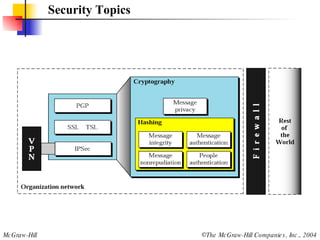
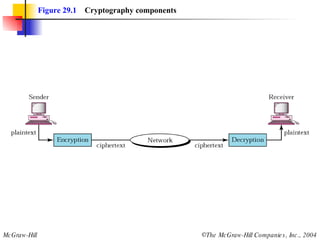
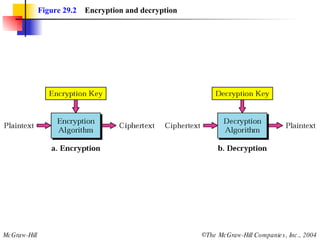
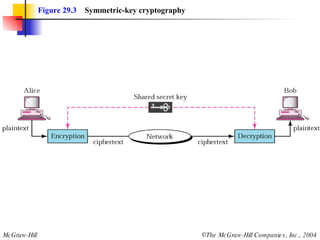
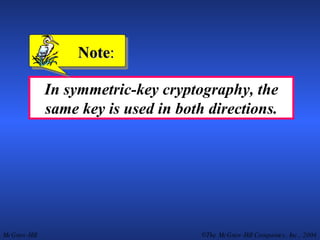
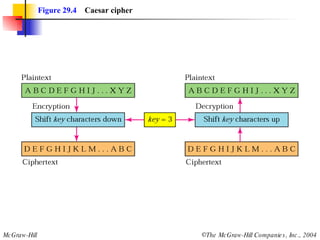
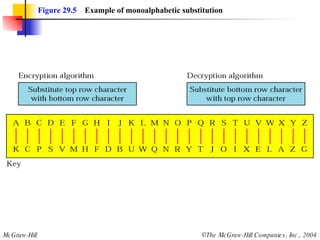
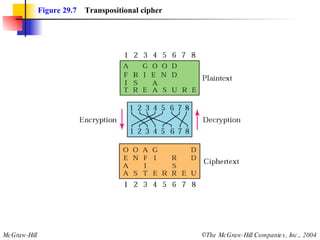
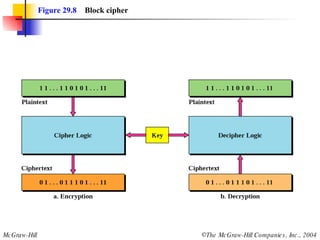
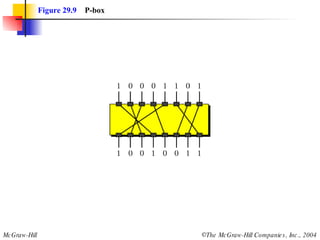
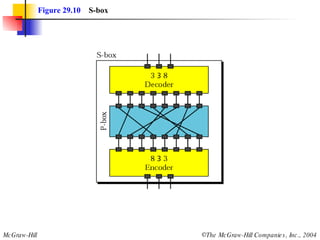
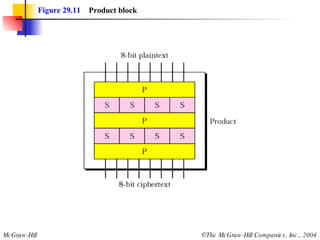
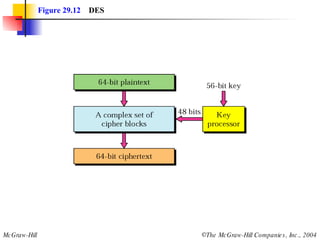
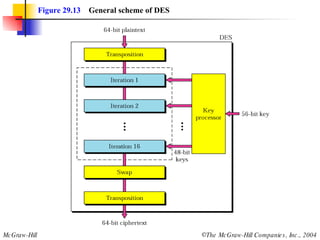
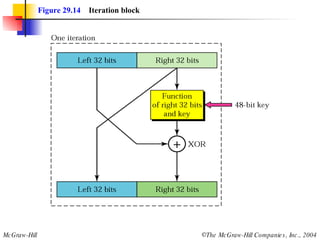
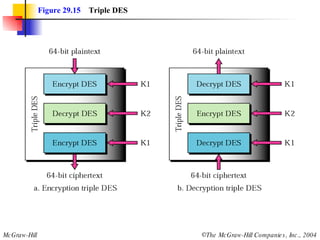
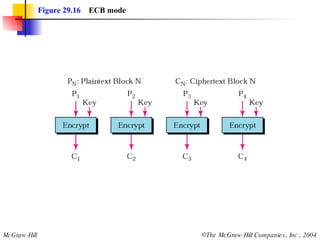
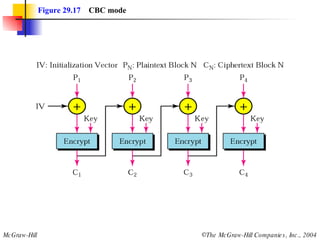
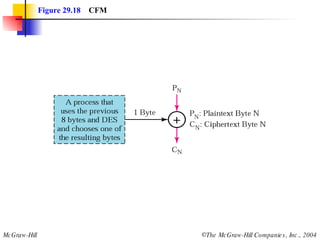
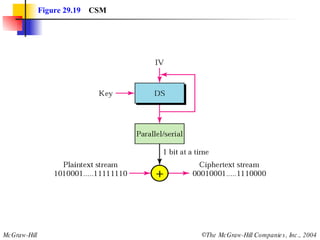
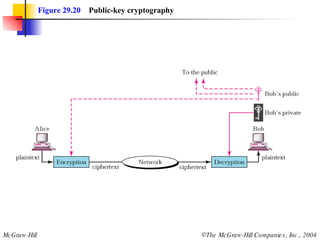
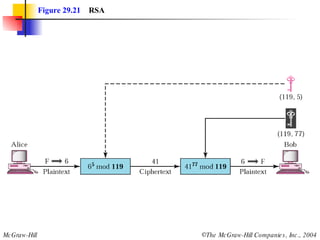
This document discusses cryptography and contains sections on symmetric-key cryptography, public-key cryptography, and security protocols on the internet. It includes diagrams of encryption algorithms like DES and RSA, as well as block ciphers, product blocks, substitution ciphers, and encryption modes like ECB and CBC. Key points covered include how symmetric-key cryptography uses the same key for encryption and decryption while public-key uses different keys, and how algorithms like DES are more complex versions of the Caesar cipher.