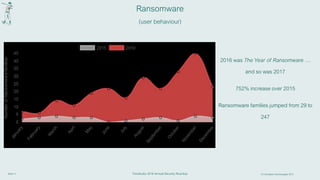
The document discusses the evolving cyber threat landscape and emphasizes the necessity of cybersecurity resilience due to increasing vulnerabilities and sophisticated attacks. Key themes include the importance of preparation, detection, response, and recovery strategies against cyber threats, with a focus on training personnel to recognize risks. Additionally, it advocates for adapting security measures to prioritize detection and response rather than solely prevention.