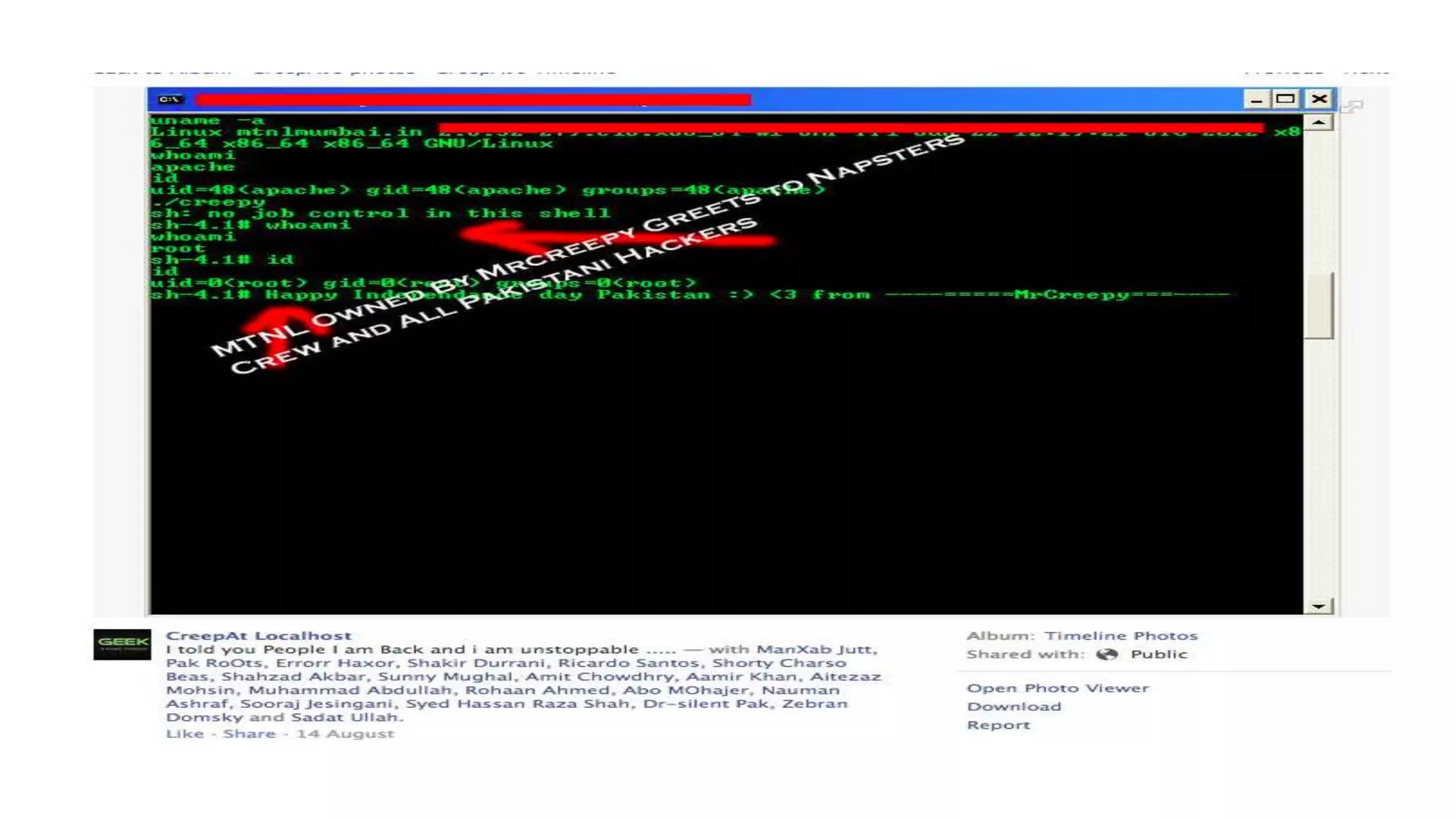
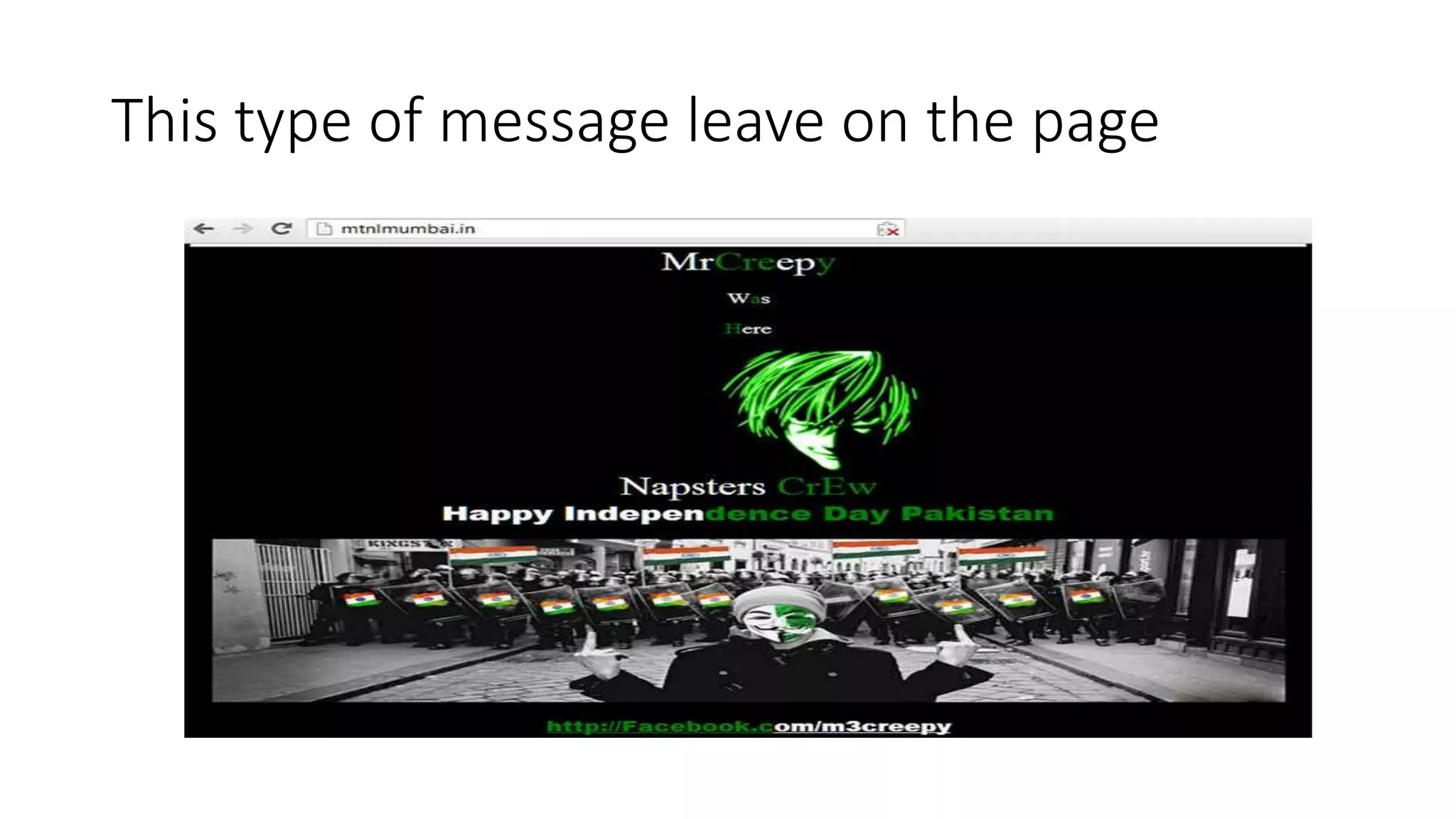
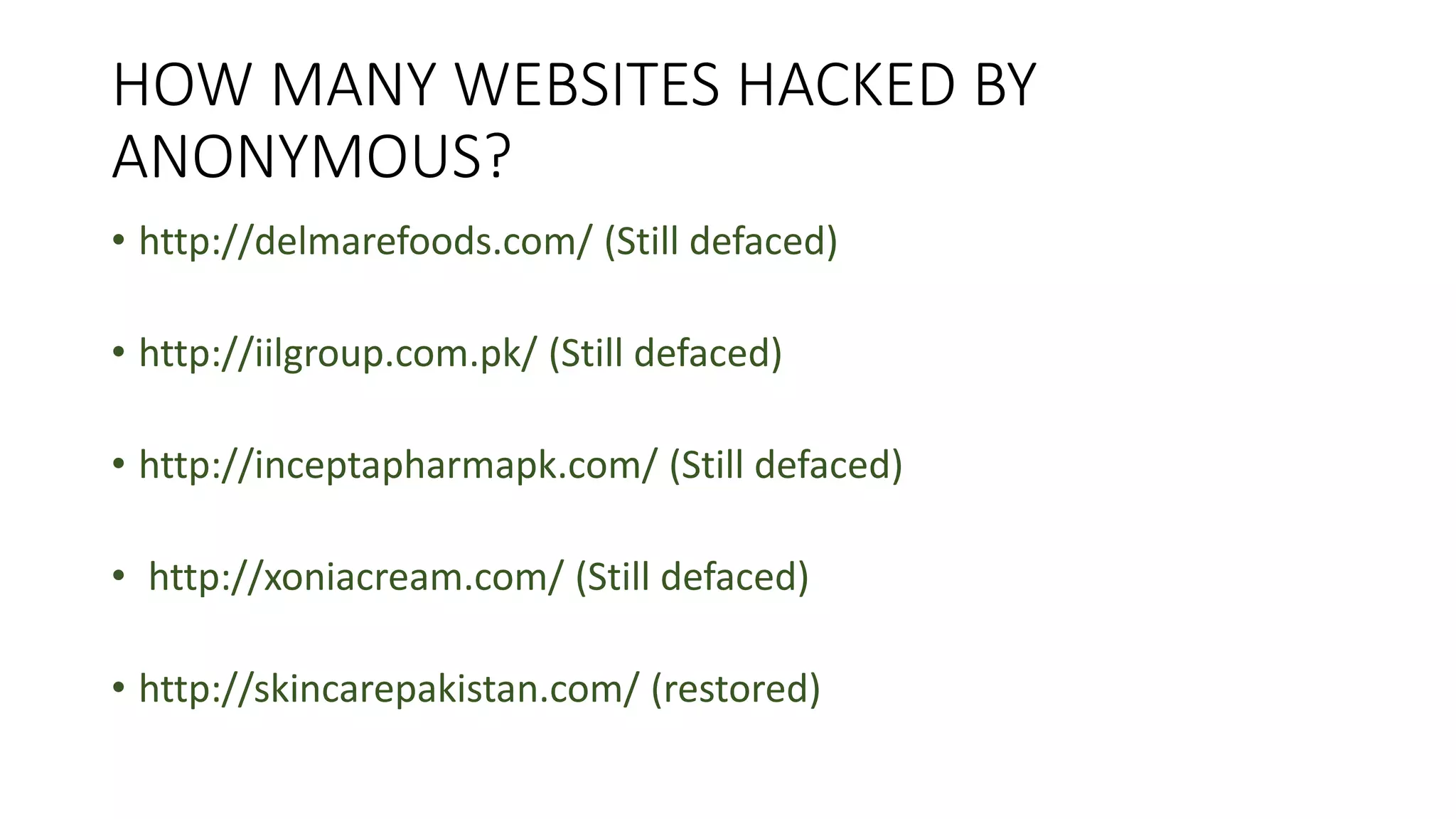
The document discusses the hacking of the Mahanagar Telecom Nigam Limited (MTNL) website on August 14, 2013, by the hacker group 'Anonymous' through a distributed denial of service (DDoS) attack, which overwhelmed the site with traffic from multiple sources, making it inaccessible. The attack was executed using a remotely administered trojan (RAT) that allowed the hacker to gain control over the MTNL systems through a malicious link, compromising user data. Recommendations for preventing such attacks include immediate site shutdown, enhancing security measures, using HTTPS, and regularly updating passwords.