Embed presentation
Download as PDF, PPTX



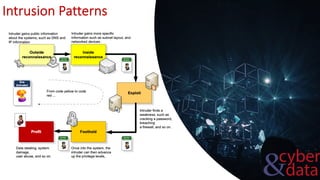
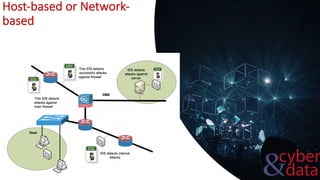
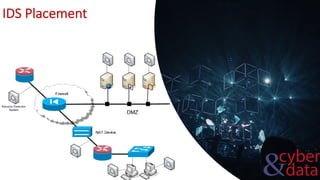

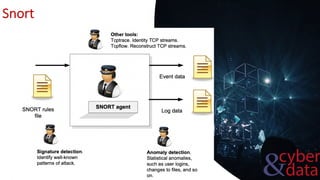
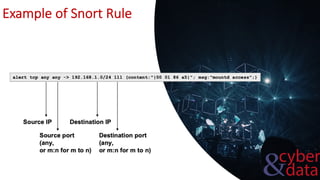
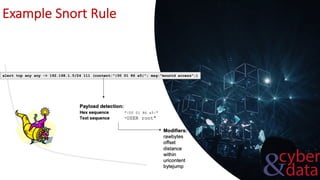



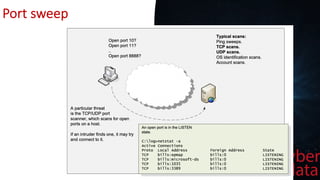
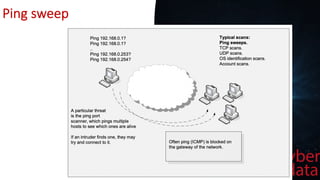
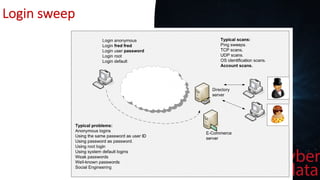
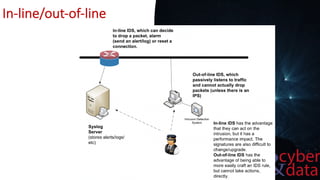


This document discusses intrusion detection systems, including common attack patterns like port, ping, and login sweeps. It outlines Snort as an example network-based intrusion detection system and provides Snort rule examples. Different types of intrusion detection systems are also covered, along with considerations for host-based versus network-based placement.

















