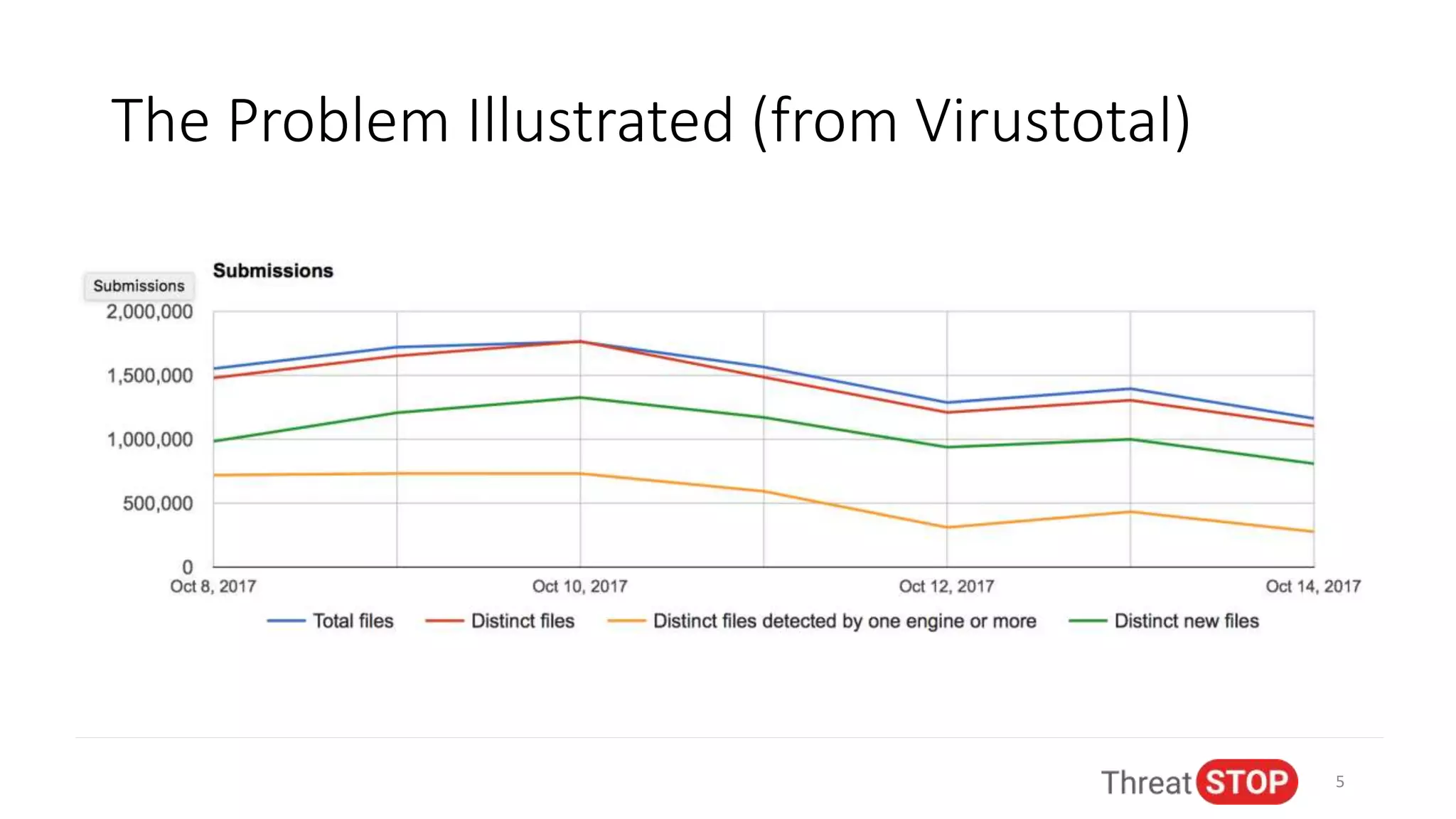
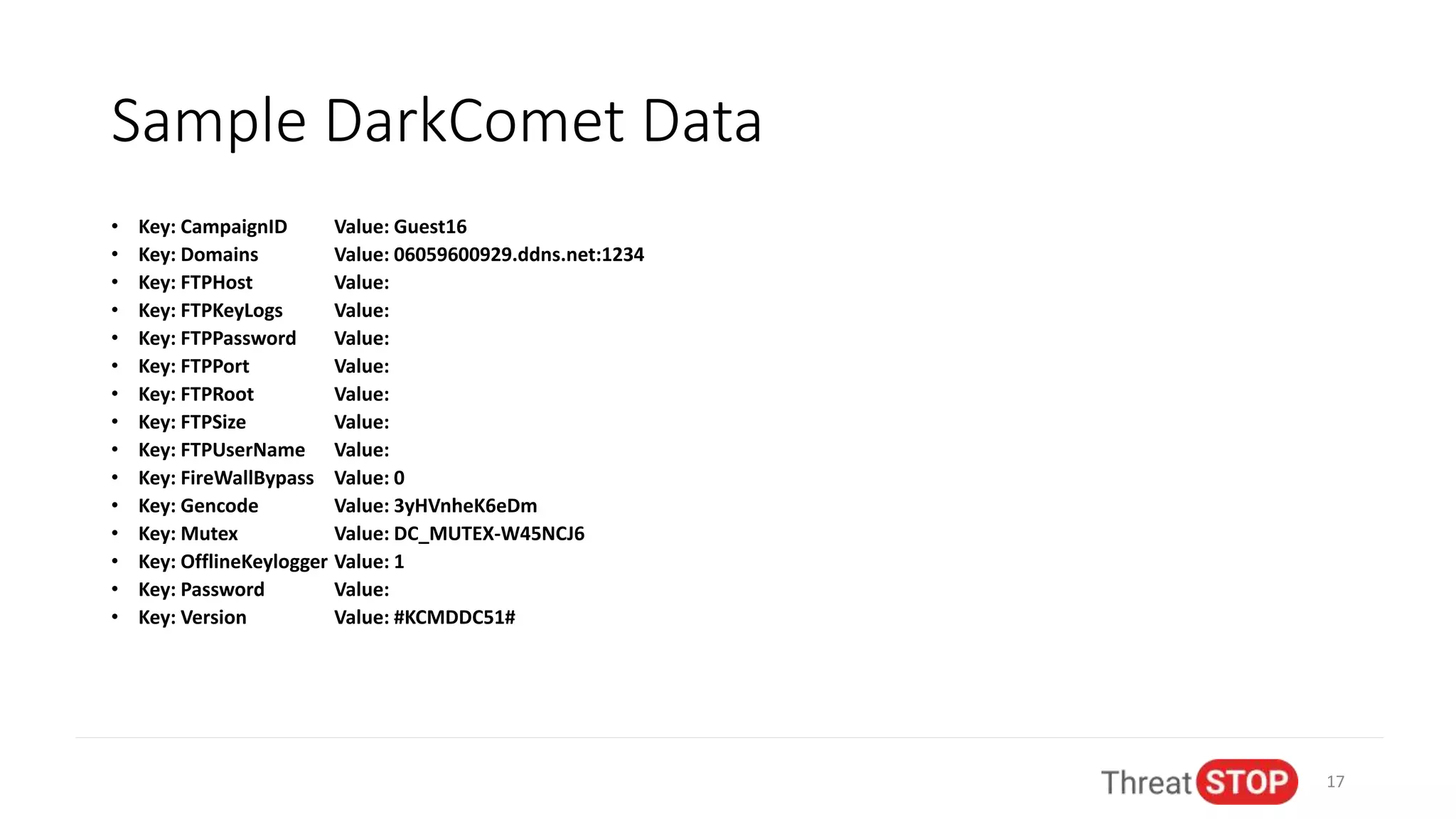
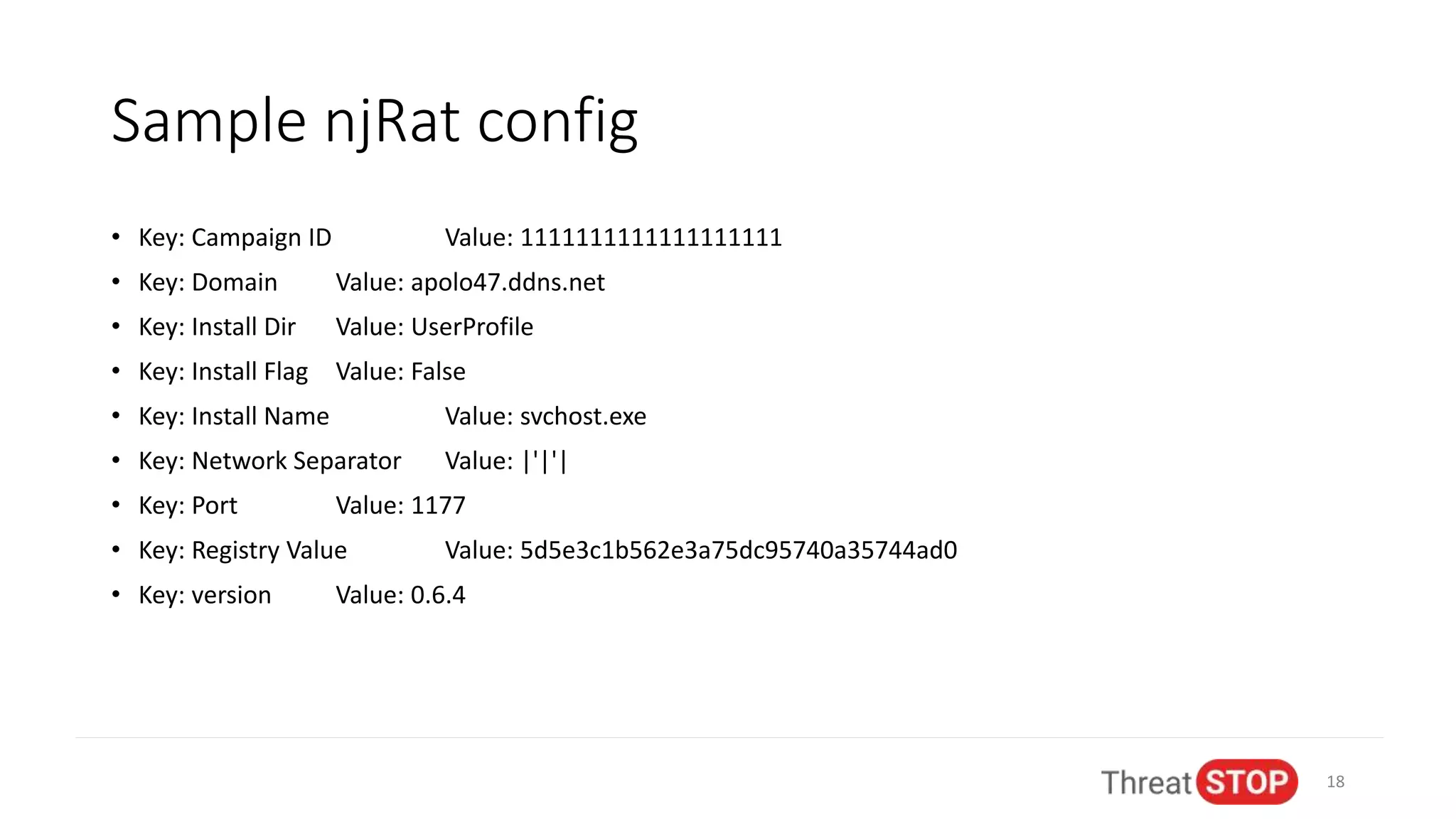
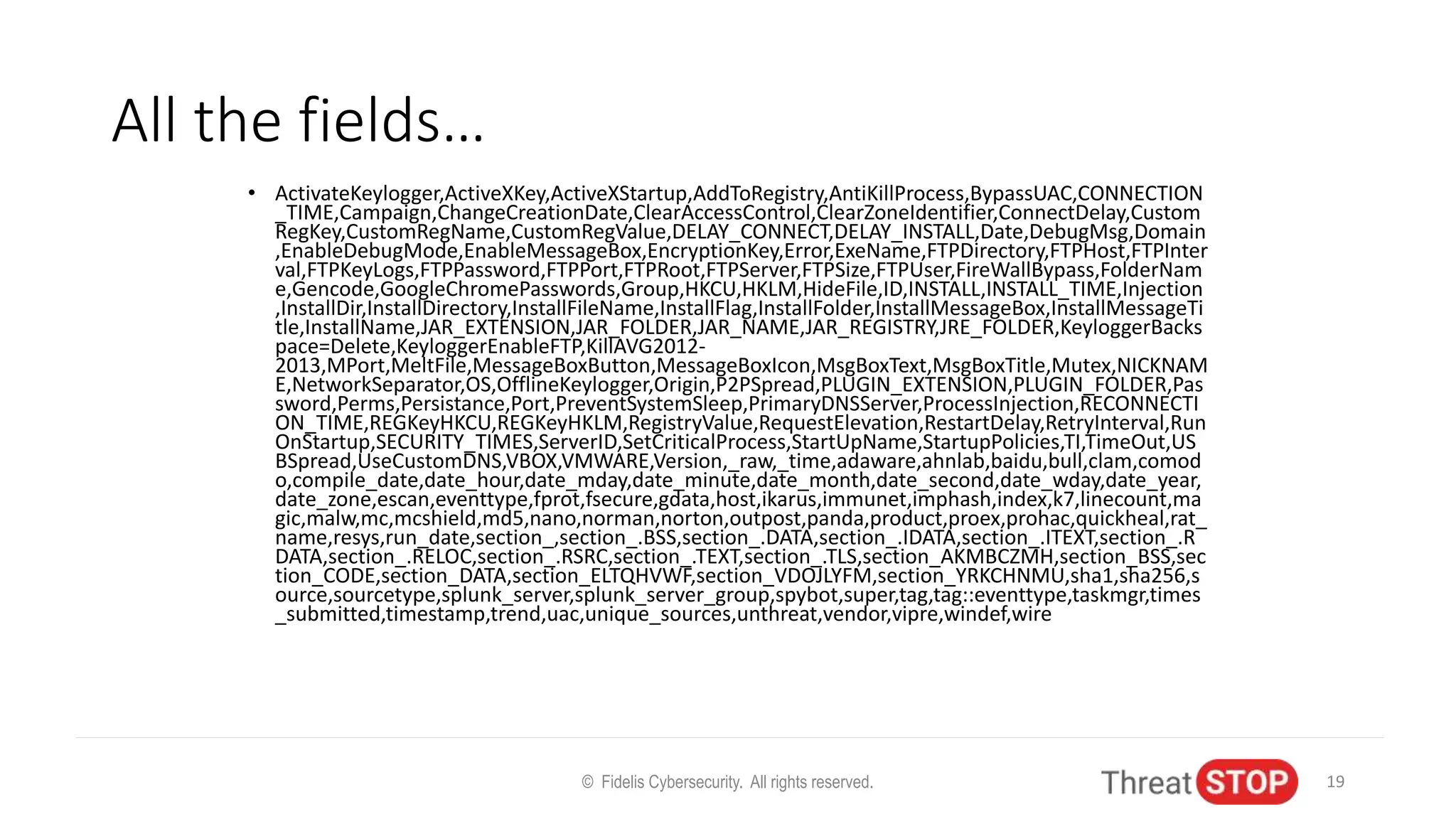
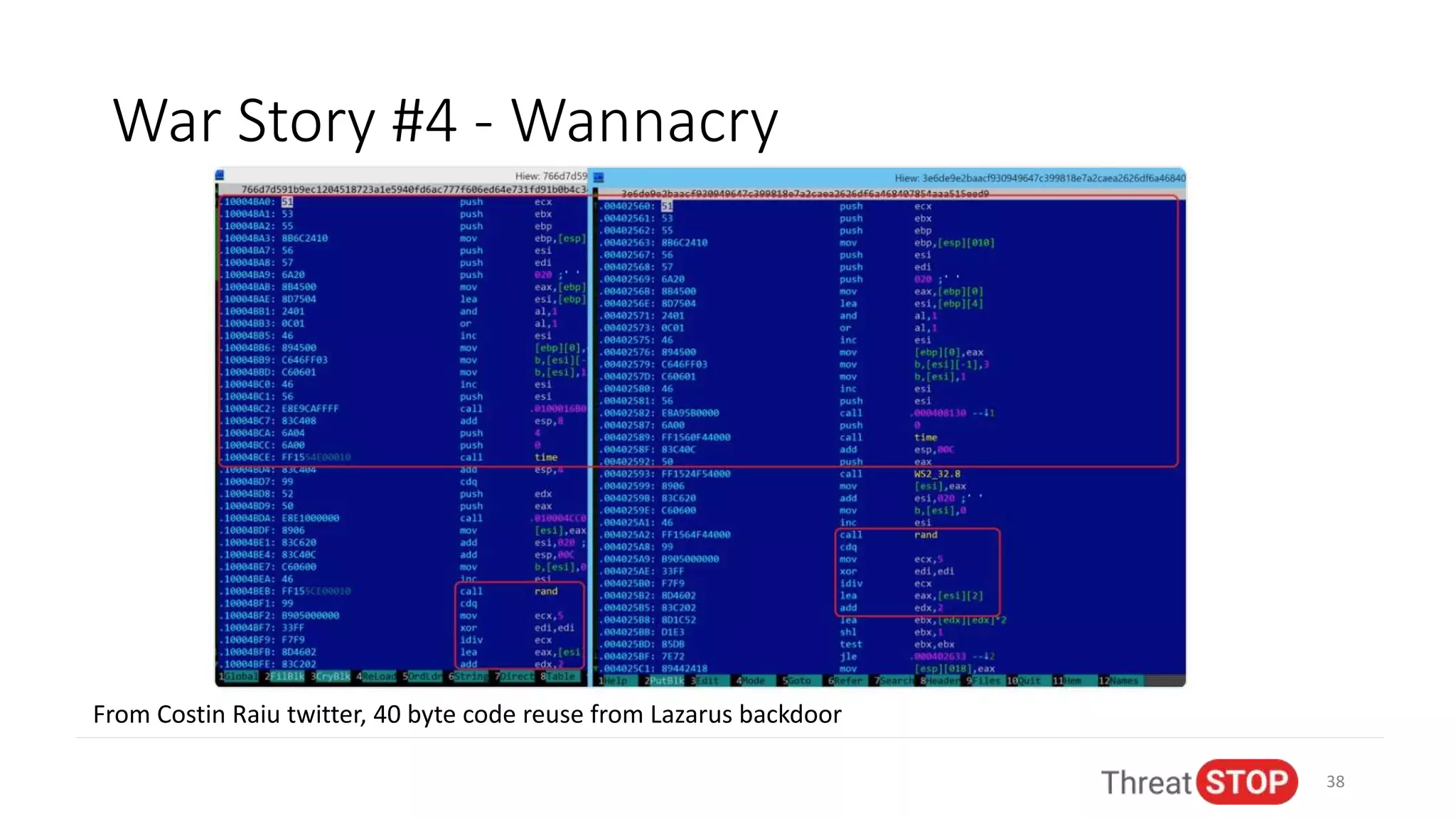
John Bambenek discusses the issues in cybersecurity including the overwhelming amount of data, unfilled job positions, and the need for effective automated threat intelligence. He shares experiences from significant cybersecurity incidents like election hacking and ransomware attacks, emphasizing the importance of proactive data sharing and analysis to mitigate threats. The presentation advocates for collaboration in the cybersecurity community to improve defenses and respond to emerging threats.