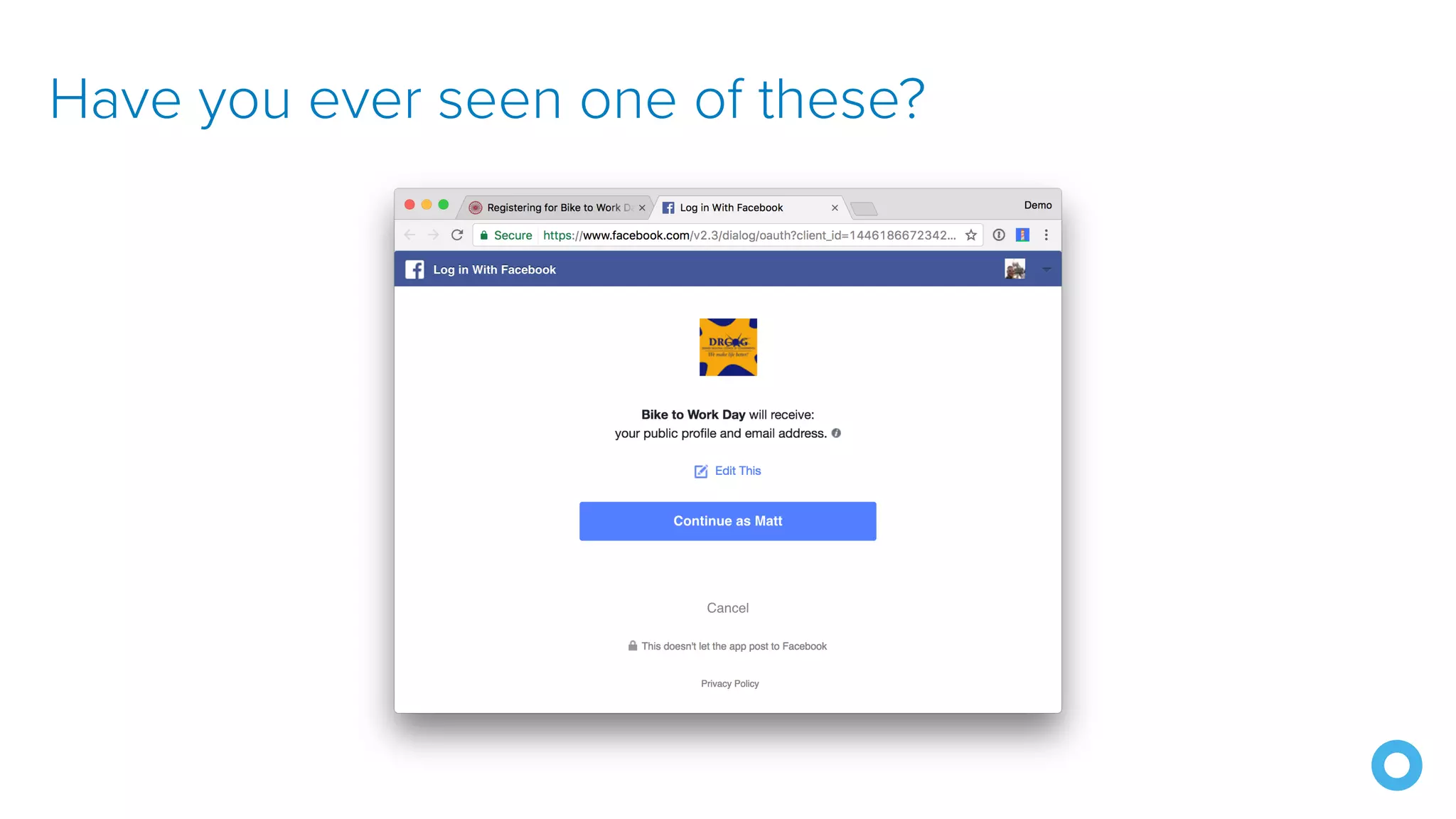
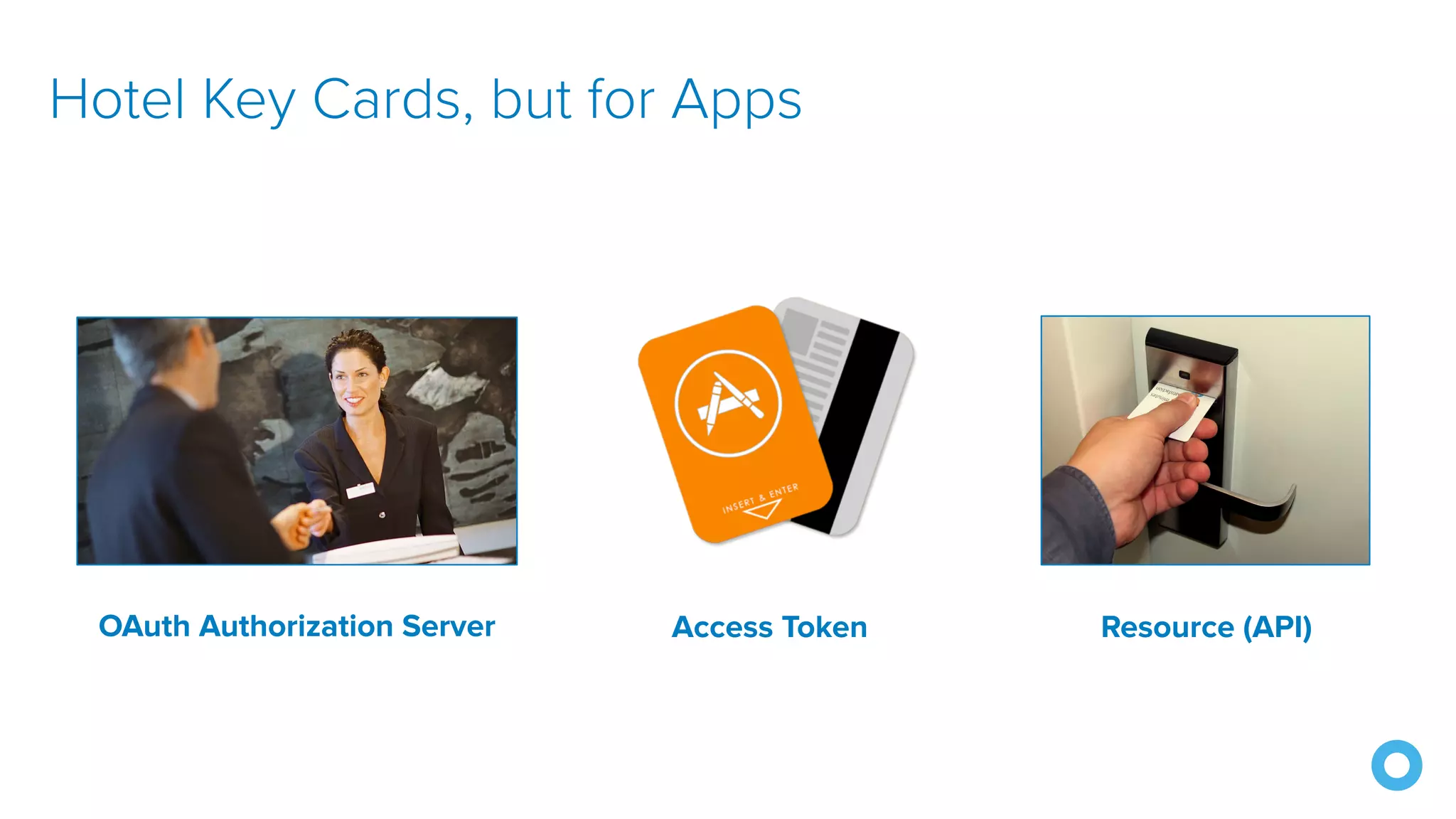
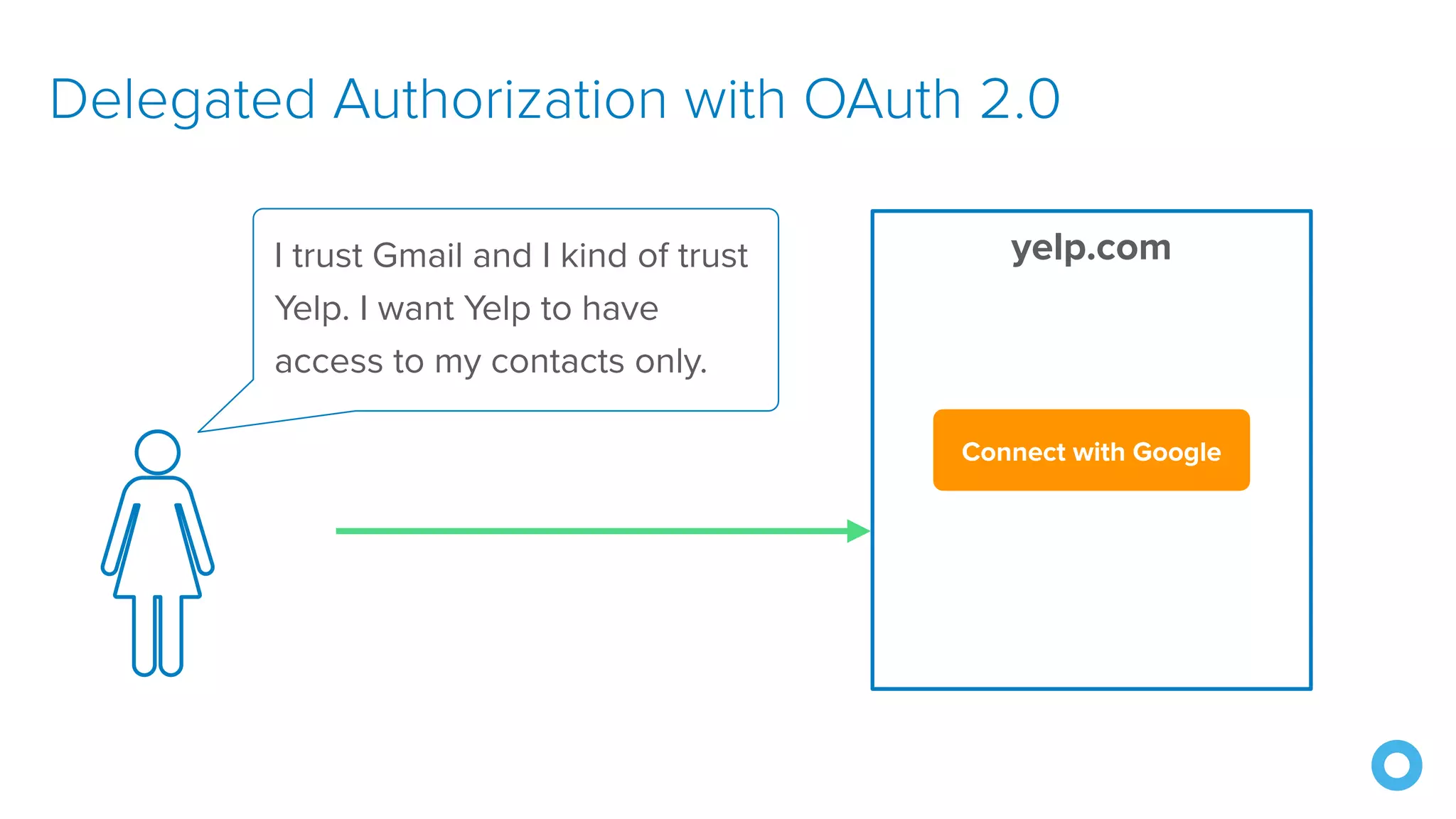
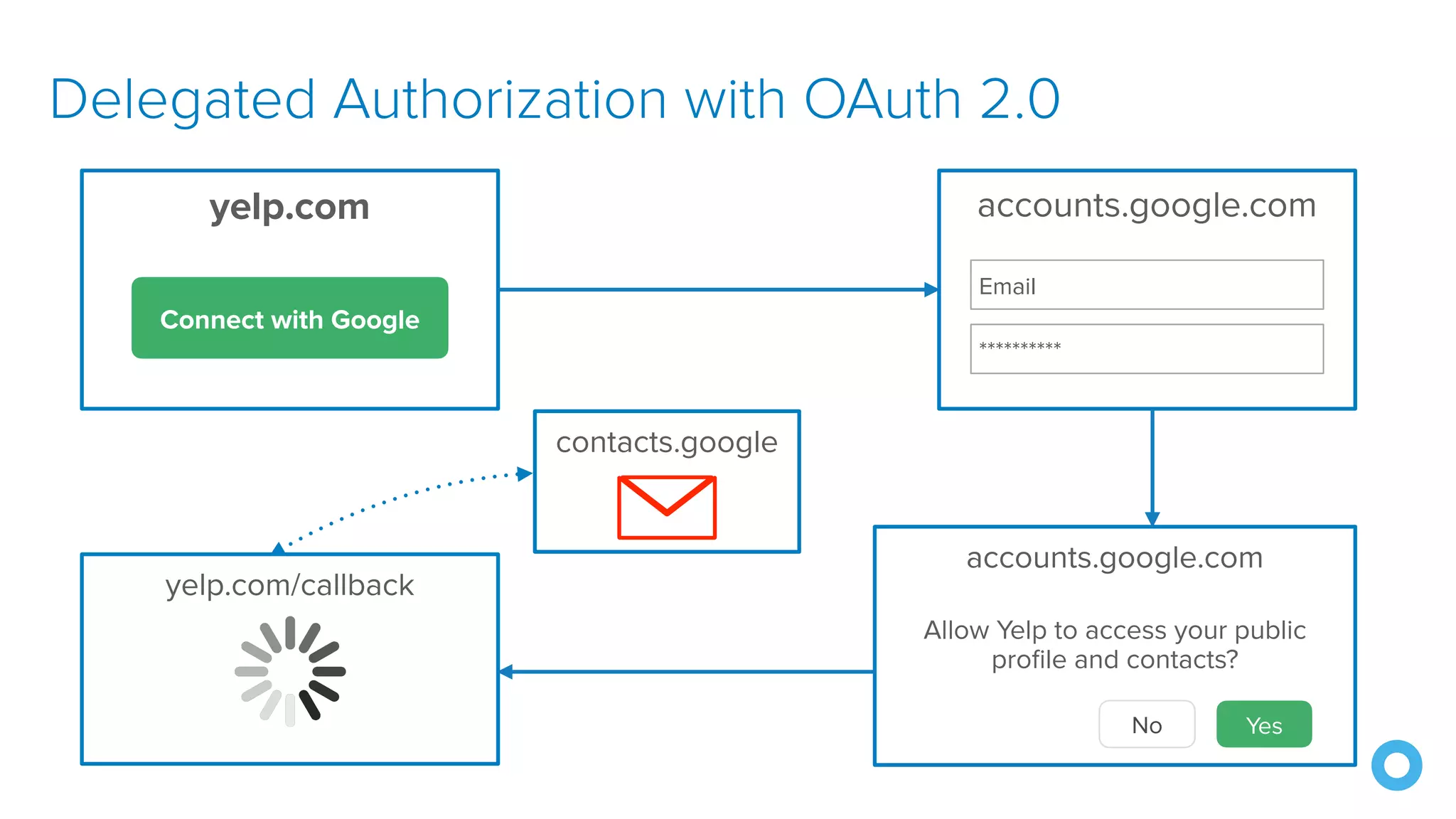
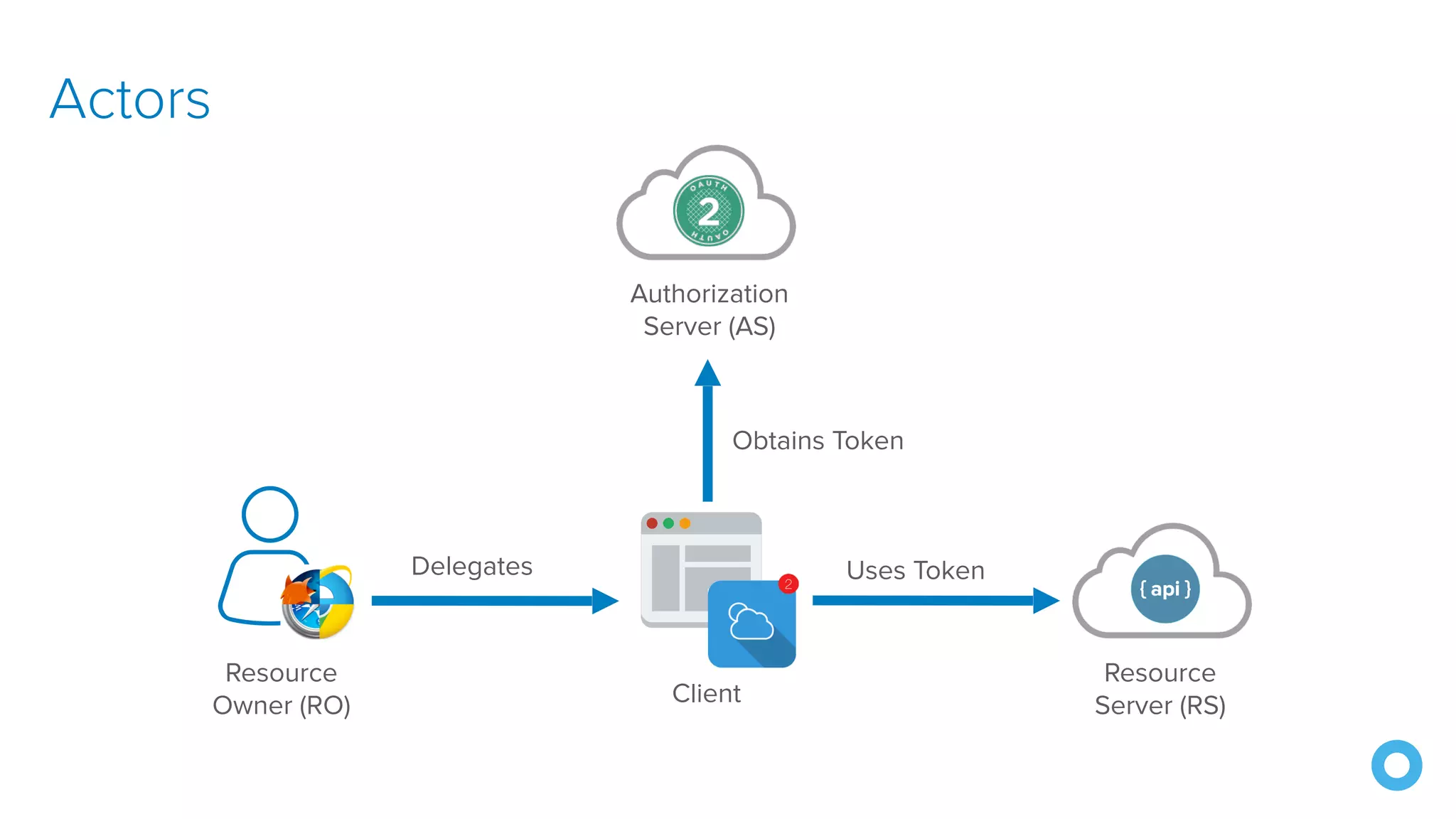
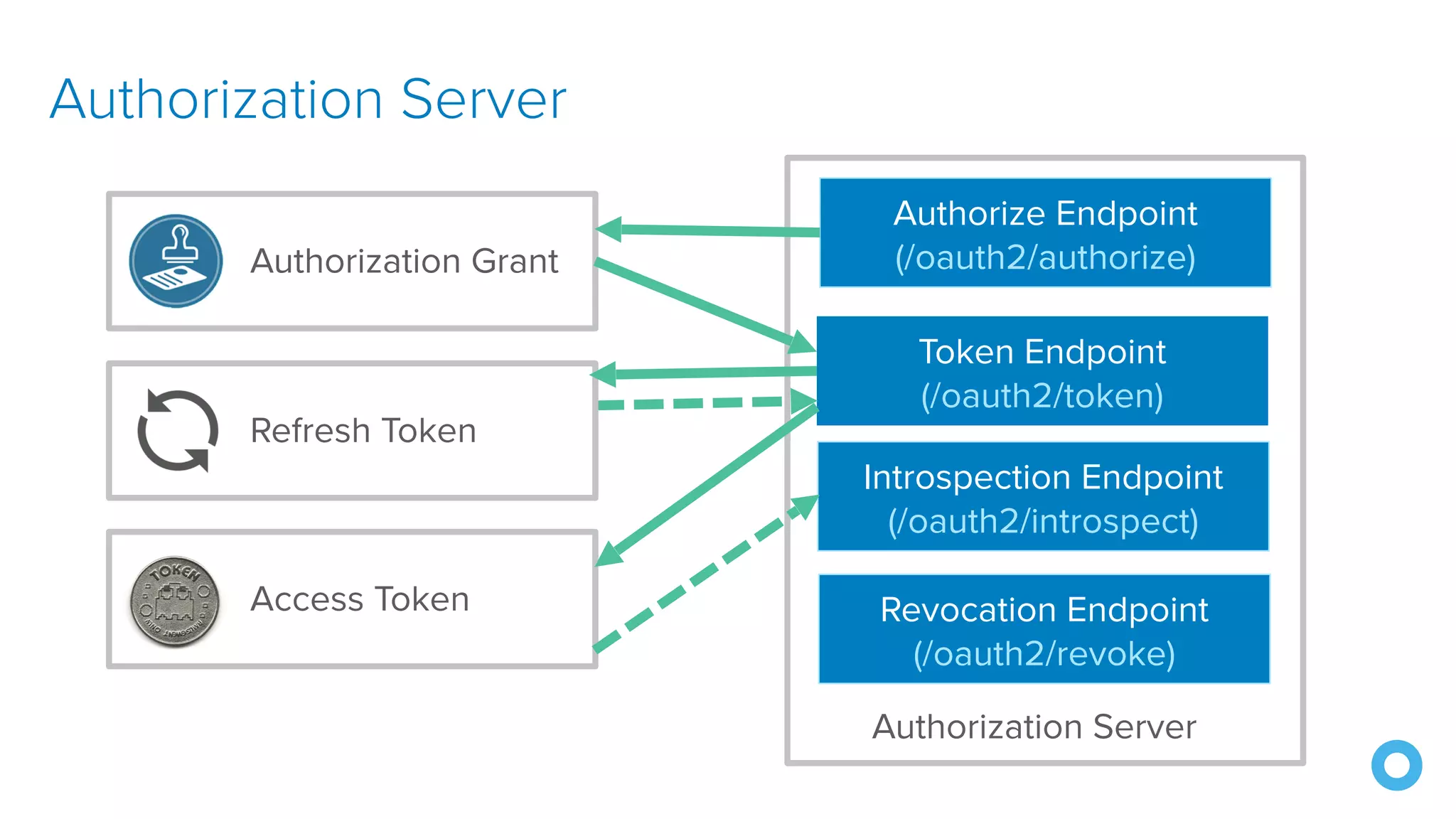
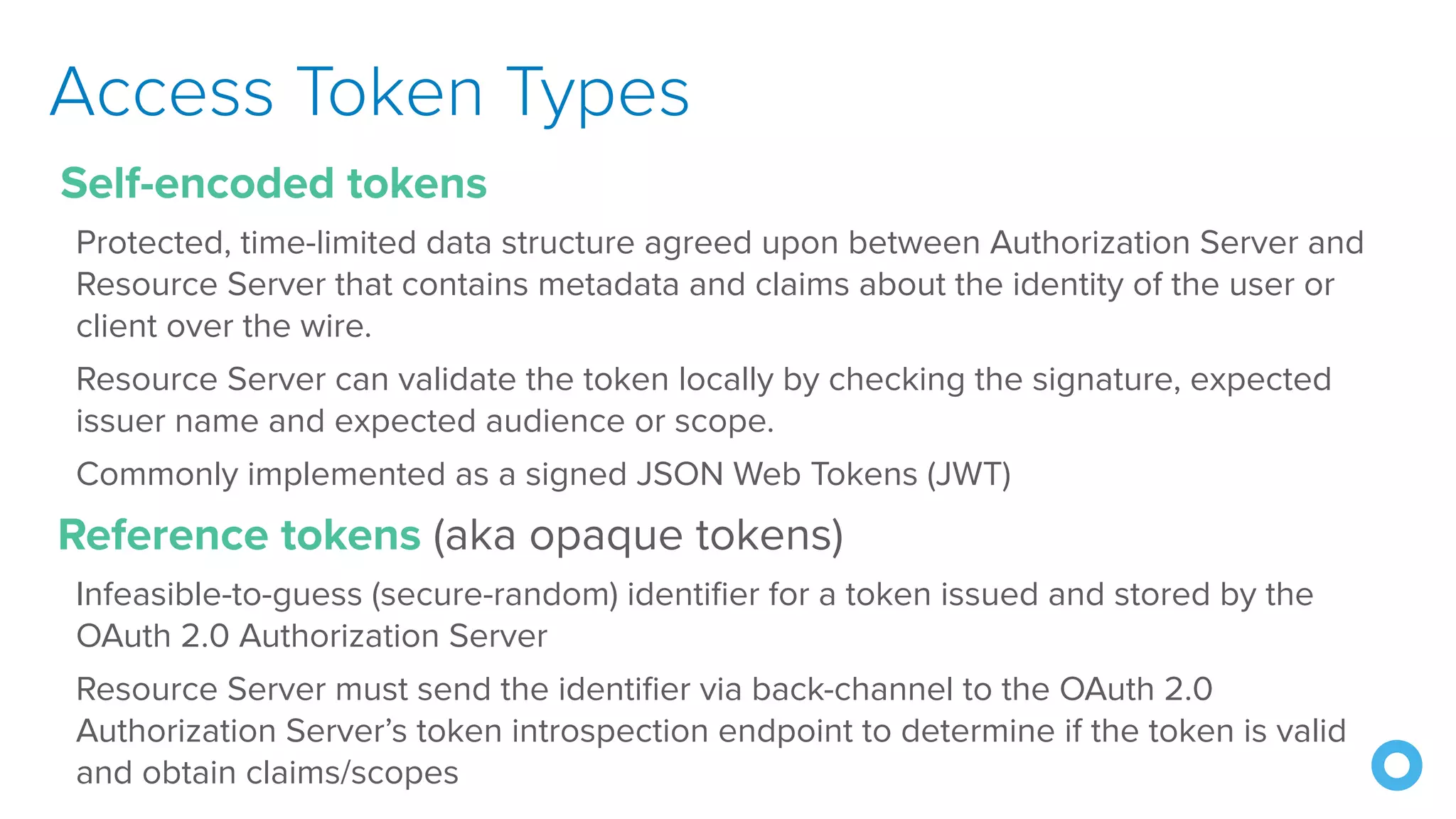
The document discusses OAuth 2.0 and OpenID Connect (OIDC), highlighting their roles in secure delegated authorization and authentication. It explores JHipster's implementation of OAuth, including integration with Keycloak and Okta, offering examples and best practices for configuring identity providers. The content further delves into technical aspects such as token types, flows, and configurations for setting up secure applications using JHipster.