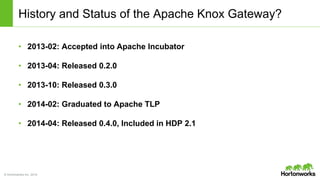
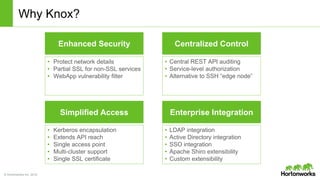
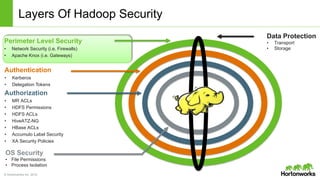
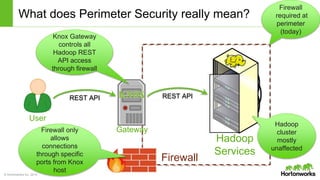
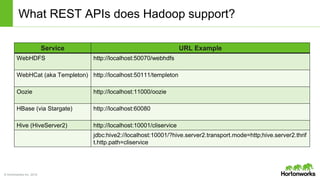
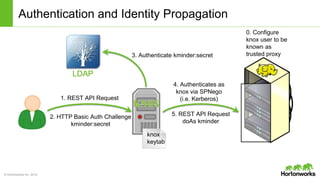
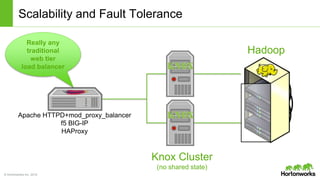
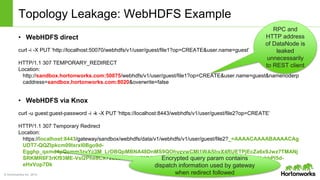
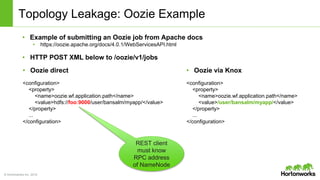
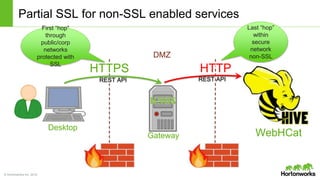
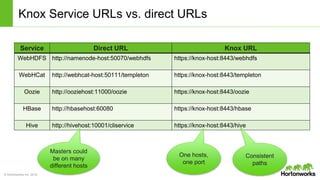
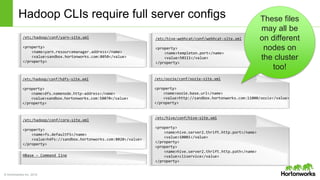
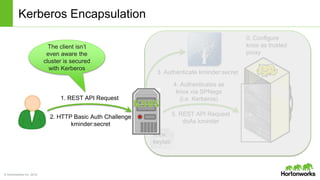
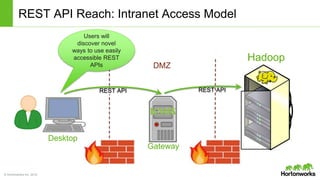
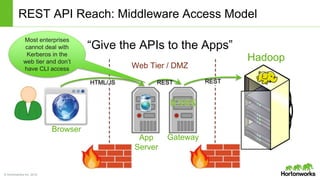
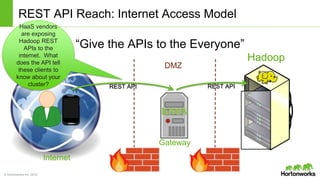
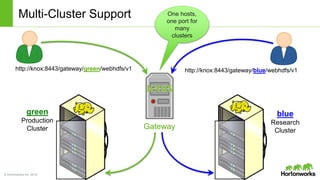
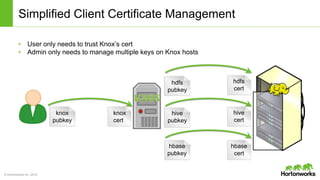
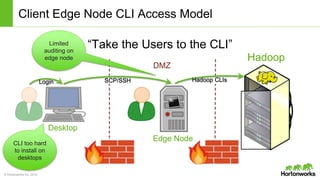
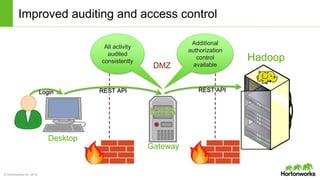
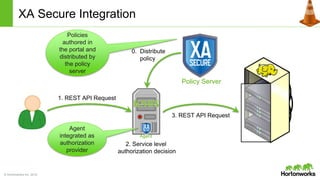
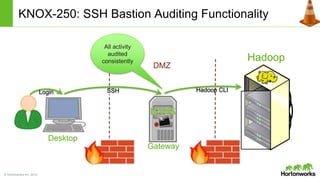
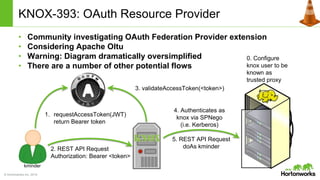
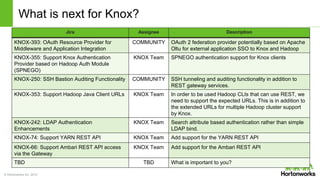
The Apache Knox Gateway is an extensible reverse proxy framework for securely exposing REST APIs and HTTP-based services at a perimeter. It provides out of the box support for several common Hadoop services, integration with enterprise authentication systems, and other useful features. Knox is not an alternative to Kerberos for core Hadoop authentication or a channel for high-volume data ingest/export. It has graduated from the Apache incubator and is included in Hortonworks Data Platform releases to simplify access, provide centralized control, and enable enterprise integration of Hadoop services.