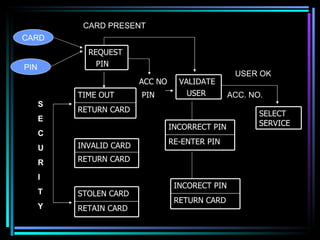
The document discusses the security features of ATM systems. It covers how ATMs work by connecting to a host computer for transaction authorization. Card readers, PIN entry, and crypto-processors securely authenticate users. Additional security measures include transaction limits, invalidating stolen cards, and encrypting transmitted data. Databases and network security aim to protect confidential user information and ensure integrity of financial transactions processed through the ATM network.