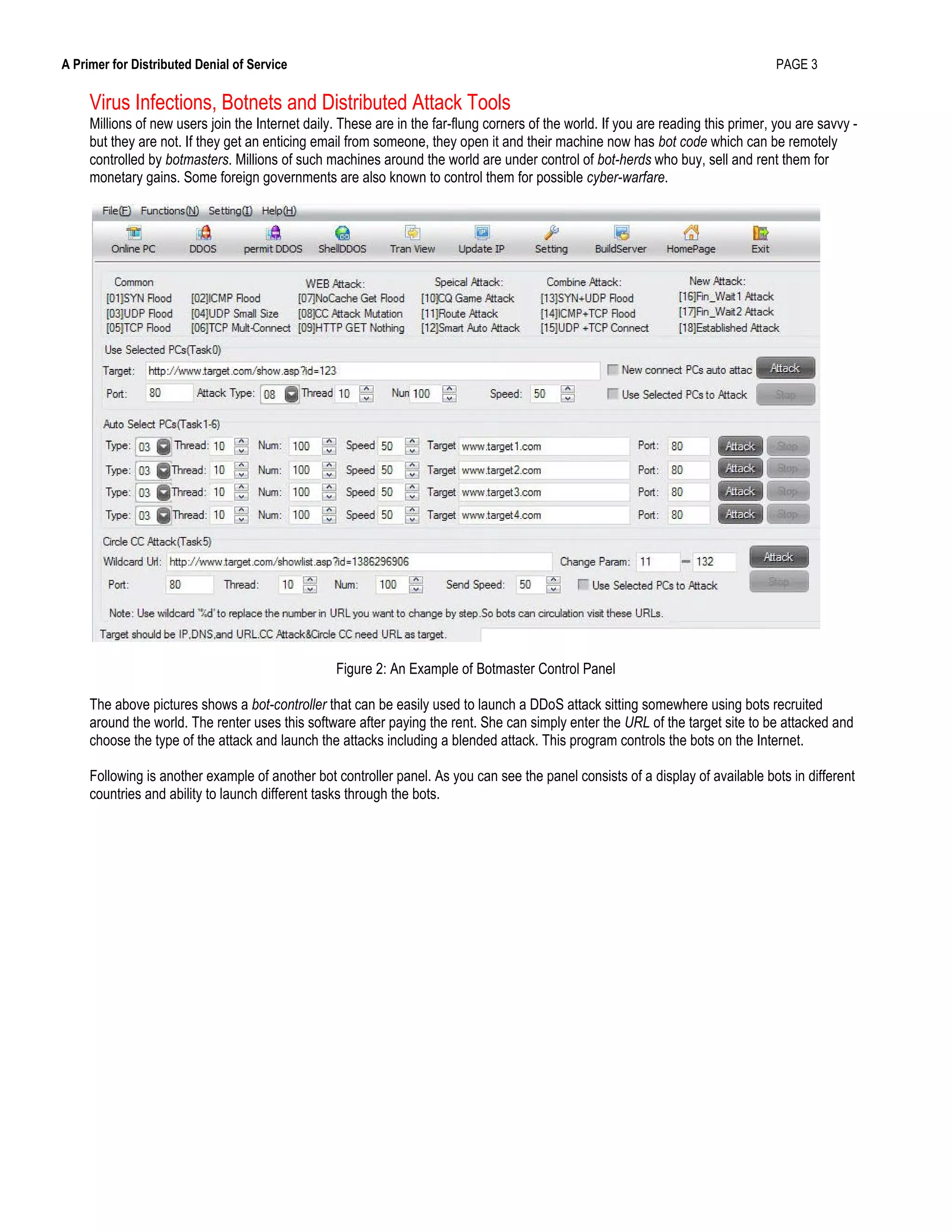
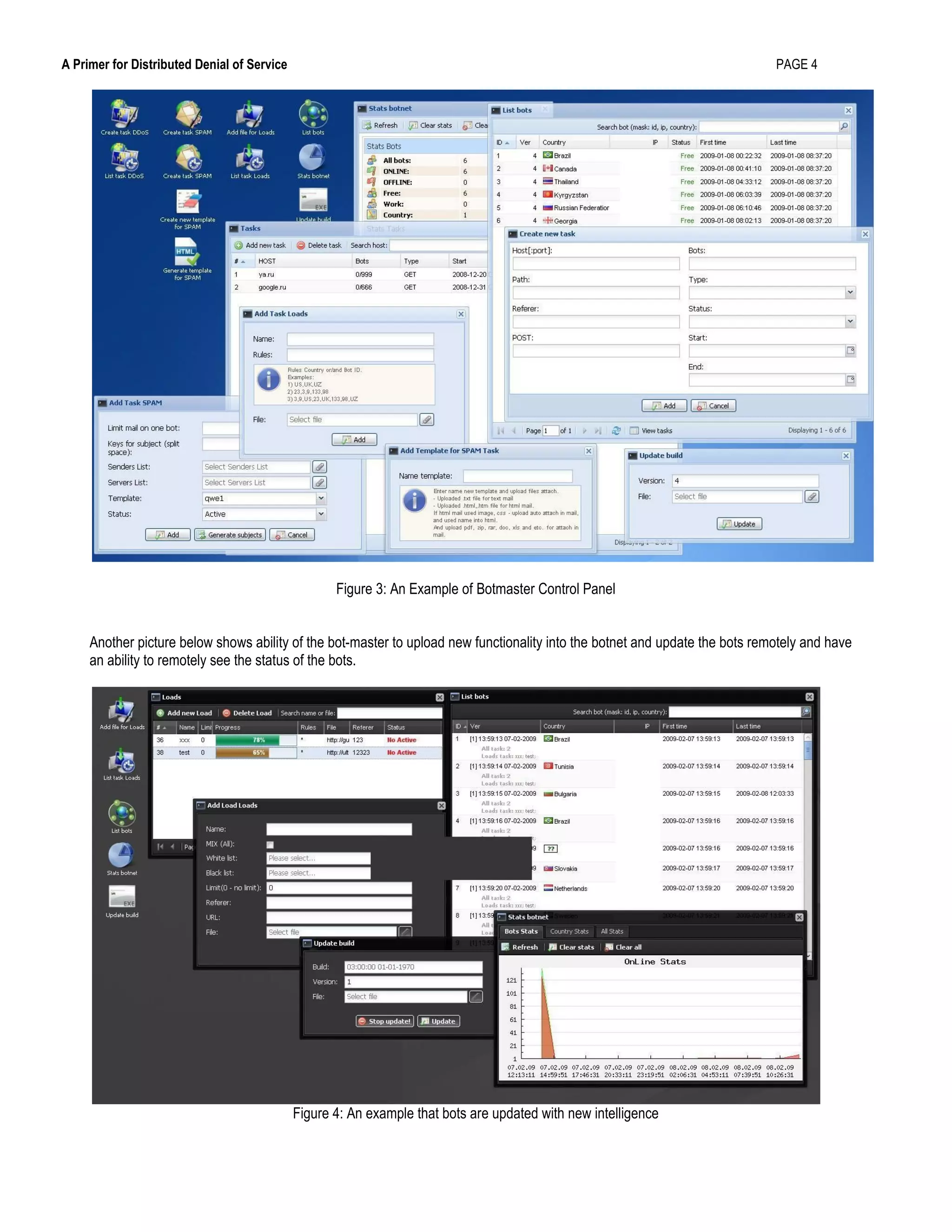
This document provides an overview of distributed denial of service (DDoS) attacks, including how they work, common techniques used, and strategies for mitigating them. It defines DDoS attacks as attempts to exhaust the resources of networks, applications, or services to deny access to legitimate users. The document discusses how botnets are commonly used to launch large-scale DDoS attacks from multiple sources simultaneously. It also outlines best practices for selecting DDoS protection devices, emphasizing the importance of up-to-date detection techniques, low latency, and customized hardware-based logic to withstand major attacks.