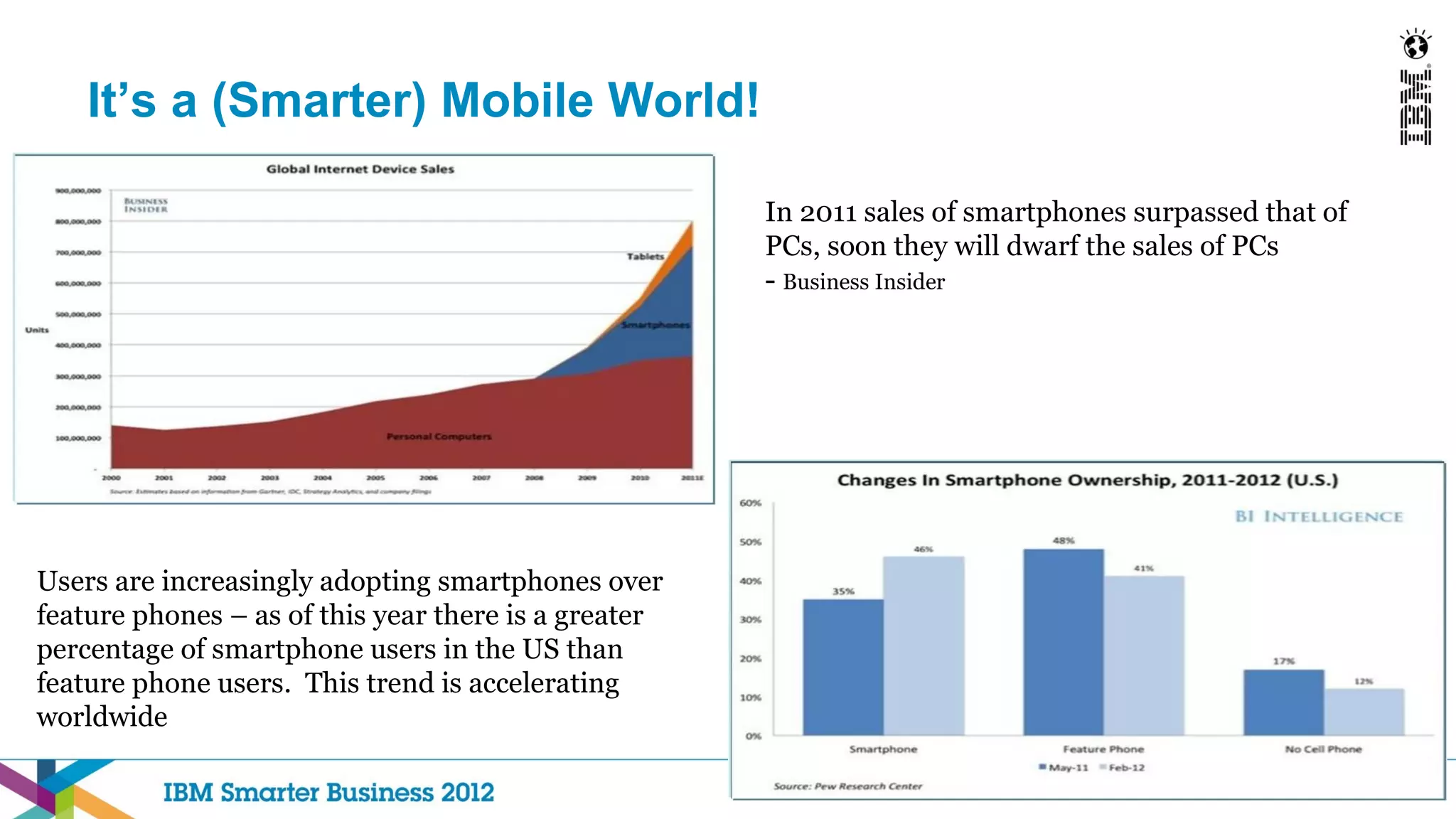
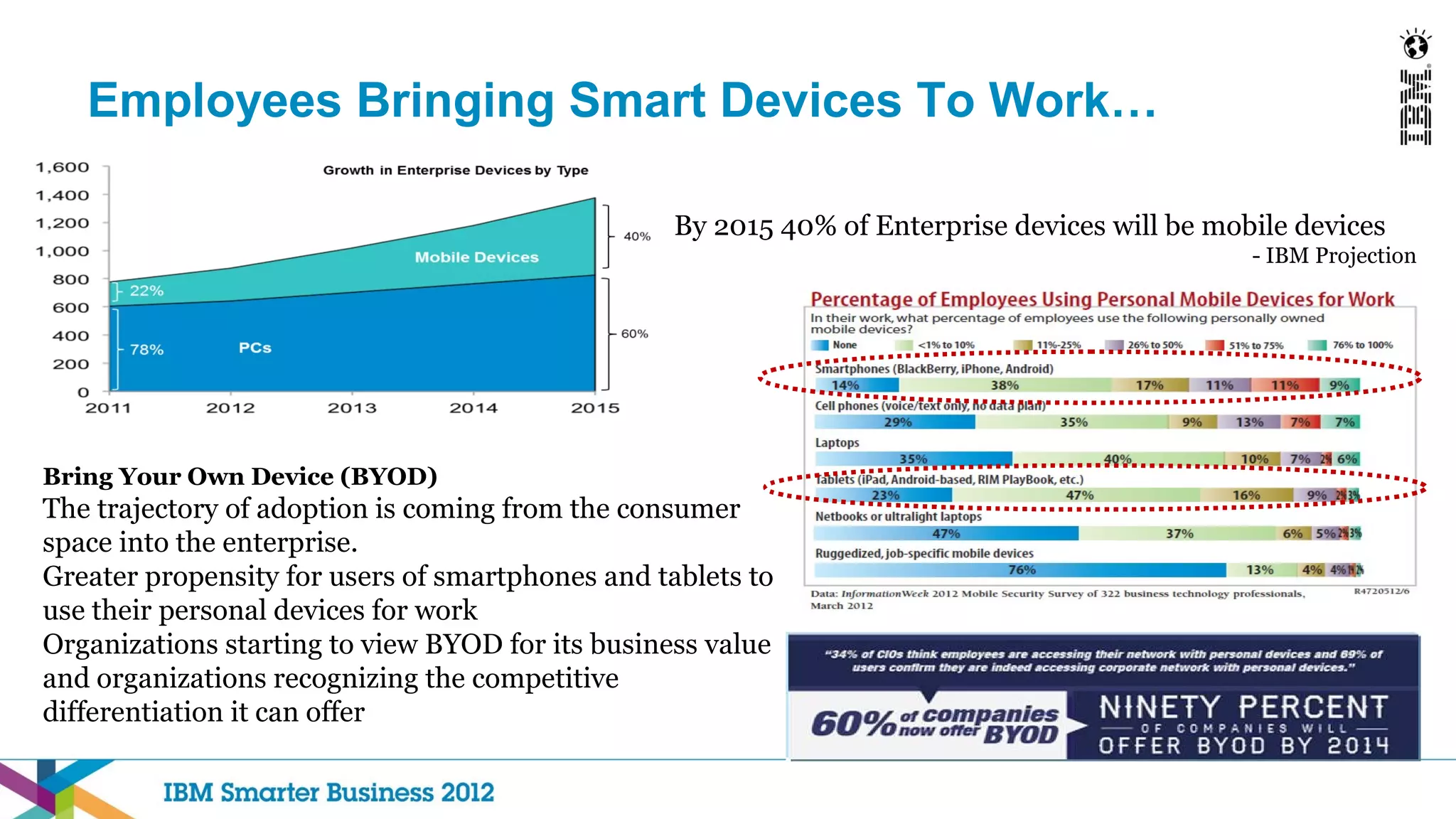
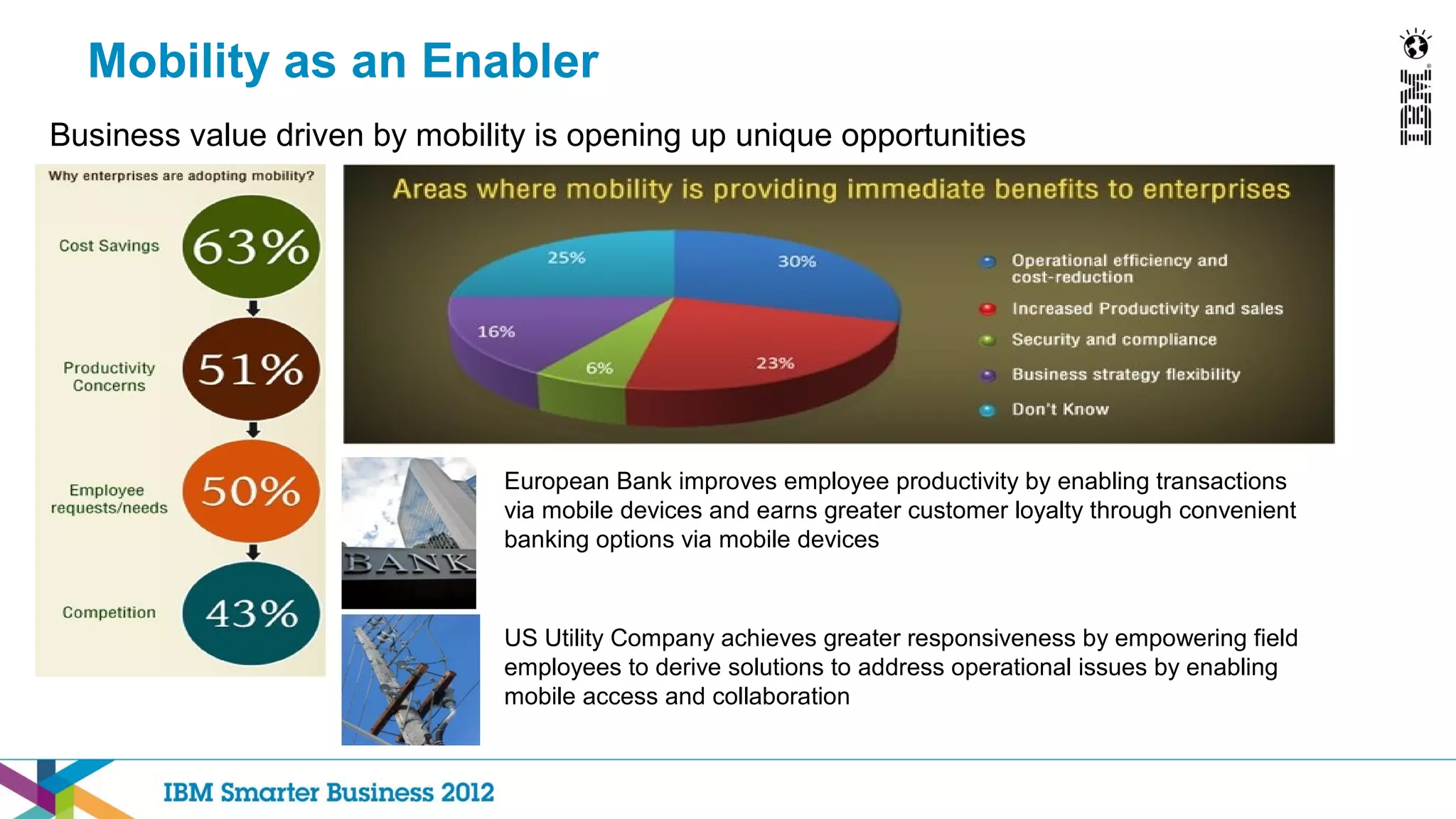
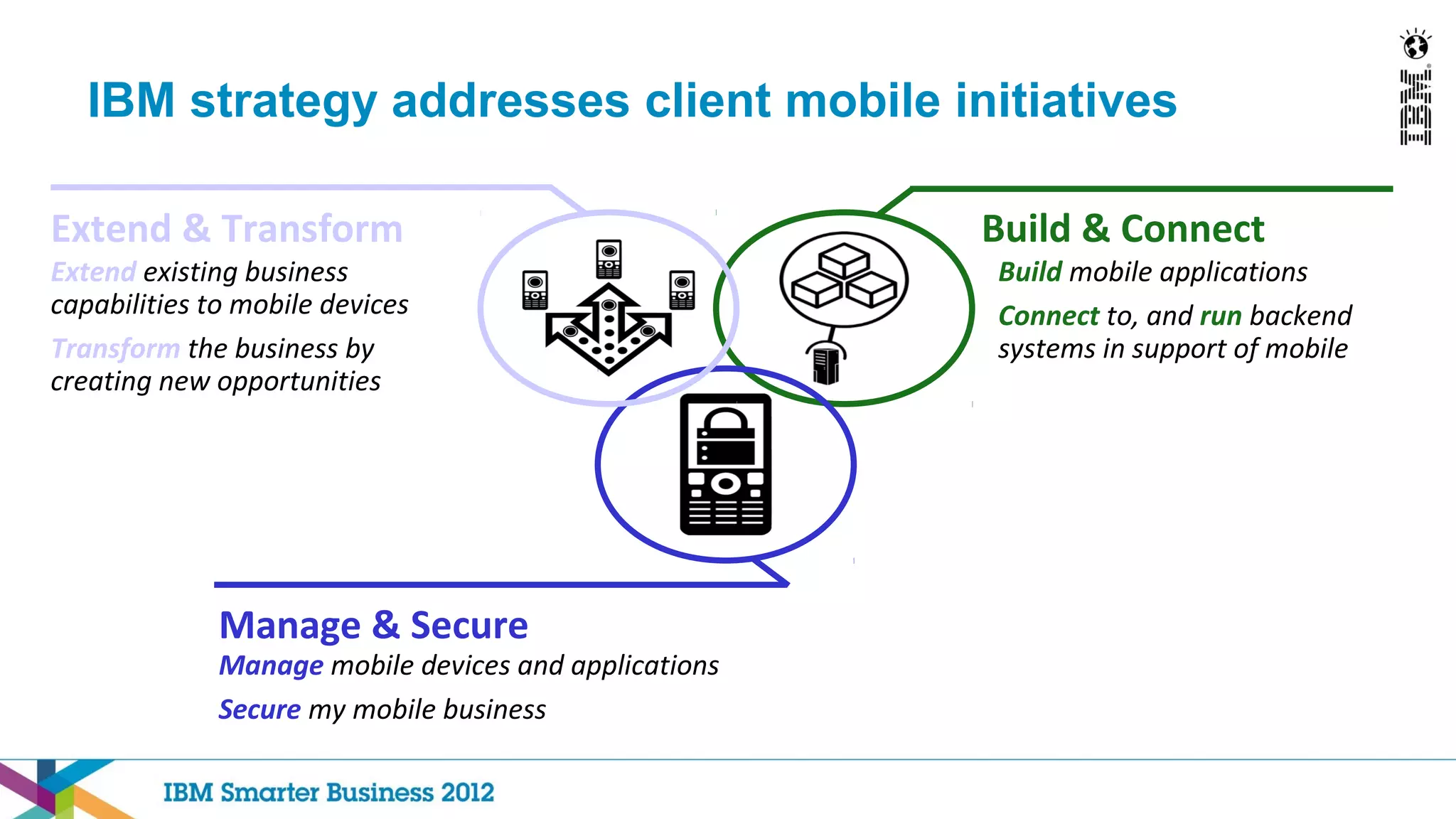
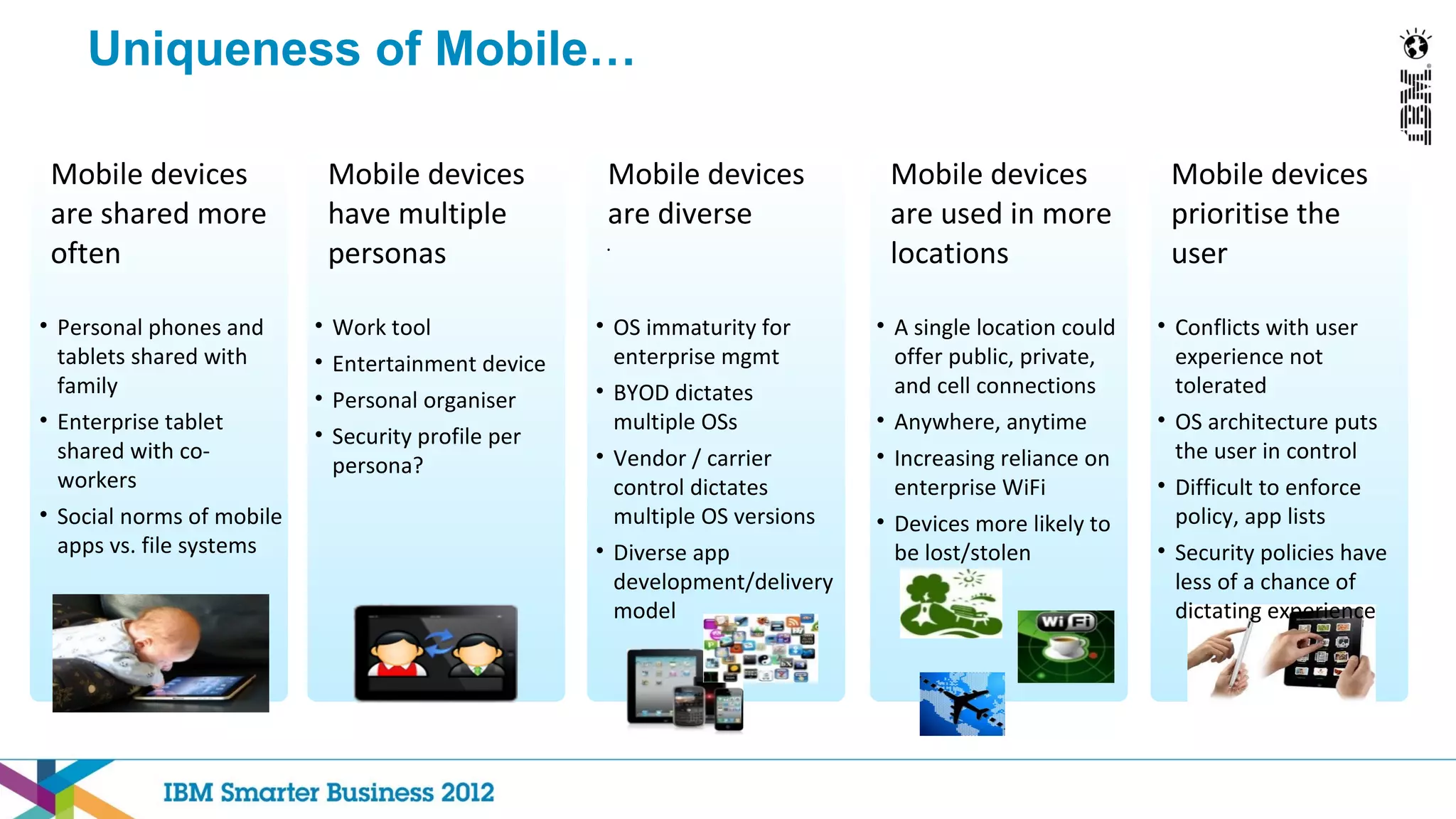
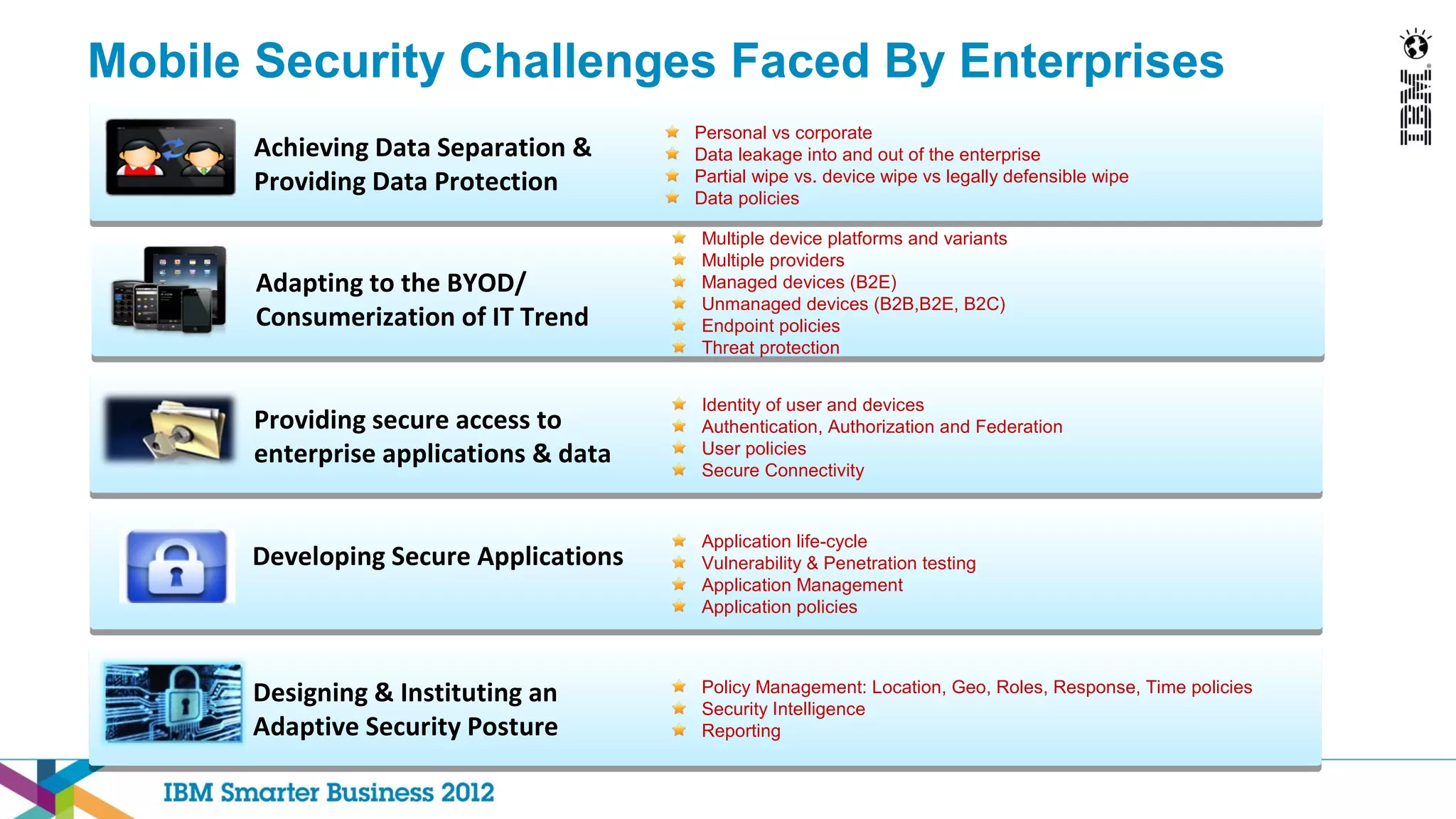
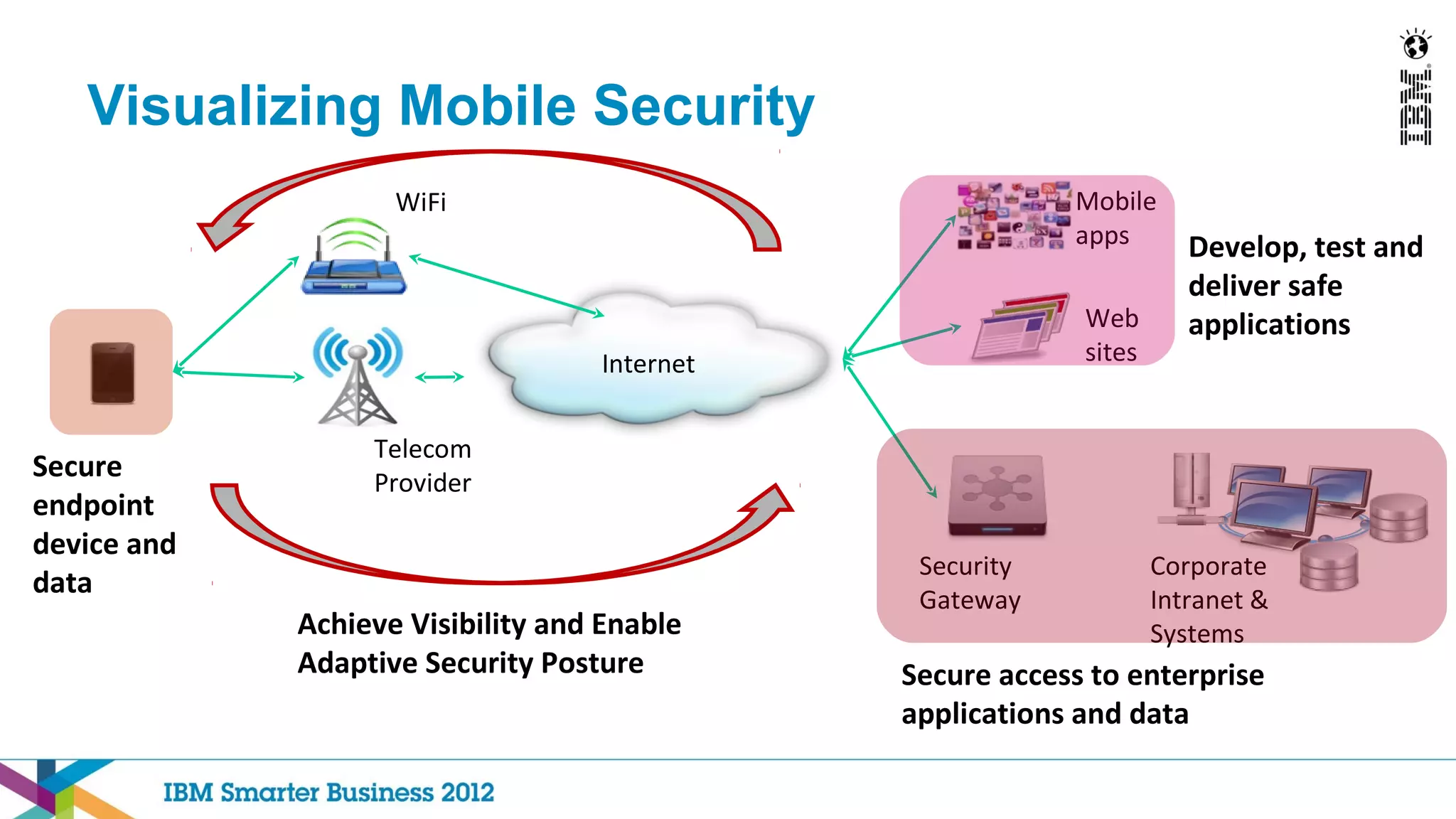
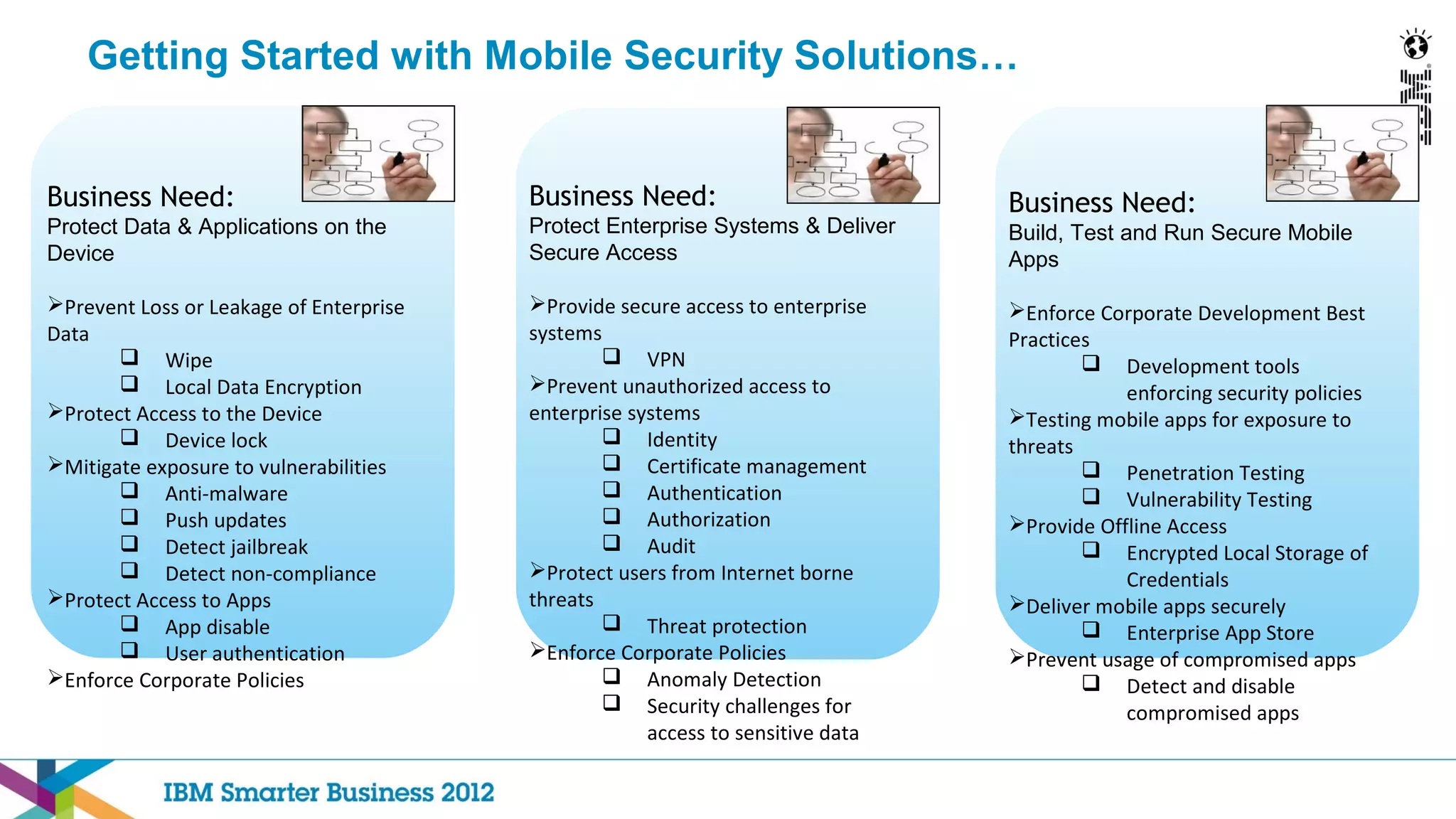
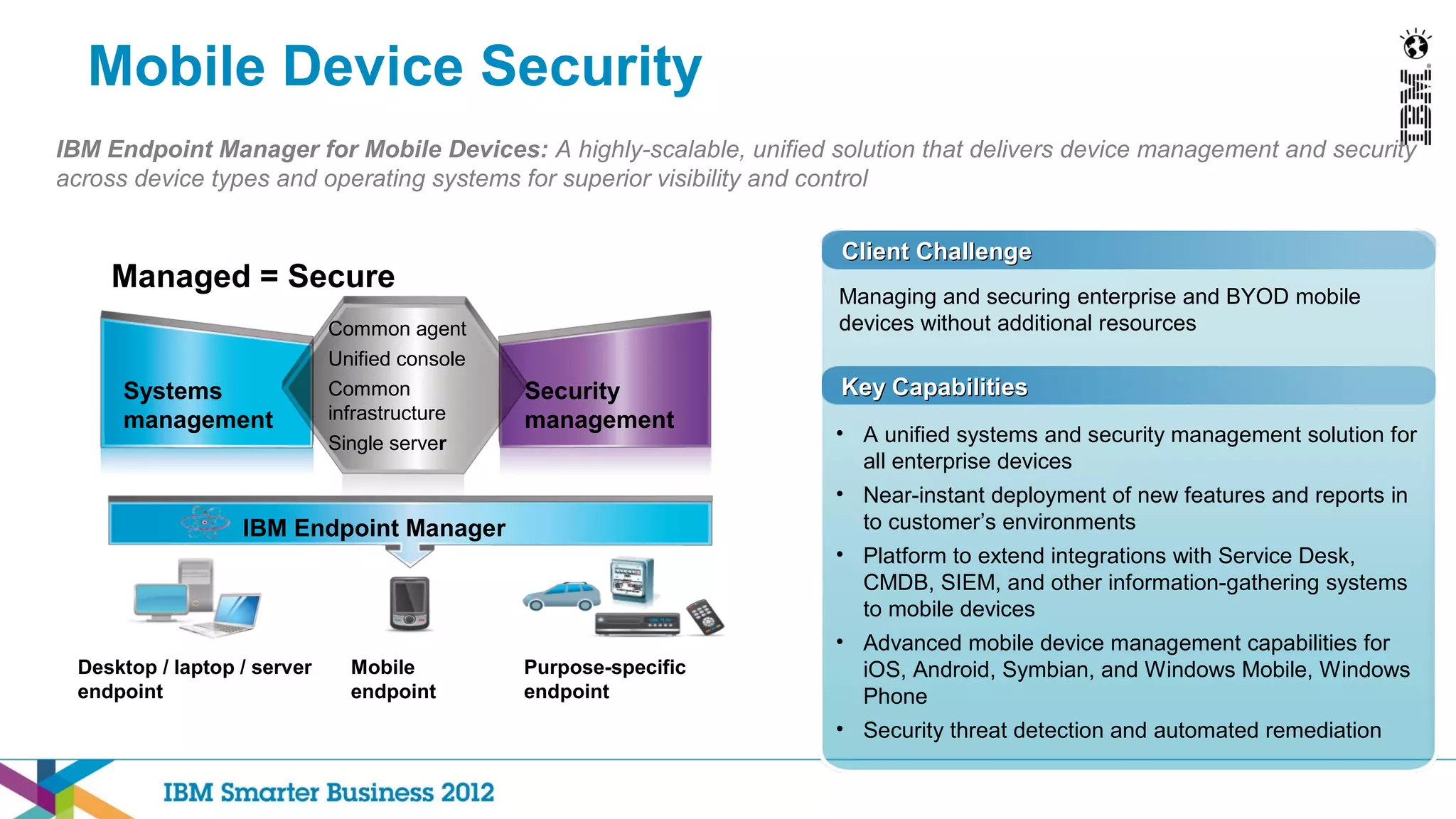
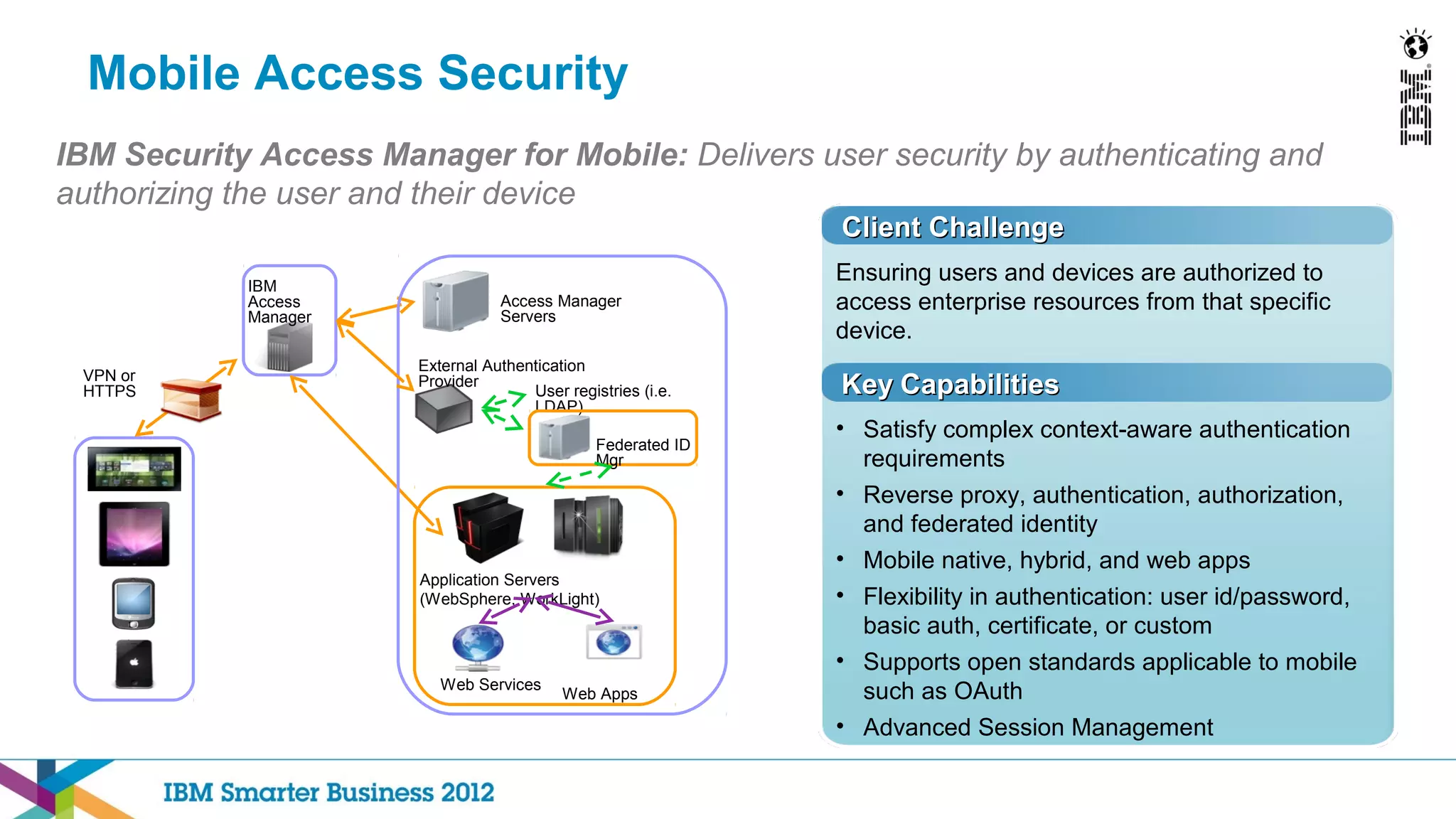
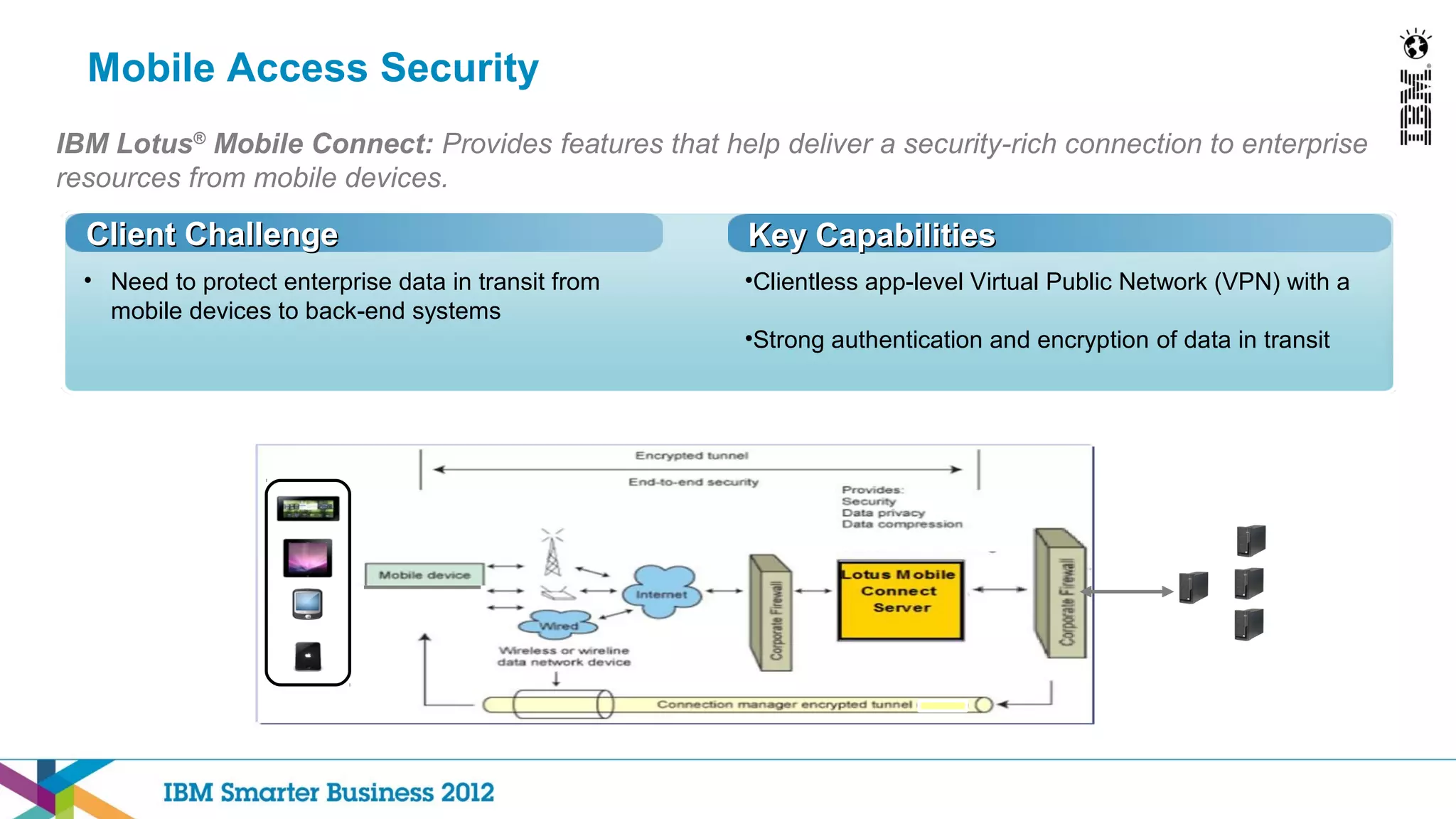
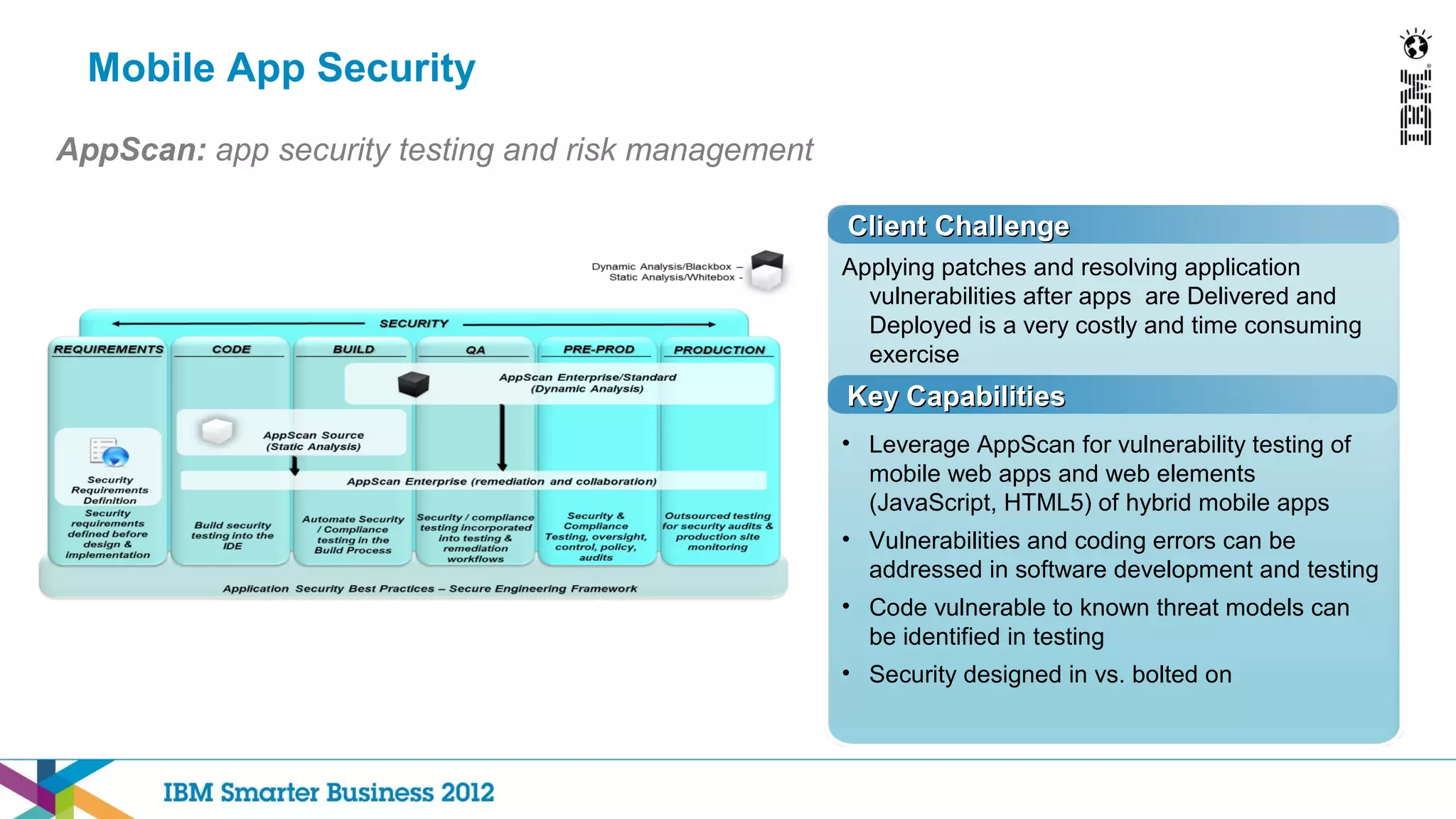
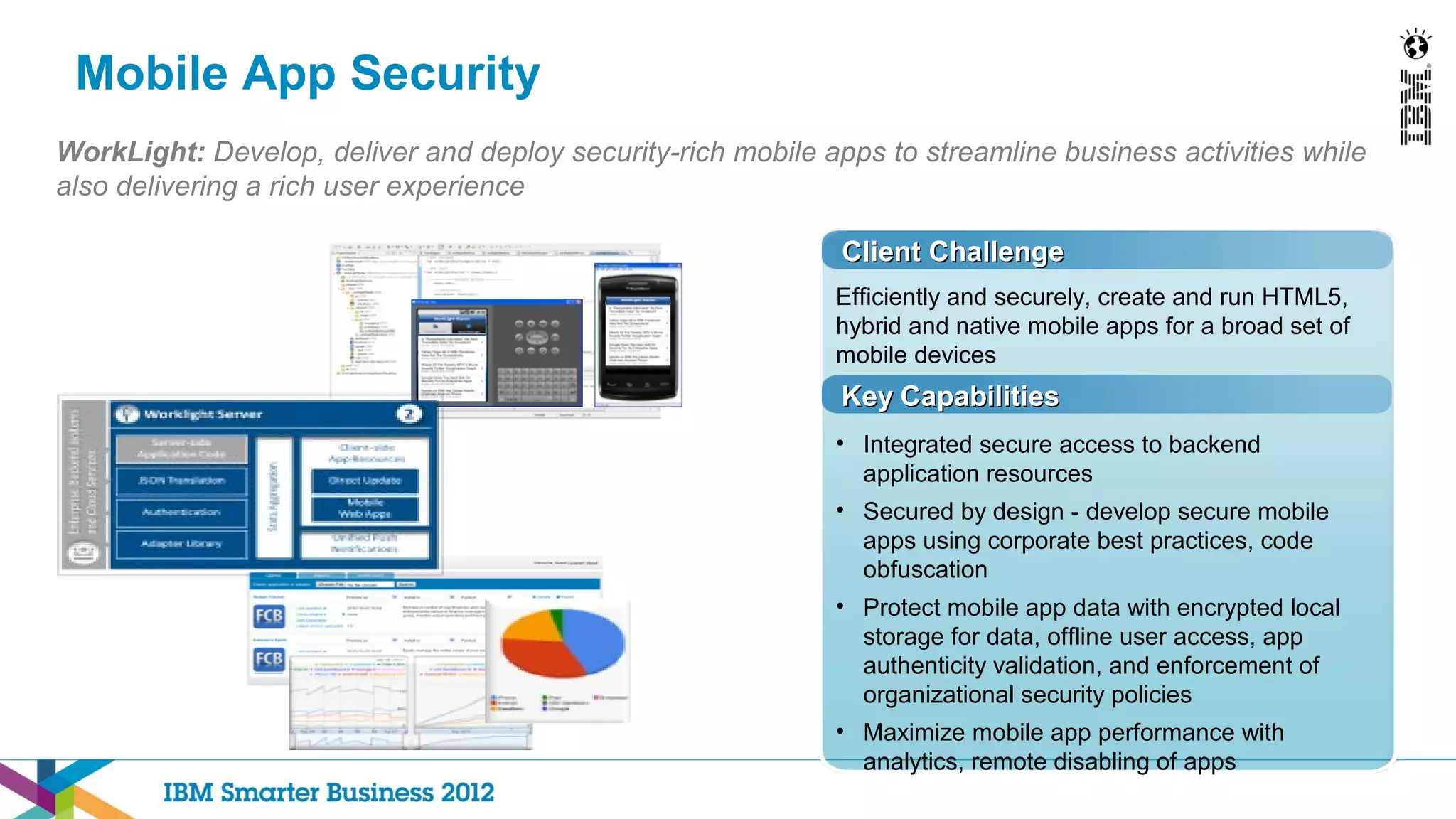
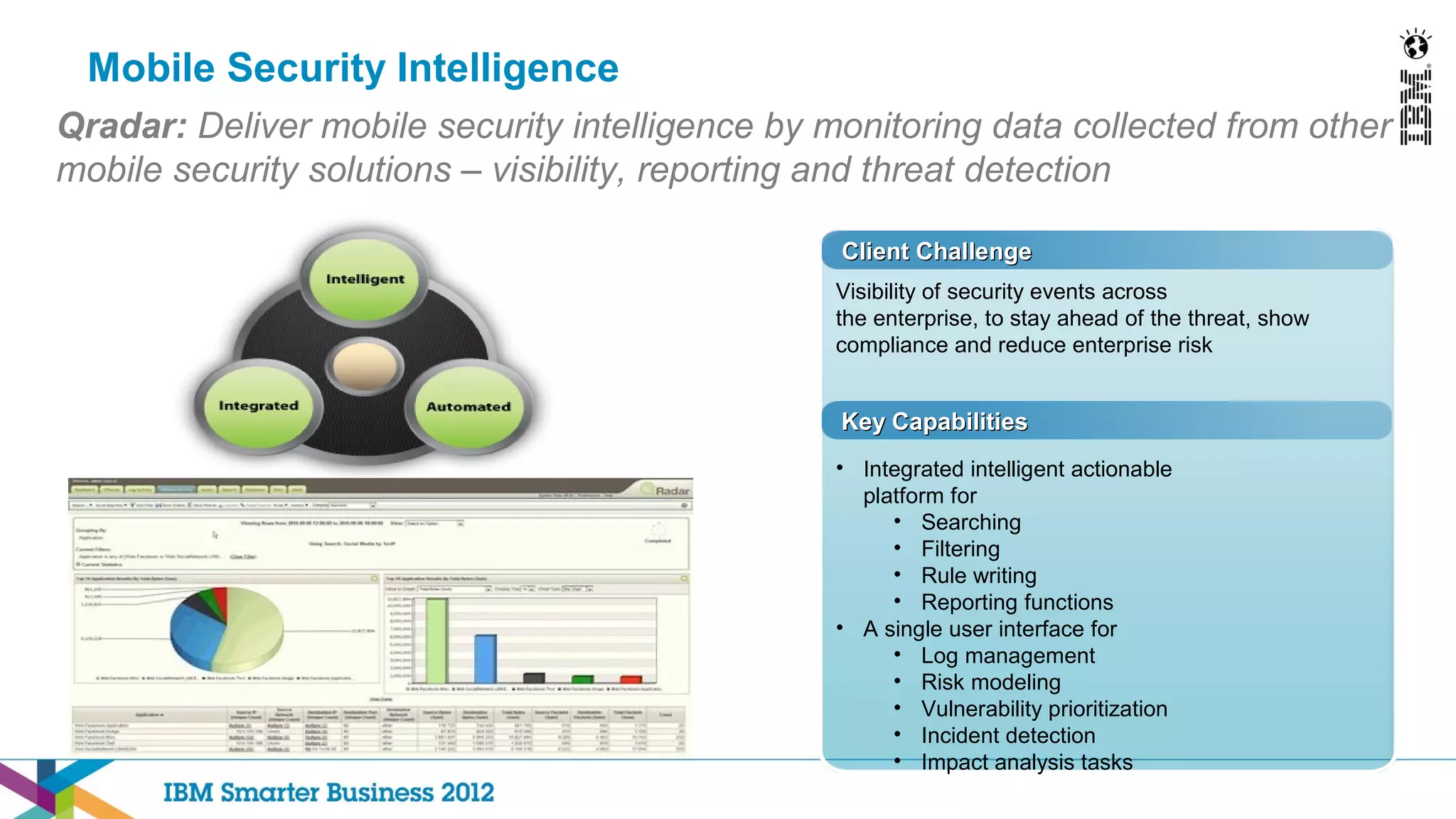
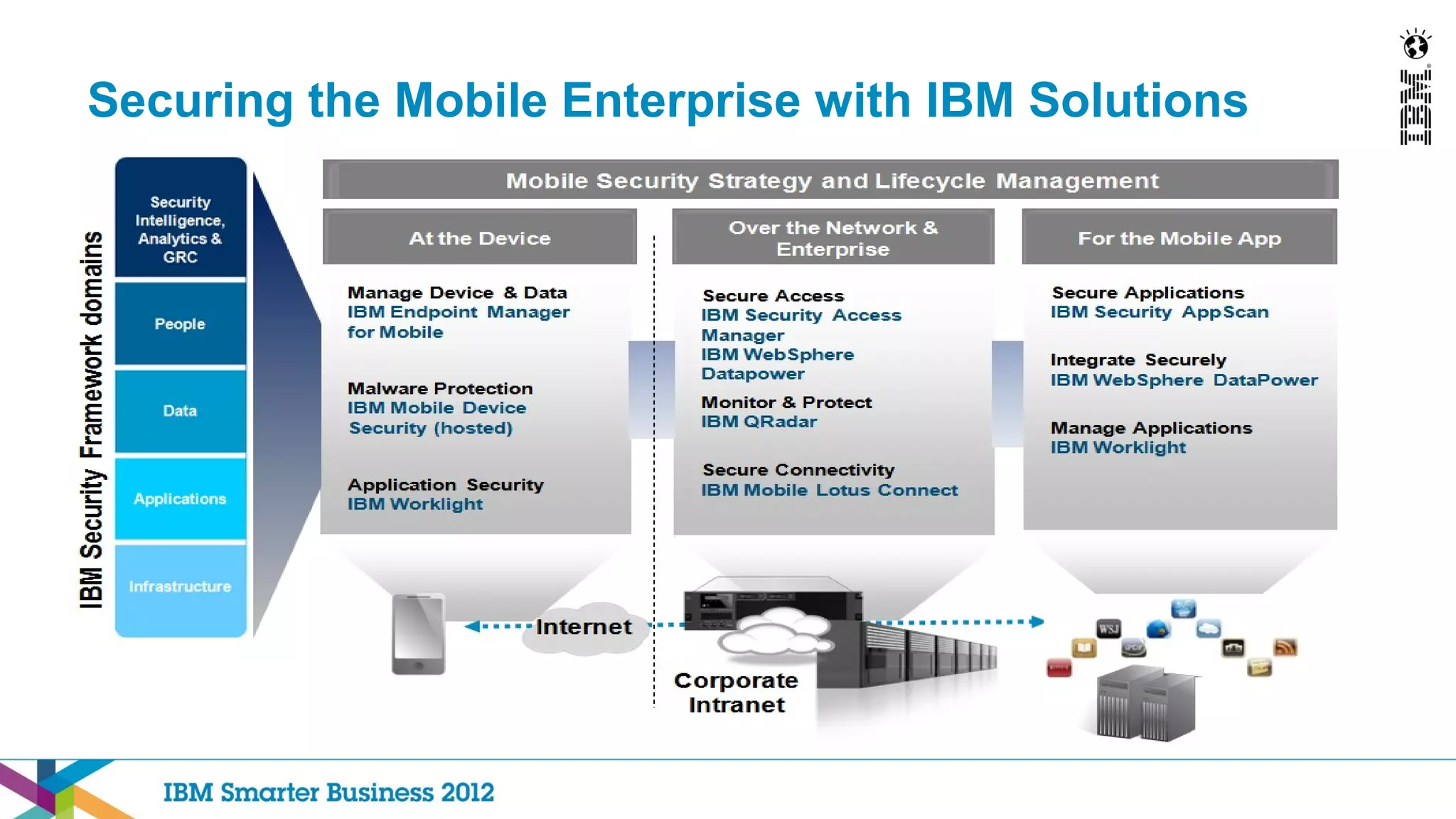
This document discusses mobility and bring your own device (BYOD) trends in the enterprise. It highlights how mobile device adoption is accelerating and how employees are increasingly using personal smartphones and tablets for work. The document outlines some of the business benefits of mobility but also discusses the unique security challenges that mobile devices present for enterprises. It provides an overview of IBM's strategy and solutions for mobile management, security, and application development.