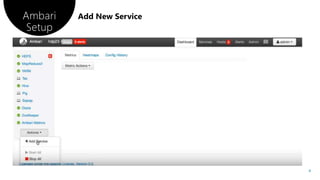
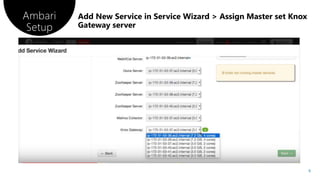
There are two ways to set up Apache Knox on a server: using Ambari or manually. The document then provides steps for configuring Knox using Ambari, including entering a master secret password and restarting services. It also provides commands for testing HDFS and Hive access through Knox by curling endpoints or using Beeline.





![Test HDFS using KNOX
• Open in browser 'https://<KnoxHostAddress>:<KnoxPort Default
8443>/gateway/<ClusterName can find on the top left of Ambari
Logo>/webhdfs/v1/?op=LISTSTATUS
• User credentials “guest” , “guest-password”
• Output
{"FileStatuses":{"FileStatus":[]}}](https://image.slidesharecdn.com/apacheknoxsetupandhiveandhdfsuse-170720131129/85/Apache-Knox-setup-and-hive-and-hdfs-Access-using-KNOX-9-320.jpg)