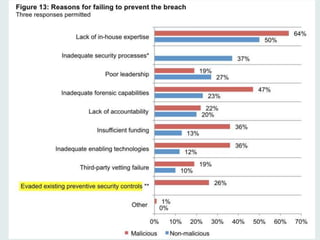
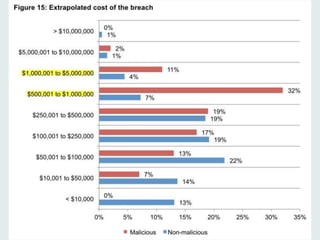
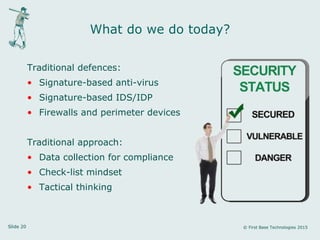
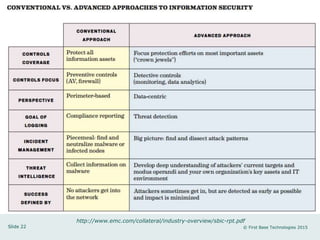
Peter Wood, CEO of First Base Technologies, discusses the current state of big data and its implications for security in a comprehensive presentation. He highlights the rapid growth of data, the increasing sophistication of cyber threats, and the potential of big data analytics to enhance security measures, while also addressing the challenges and privacy concerns associated with its use. The presentation emphasizes the necessity for organizations to adapt their security strategies in light of these developments and invest in big data security analytics.