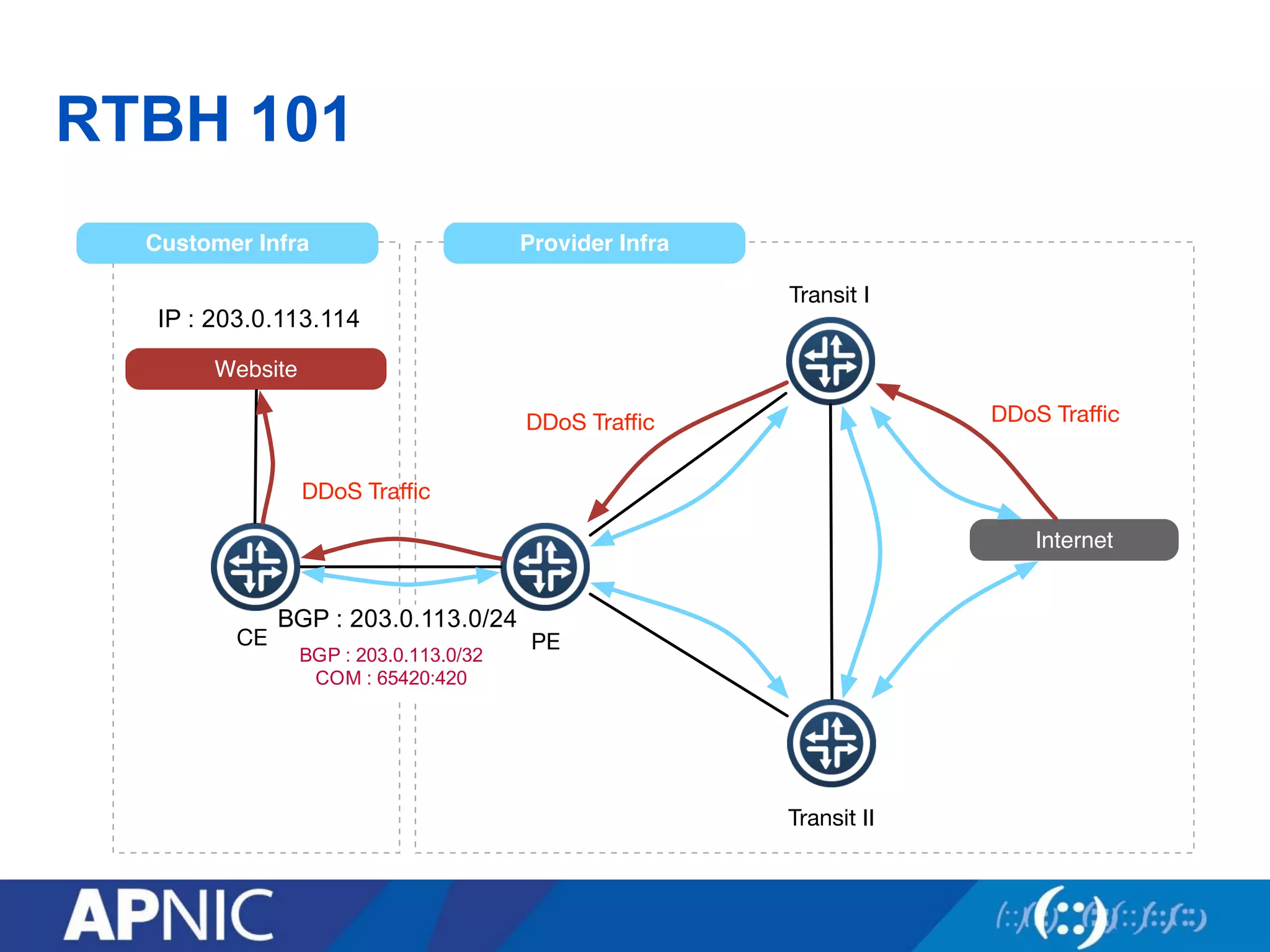
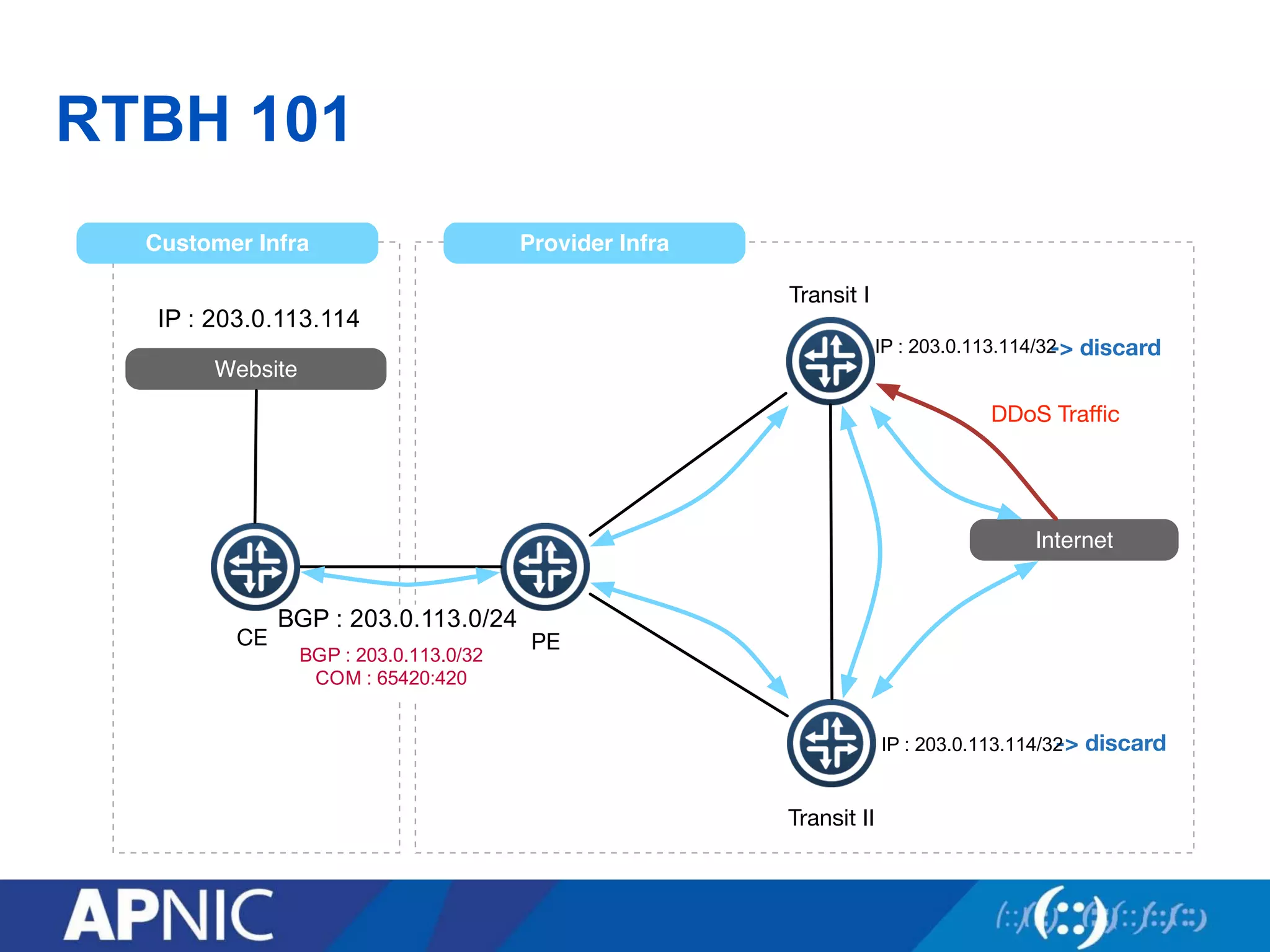
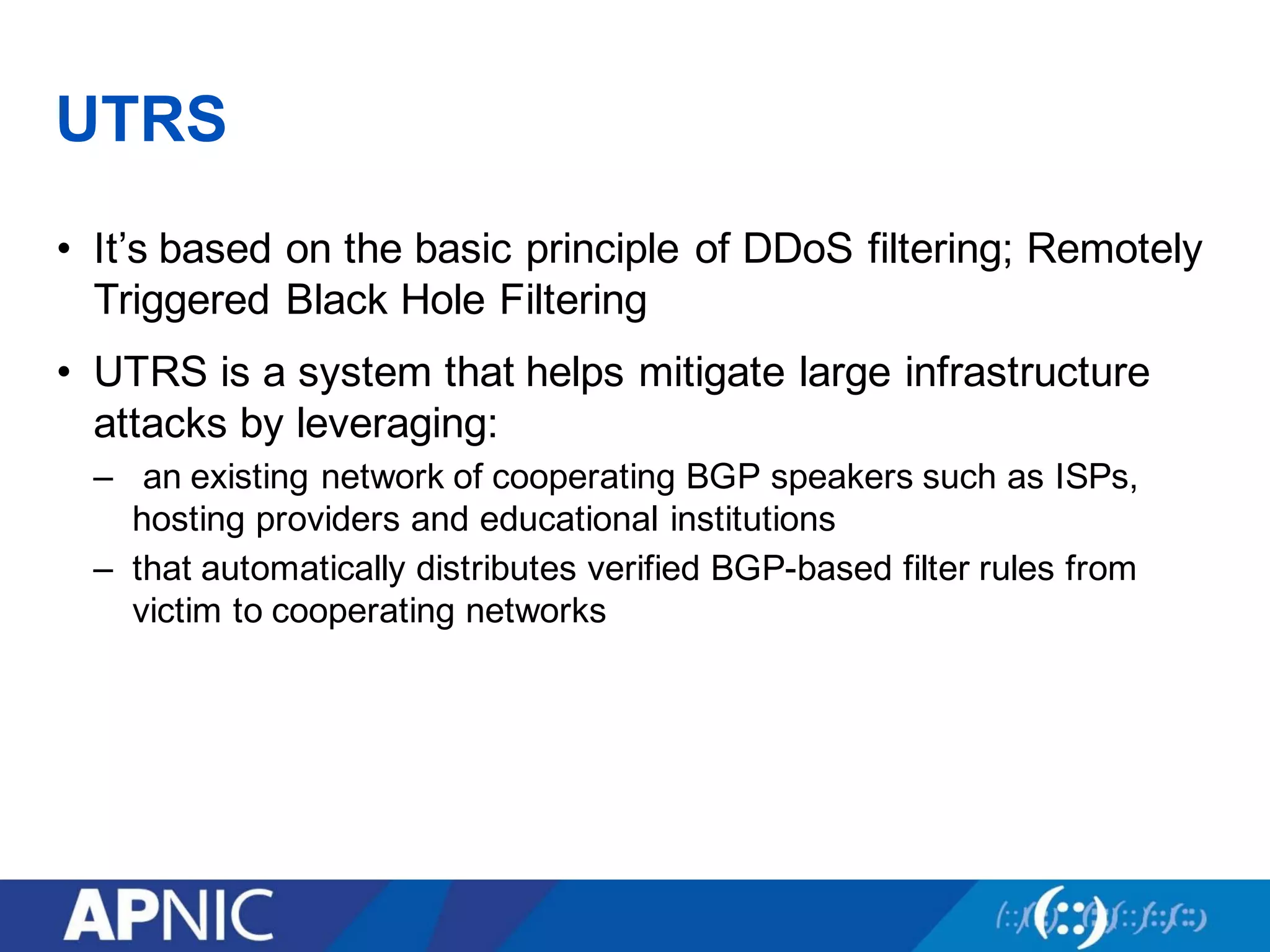
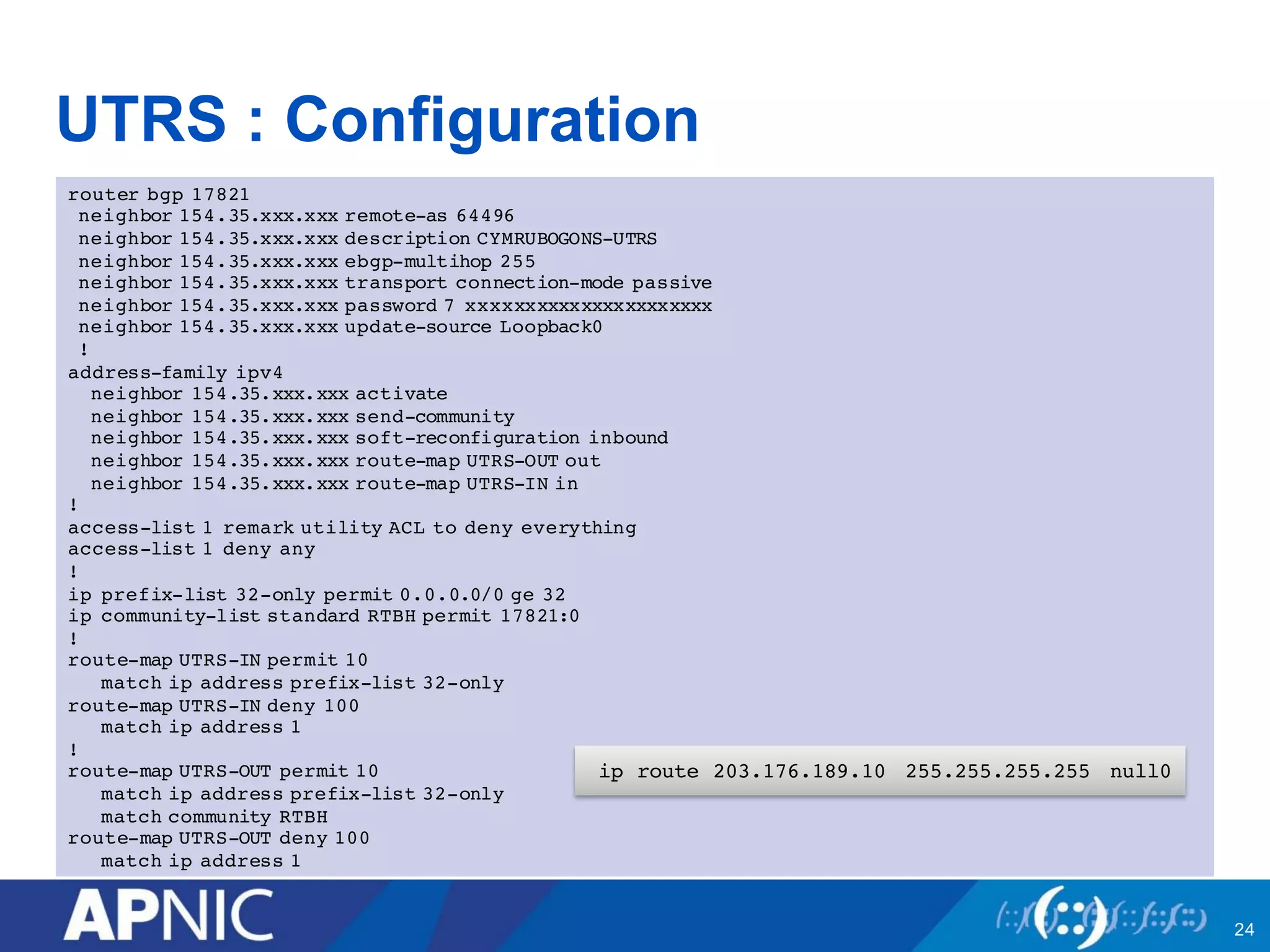
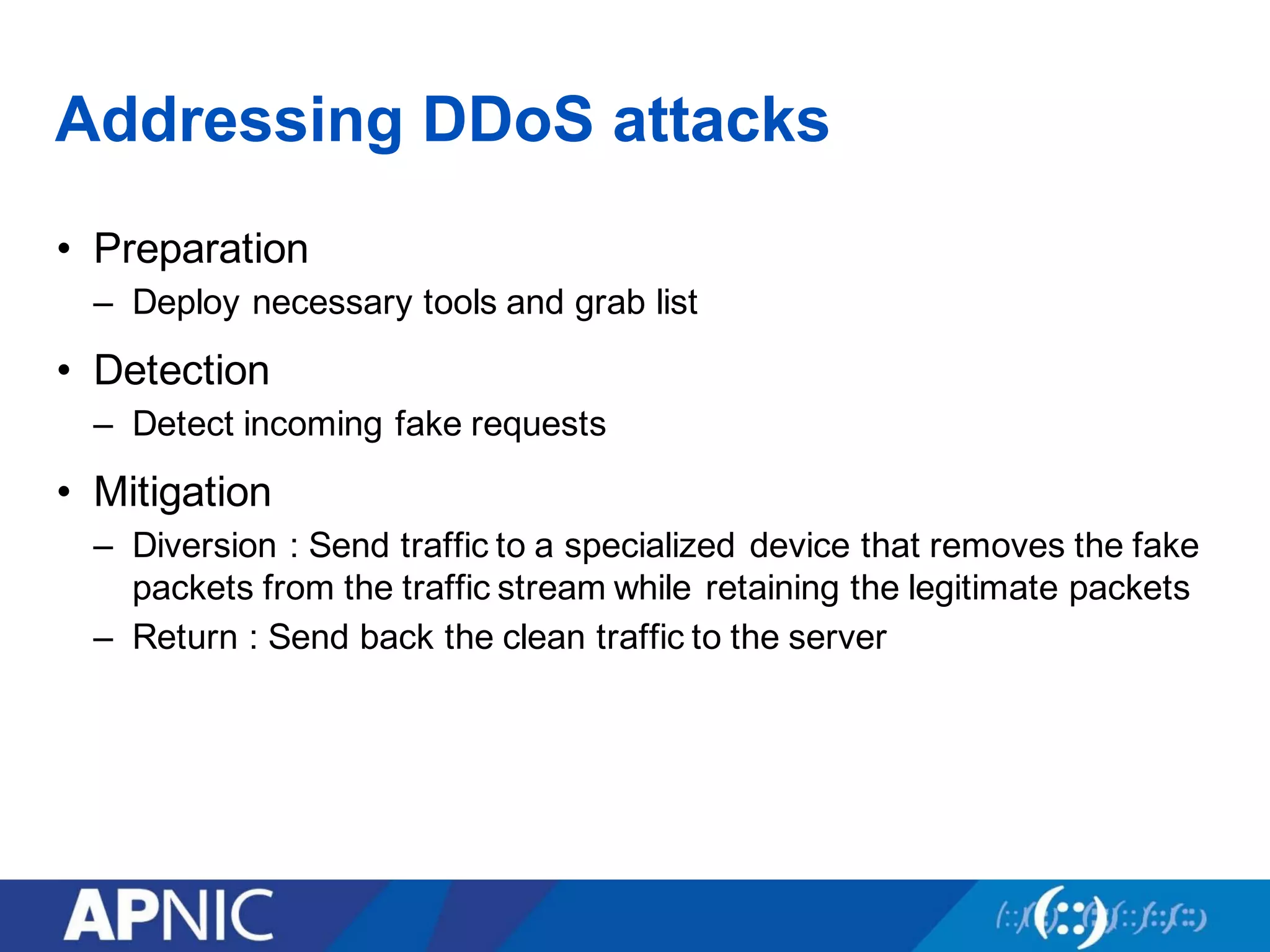
Community tools can help fight DDoS attacks in three ways:
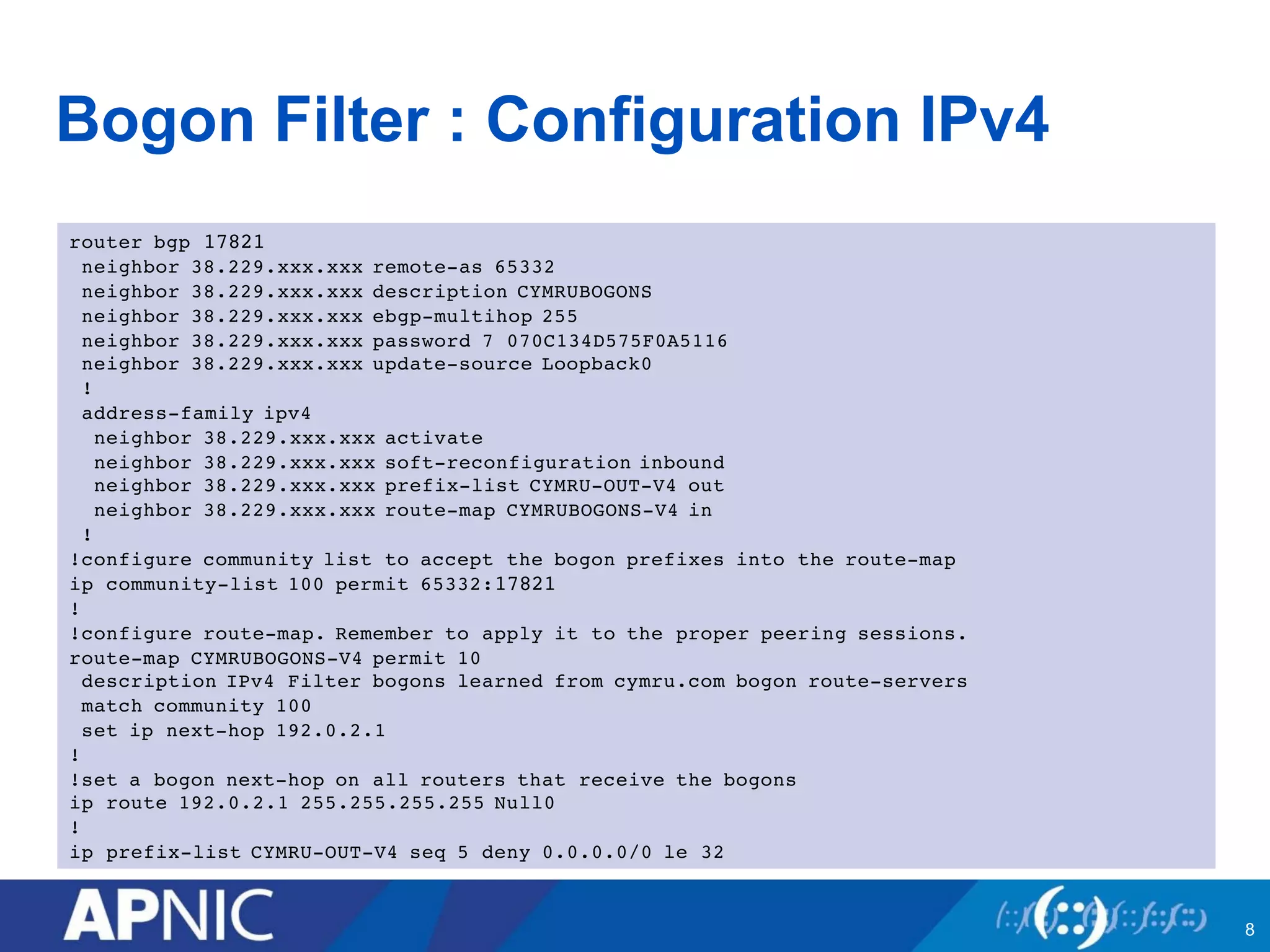
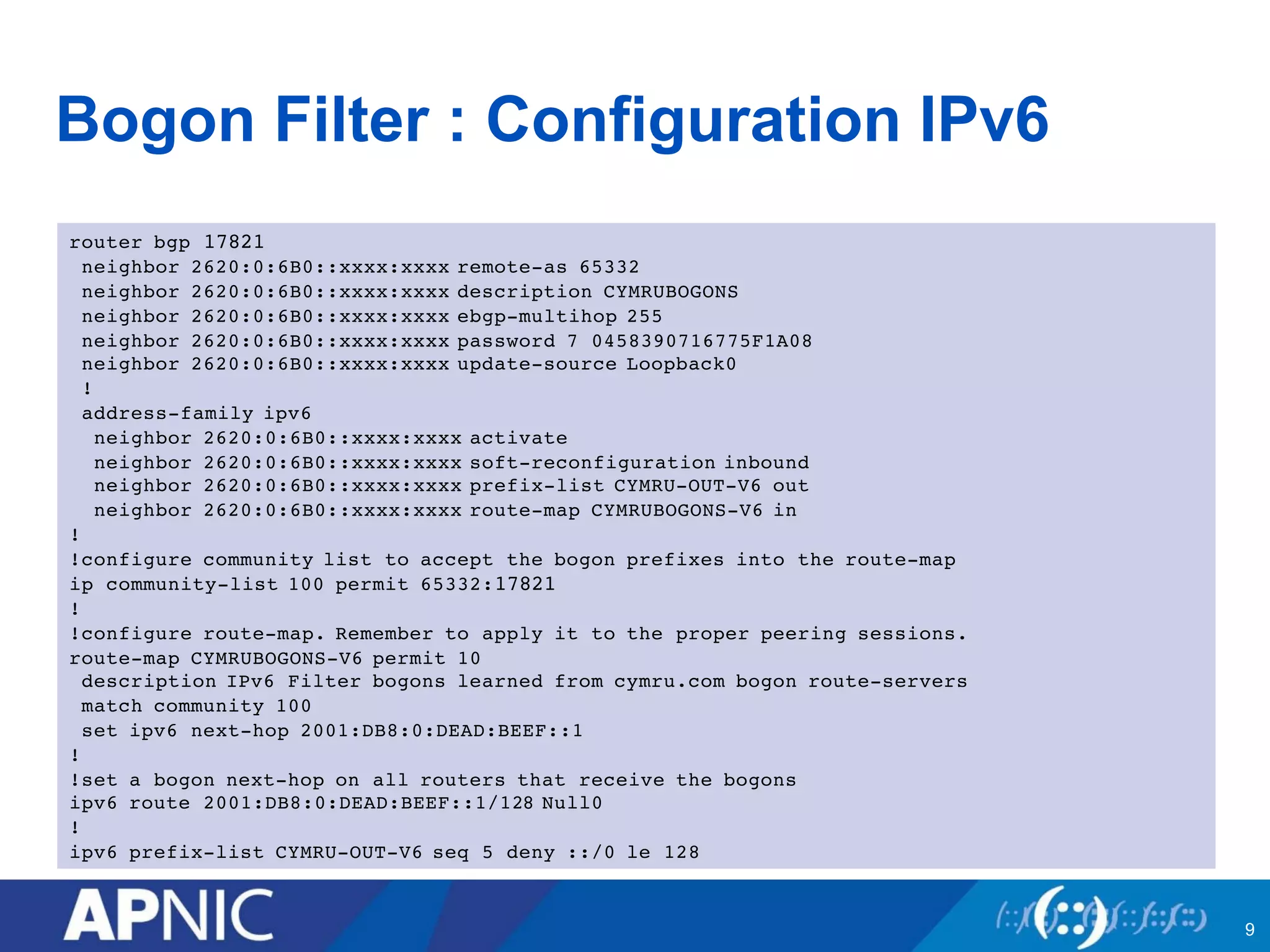
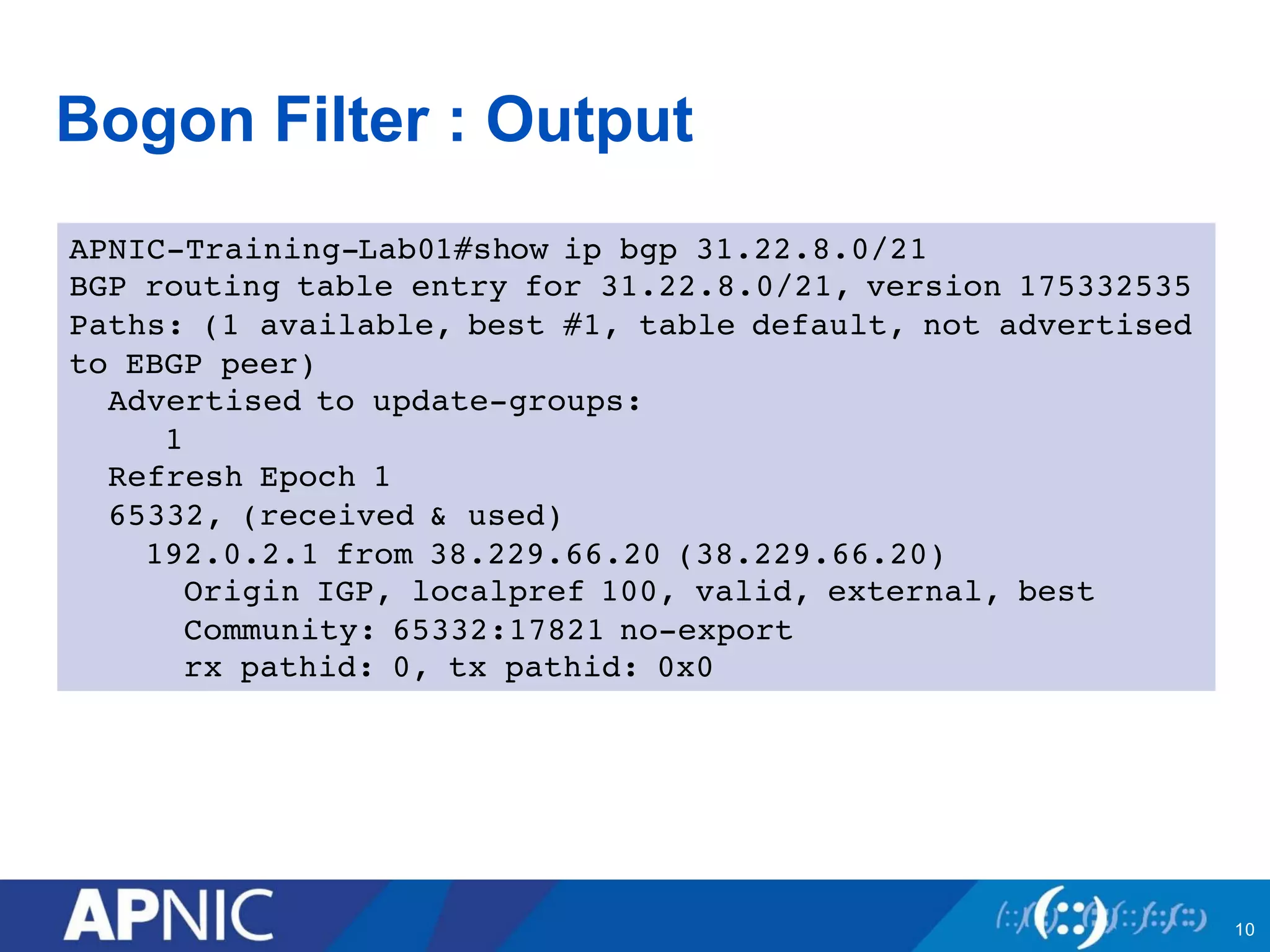
1. Bogon filtering blocks traffic from bogon address space not assigned to any network. Networks share bogon lists and filter incoming routes.
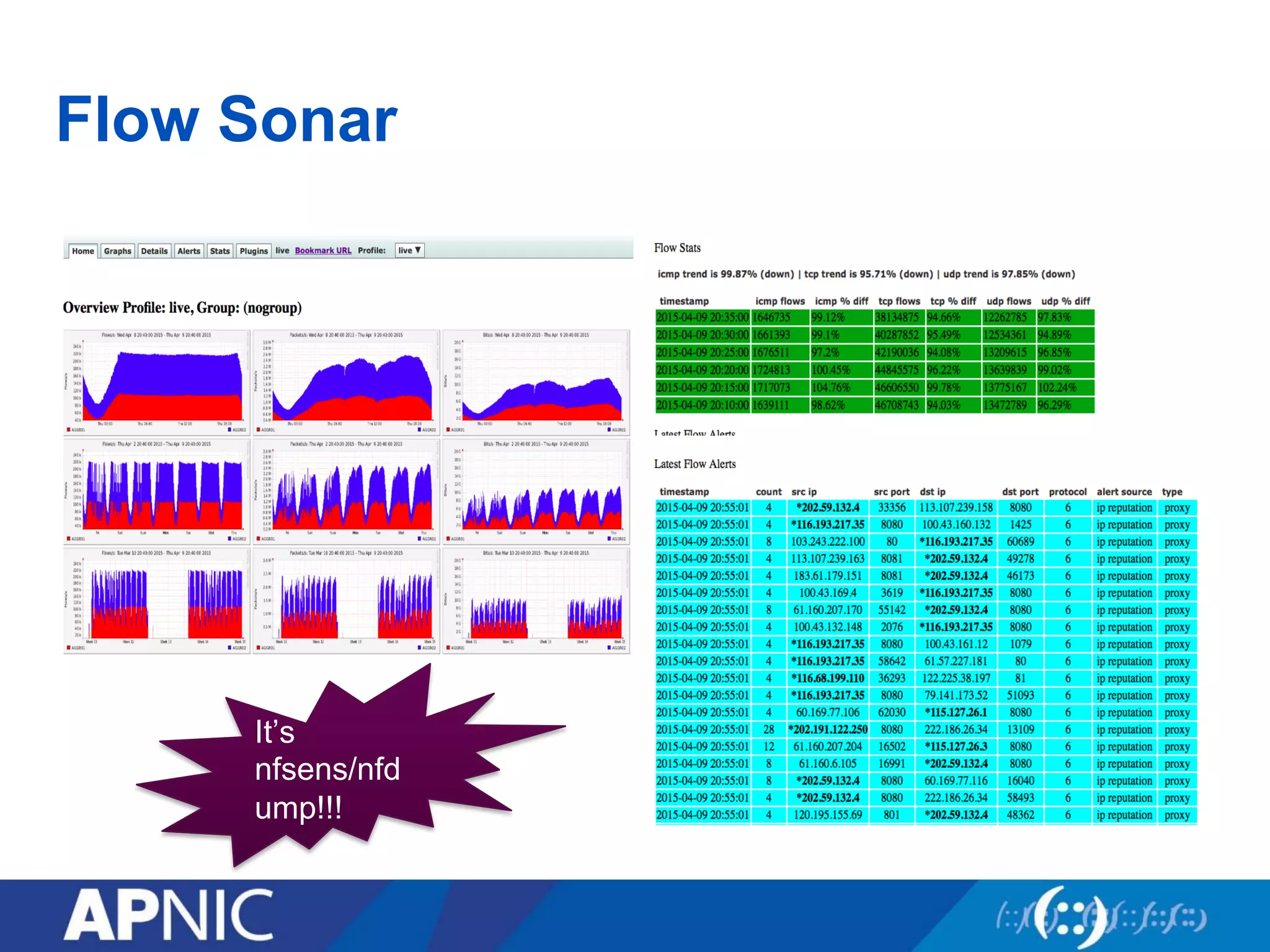
2. Flow Sonar provides visual network traffic analysis to detect anomalies indicating attacks. It incorporates DDoS alert feeds to identify compromised sources.
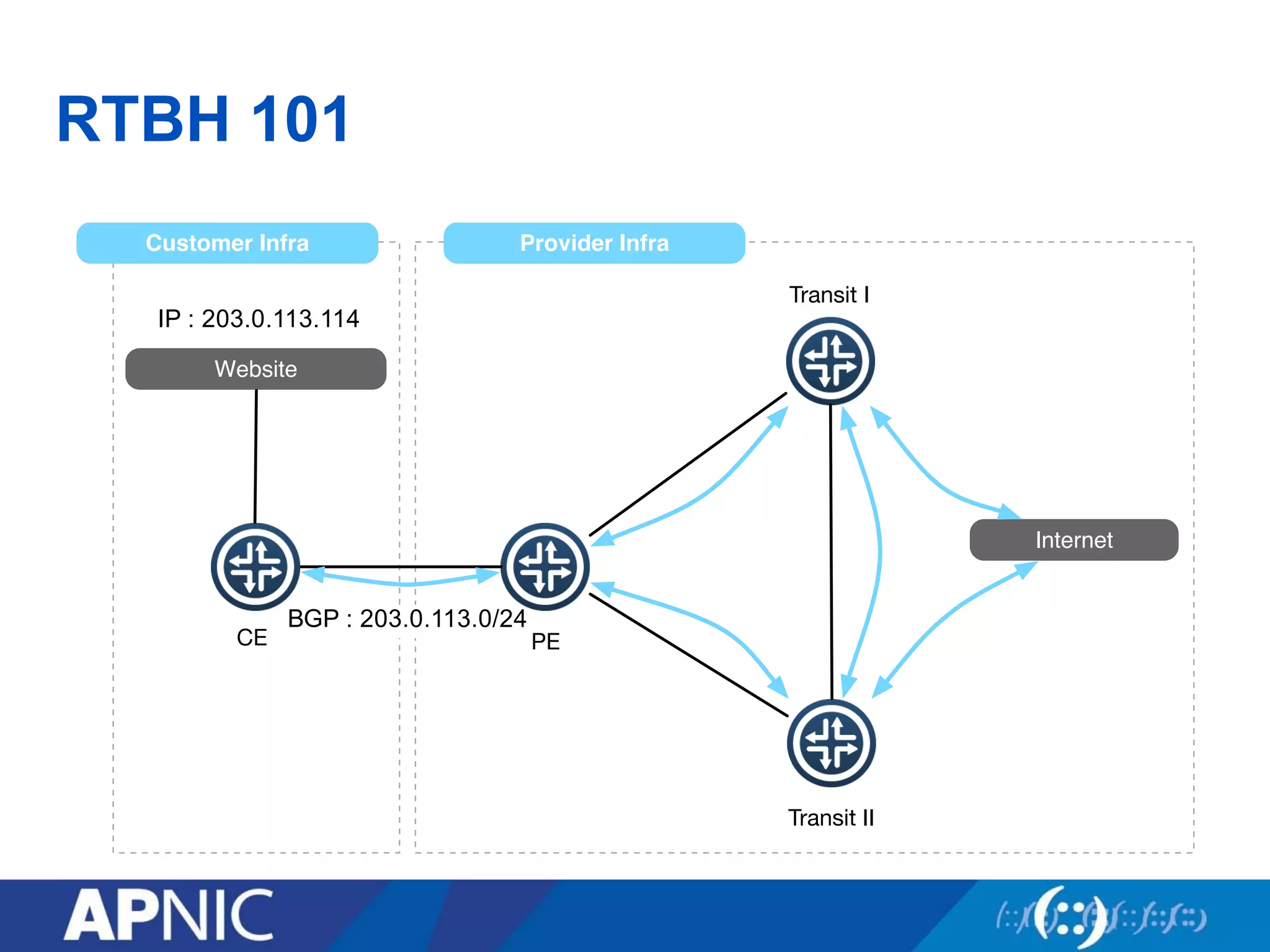
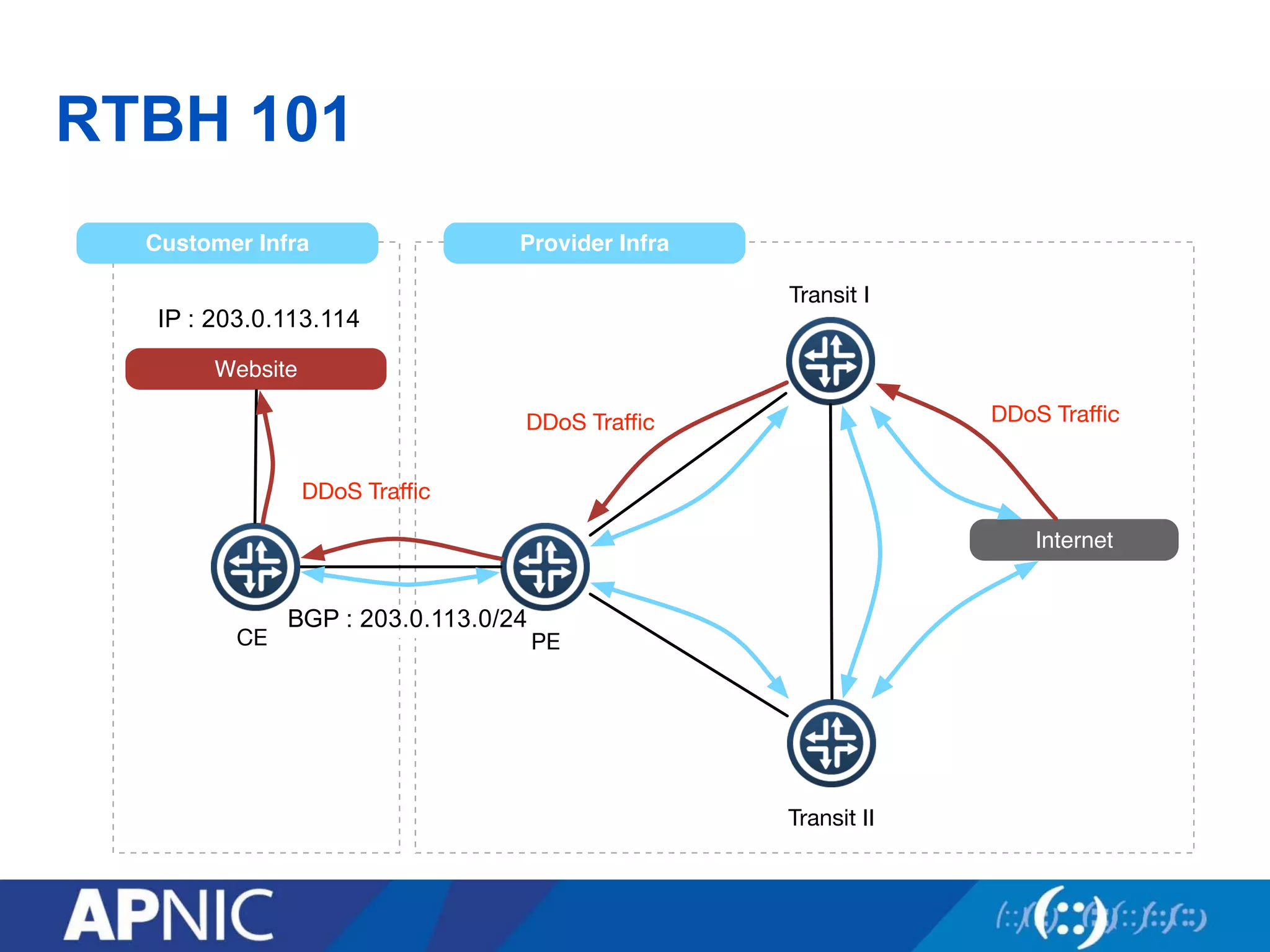
3. UTRS implements remote triggered blackhole filtering to divert suspected attack traffic to a null route. Cooperating networks distribute and apply attack filters to mitigate large infrastructure attacks.





![Bogon Filter : Status
• The IPv4 fullbogons list is approximately 3,714 prefixes.
– [date : 26th January, 2016]
• The IPv6 fullbogons list is approximately 65,788 prefixes.
– [date : 26th January, 2016]
Neighbor V AS MsgRcvd MsgSent TblVer InQ OutQ
Up/Down State/PfxRcd
38.229.xxx.xxx 4 65332 12017 12017 186072391 0
0 1w0d 3733
Neighbor V AS MsgRcvd MsgSent TblVer InQ OutQ
Up/Down State/PfxRcd
2404:A800:xxxx:xx::xxxx
4 9498 3239994 72131 40075514 0 0
3w1d 65788](https://image.slidesharecdn.com/sanog27-conferencecommunitytoolstofightagainstddos-160202010702/75/Community-tools-to-fight-against-DDoS-SANOG-27-11-2048.jpg)