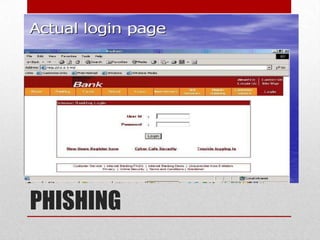
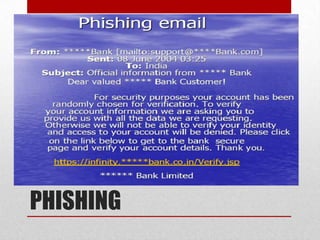
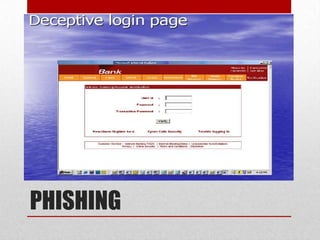
Cyber crime involves using computers or the internet to commit illegal acts. There are three main types of cyber crimes: those against individuals, like cyber harassment; those against property, such as hacking to steal data from companies; and those against government, including terrorists using the internet to plan attacks. As more financial transactions move online, cyber crimes are increasing and pose a threat to both individuals and organizations. Effective prevention requires education about cyber security risks.