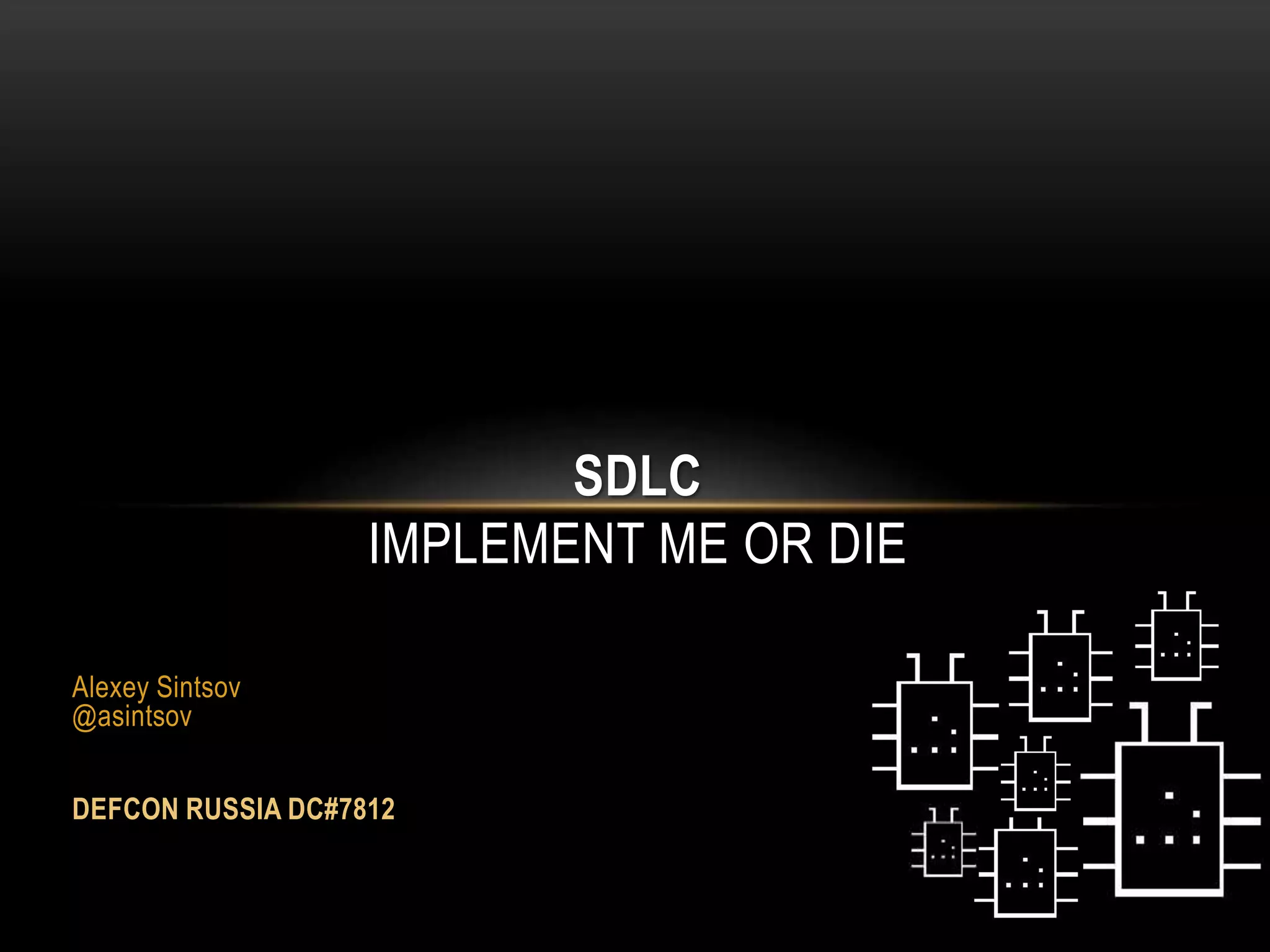
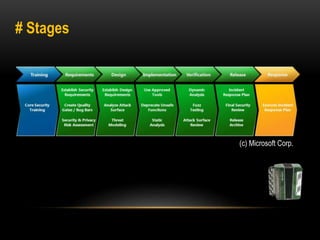
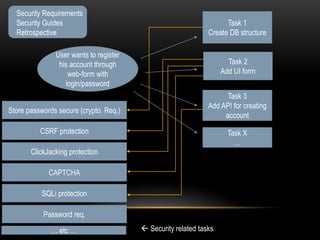
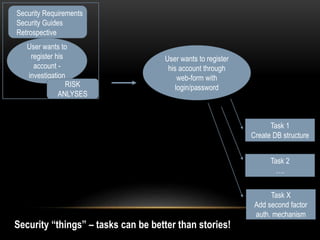
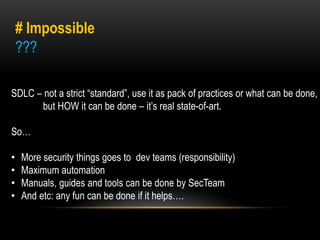
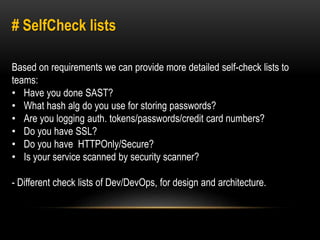
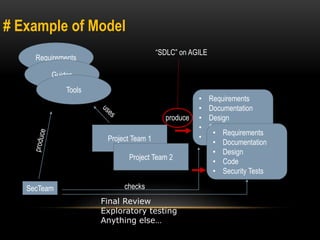
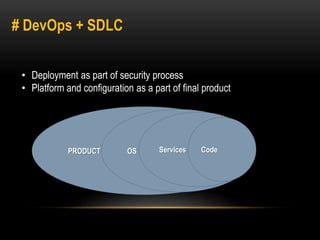
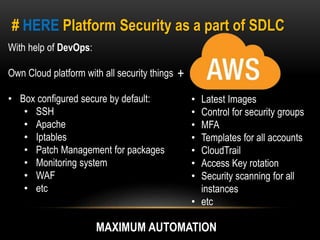
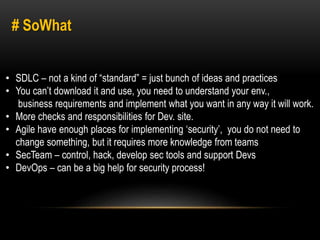
This document discusses implementing security best practices within an agile software development lifecycle (SDLC). It recommends that security requirements and testing be integrated into each sprint or iteration. The security team would provide requirements, guides, tools, and training to development teams. They would conduct a final security review before software releases. DevOps practices could help automate security processes and configuration of cloud platforms. The overall approach is to distribute security responsibilities to development teams with support from the centralized security team.