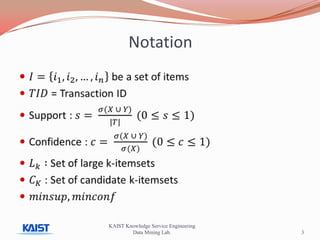
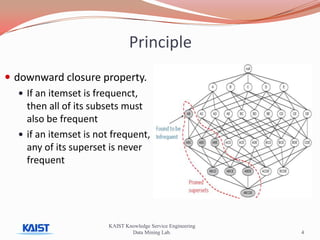
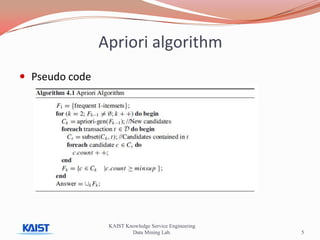
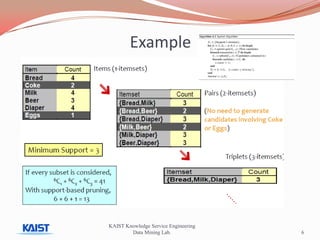
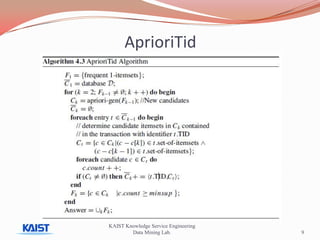
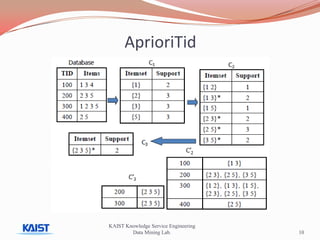
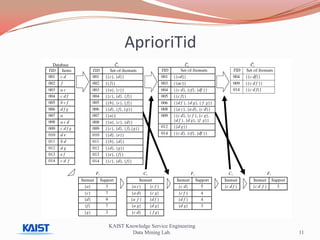
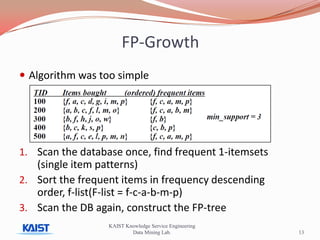
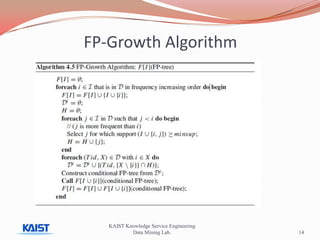
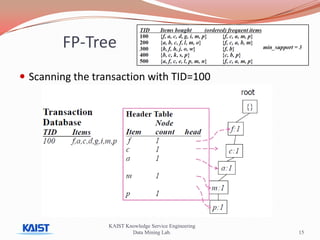
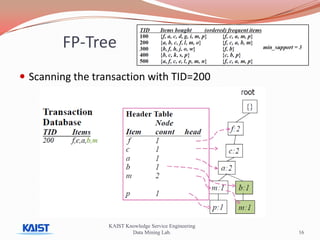
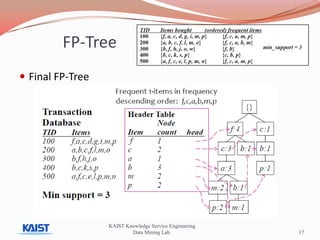
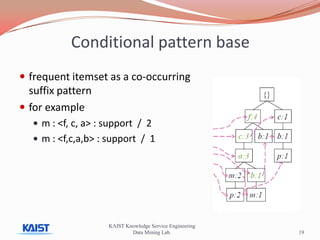
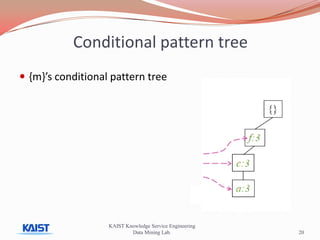
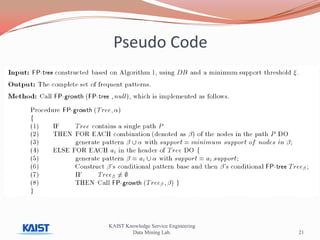
This document discusses frequent pattern mining algorithms. It describes the Apriori, AprioriTid, and FP-Growth algorithms. The Apriori algorithm uses candidate generation and database scanning to find frequent itemsets. AprioriTid tracks transaction IDs to reduce scans. FP-Growth avoids candidate generation and multiple scans by building a frequent-pattern tree. It finds frequent patterns by mining the tree.