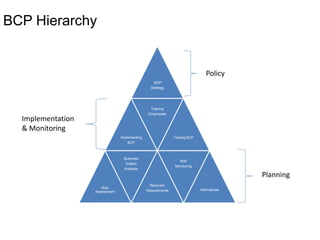
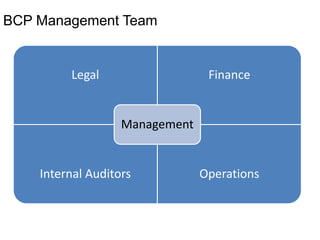
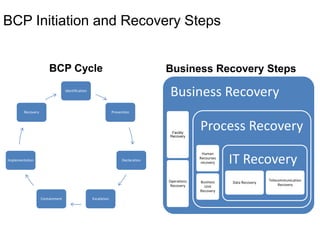
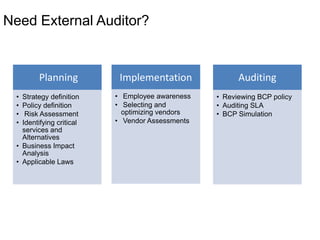
Yes, an external auditor can help validate the effectiveness of the BCP. Some key reasons are:
- Provide an independent third-party perspective
- Ensure compliance with regulations and industry standards
- Test processes and identify gaps/areas for improvement
- Verify ability to execute the plan effectively in a disaster scenario
So in summary, an external audit is recommended as part of the BCP management process to independently validate that the plan is robust, compliant and operationally effective.