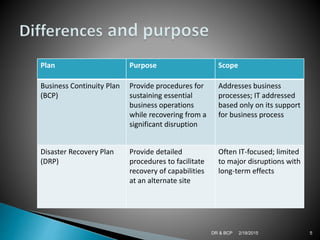
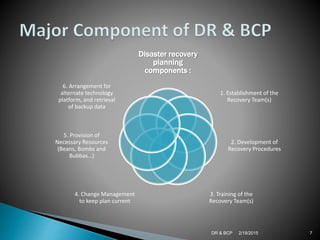
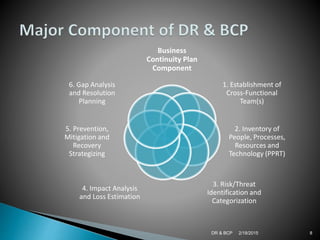
Disaster recovery (DR) and business continuity planning (BCP) are important for organizations to plan for disasters and disruptions. A DR plan provides procedures to recover IT capabilities at an alternate site after a disaster. A BCP addresses risks to business processes and prepares an organization to continue essential operations. Both plans aim to minimize downtime and losses. Key components of DR plans include establishing recovery teams, developing procedures, training, and arranging alternate IT resources. BCP components involve identifying critical resources, conducting risk and impact analyses, and developing prevention, mitigation and recovery strategies. Maintaining and testing plans is important to ensure preparedness for disasters.