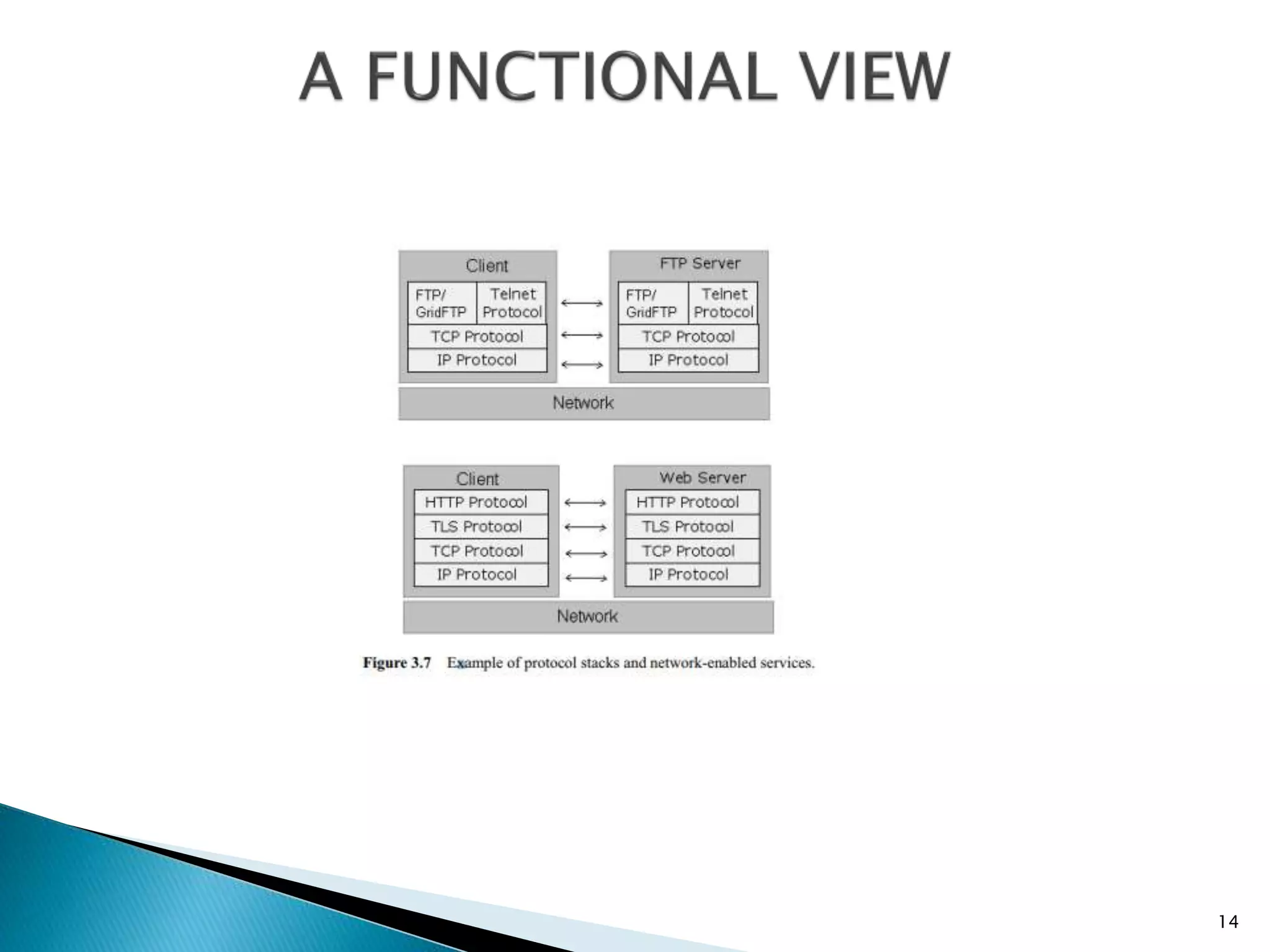
The document discusses the major functional components of a grid computing system. It describes 12 functional blocks: 1) resource, 2) portal/user interface, 3) user security, 4) node security, 5) broker and directory, 6) scheduler, 7) data management, 8) job and resource management, 9) user/application submission, 10) resources, 11) protocols to interconnect blocks, and 12) examples of protocol stacks. Each block performs an essential role in the grid system such as providing user access, resource scheduling, security, and data management. Protocols are also needed to allow communication between the different functional blocks.