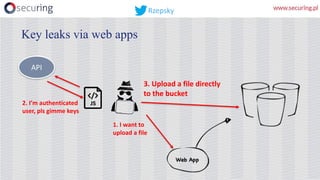
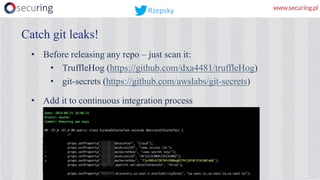
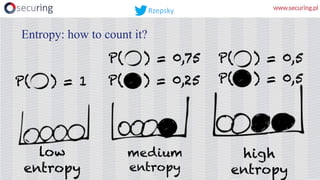
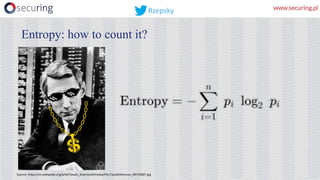
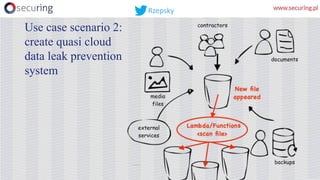
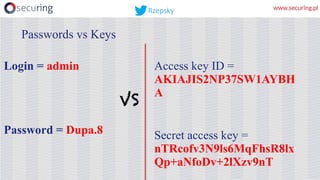
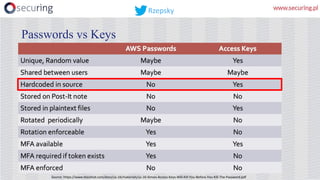
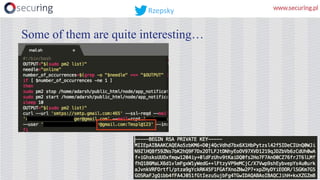
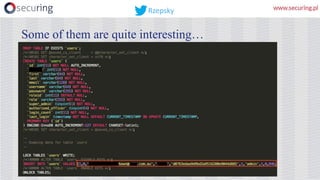
This presentation discusses how access keys can leak from cloud services like AWS, Azure, and GCP. It outlines several ways keys may leak, such as from unsecured storage containers, compromised accounts, and web applications. The presentation then demonstrates a tool called DumpsterDiver that uses entropy analysis to hunt for private keys within files. Countermeasures discussed include access control, encryption, VPN access only, multi-factor authentication, regular data verification, and penetration testing. The goal is to show how keys can leak and discuss reliable prevention strategies.



![https://[bucketname].s3.amazonaws.com
https://[aws_endpoint].amazonaws.com/[bucket_name]/
For example: https://chicagodb.s3.amazonaws.com/
Source: https://www.upguard.com/breaches/cloud-leak-chicago-voters
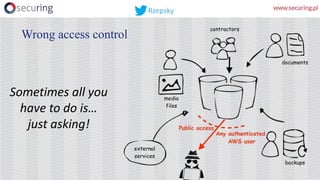
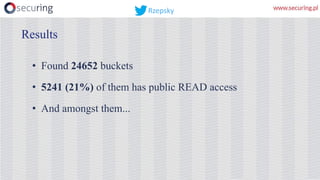
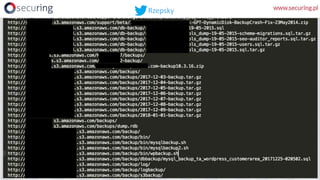
Let’s find open buckets
Rzepsky](https://image.slidesharecdn.com/huntingforthesecretsinacloudforestreduced-180607083612/85/Hunting-for-the-secrets-in-a-cloud-forest-11-320.jpg)
![• There is no groups like “Any authenticated Azure user” (thanks Microsoft!)
• You have to discover 2 variables instead of 1 (consider only Full public read access):
http://[storage account name].blob.core.windows.net/[container
name]?restype=container&comp=list
What about Azure?
Rzepsky](https://image.slidesharecdn.com/huntingforthesecretsinacloudforestreduced-180607083612/85/Hunting-for-the-secrets-in-a-cloud-forest-18-320.jpg)