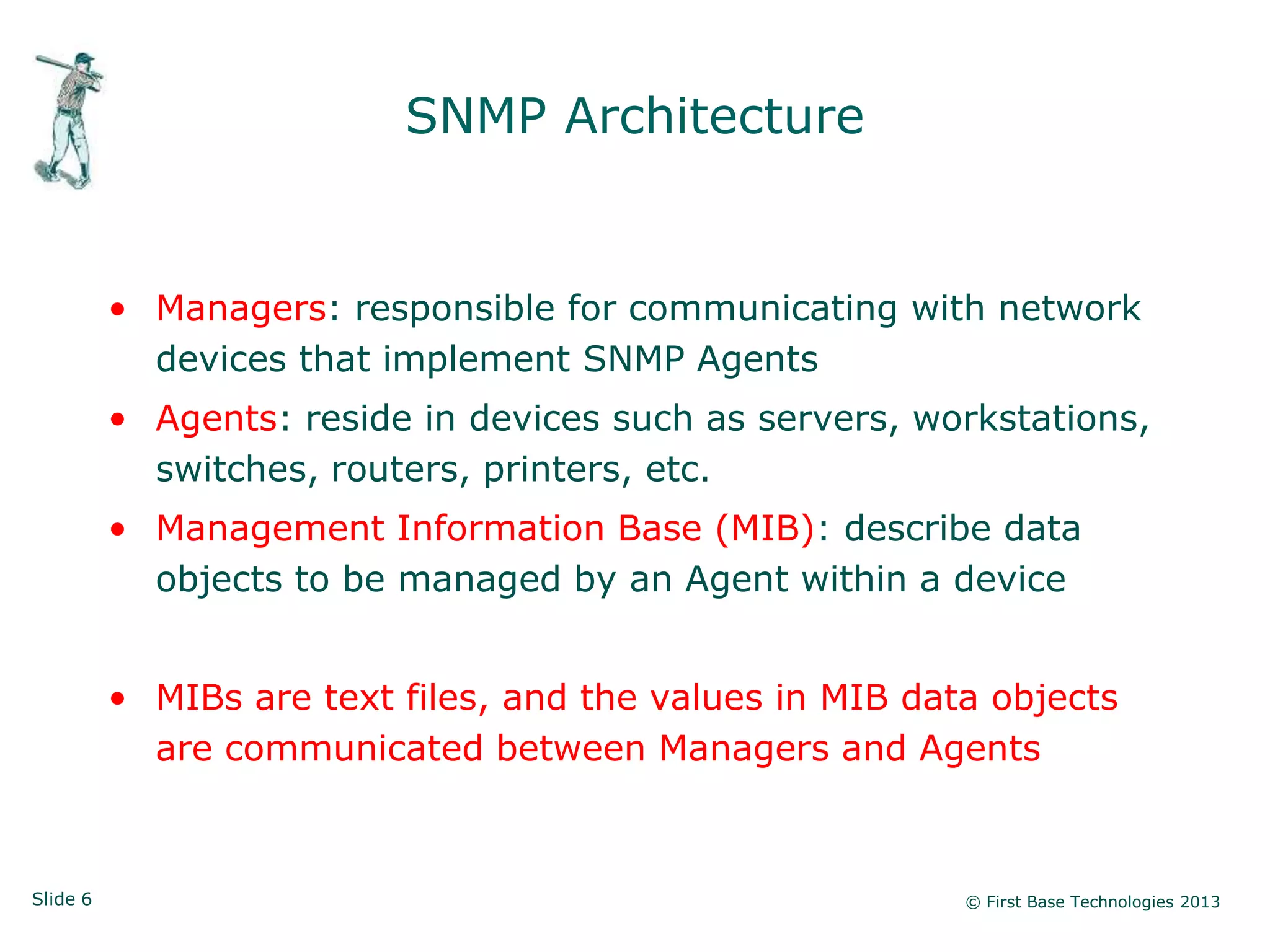
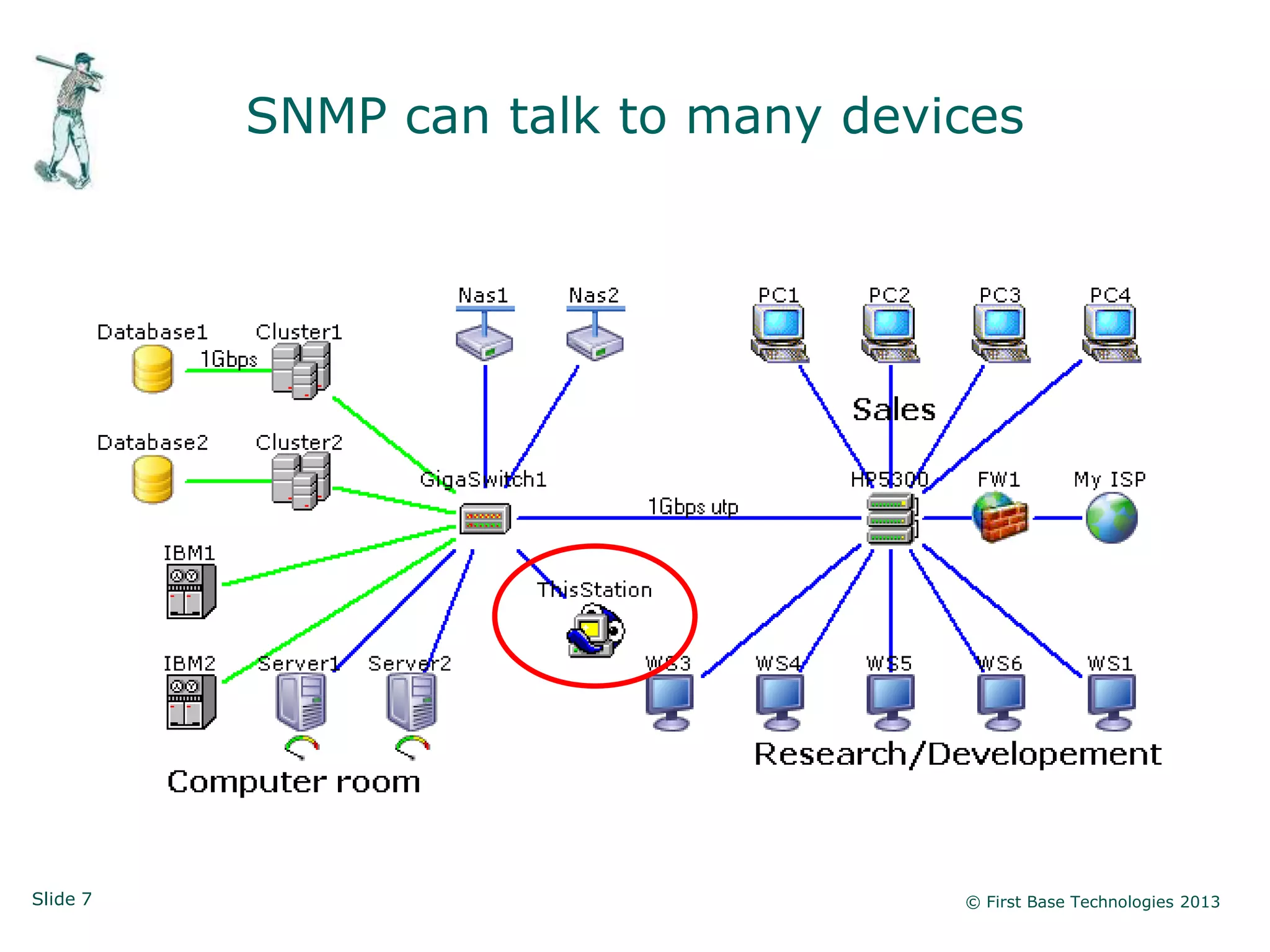
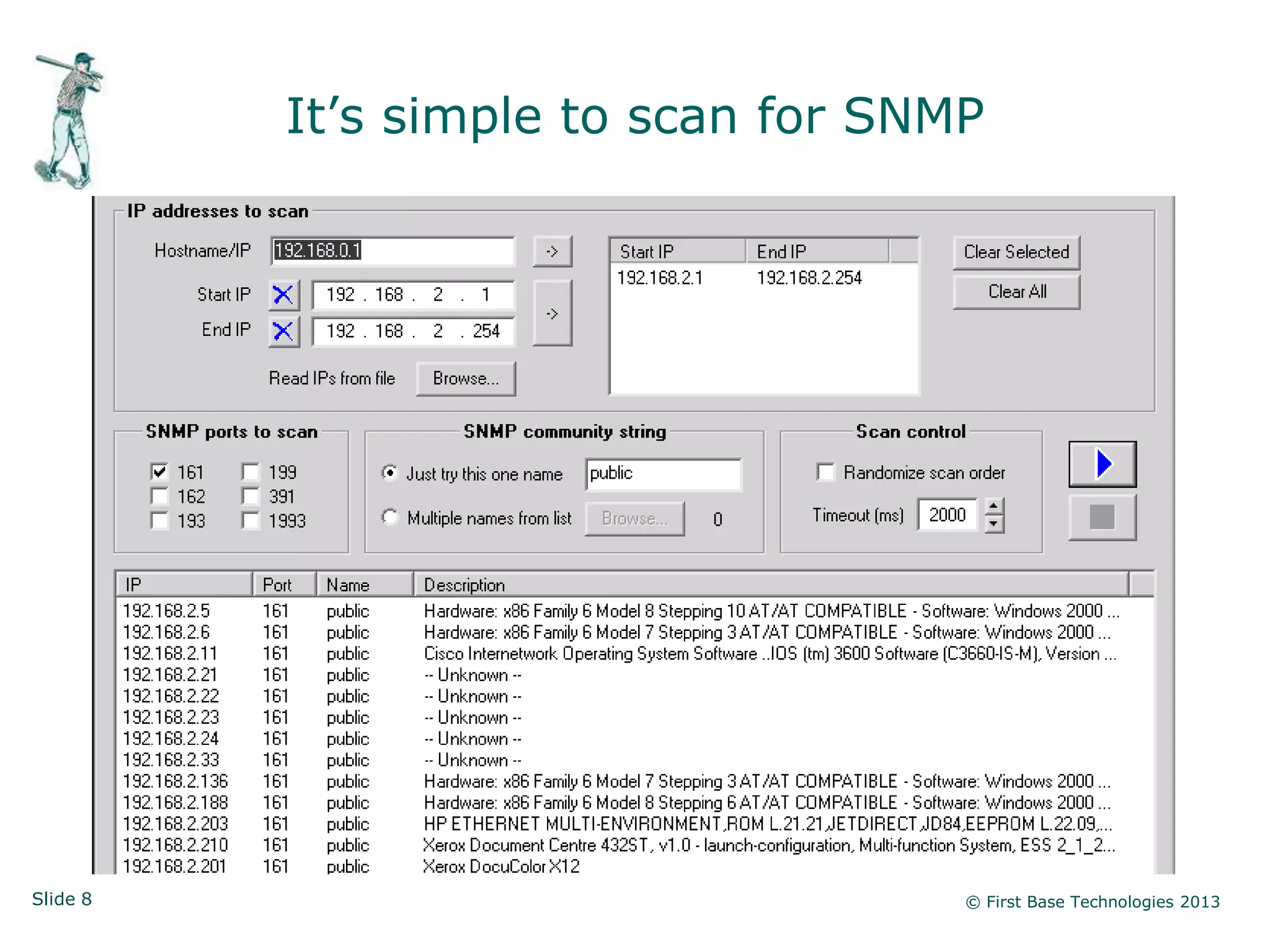
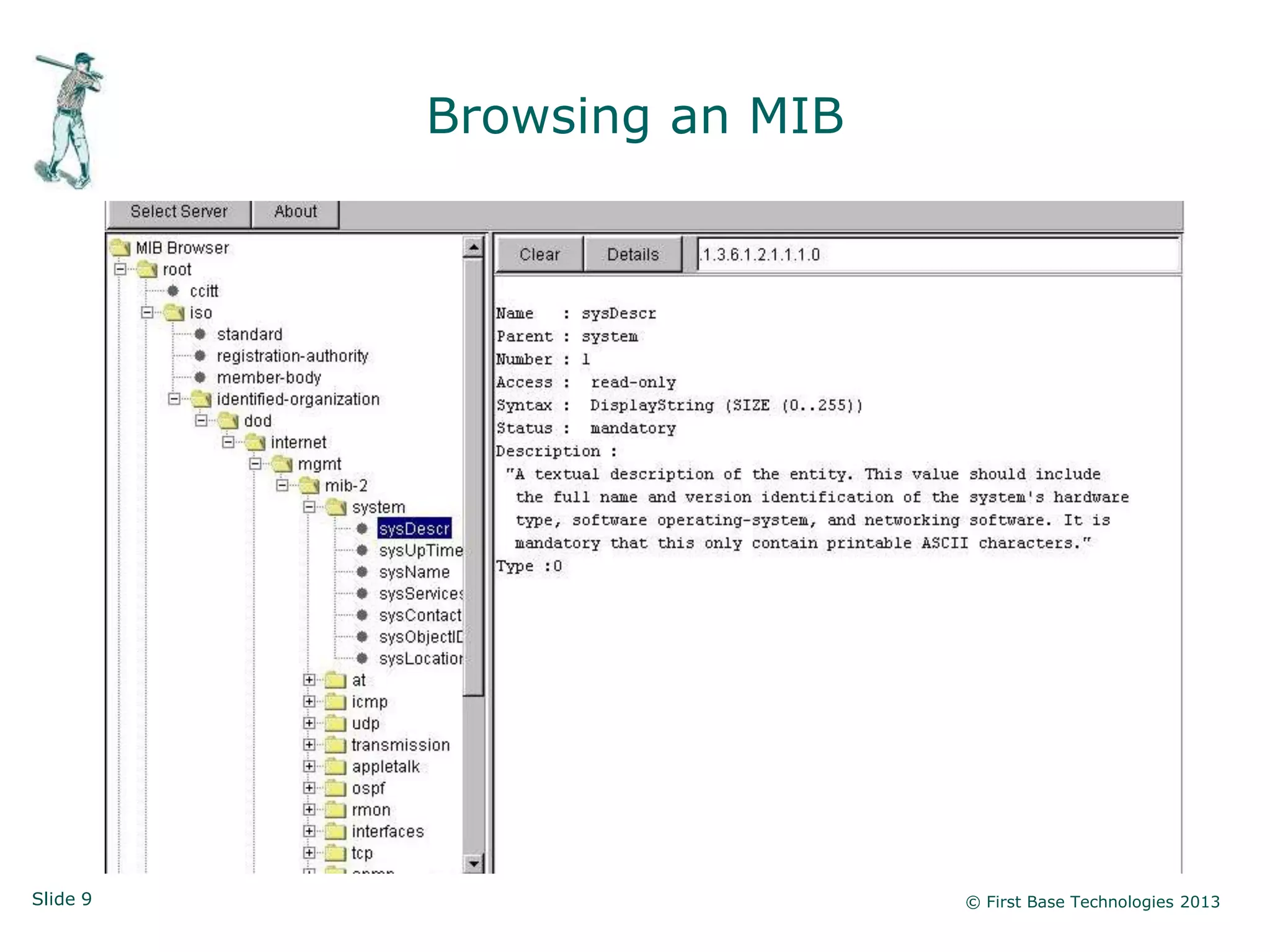
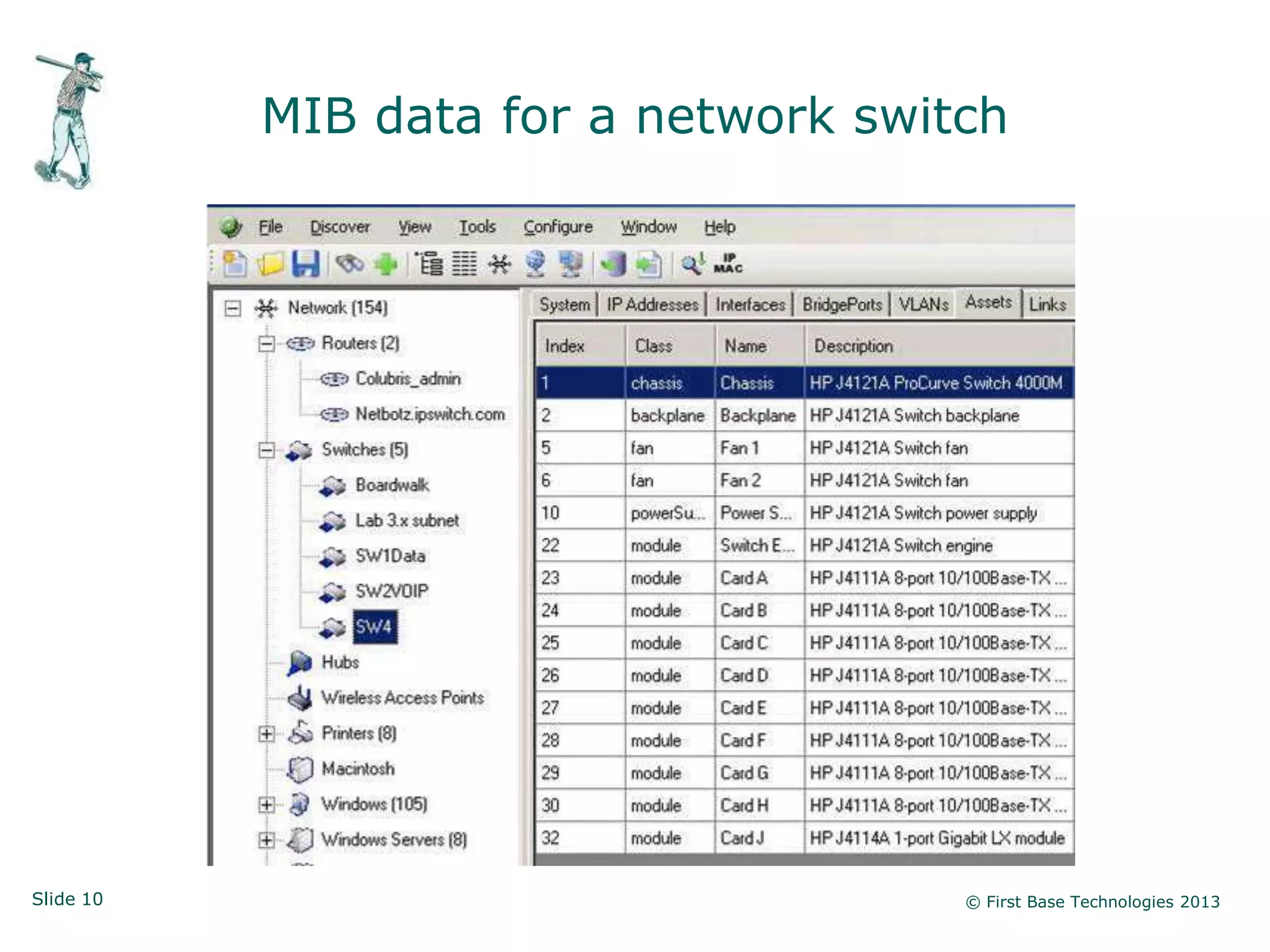
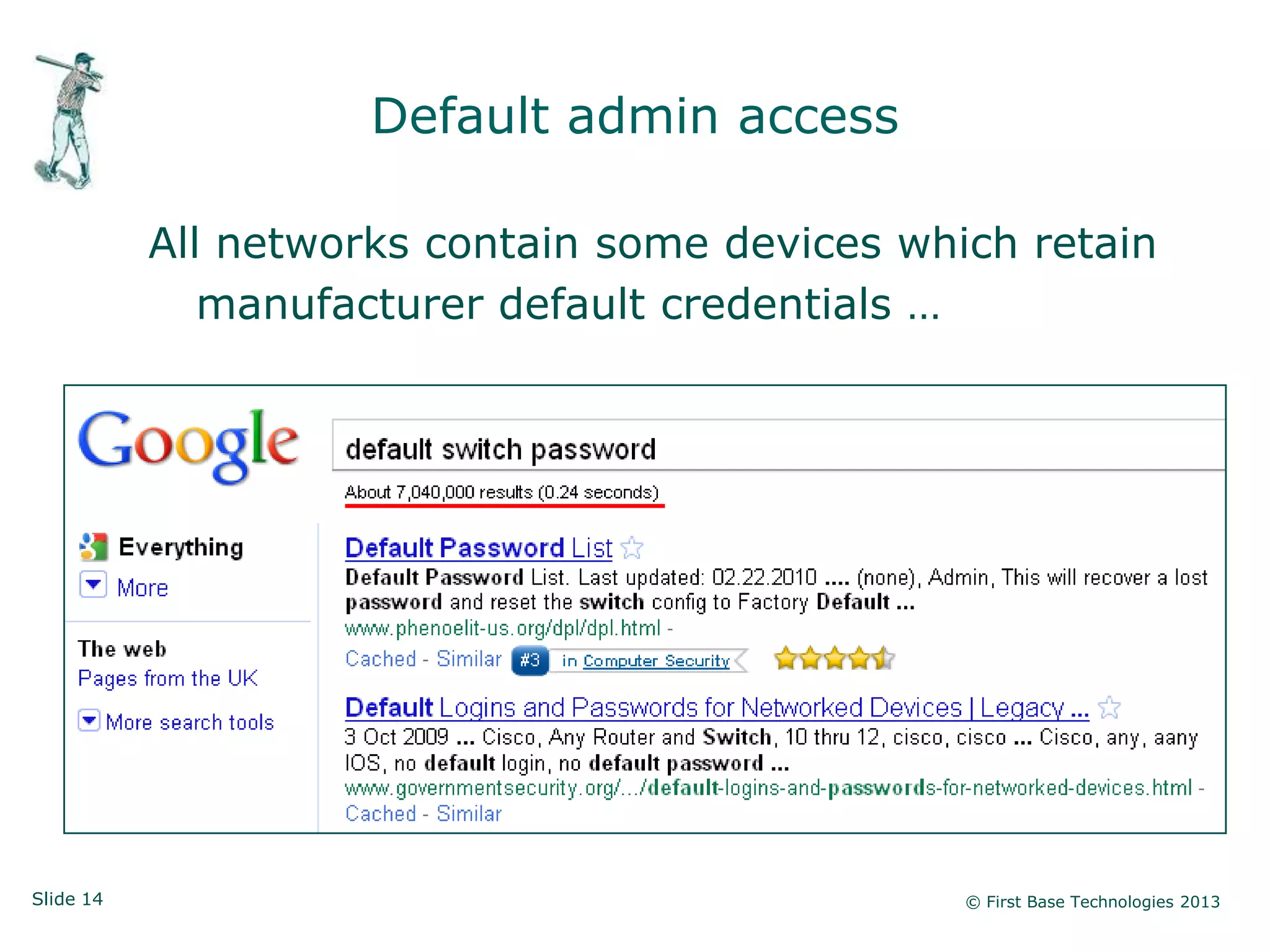
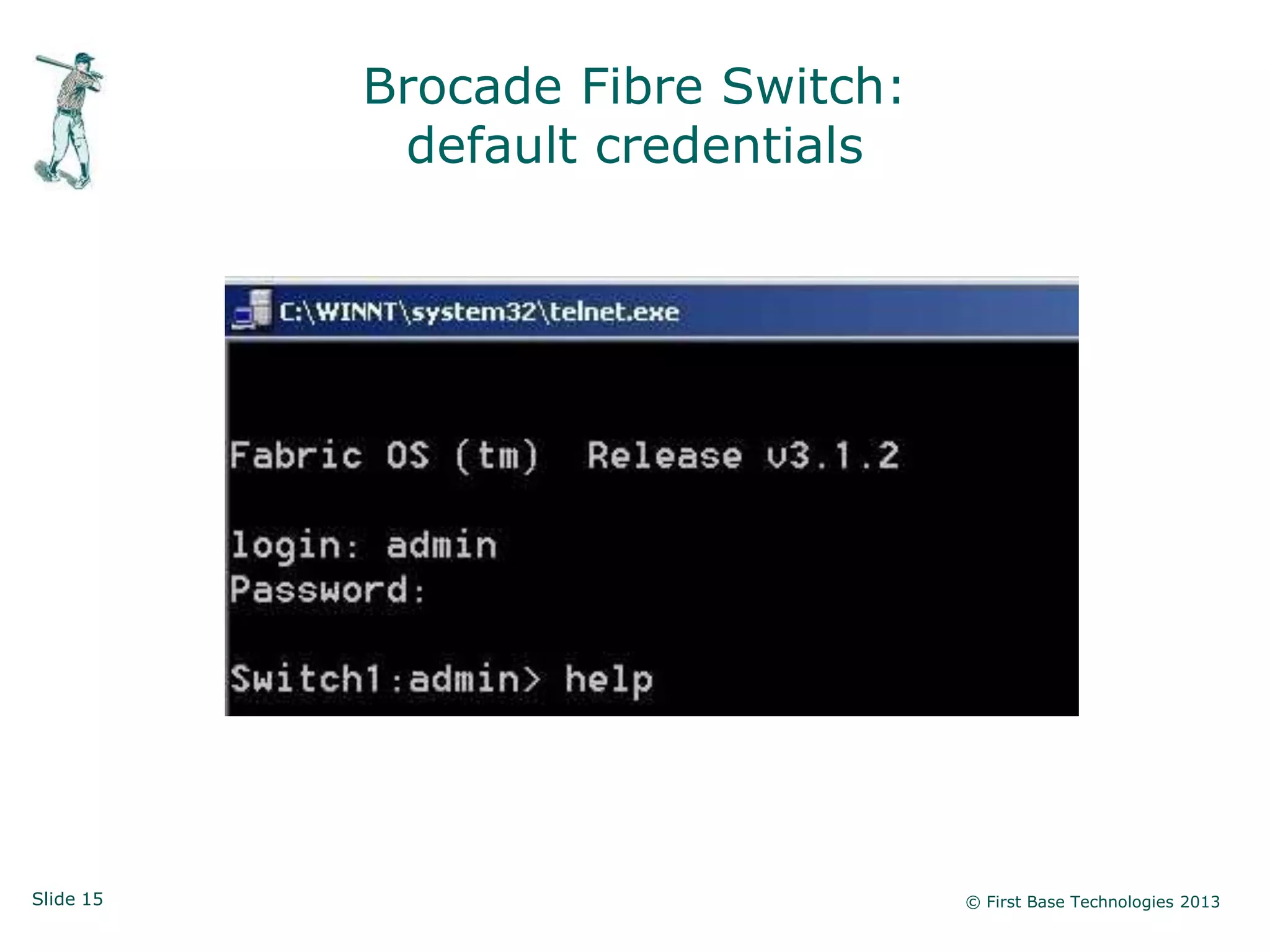
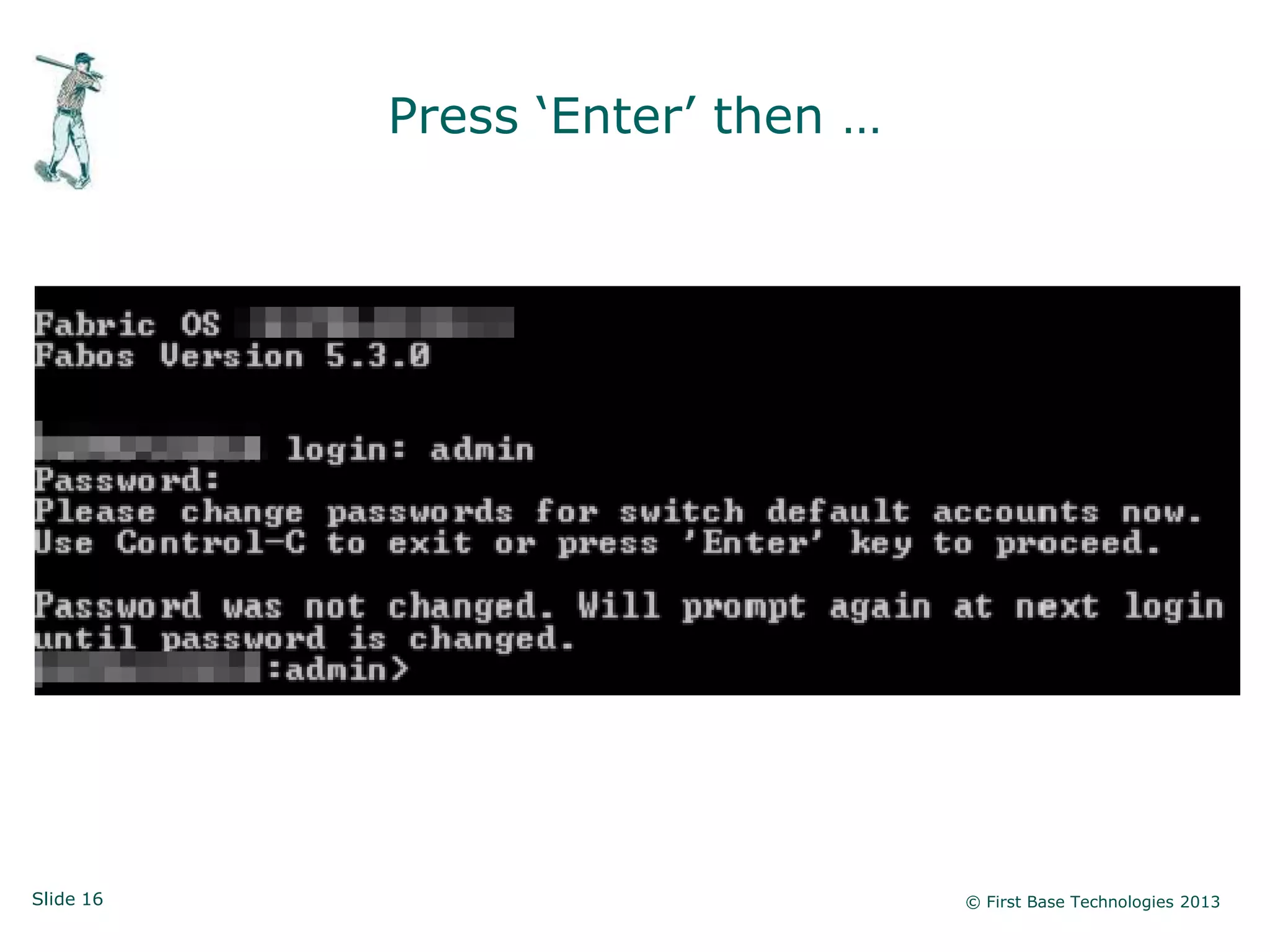
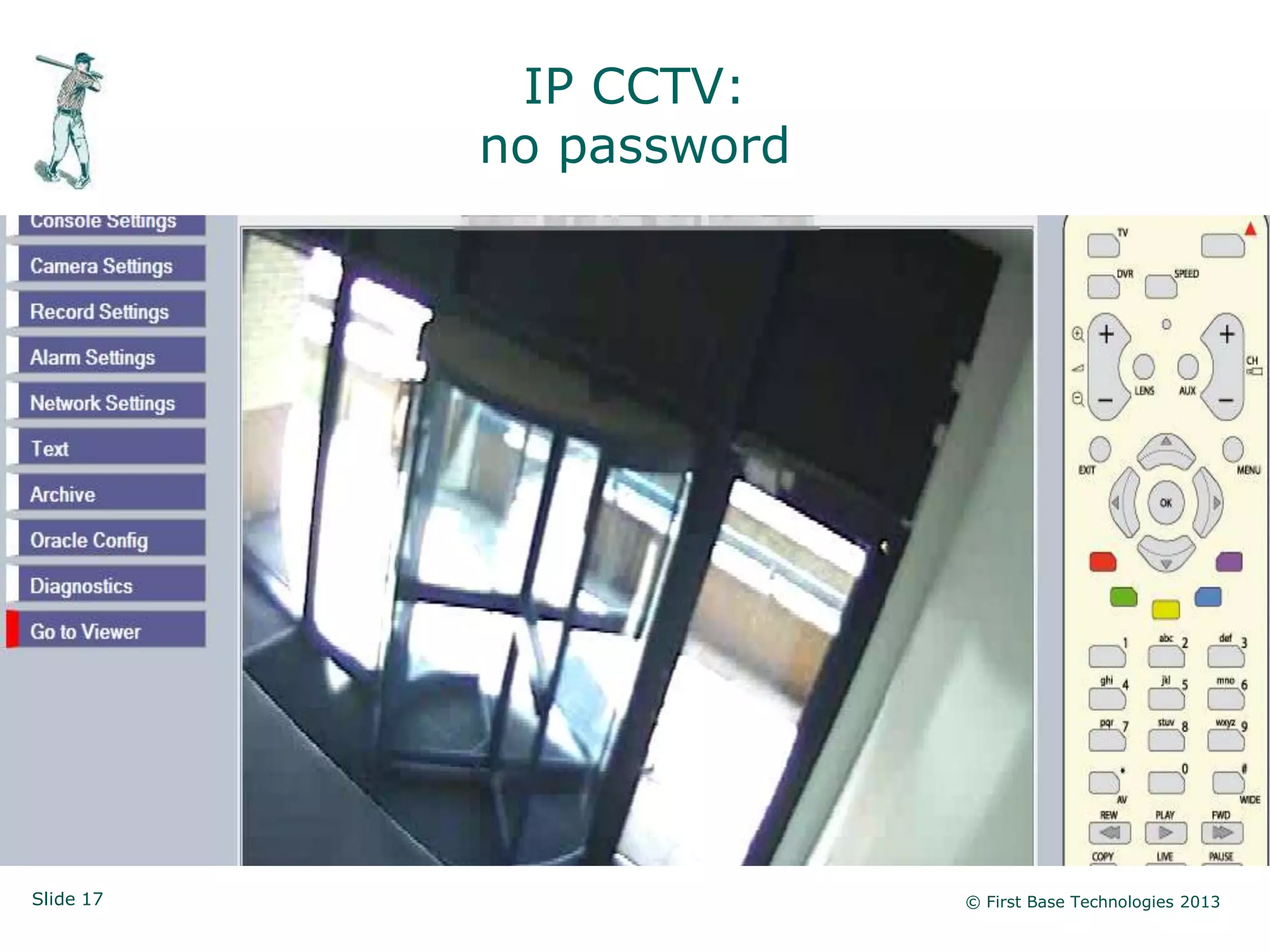
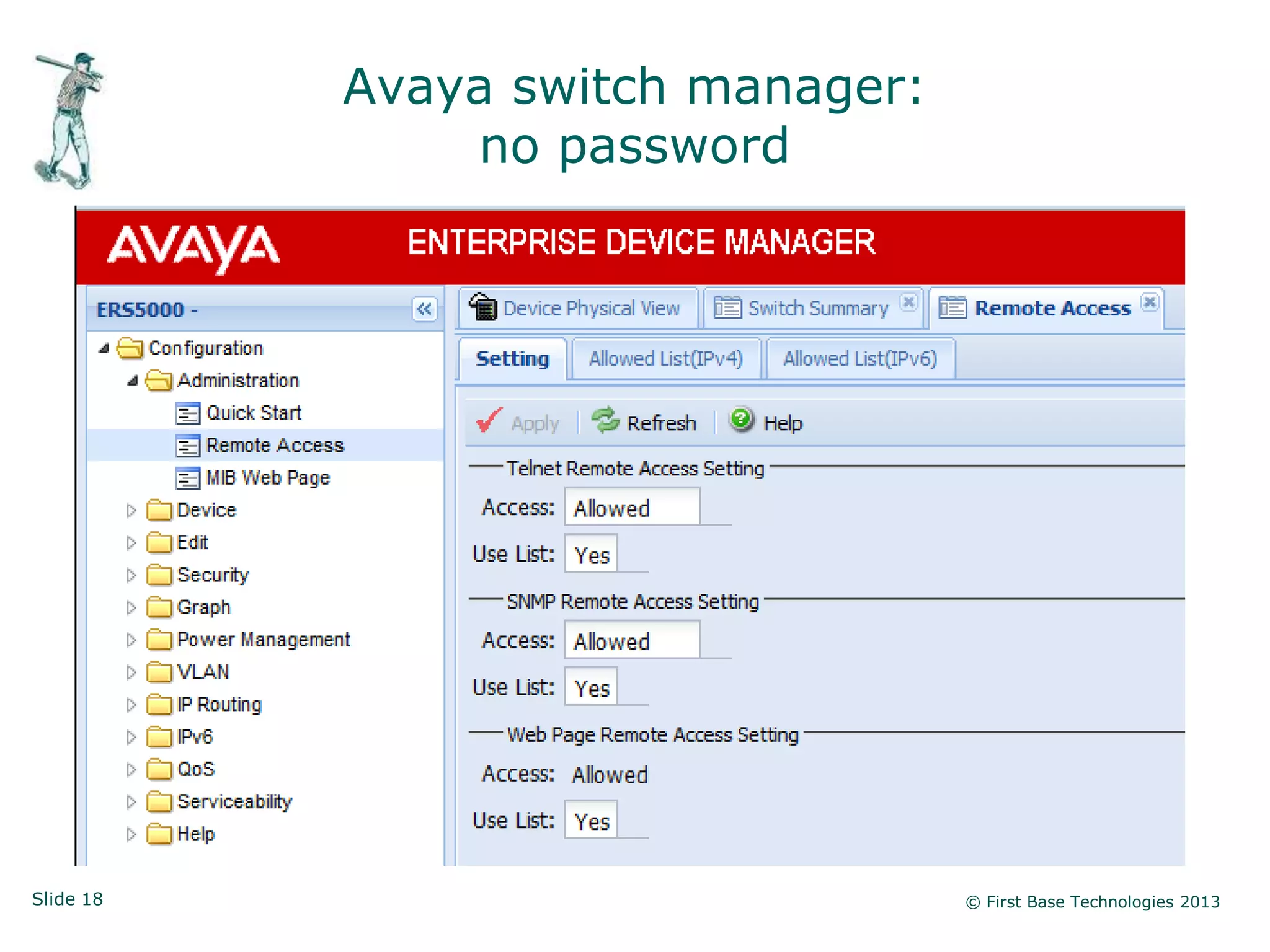
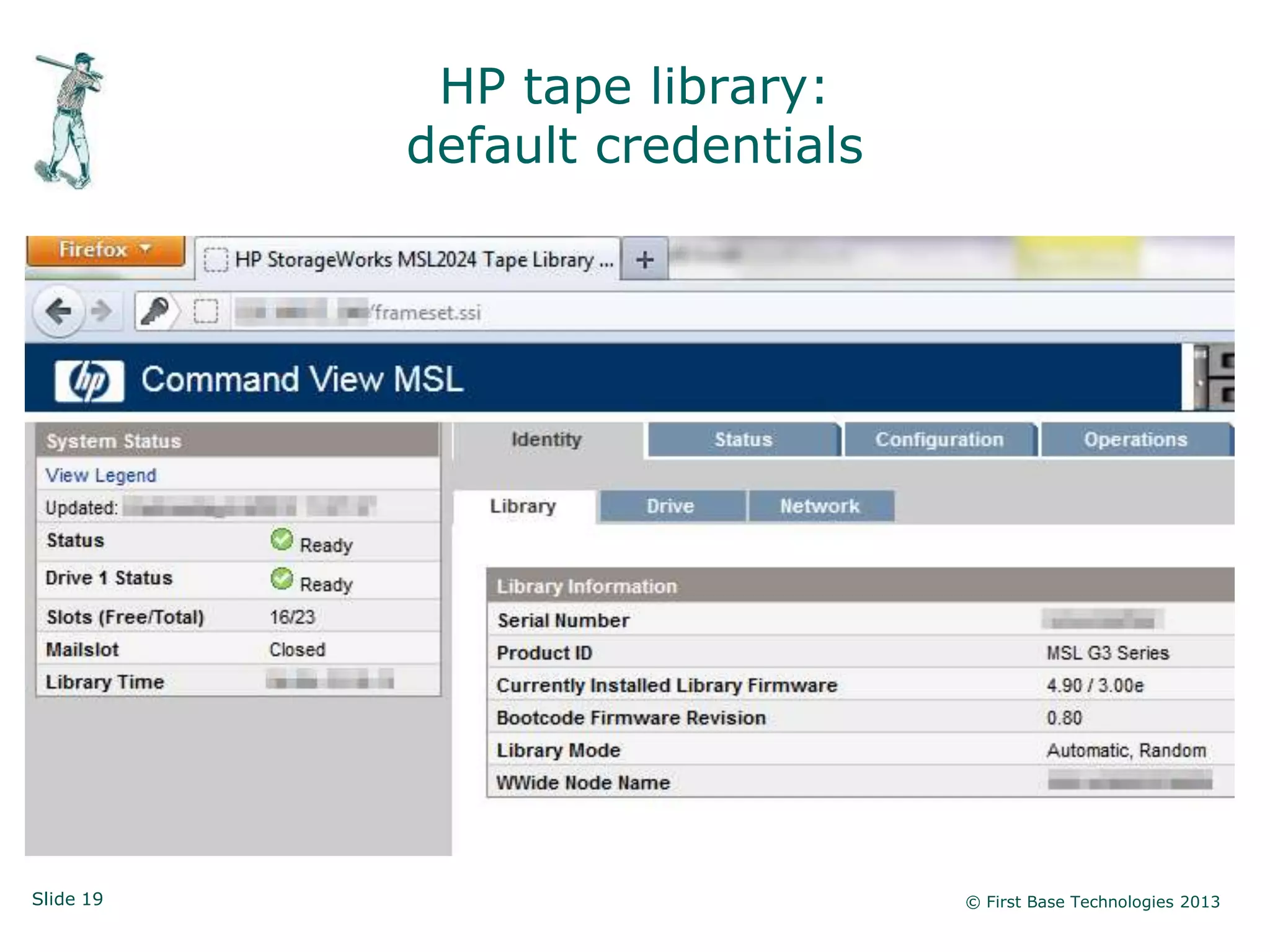
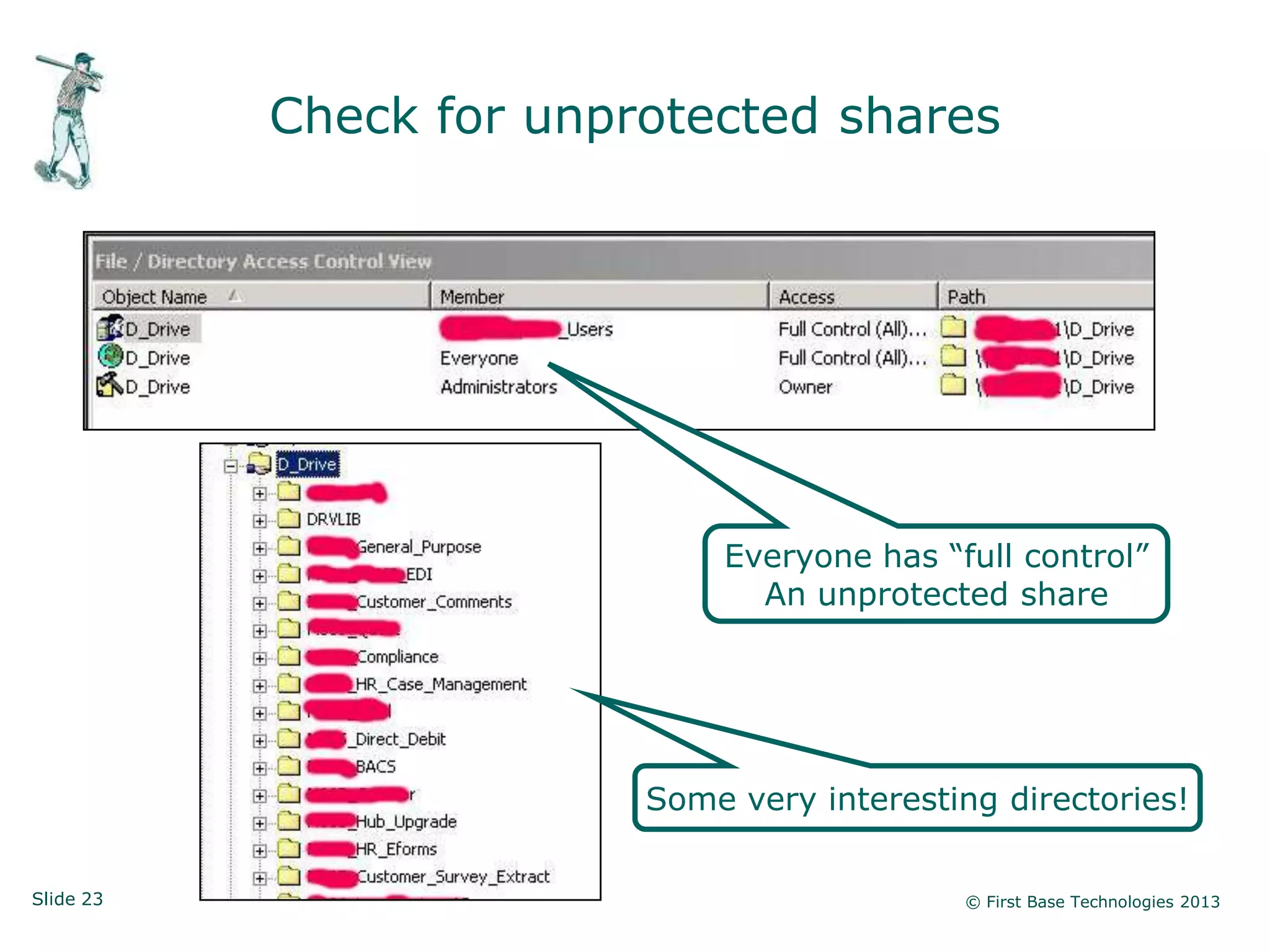
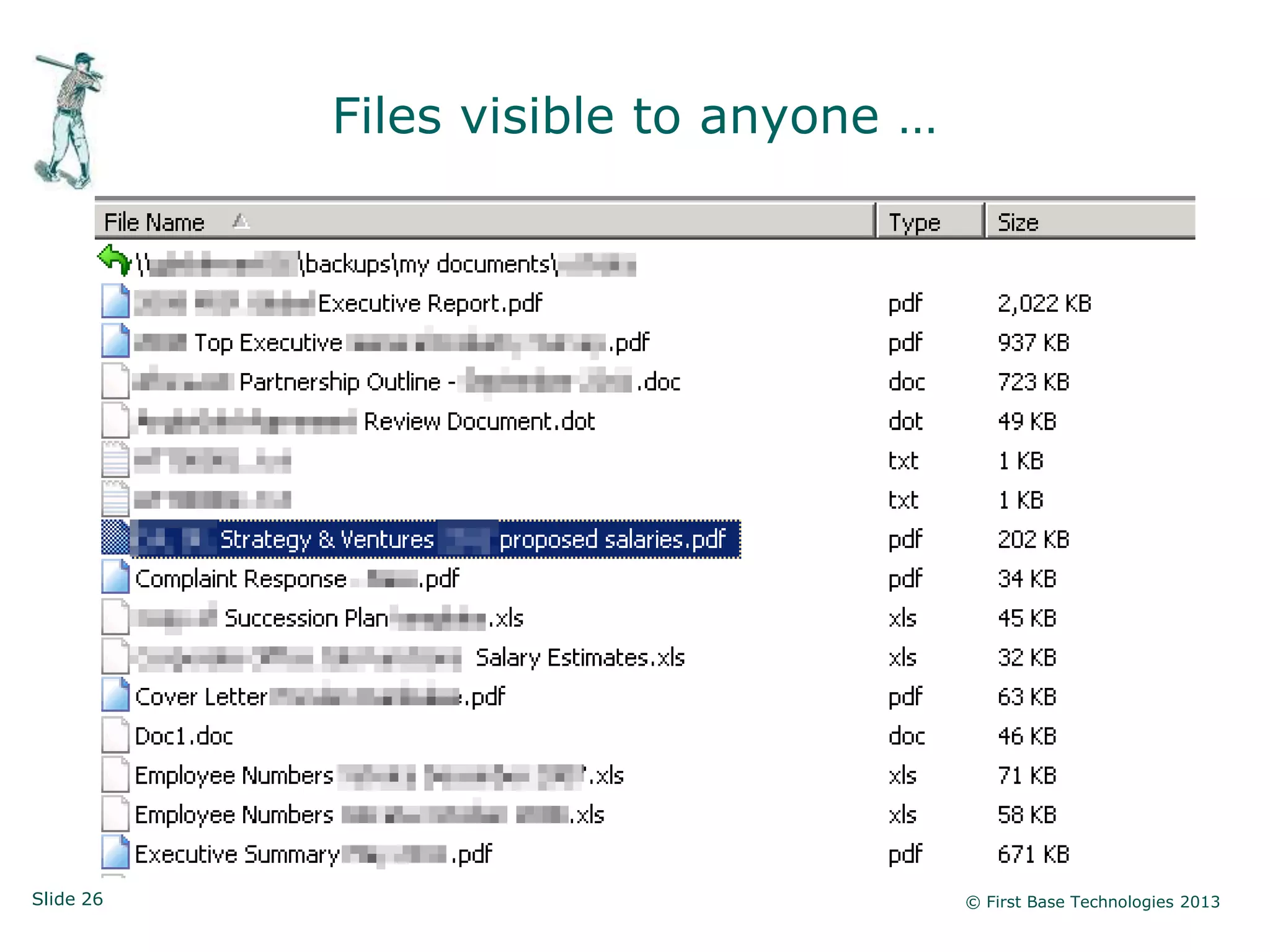
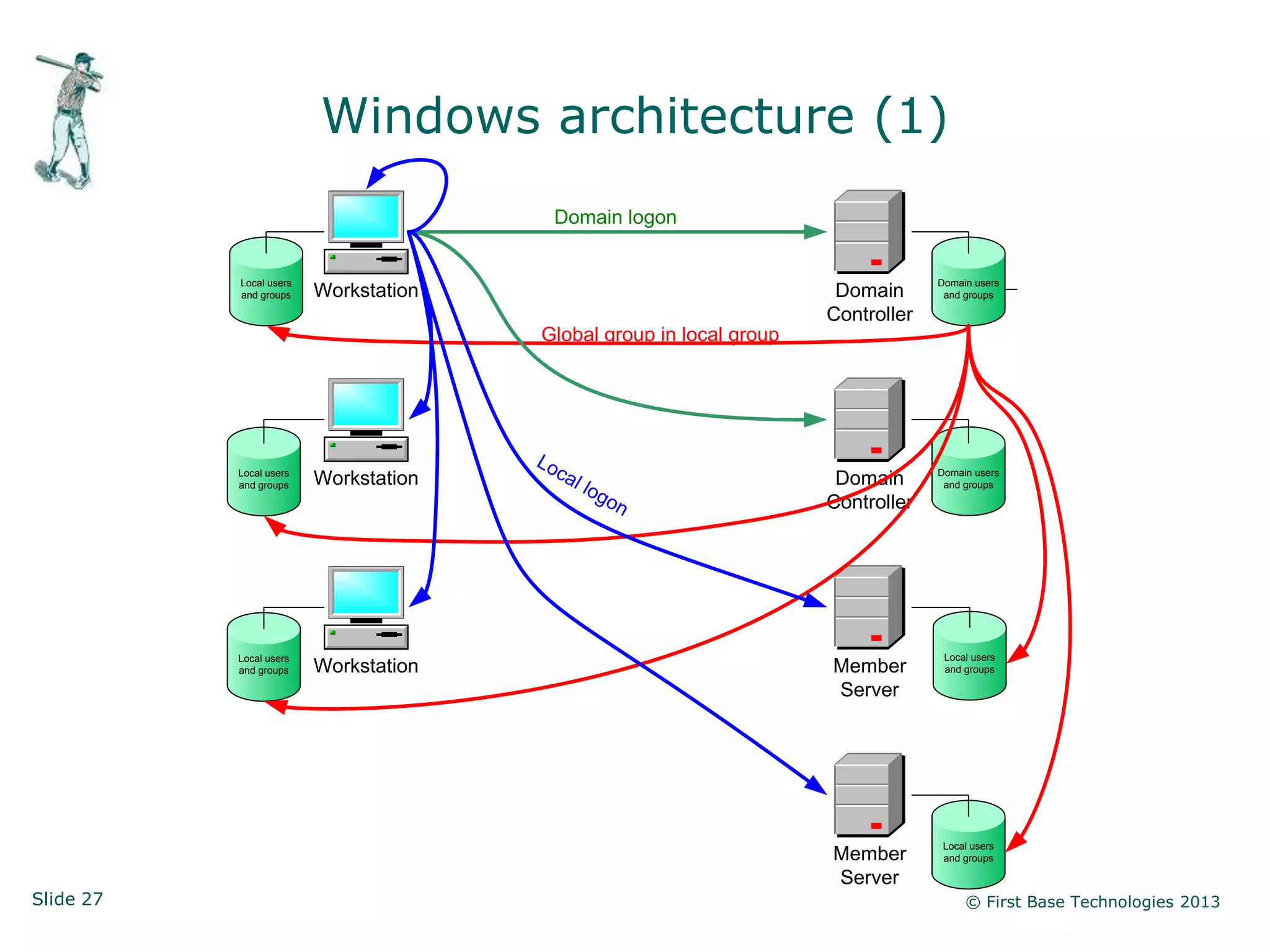
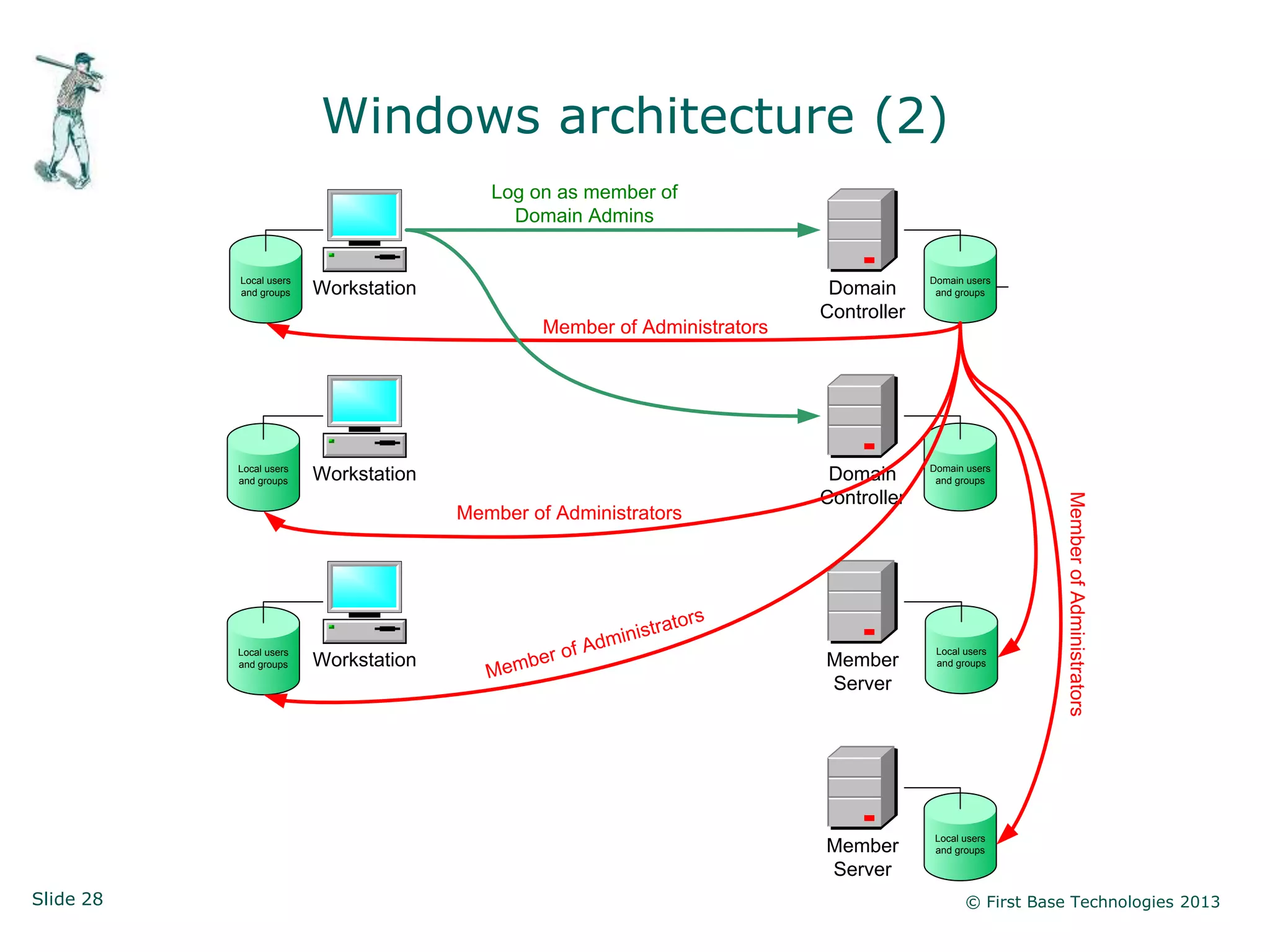
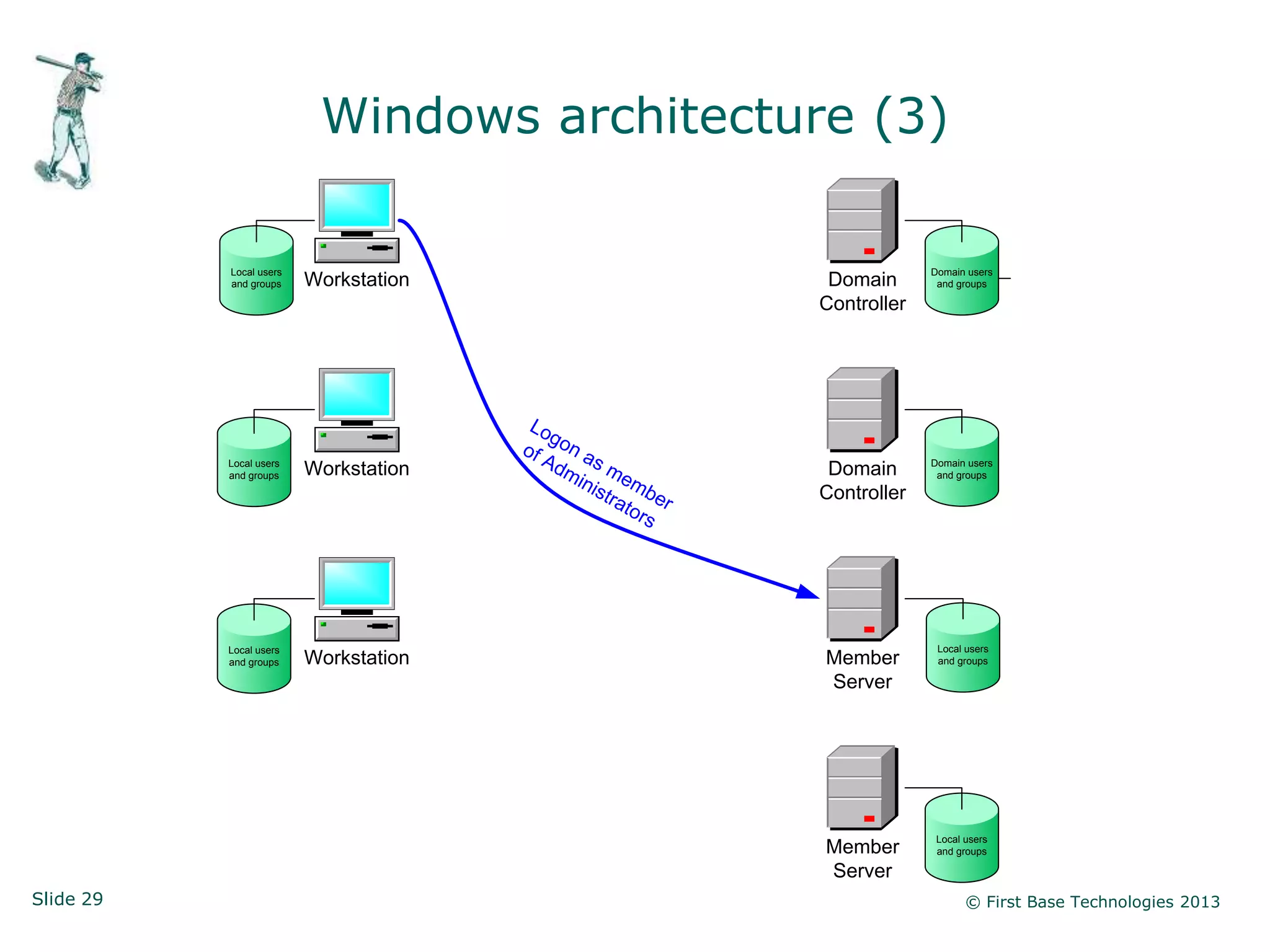
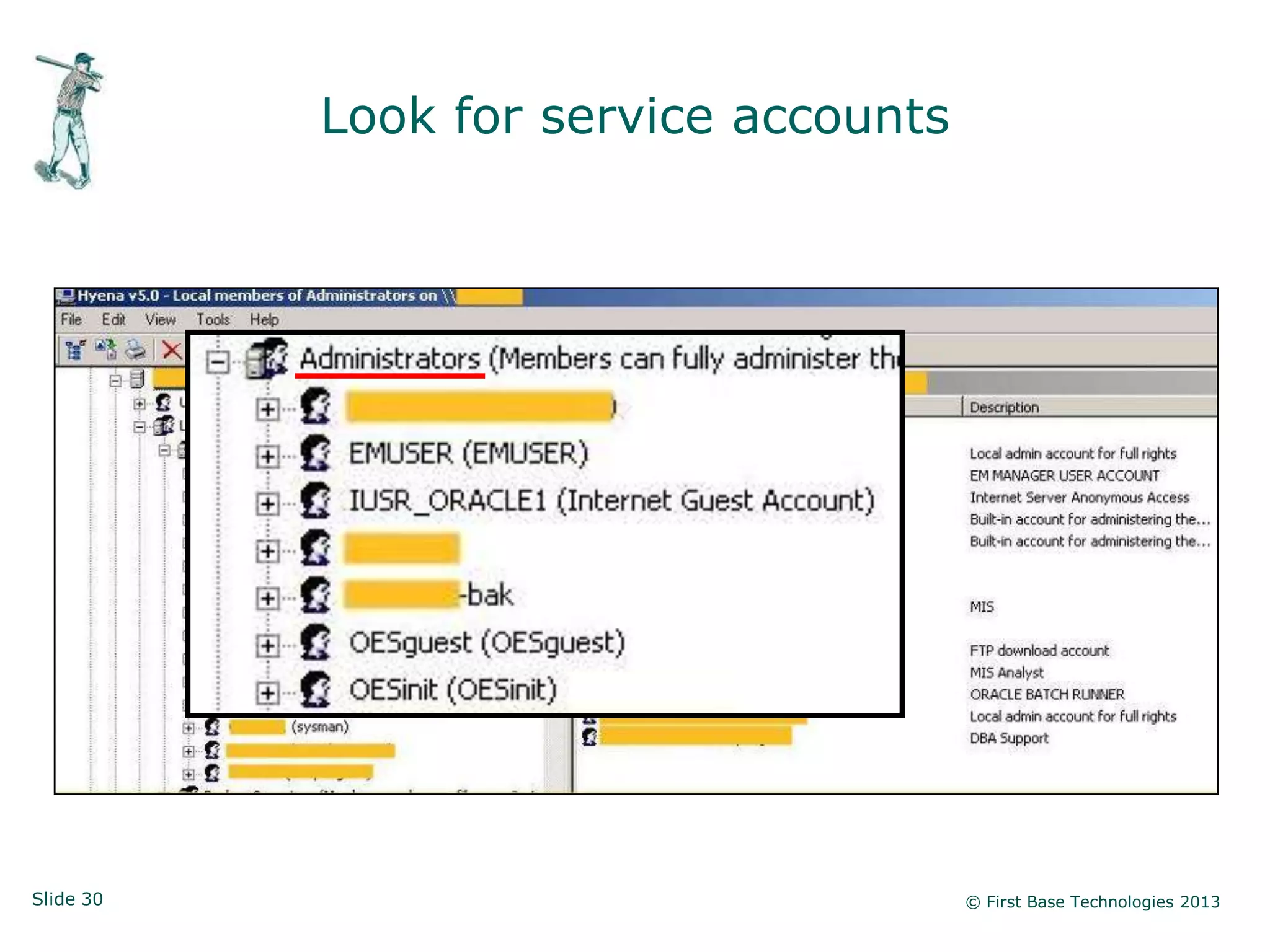
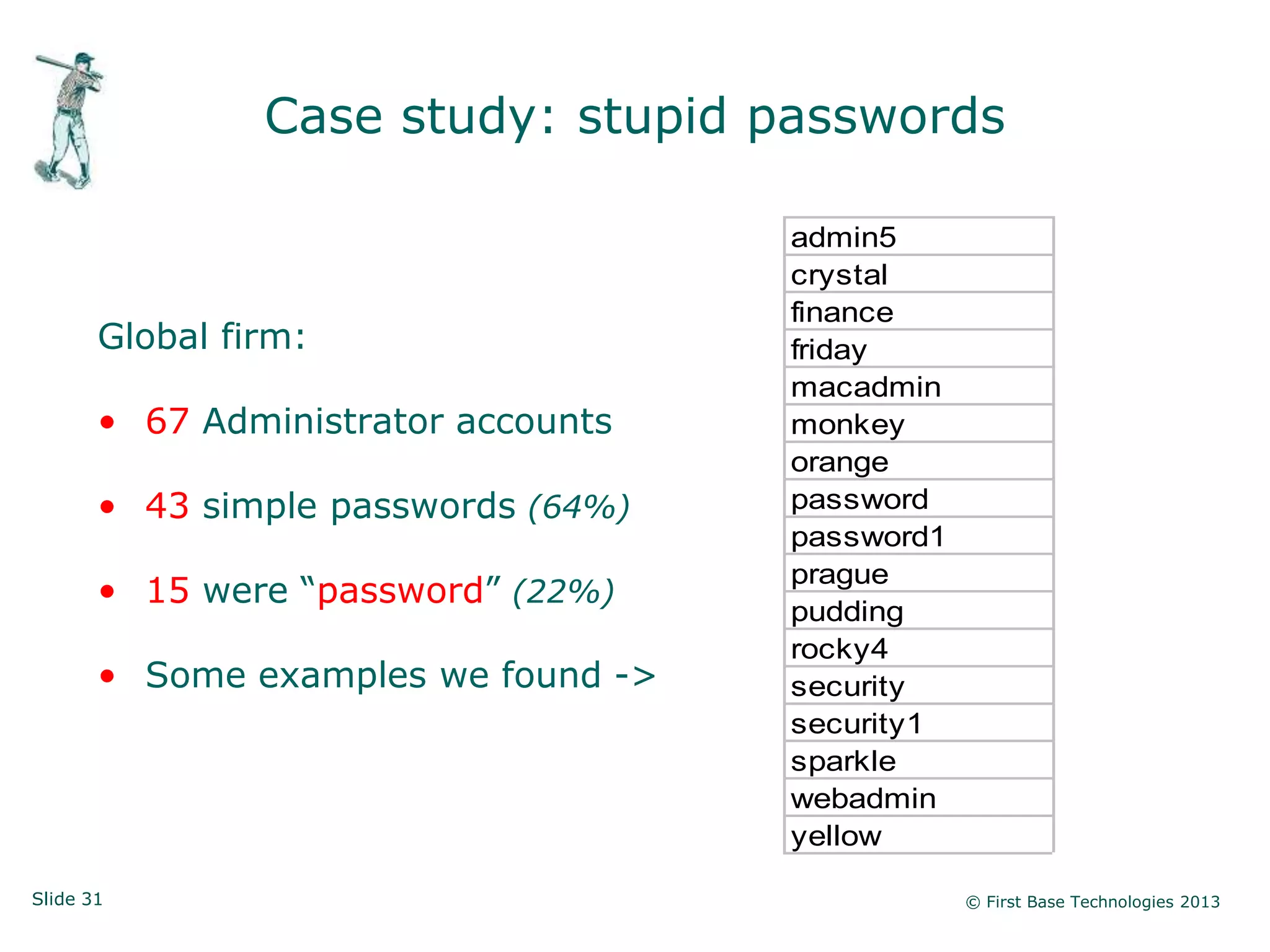
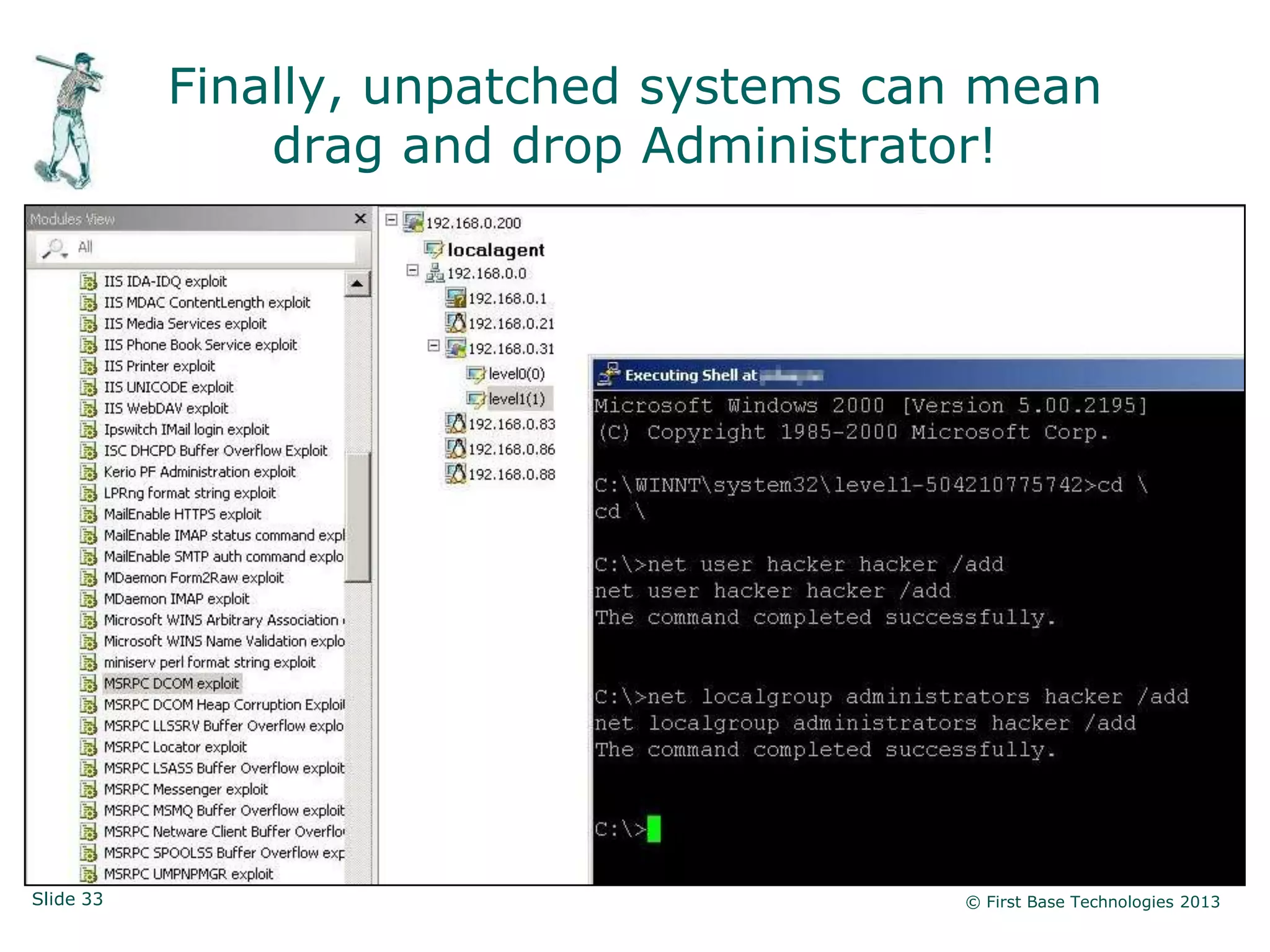
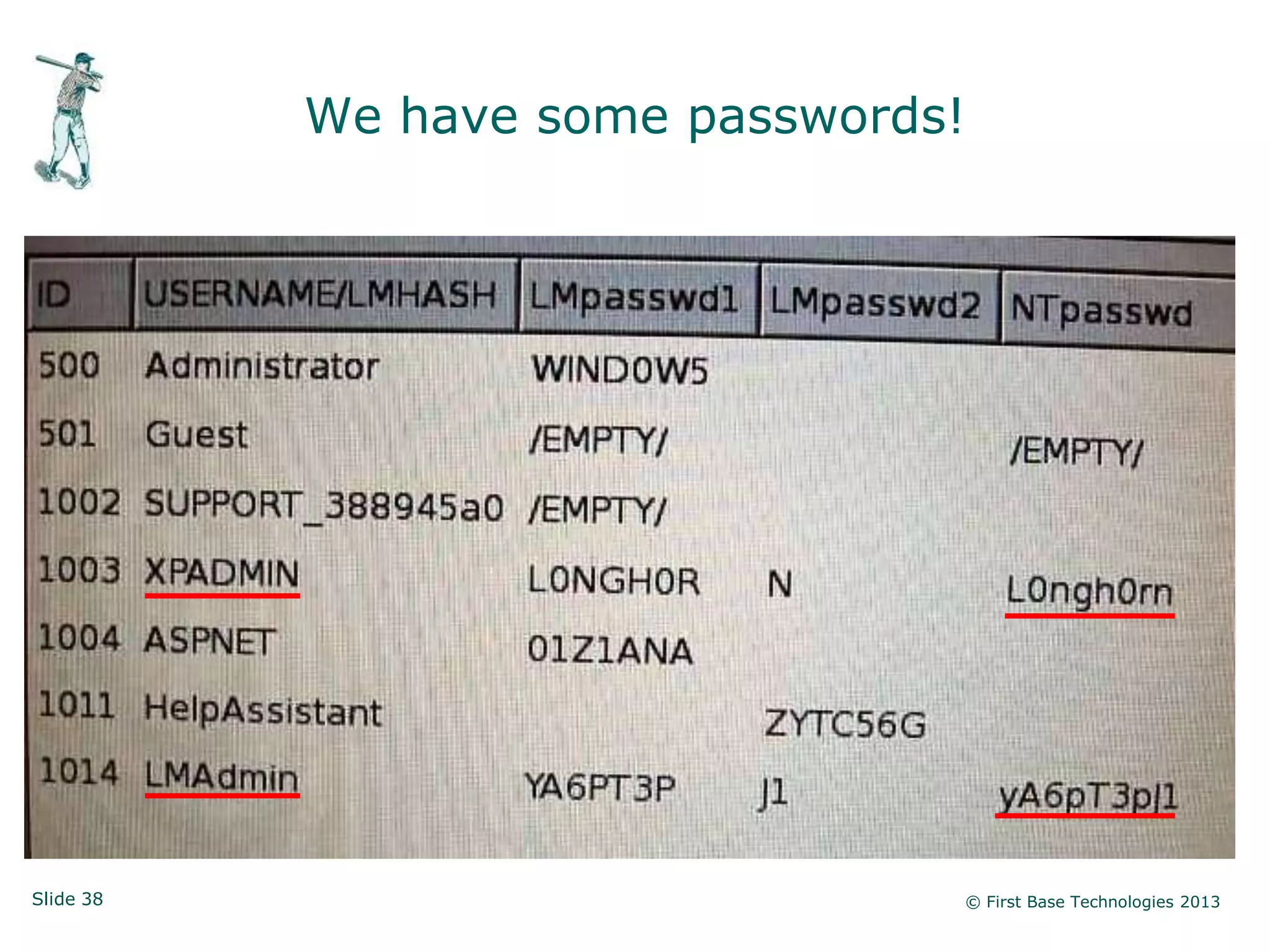
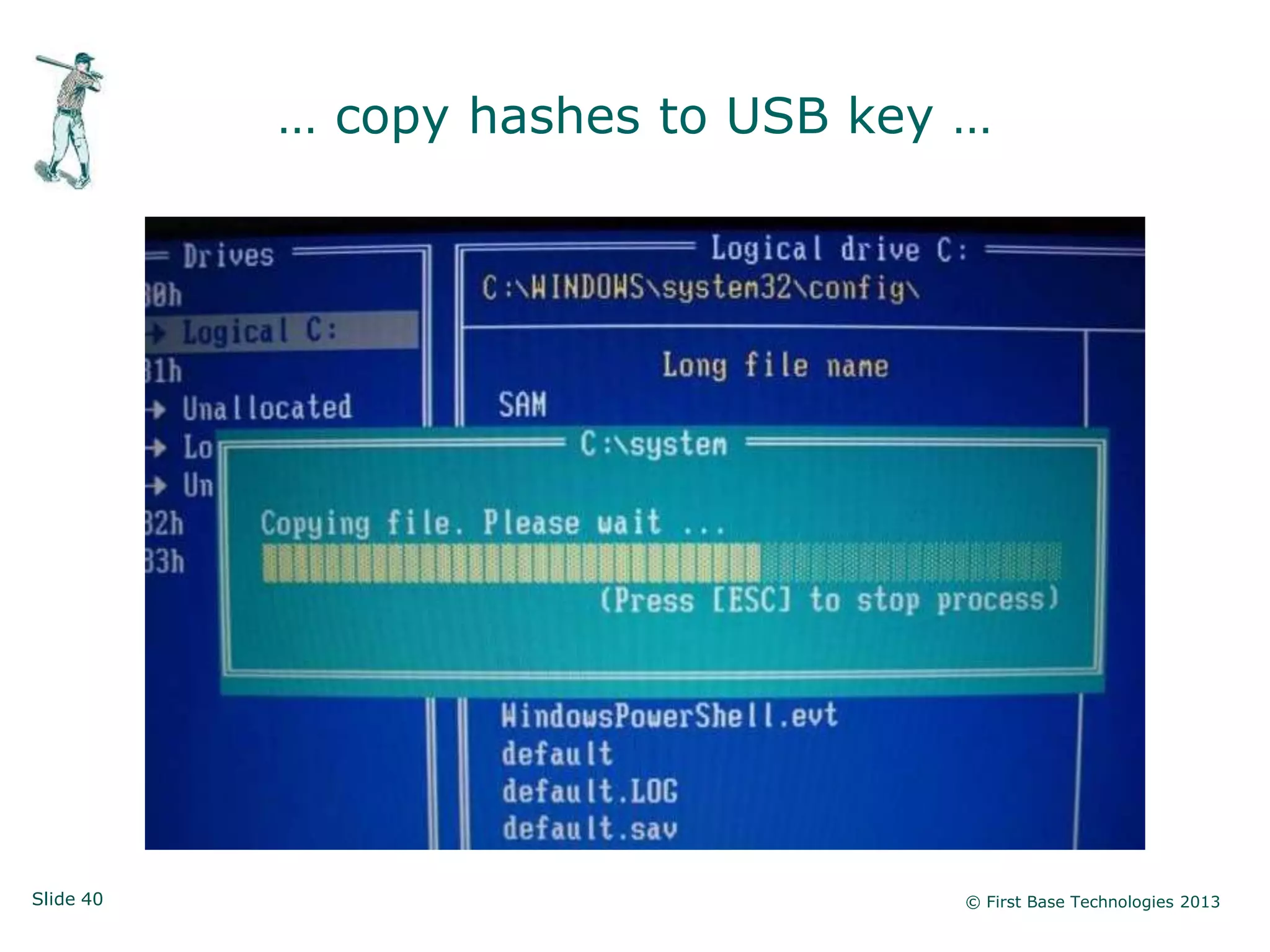
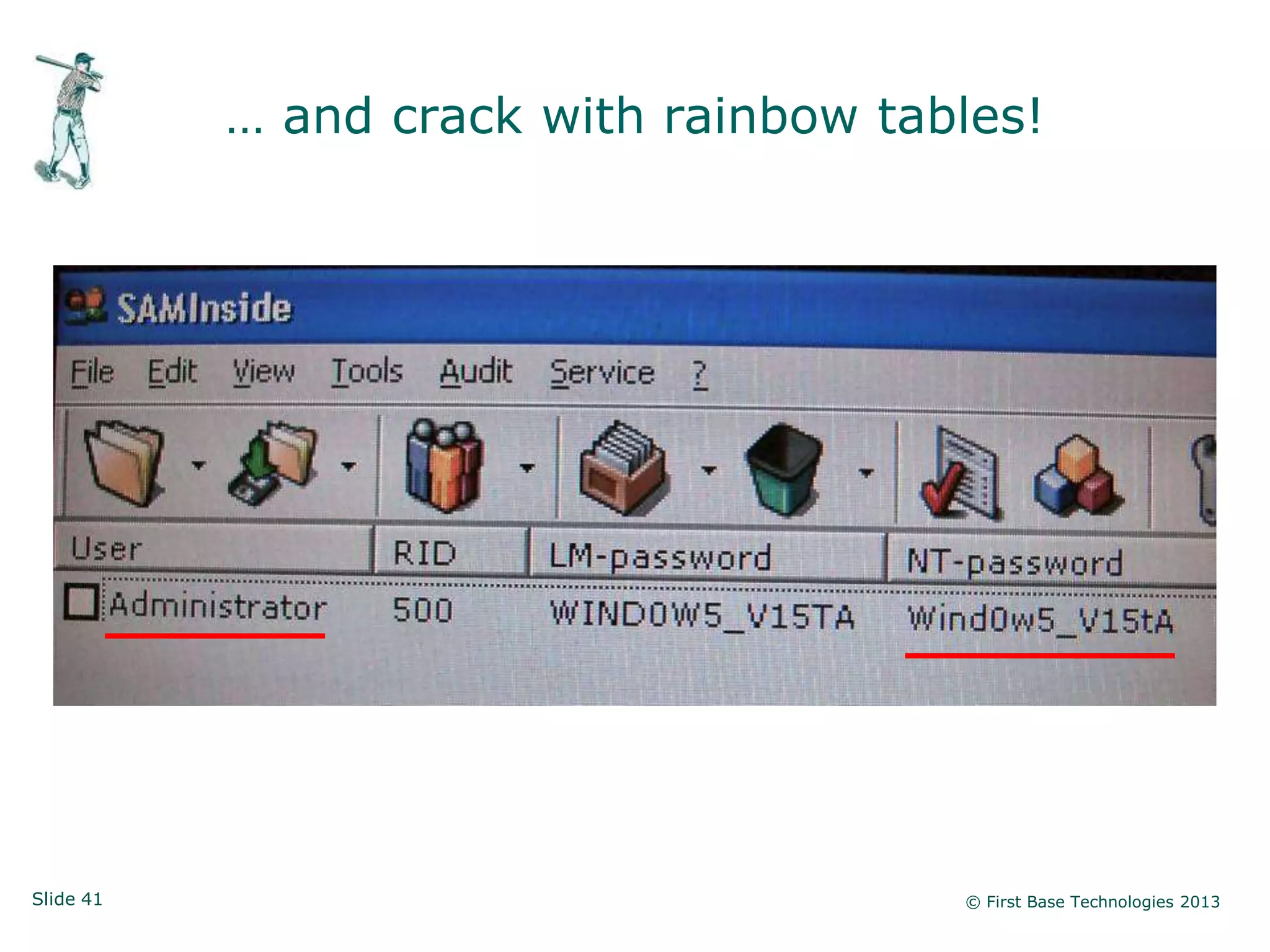
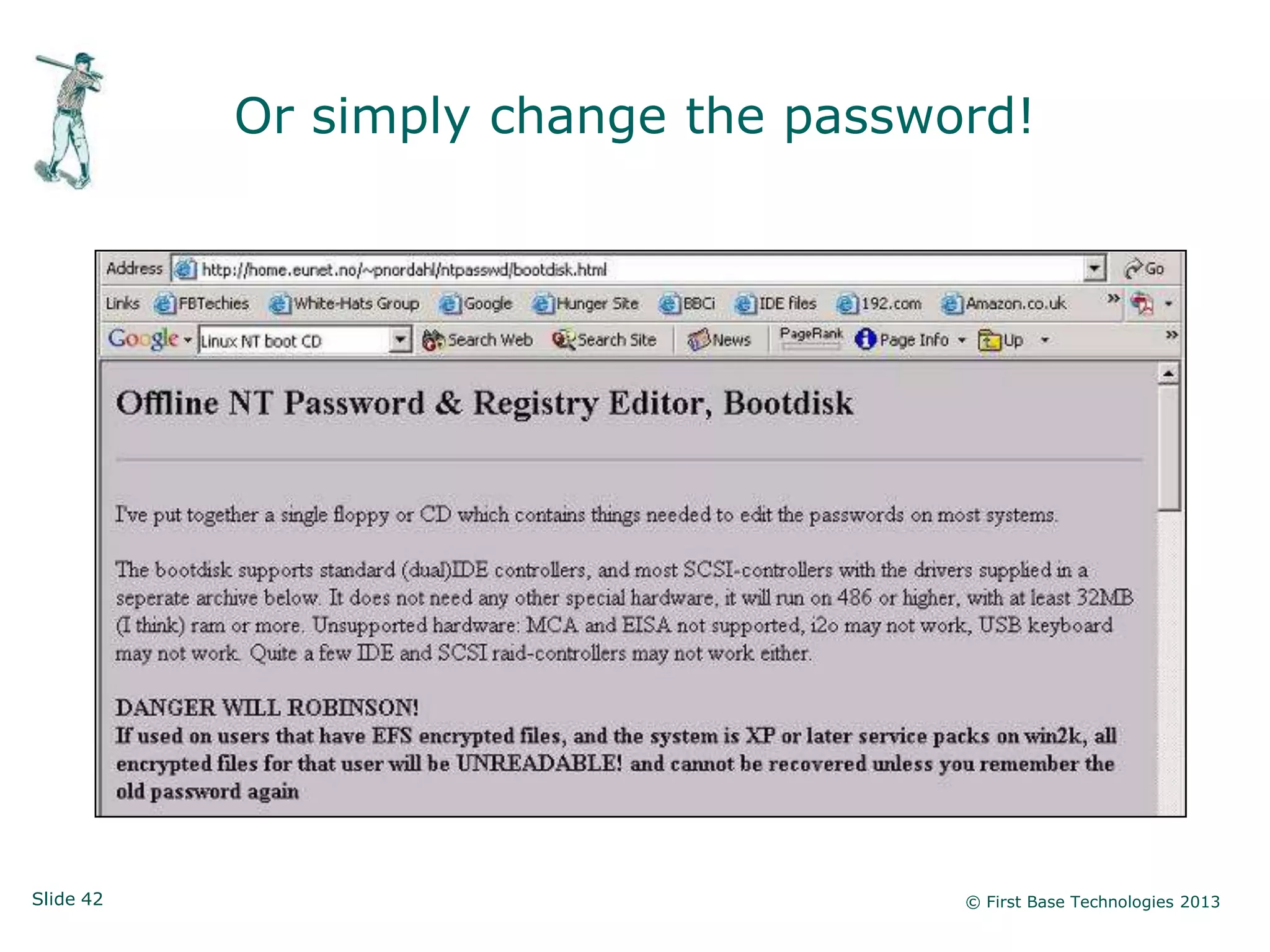
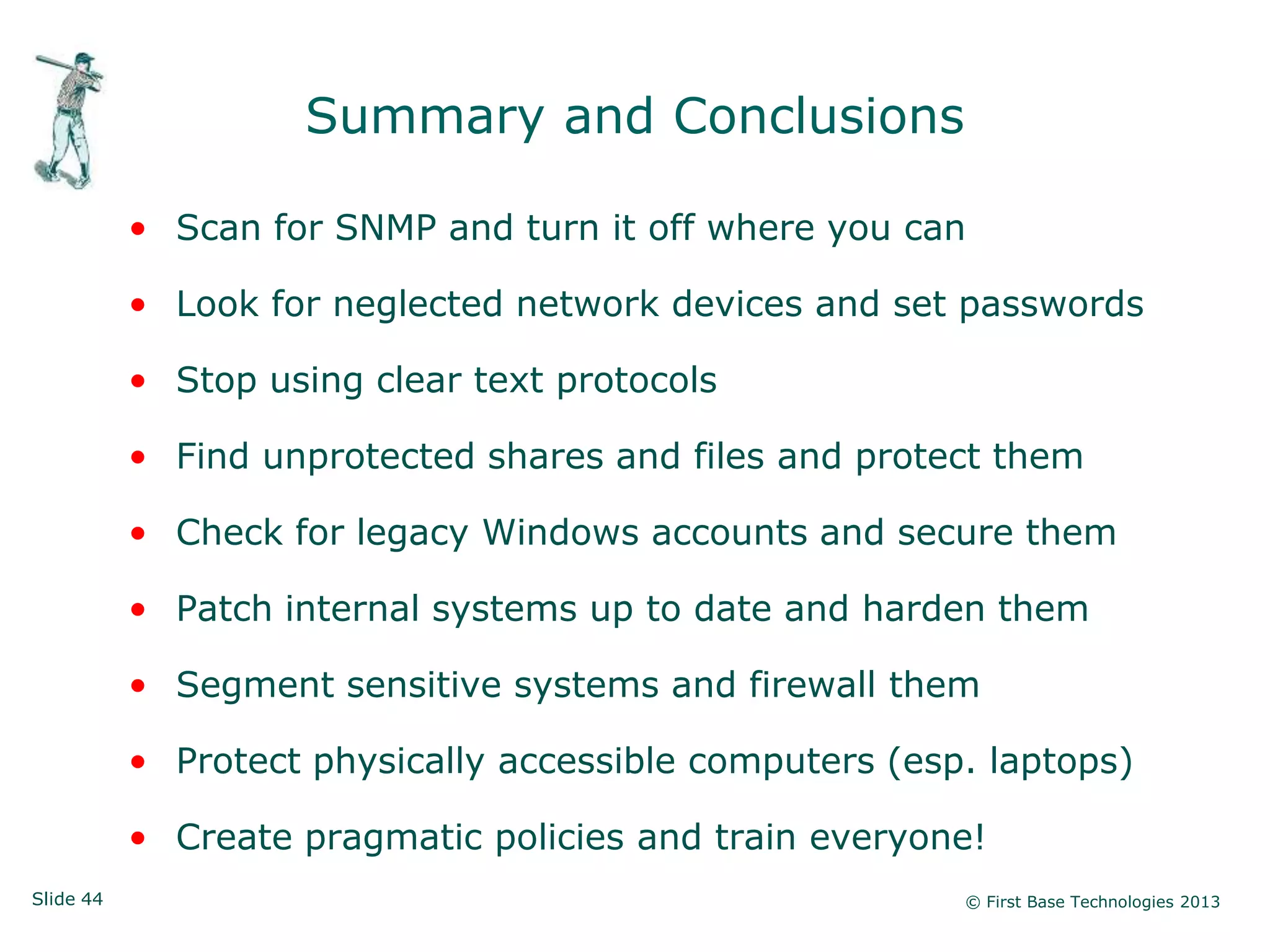
The document presents an overview of network vulnerabilities from an ethical hacker's perspective, emphasizing the risks associated with protocols like SNMP and the common misuse of default access credentials across network devices. It discusses various hacking techniques related to Windows systems, including password weaknesses and unprotected shares, and emphasizes the importance of regular security practices to safeguard against these threats. The conclusion highlights actionable strategies for improving network security, such as disabling unnecessary protocols, enforcing strong passwords, and providing thorough training.