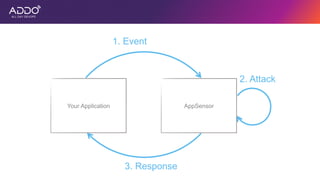
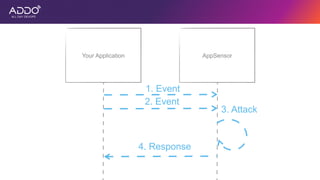
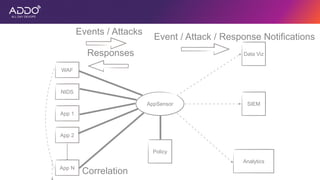
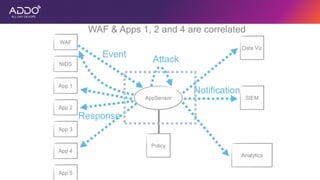
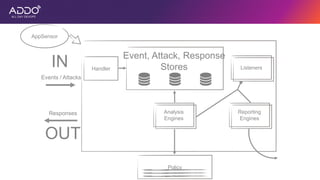
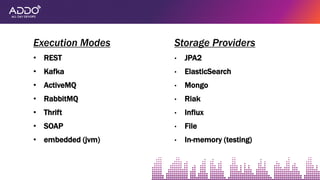
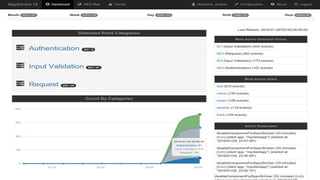
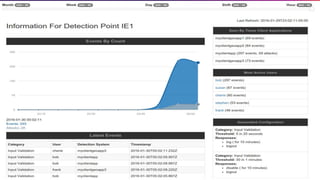
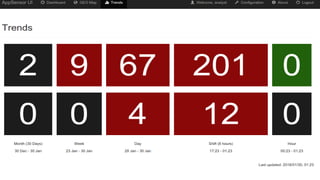
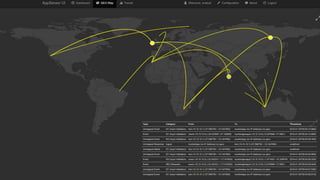
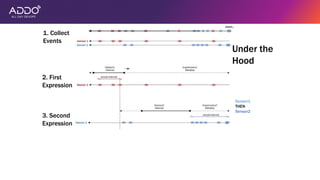
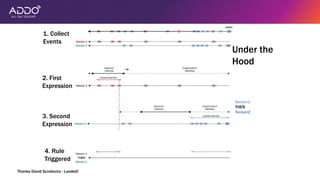
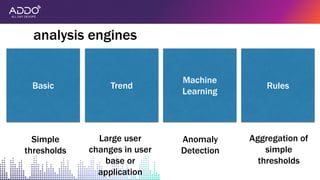
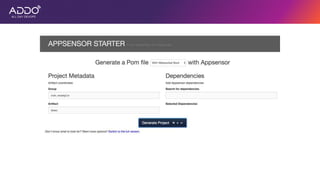
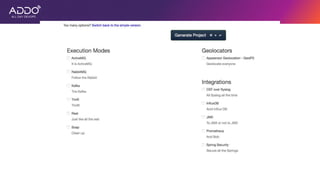
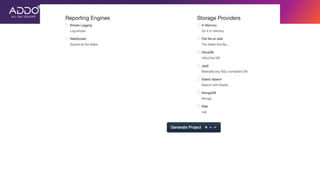
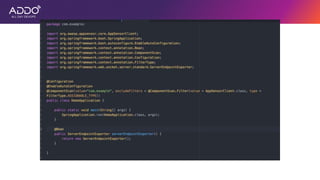
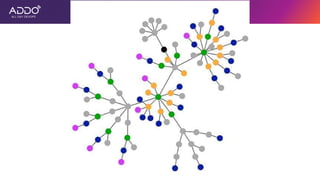
Modern applications can protect themselves from attackers by incorporating runtime monitoring capabilities. The OWASP AppSensor project aims to make intrusion detection primitives available within applications so they can detect attacks and automatically respond before an attacker succeeds. It works by collecting event data from applications and analyzing them for attacks using configurable rules. This allows applications to become self-defending by detecting and stopping attackers without needing manual responses.






![• servicemesh
• functional/rxprogramming
• cloudeverything
• nosql/CAPlight
• containers /orchestration
• bigdata
• streamprocessing
• microservices
~now dev
• configmanagement
• ci/cd
• beacons[usage,ads,errors,
performance]
• actors/csp
• cqrs/eventsourcing
• mobile
• JSEverywhere
1 .. * of [scale, speed, cloud, lack of environmental access]](https://image.slidesharecdn.com/addo2019appsensormelton-191106213633/85/AllDayDevOps-2019-AppSensor-7-320.jpg)

![• 3rd party libs (dep-check)
• bug bounties
• sast / dast evolve (ZAP)
• iast / rasp
• http security headers
• automatic encoding (JXT)
last ~5 years security
• *-monkey –NetflixOSS
• bdd-security/gauntlt
• ci/cd plugins
• 2fa
• osquery
1 .. * of [scale, speed, cloud, lack of environmental access]](https://image.slidesharecdn.com/addo2019appsensormelton-191106213633/85/AllDayDevOps-2019-AppSensor-9-320.jpg)



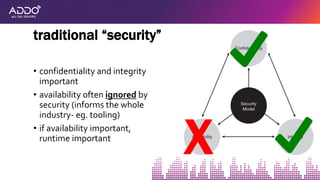


![• what do dev/qa do for functionality?
• test [unit, integration, system, manual, tools]
• what do attackers do for security?
• test [automated tools, manual]
catching defects](https://image.slidesharecdn.com/addo2019appsensormelton-191106213633/85/AllDayDevOps-2019-AppSensor-21-320.jpg)




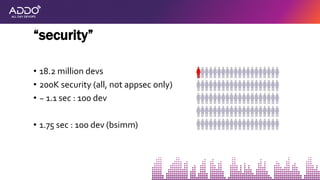





![having to deal with [scale, speed, cloud, lack
of environmental access]..
..this as of now incomplete transition..
..is a huge opportunity for improving security](https://image.slidesharecdn.com/addo2019appsensormelton-191106213633/85/AllDayDevOps-2019-AppSensor-37-320.jpg)