
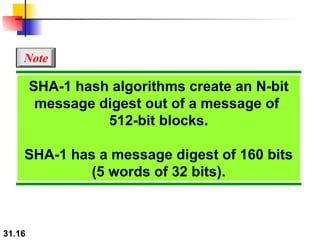
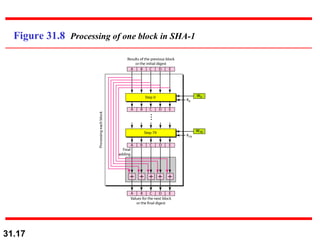
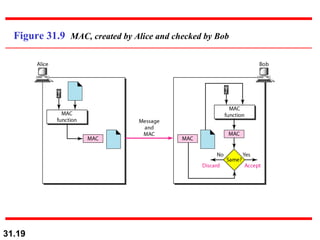
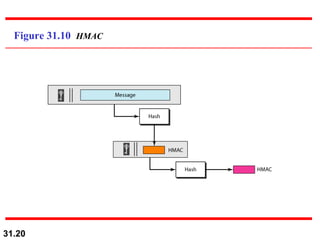
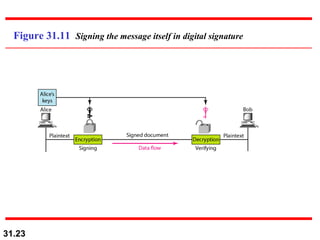
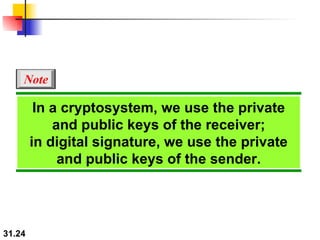
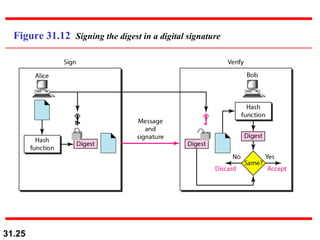
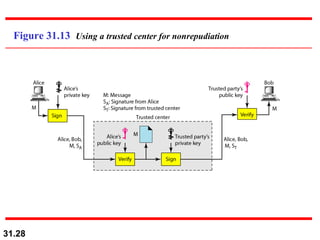
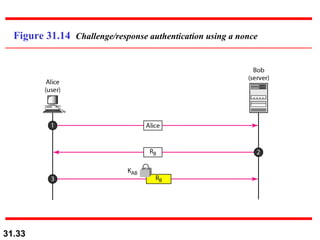
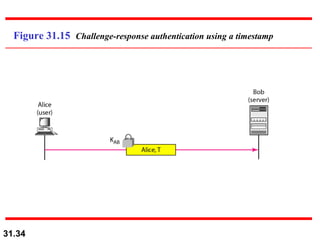
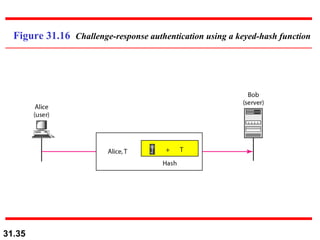
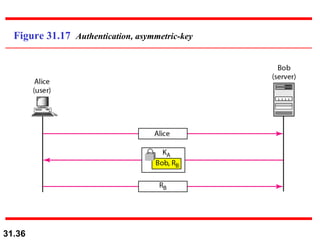
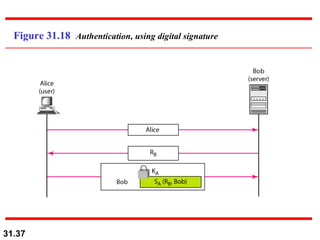
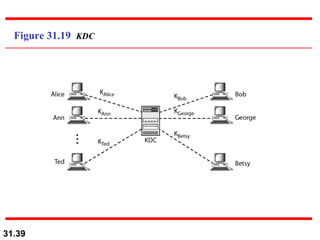
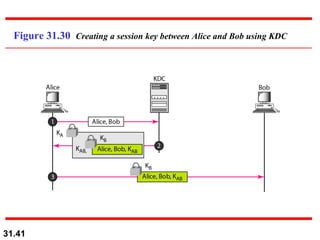
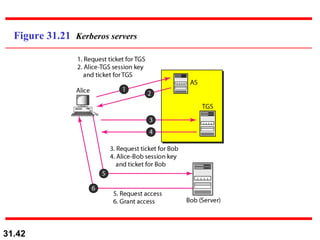
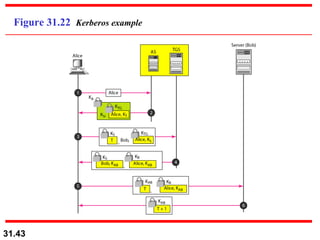
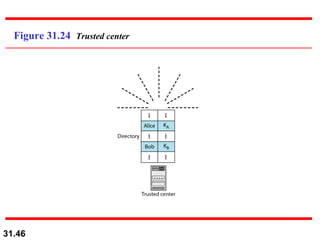
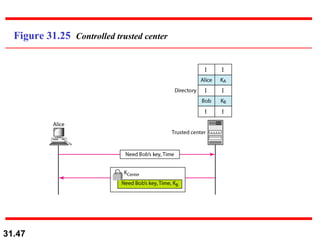
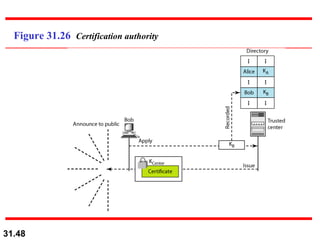
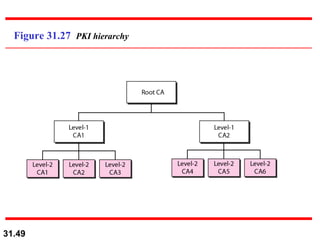
The document discusses network security and provides an overview of five security services: message confidentiality, message integrity, message authentication, message nonrepudiation, and entity authentication. It describes how each of these services can be achieved using techniques like symmetric and asymmetric encryption, hashing, digital signatures, challenge-response authentication, and key management protocols.