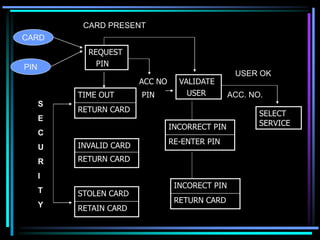
The document discusses the security features of ATM systems. It covers how ATMs work by requiring customers to insert their card and enter a PIN for authentication. It then describes the various security mechanisms in place, including using time outs, invalidating cards, and retaining stolen cards. The document also outlines the network, database, hardware/software security measures to protect confidentiality, integrity, and accountability of transactions. Overall, the ATM system aims to securely authenticate users and protect their information and money.