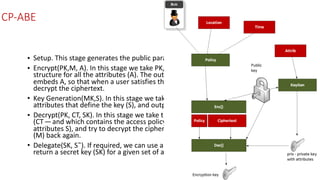
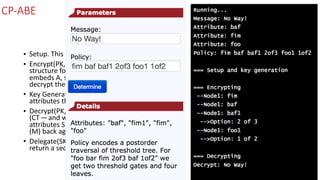
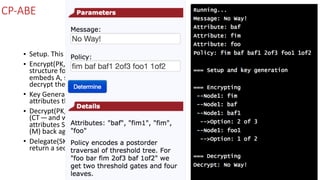
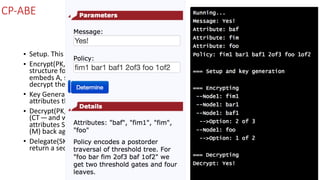
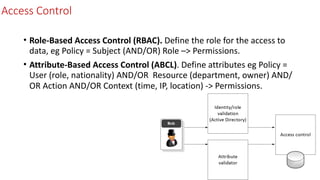
The document discusses attribute-based encryption (ABE) techniques for access control of encrypted data. It describes ciphertext-policy attribute-based encryption (CP-ABE) which allows a user to decrypt a ciphertext if they possess a set of attributes that satisfy the ciphertext's access policy. The CP-ABE scheme involves four algorithms: Setup generates public and master keys, Encrypt generates a ciphertext based on an access policy and attributes, KeyGeneration generates a private key for a set of attributes, and Decrypt decrypts a ciphertext if a user's attributes satisfy the access policy.

![Finite Fields with Prime
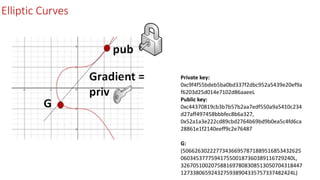
• A: 0
• B: 7
• Prime number: 38047
• Elliptic curve is: y2=x3+ 7
• Finding the first 20 points
• (83, 33) (180, 104) (296, 156) (491, 81) (896,
81) (905, 155) (1307, 86) (1563, 41) (1570,
136) (1857, 56) (1904, 25) (2004, 119)
(2011, 170) (2209, 75) (2219, 90) (2447, 51)
(2767, 40) (2843, 170) (3138, 29) (3485, 33)
(3713, 109)
• [Link]](https://image.slidesharecdn.com/cpabe-190102221512/85/Attribute-Based-Encryption-5-320.jpg)