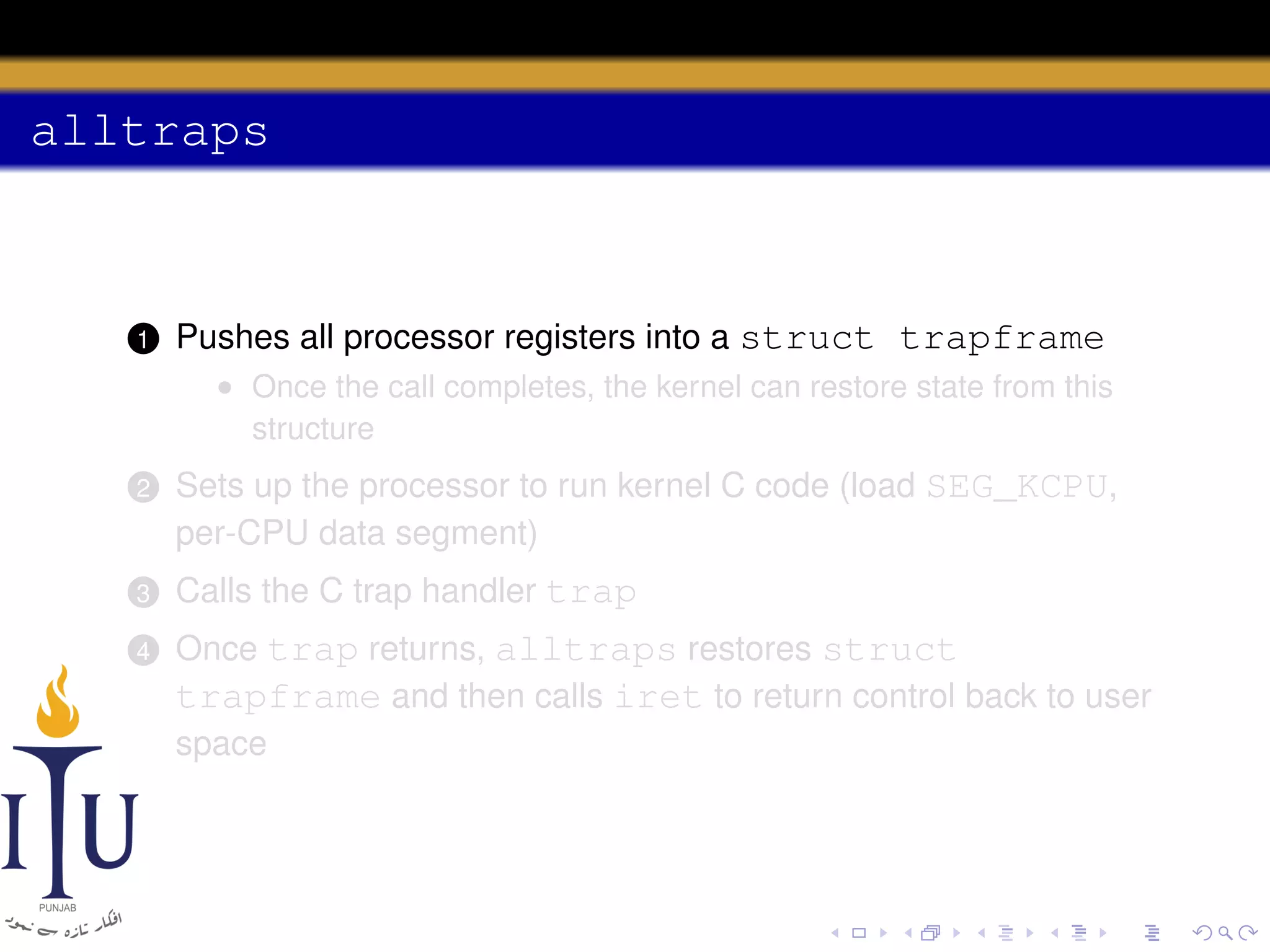
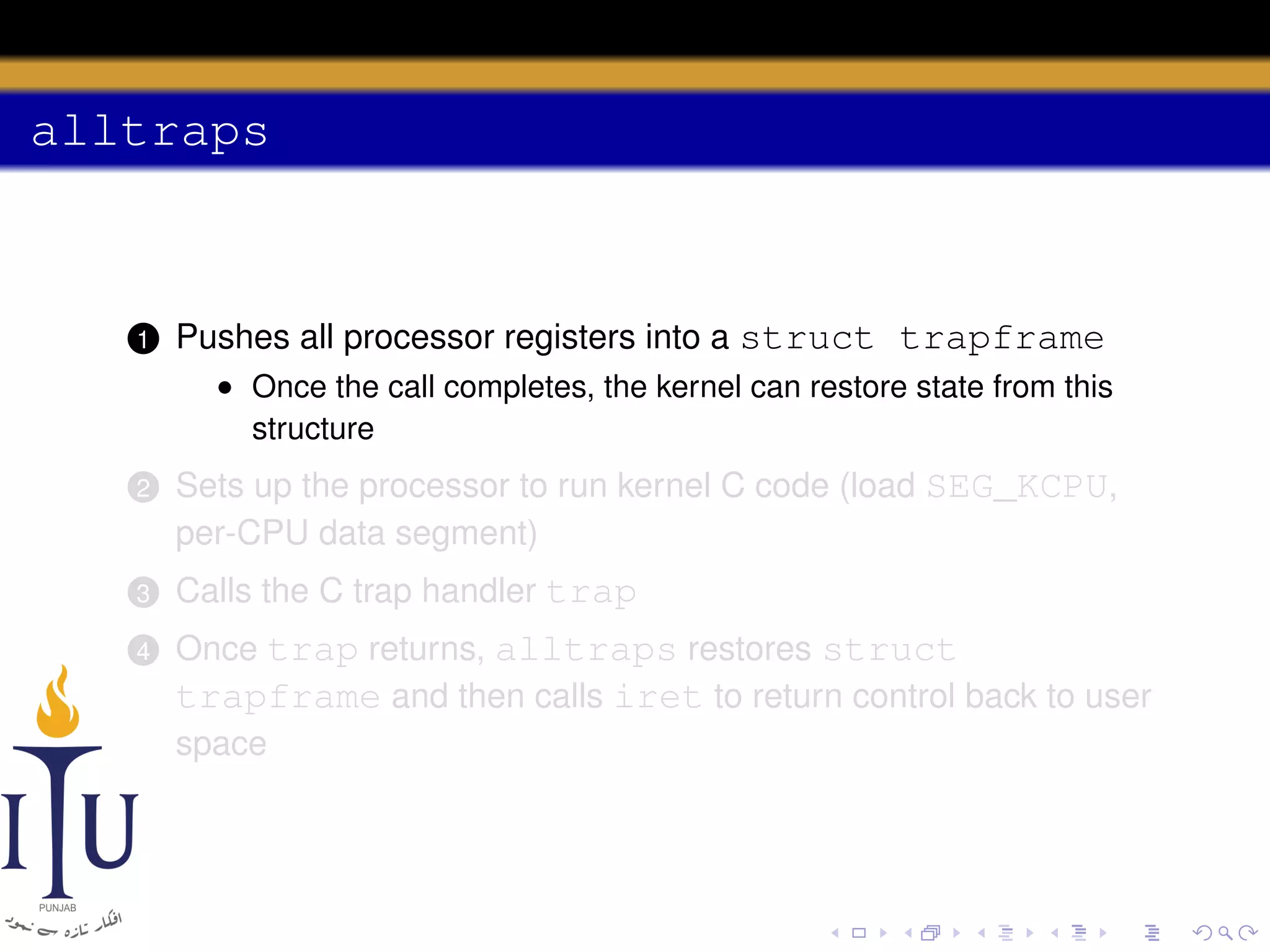
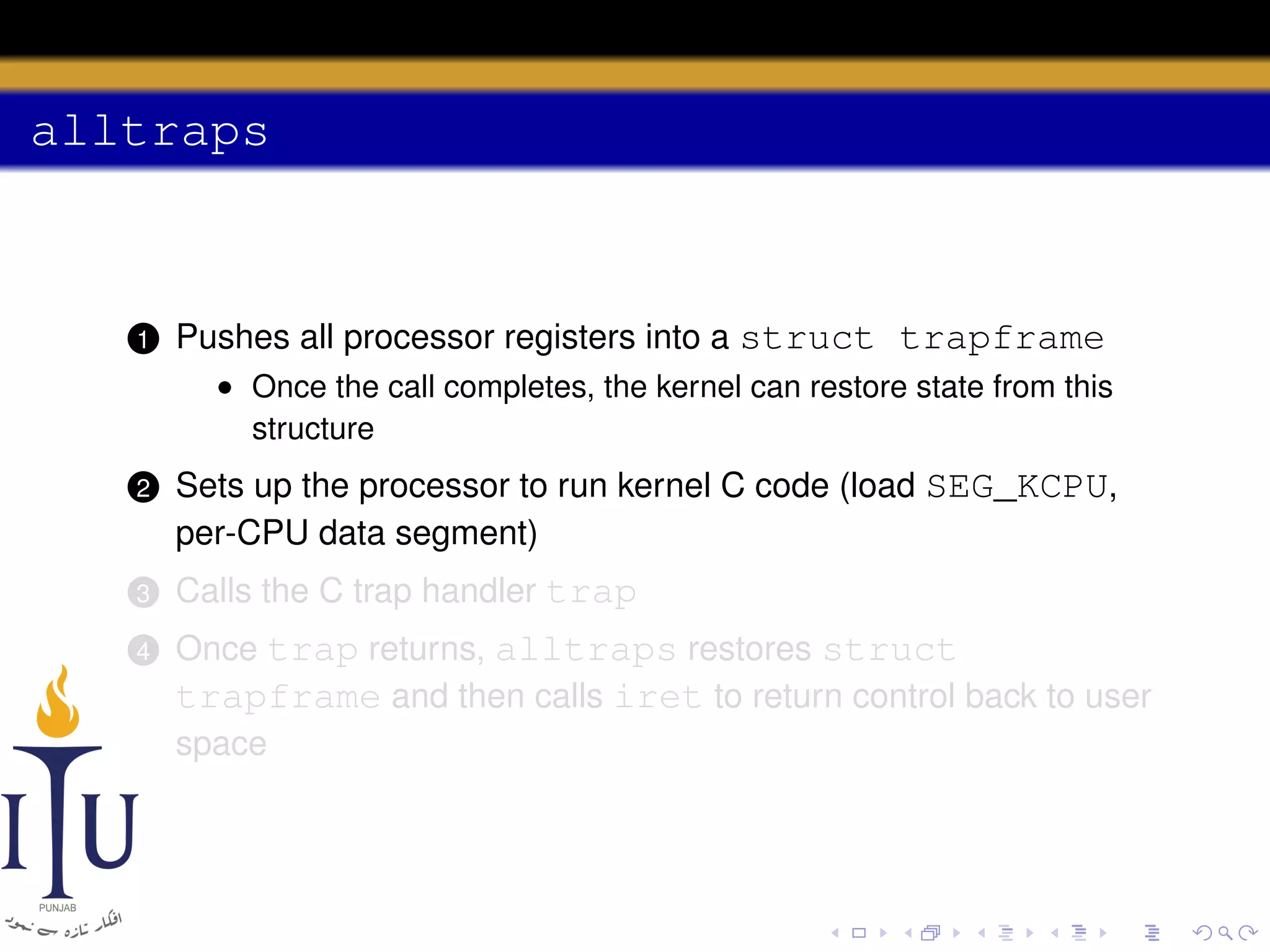
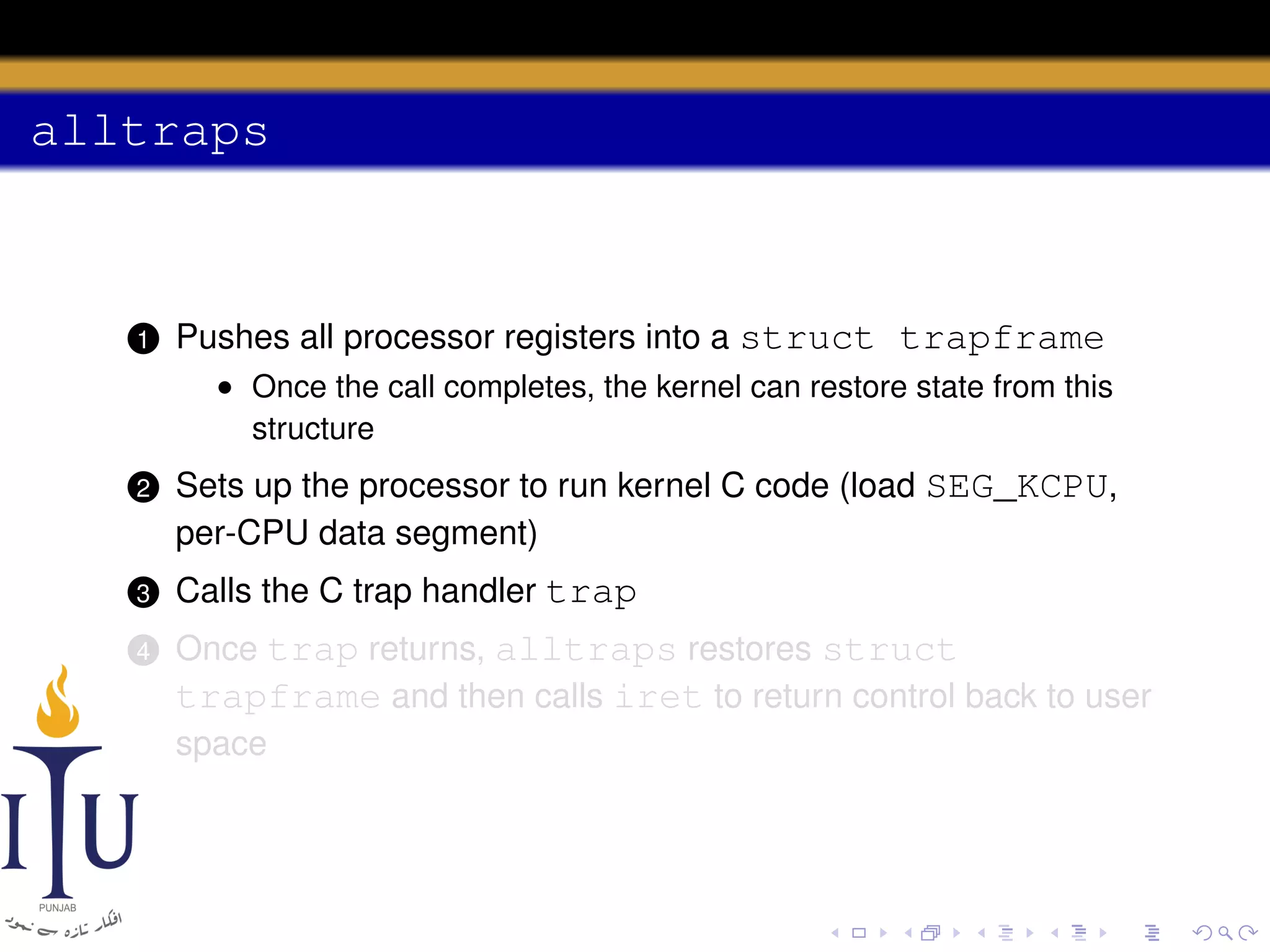
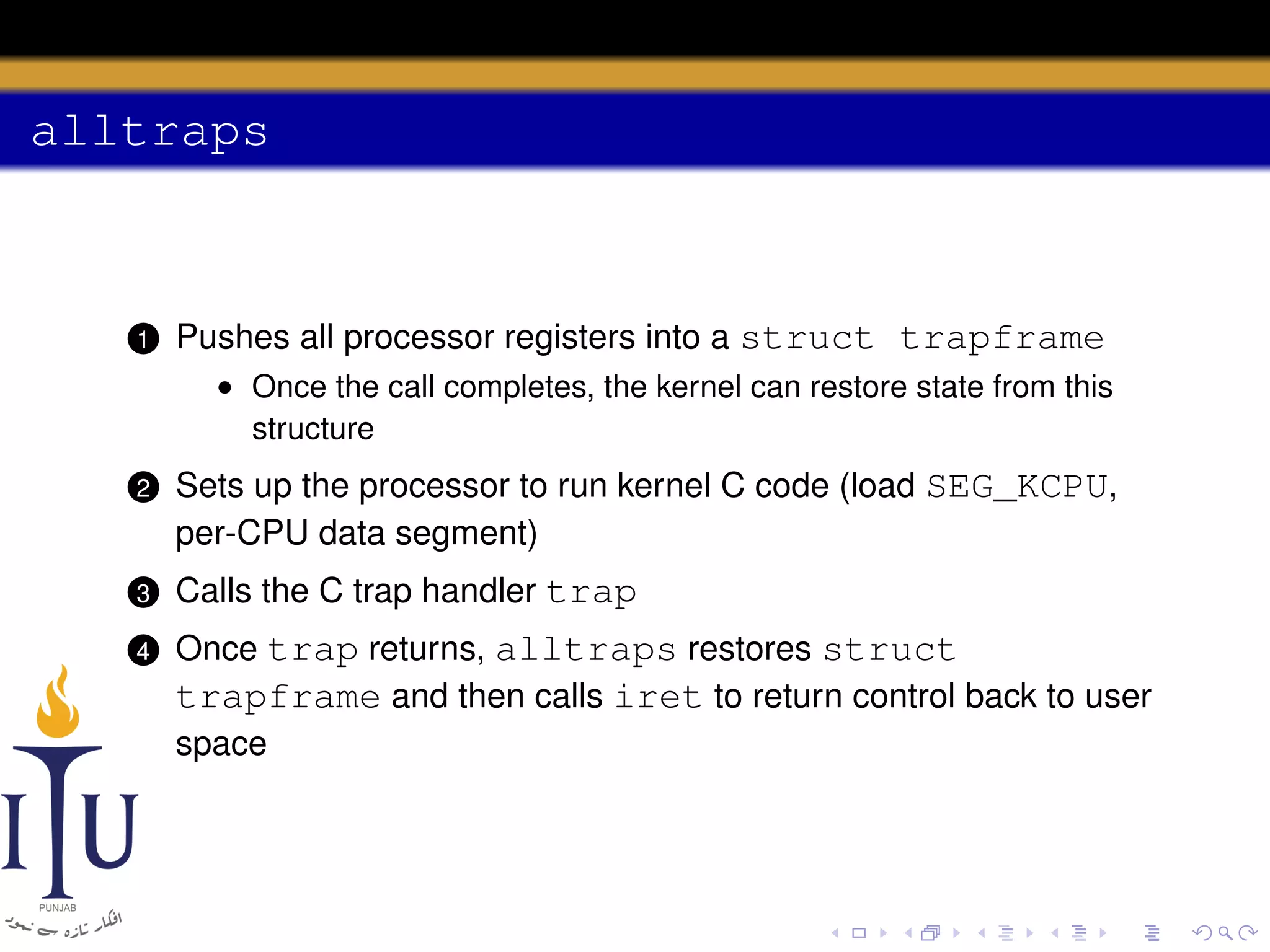
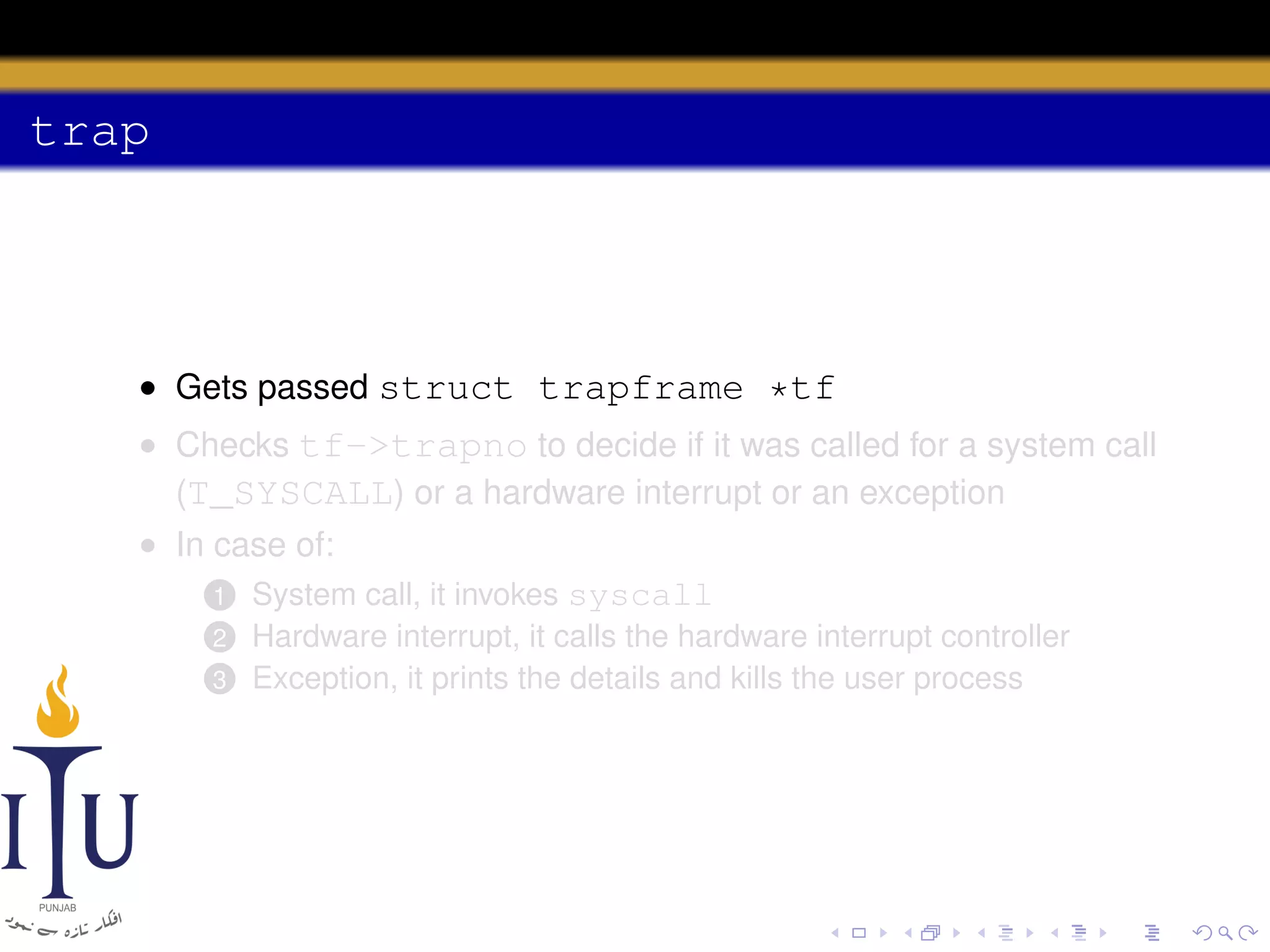
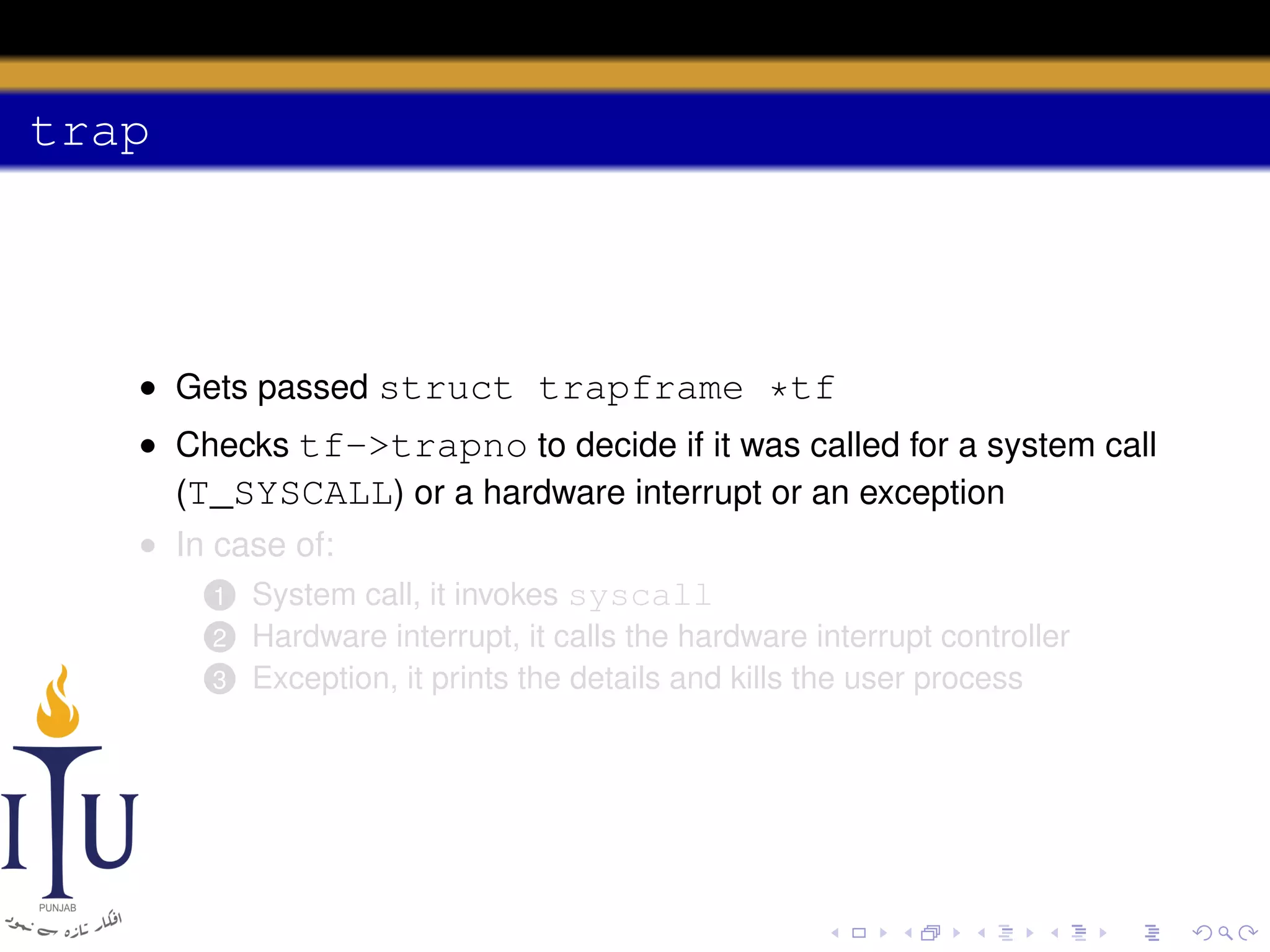
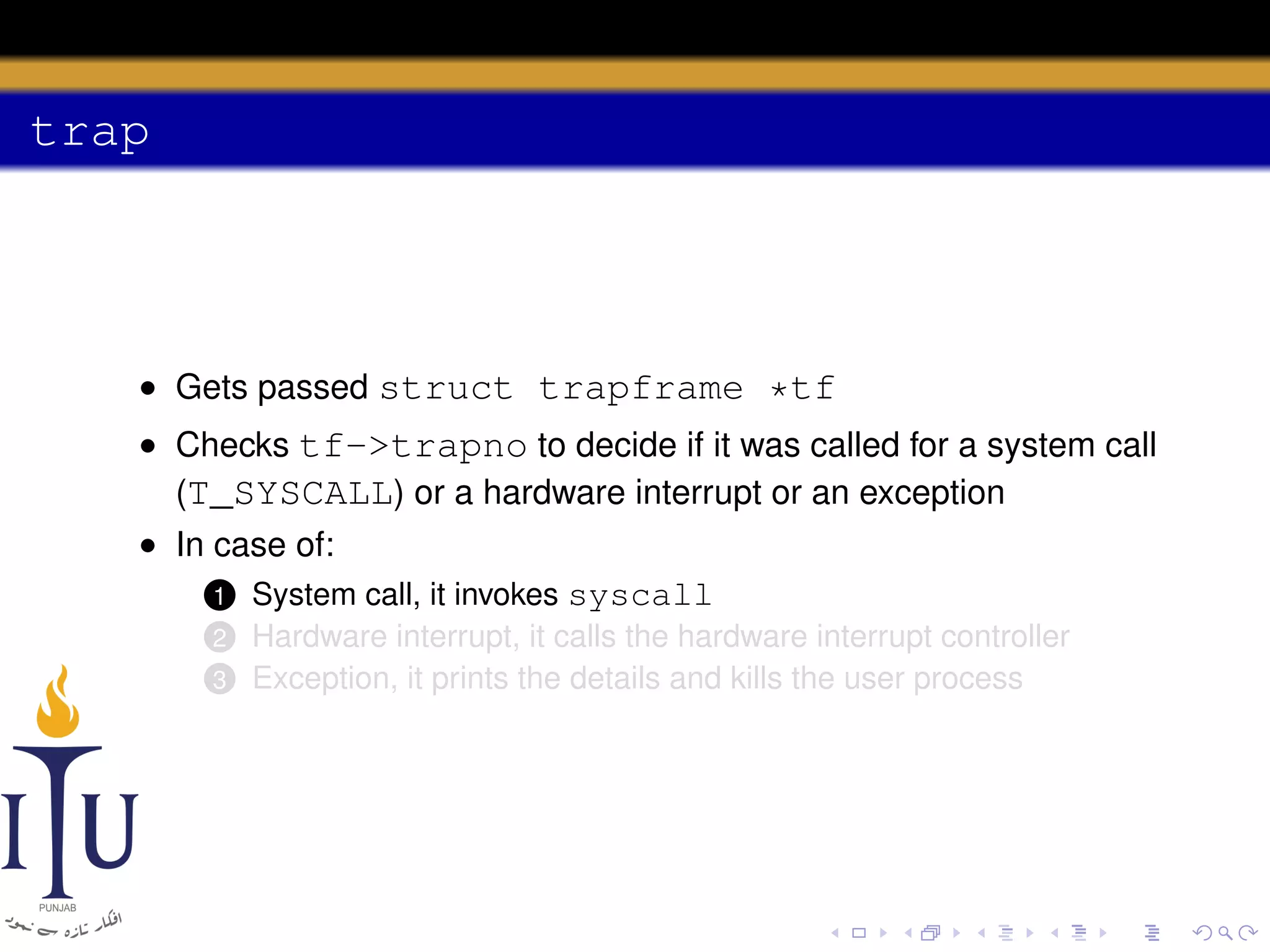
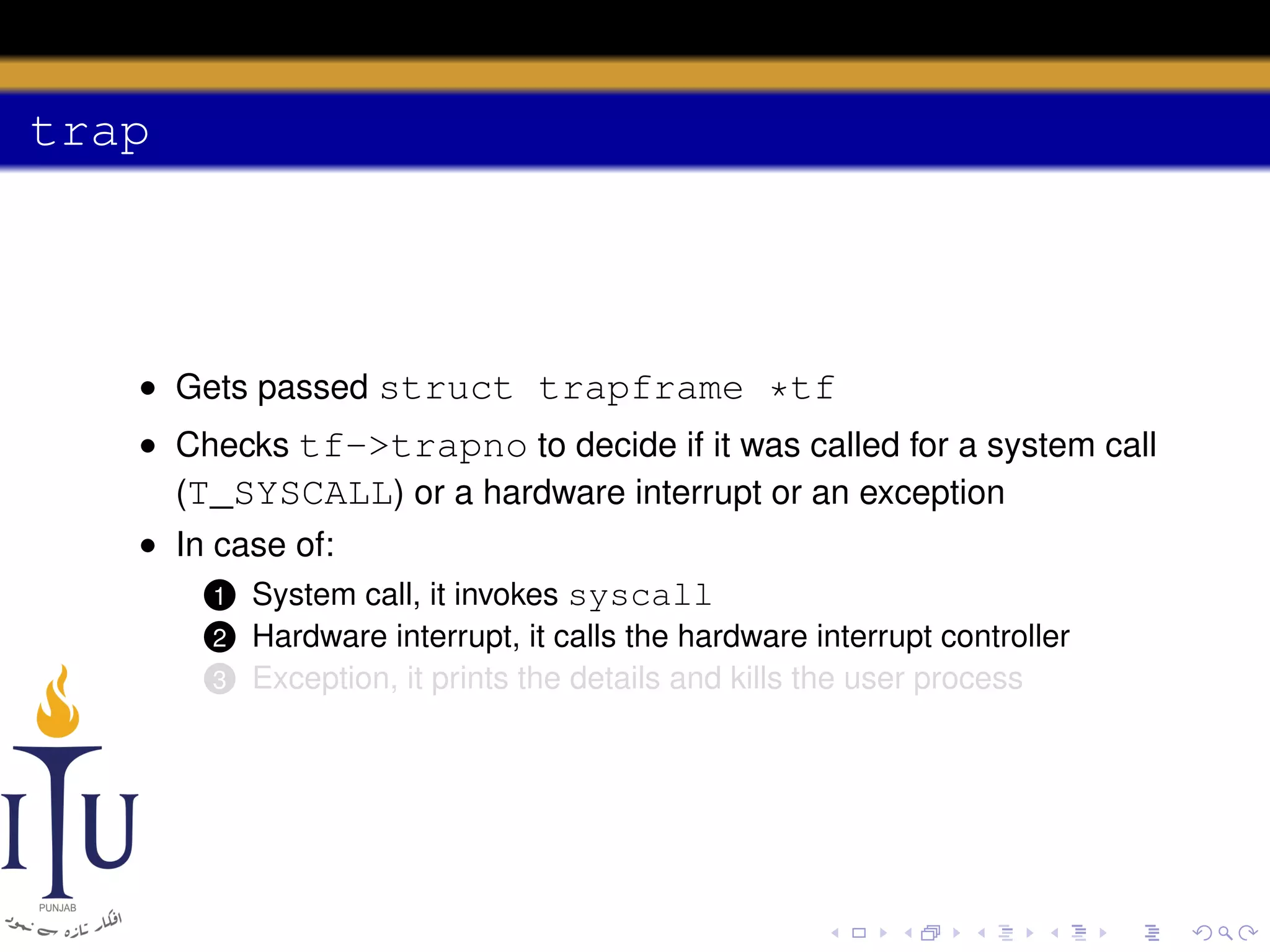
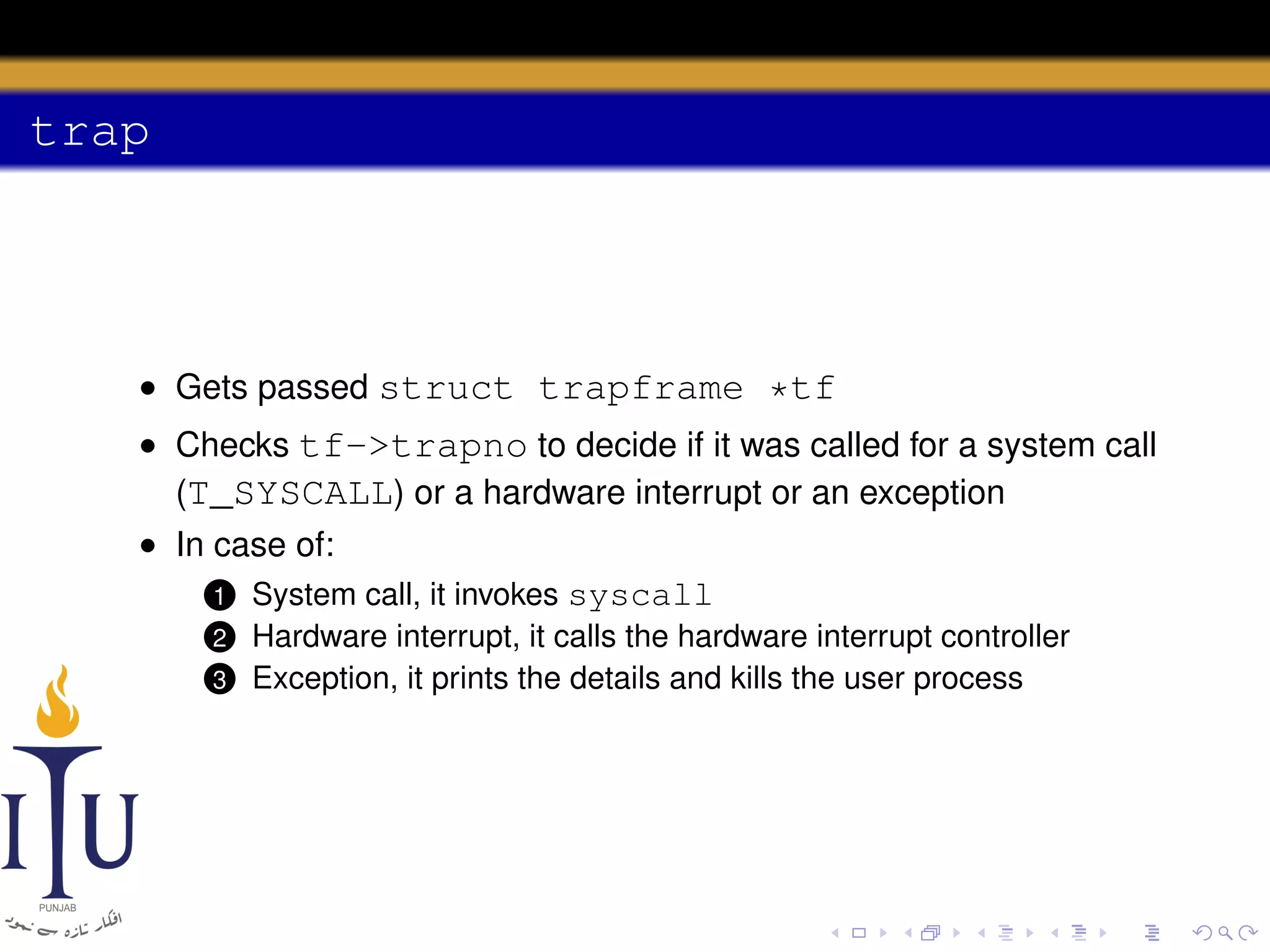
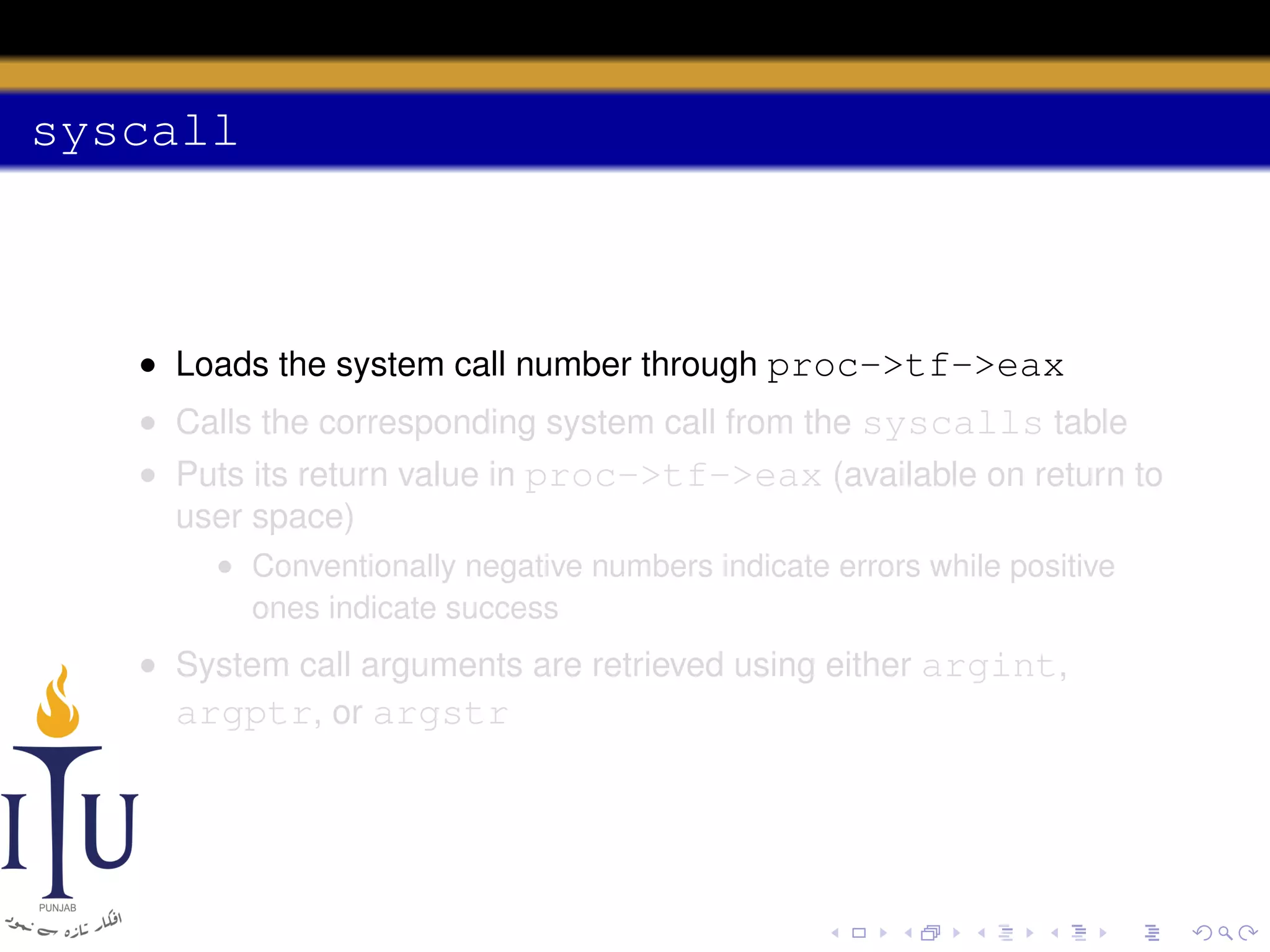
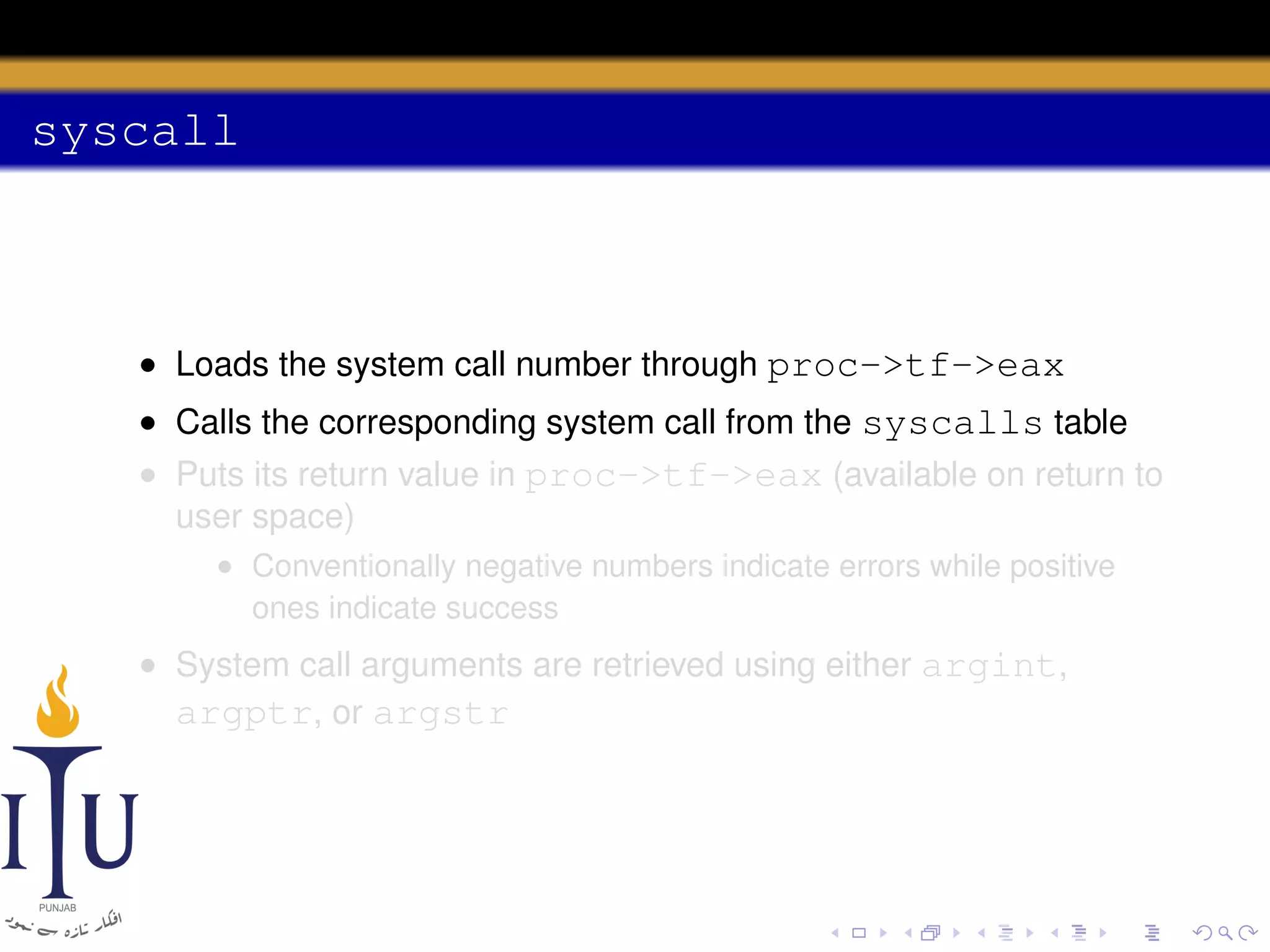
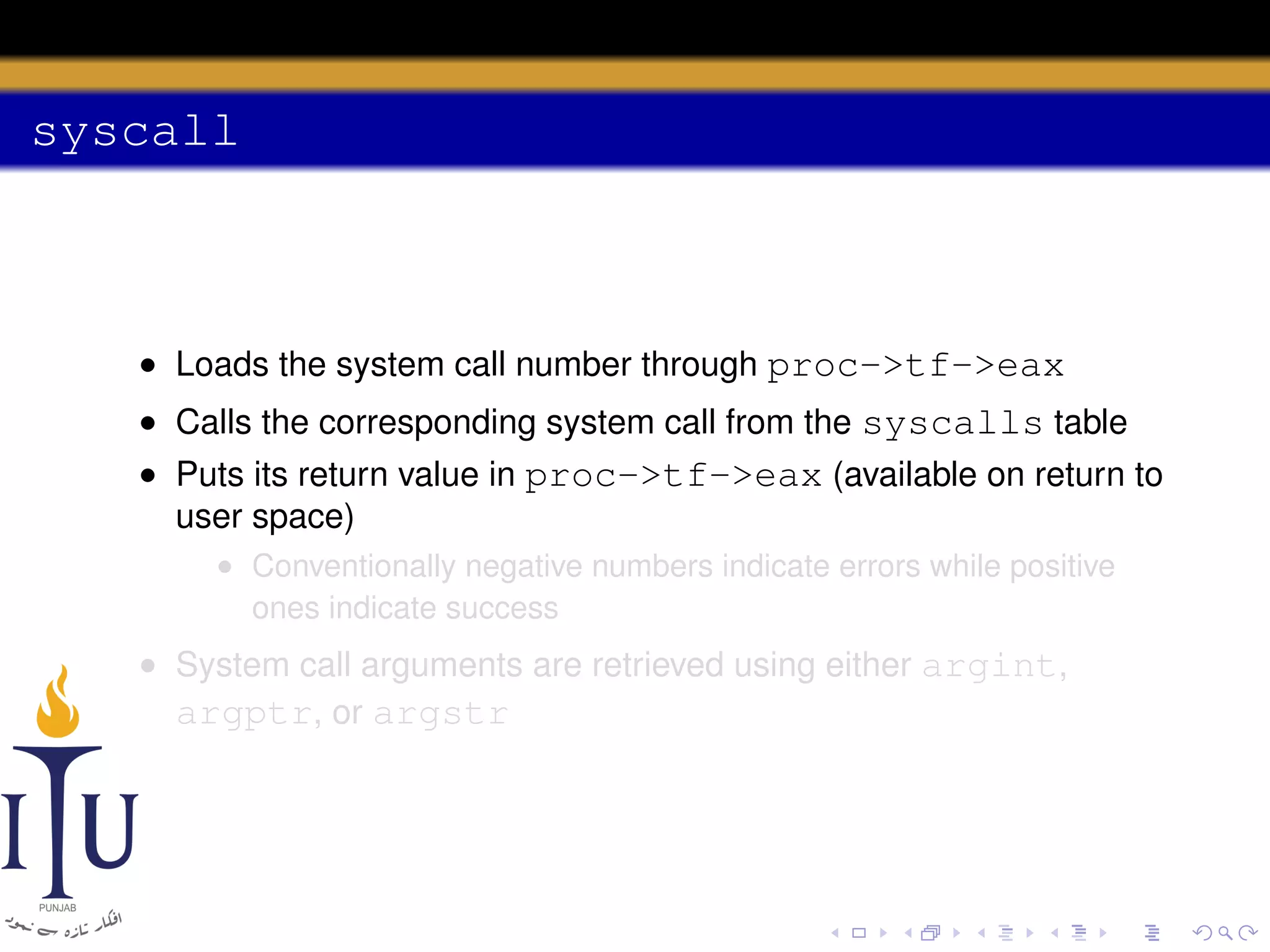
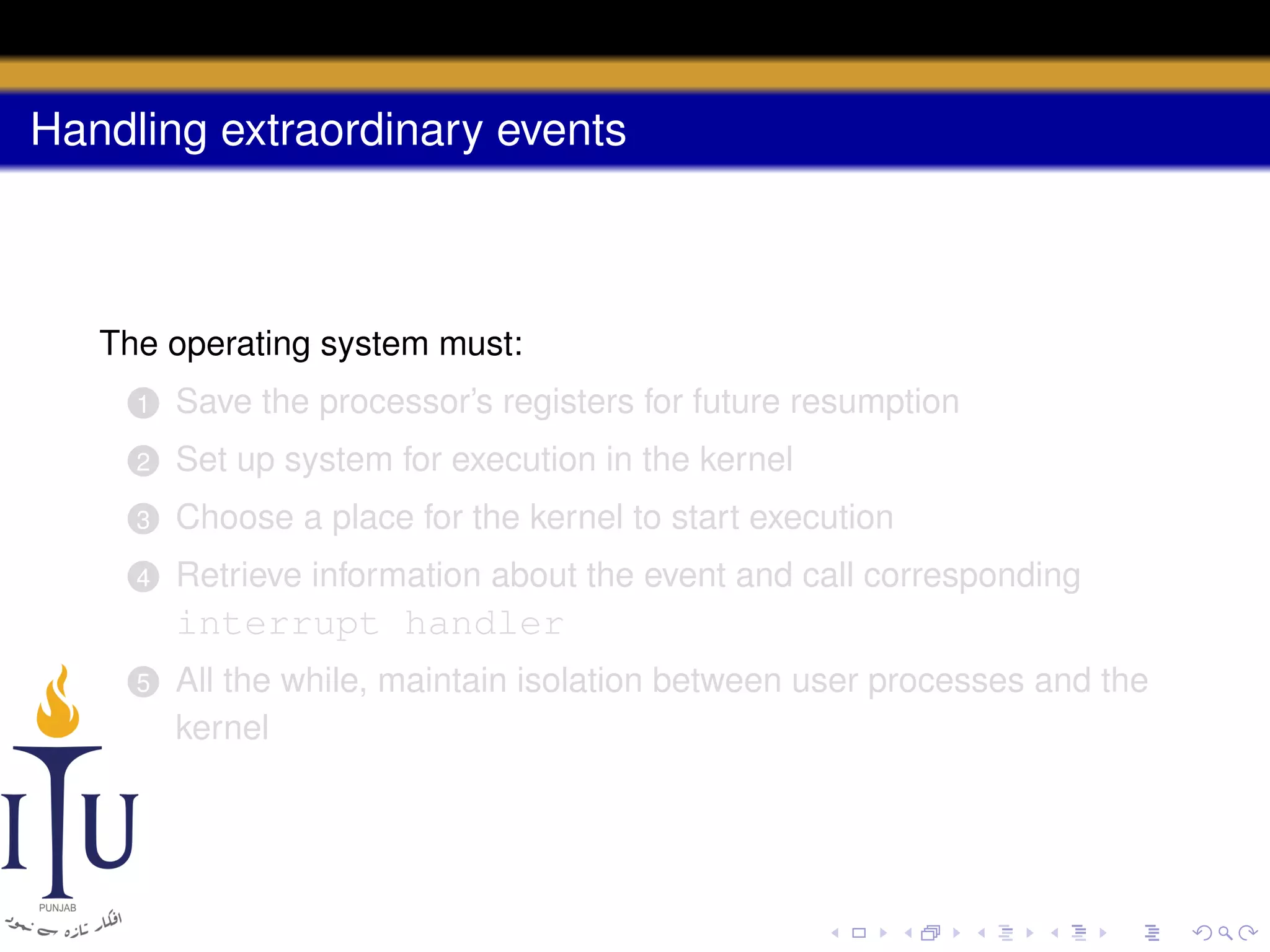
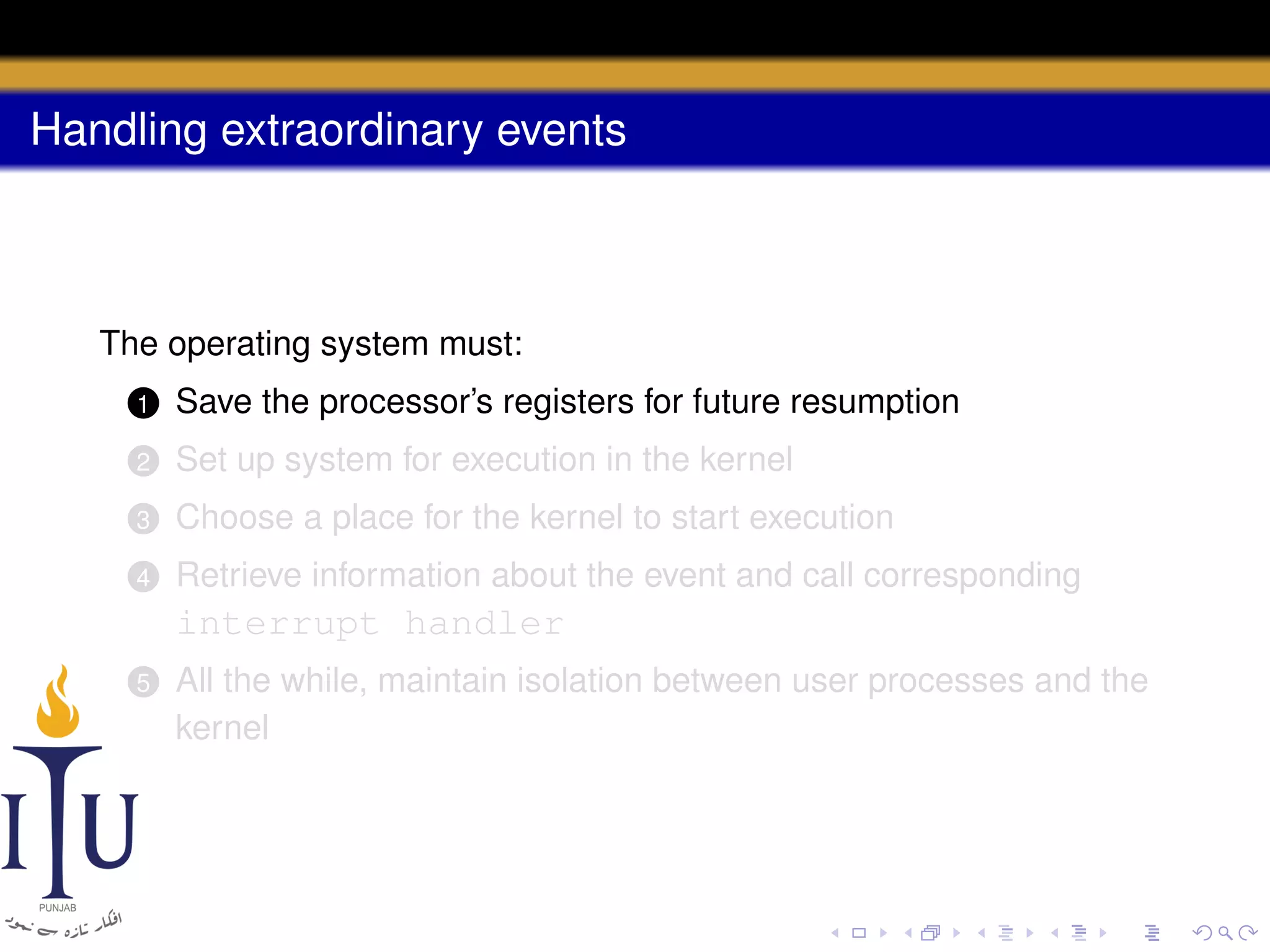
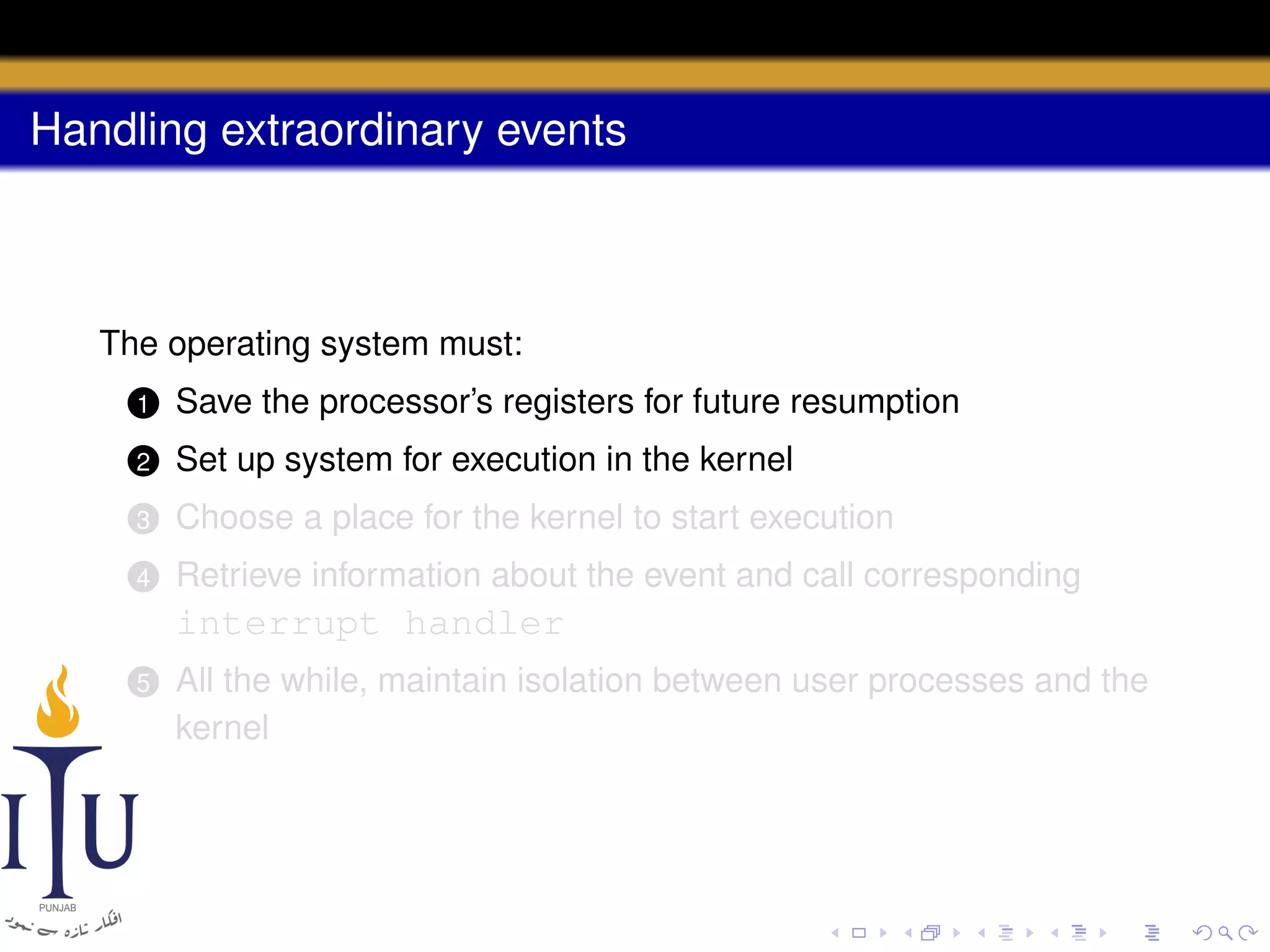
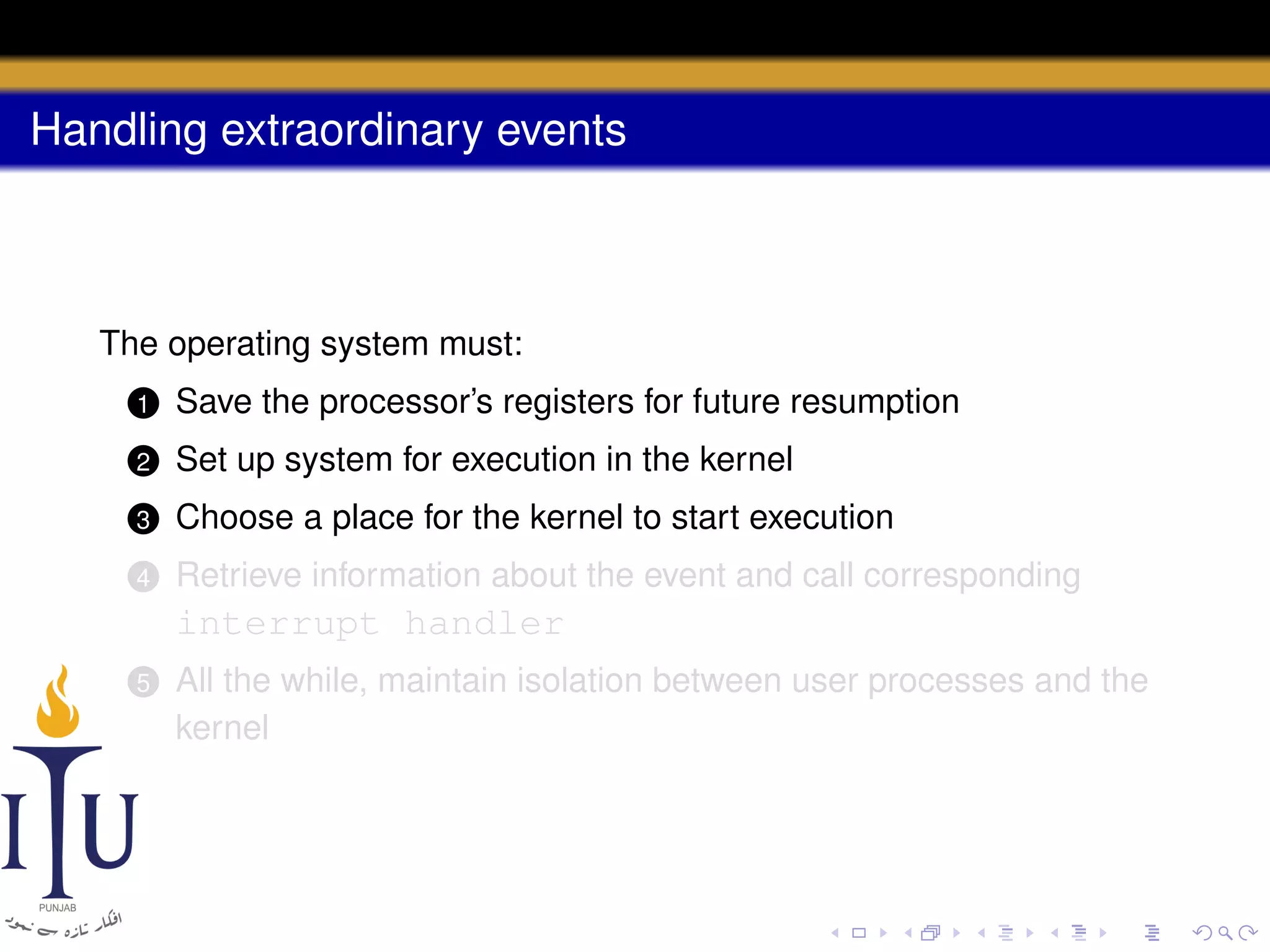
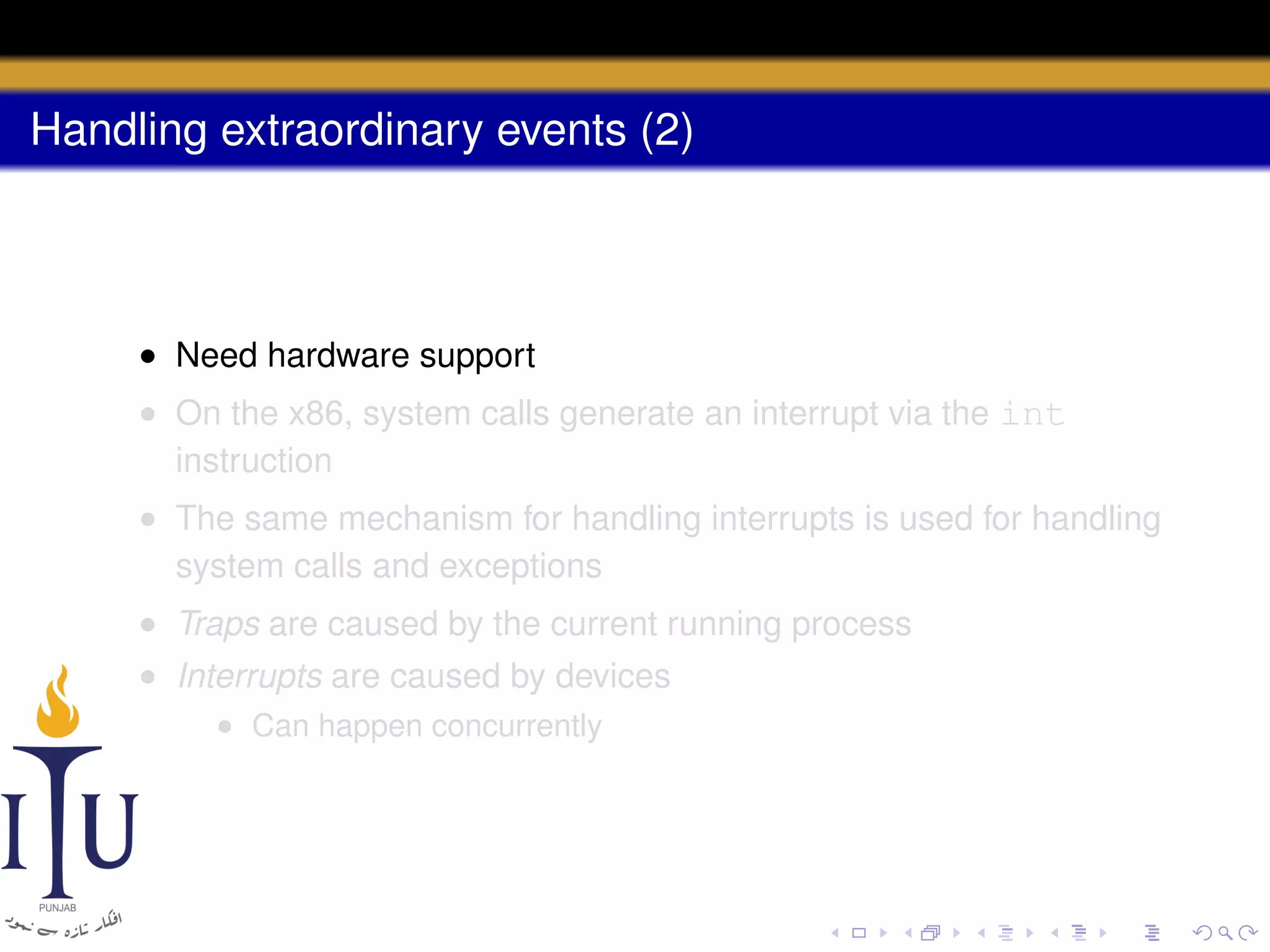
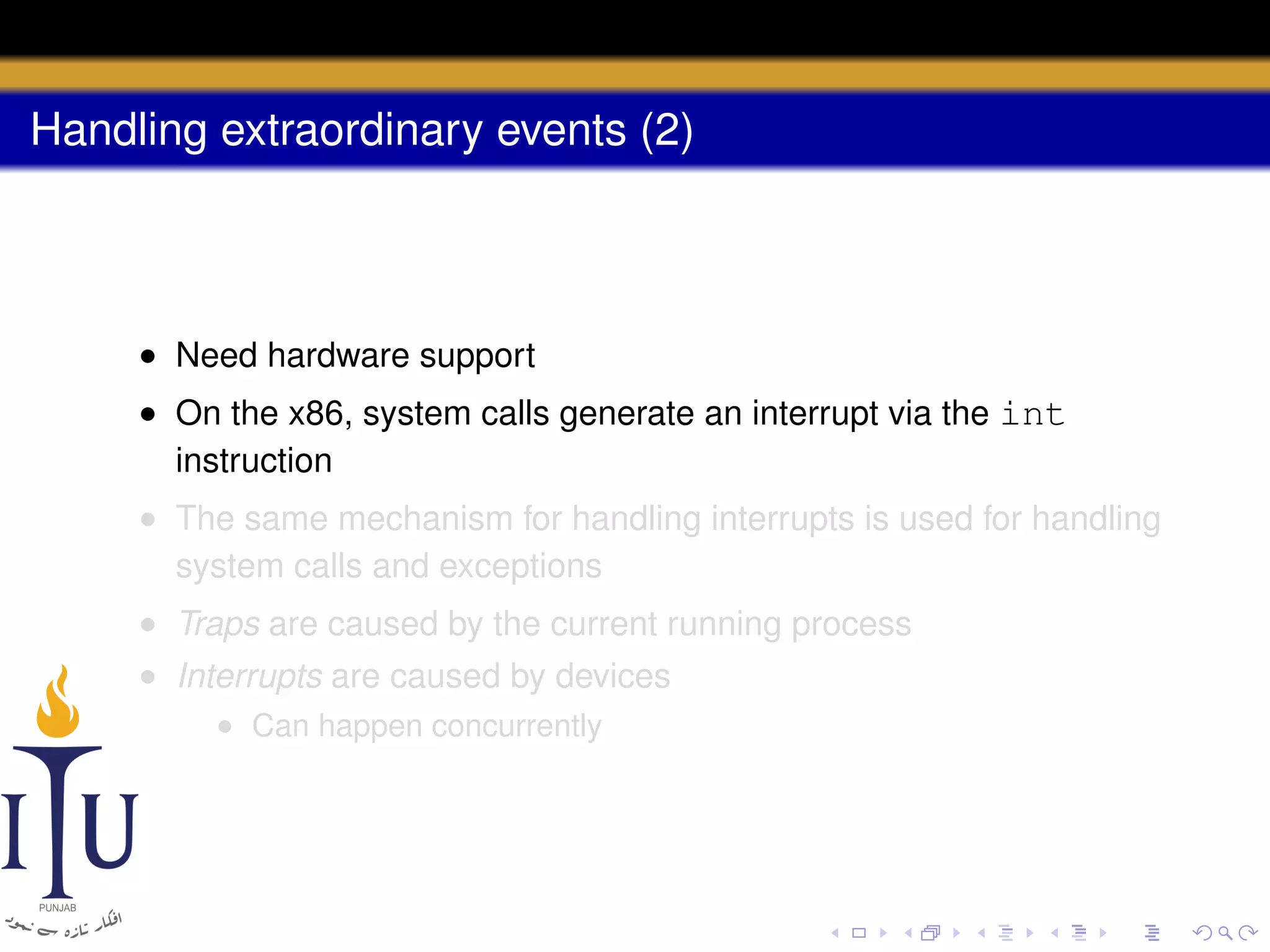
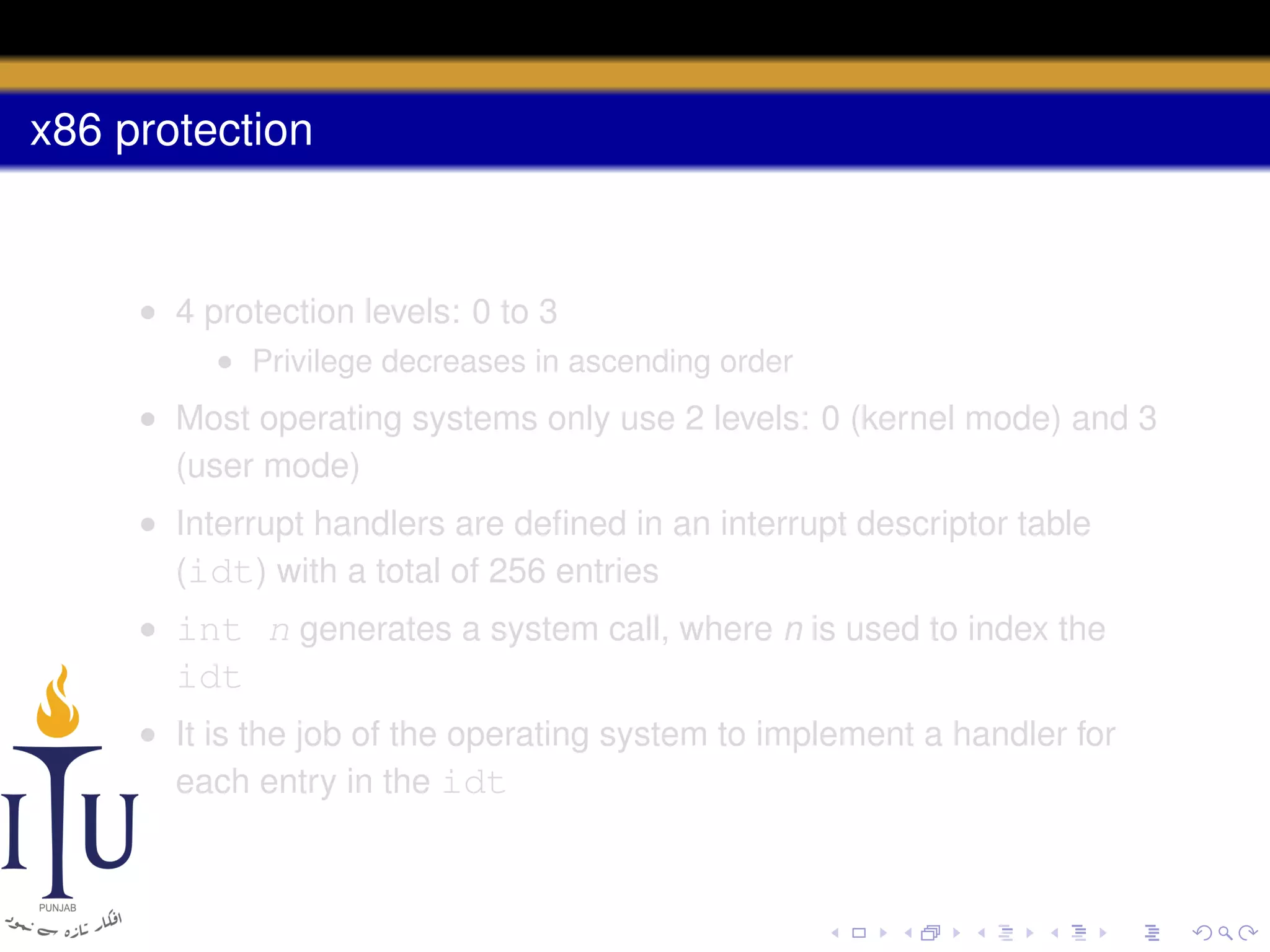
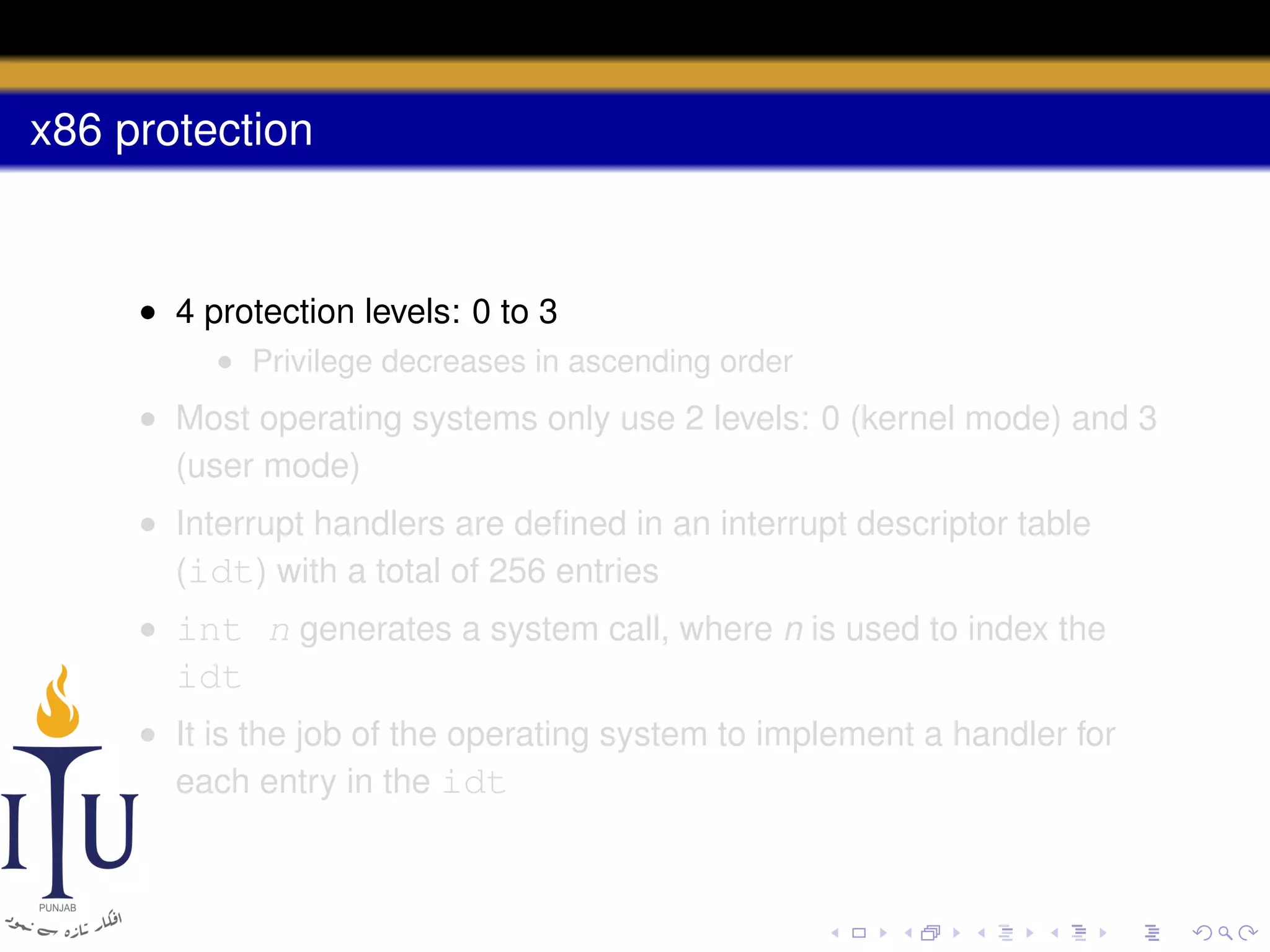
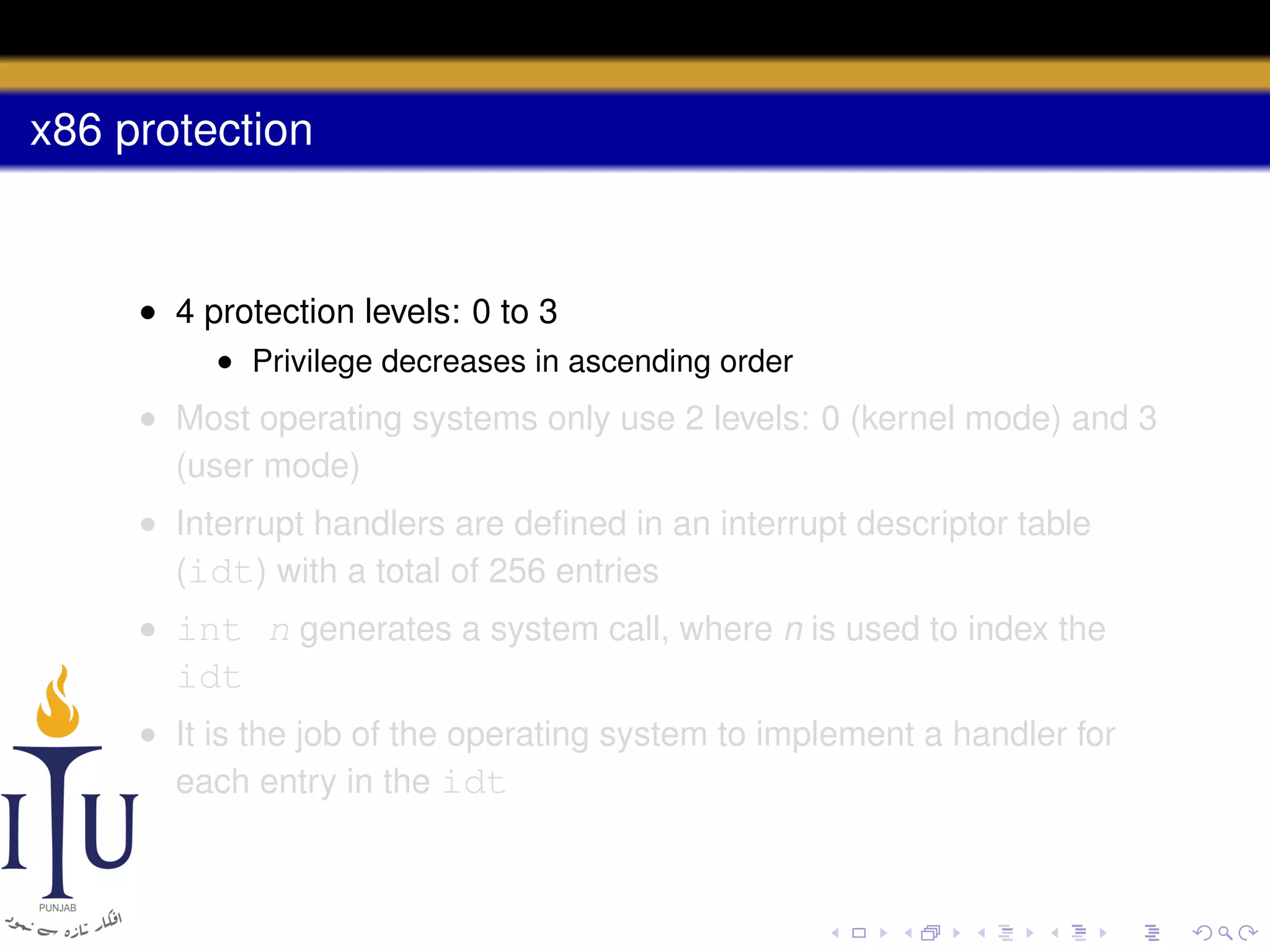
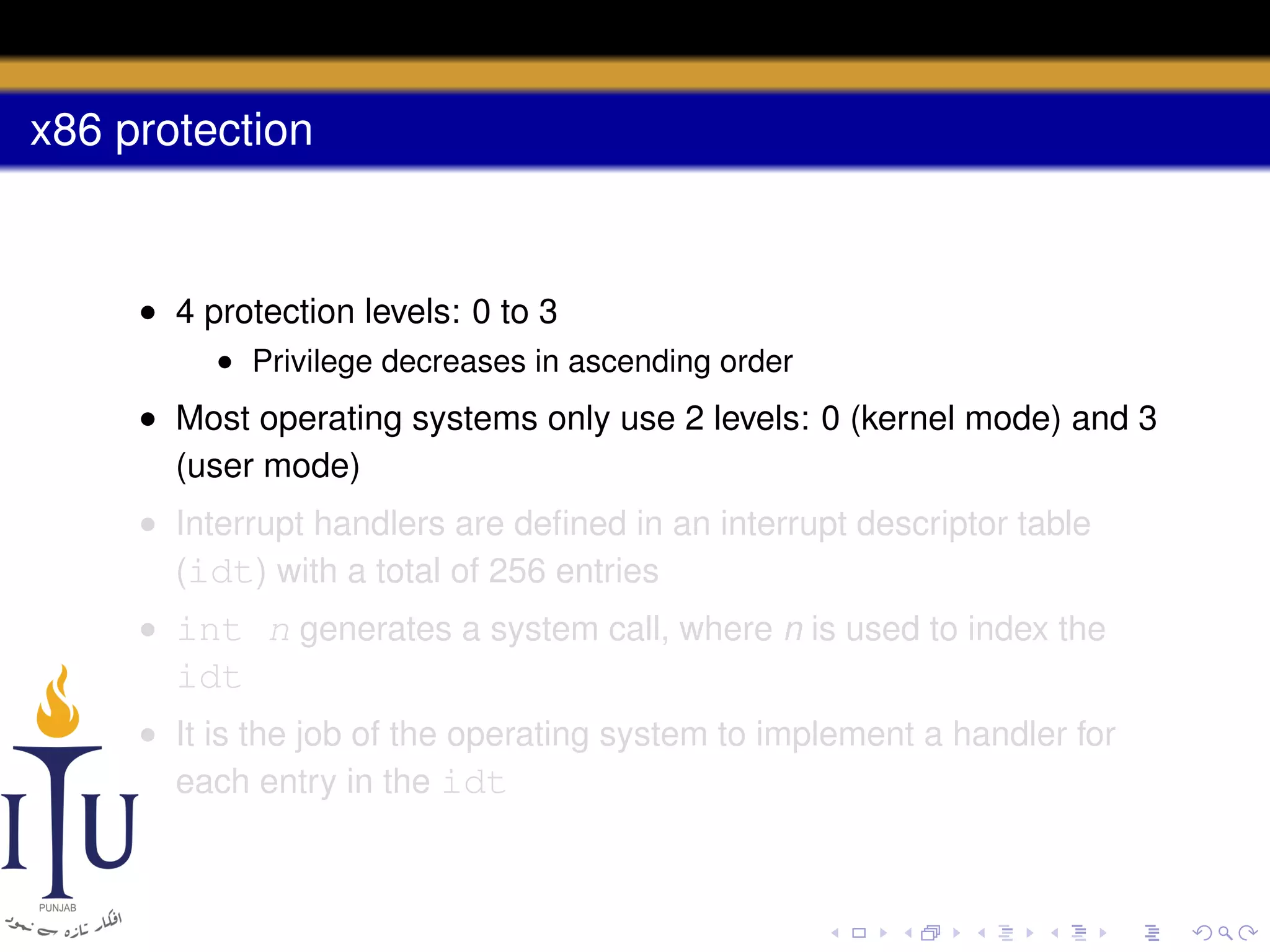
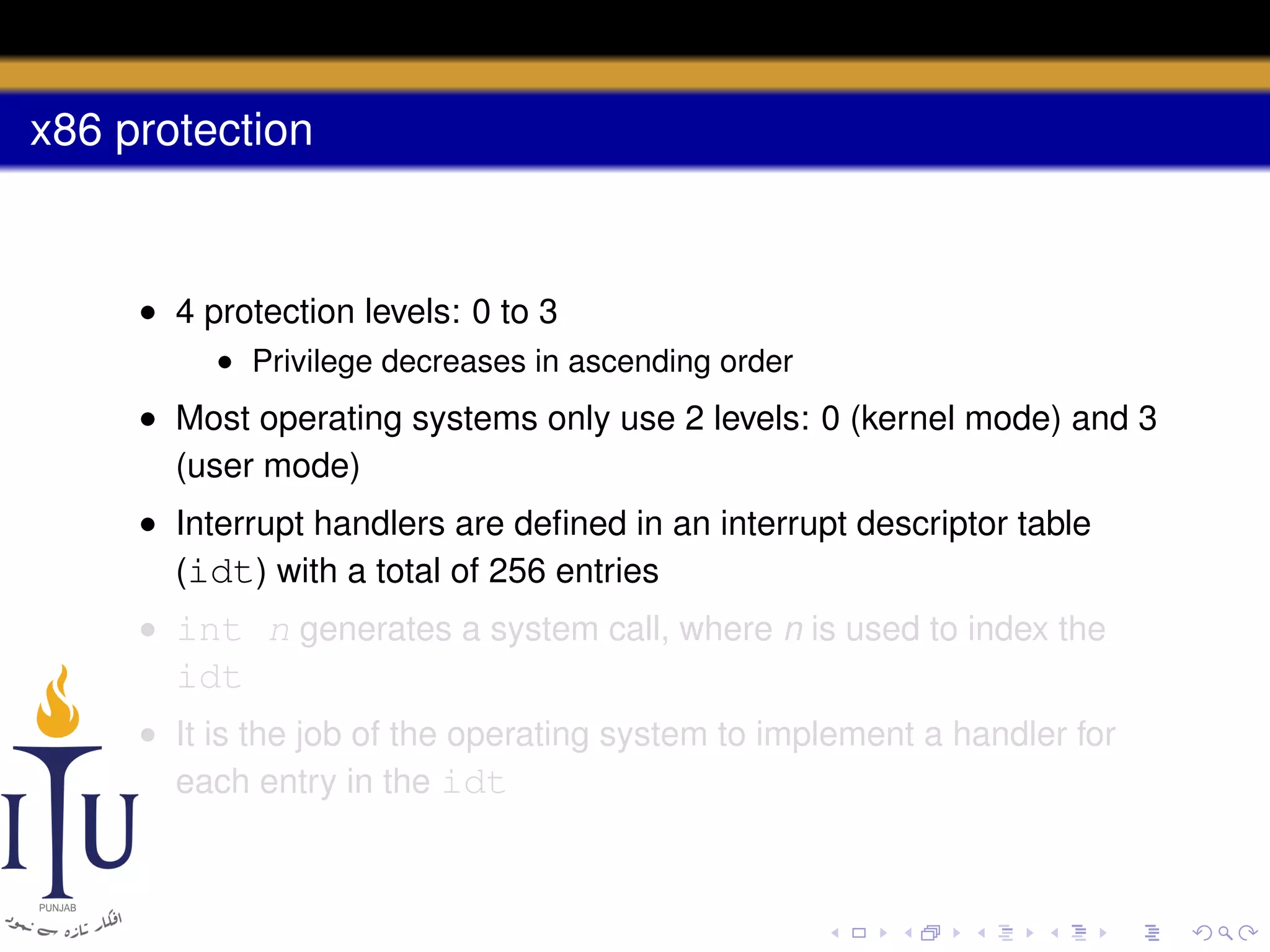
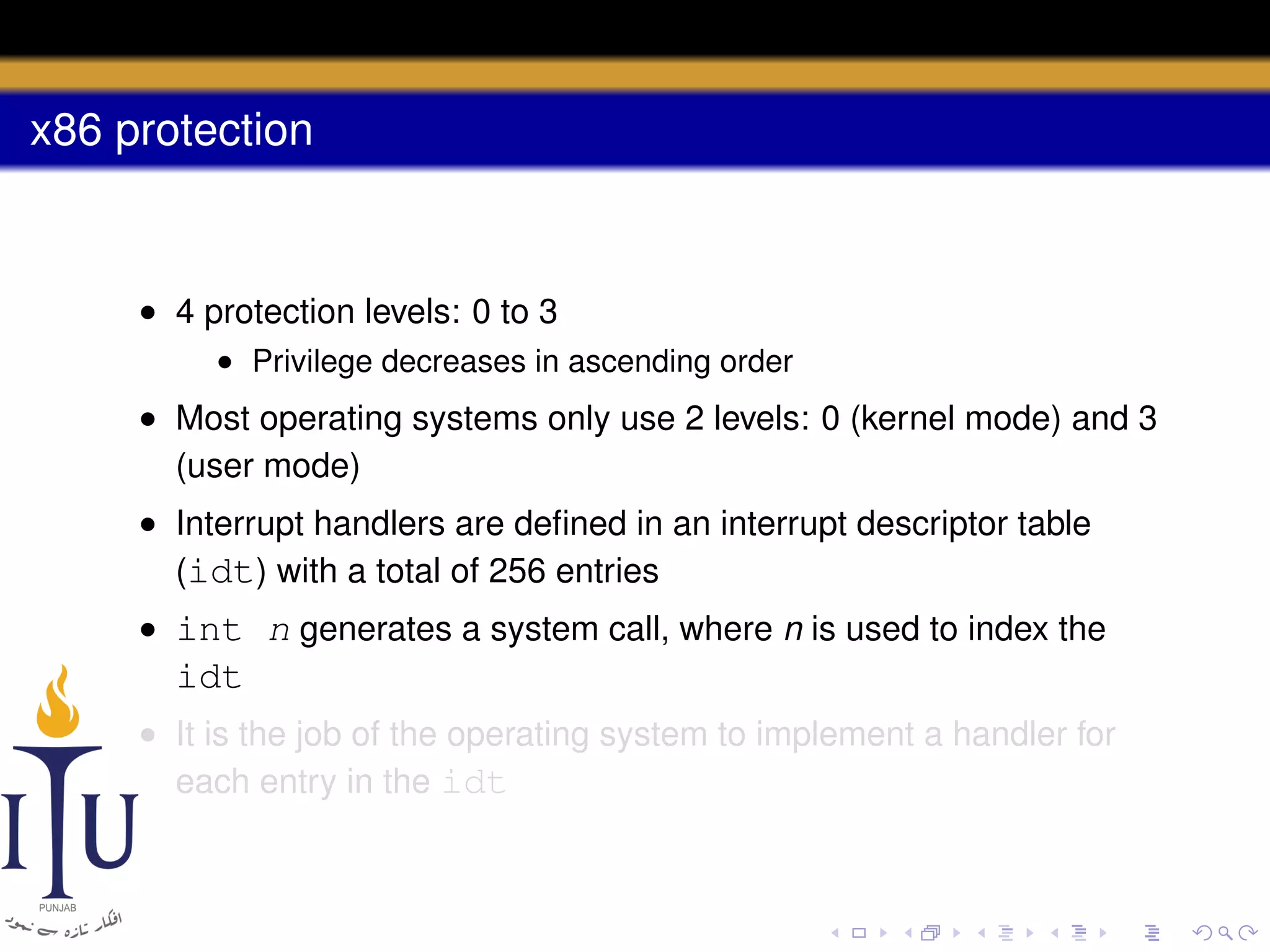
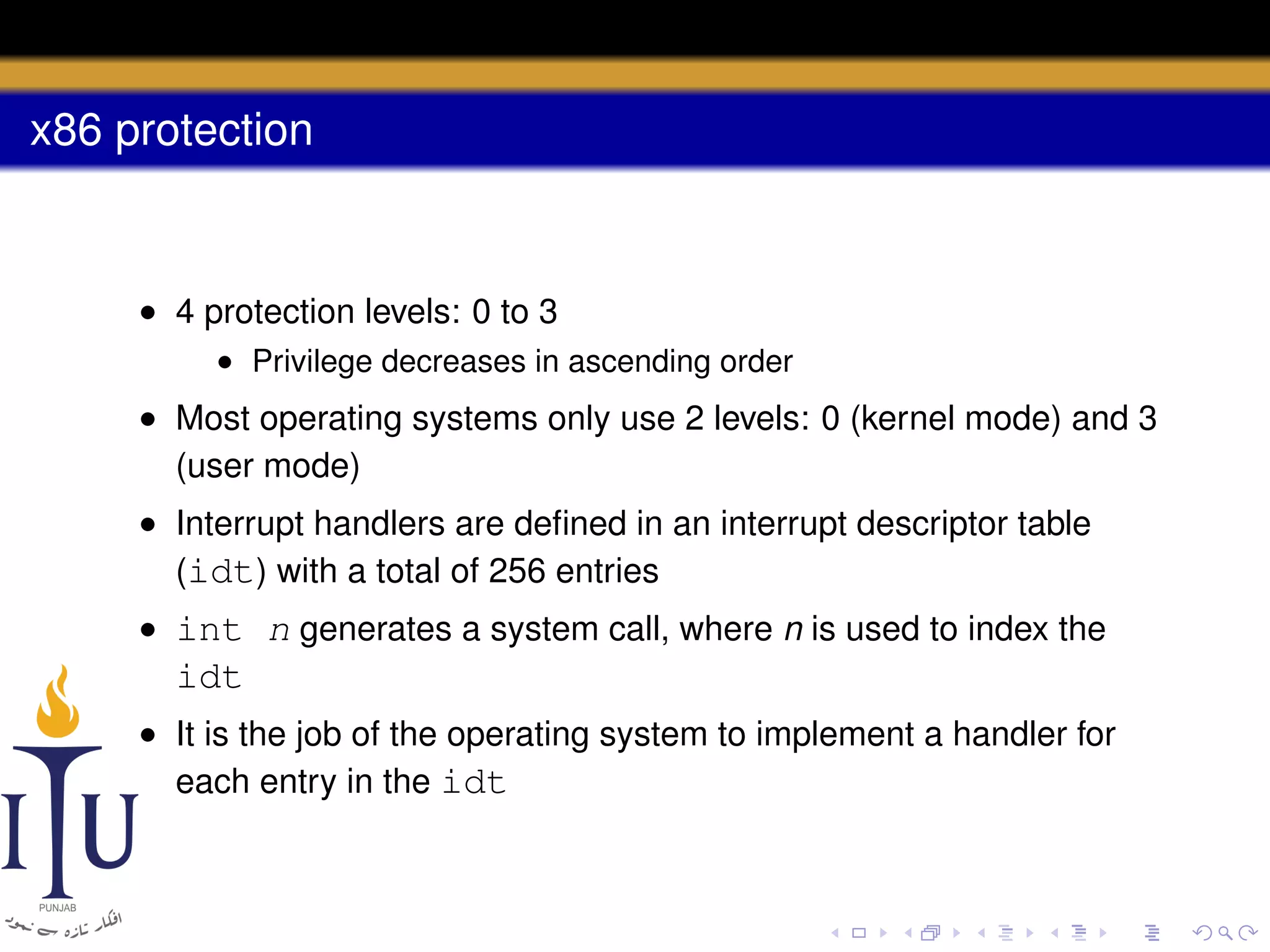
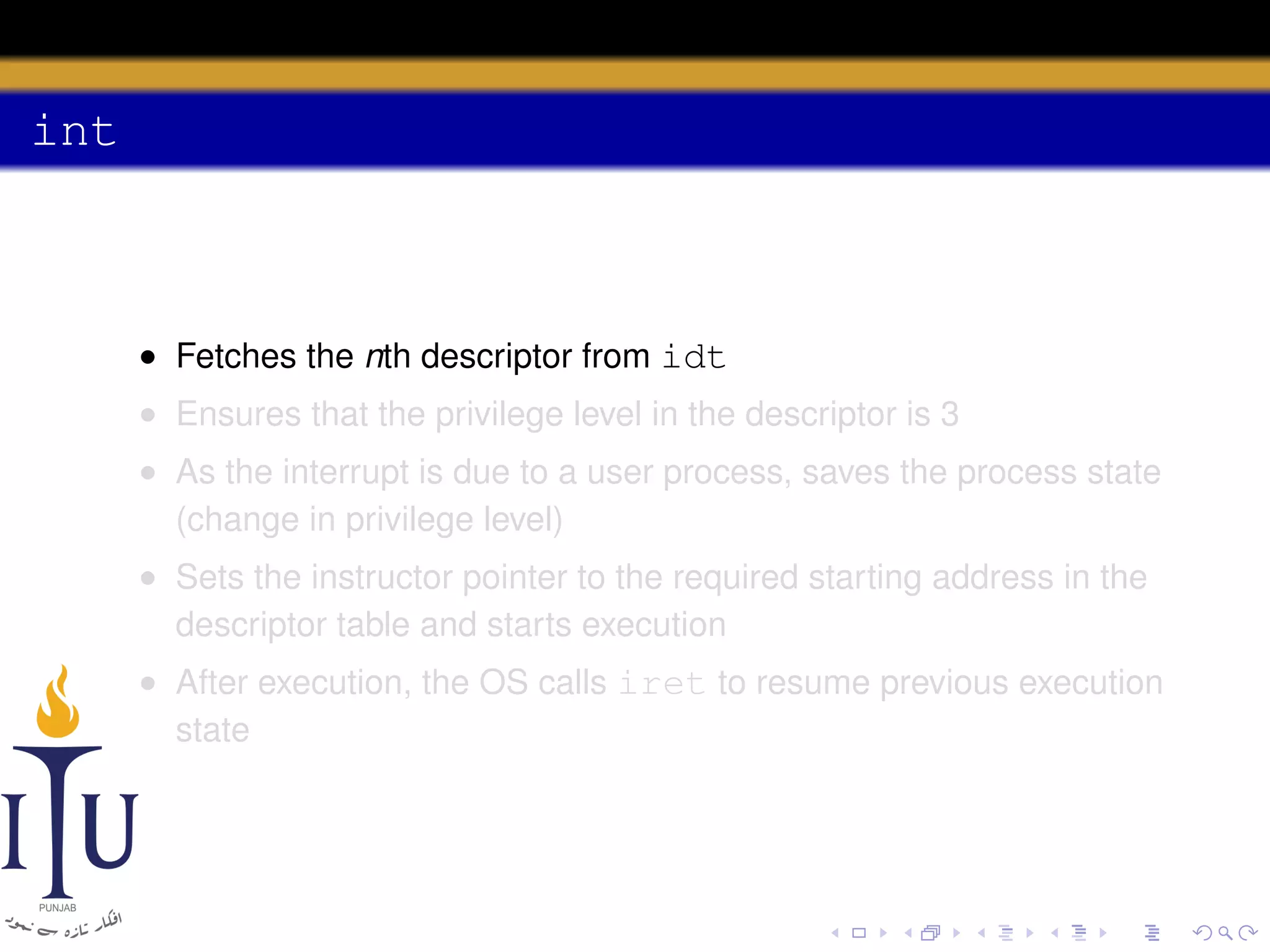
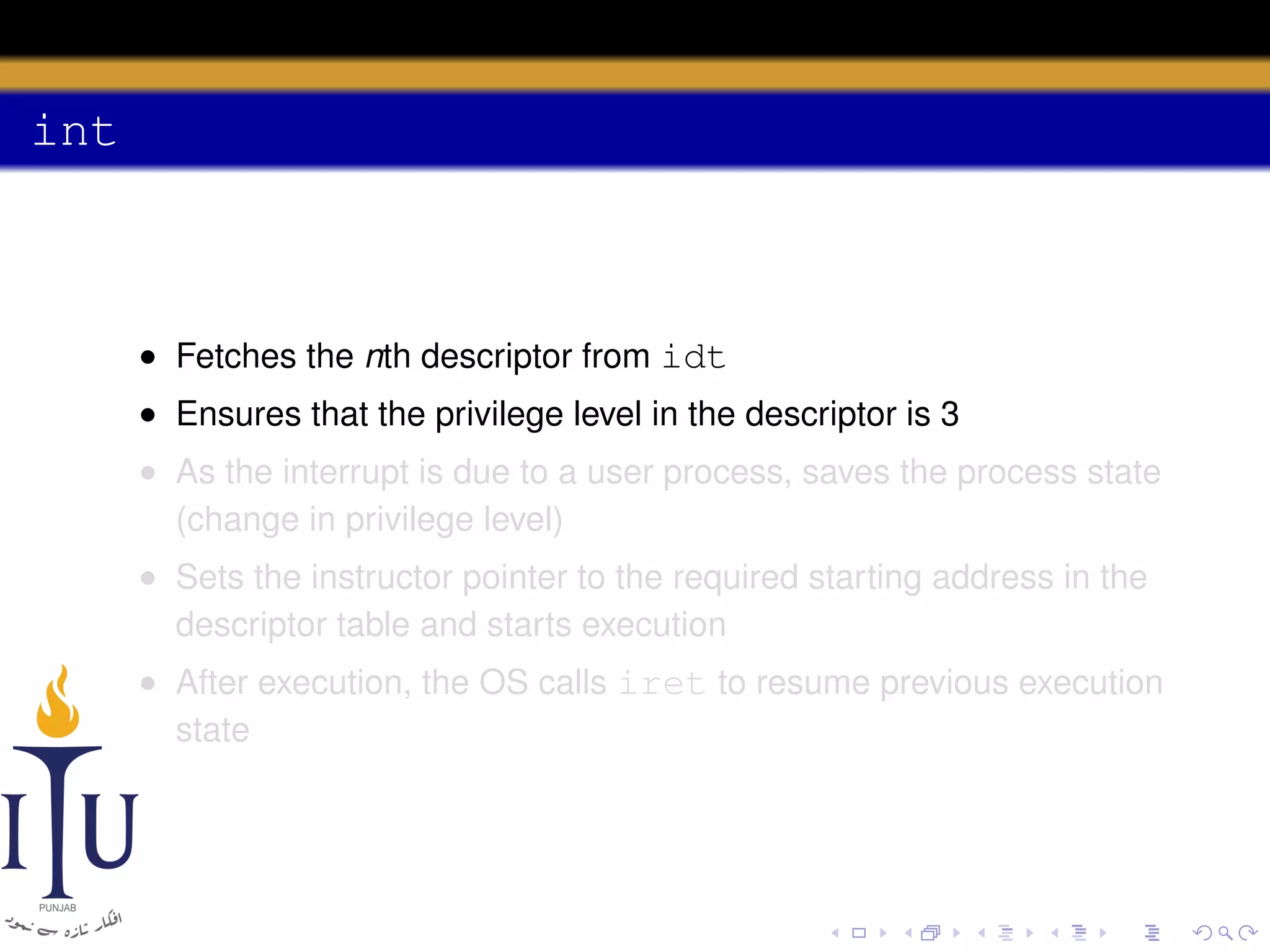
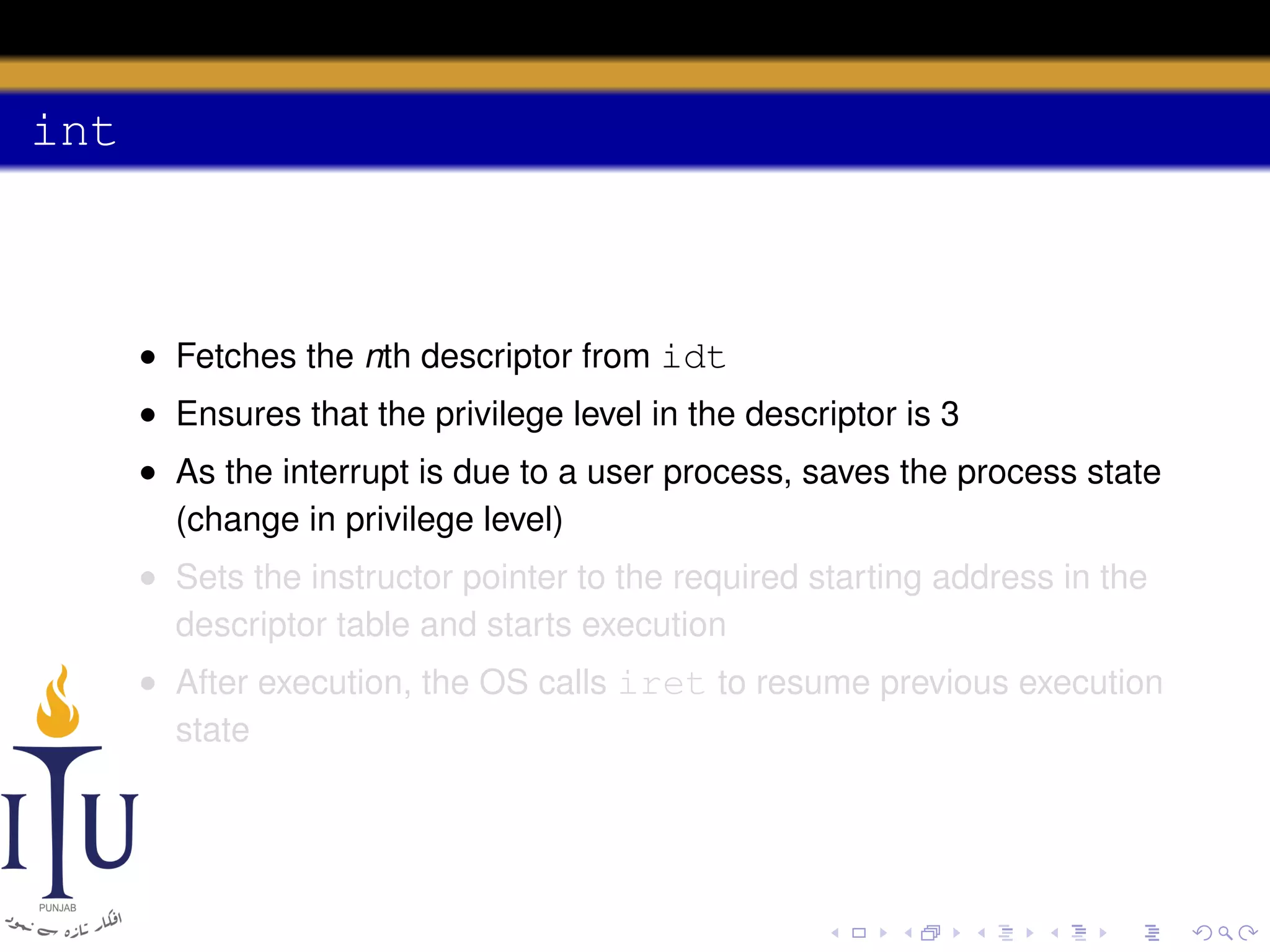
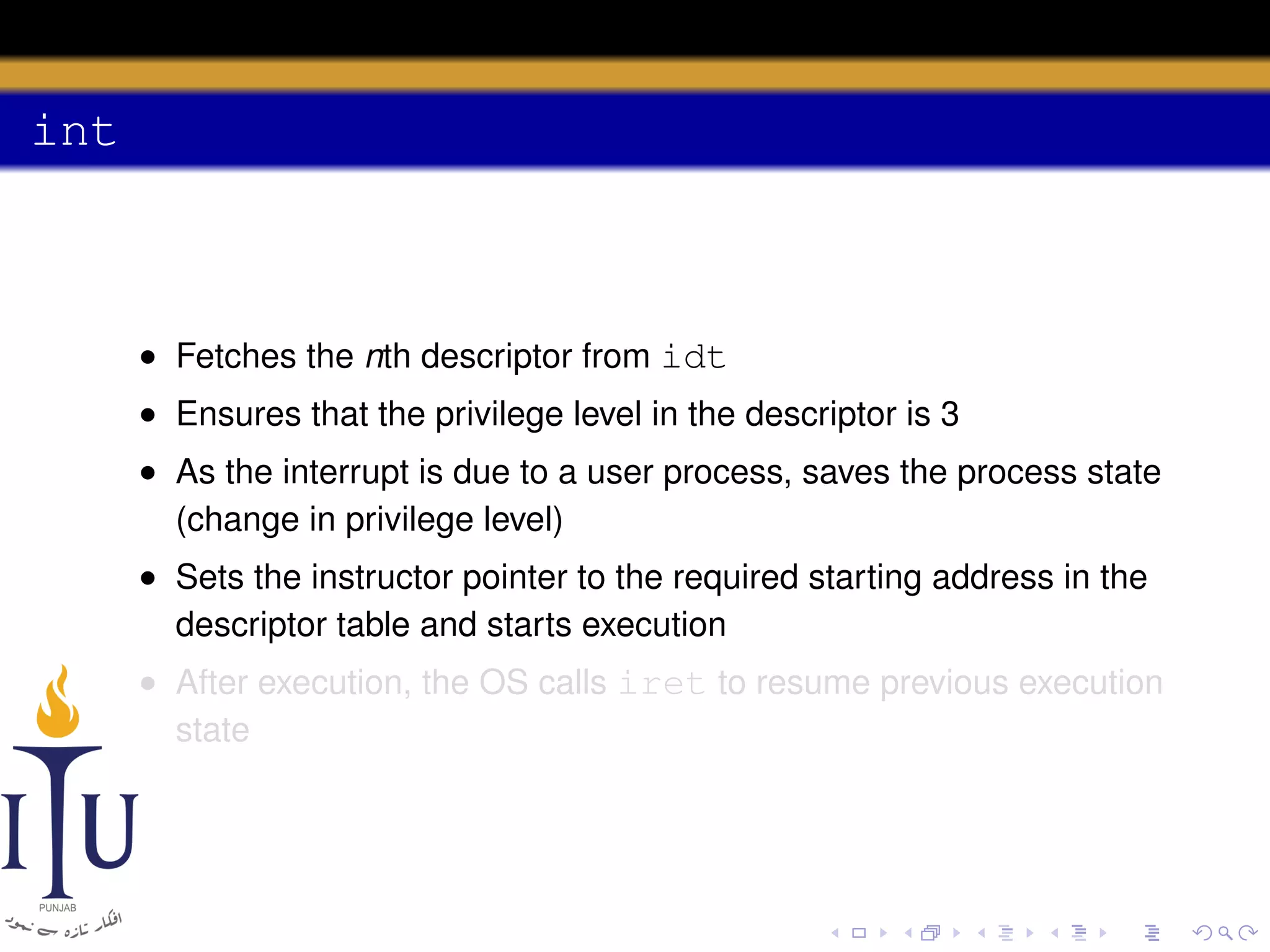
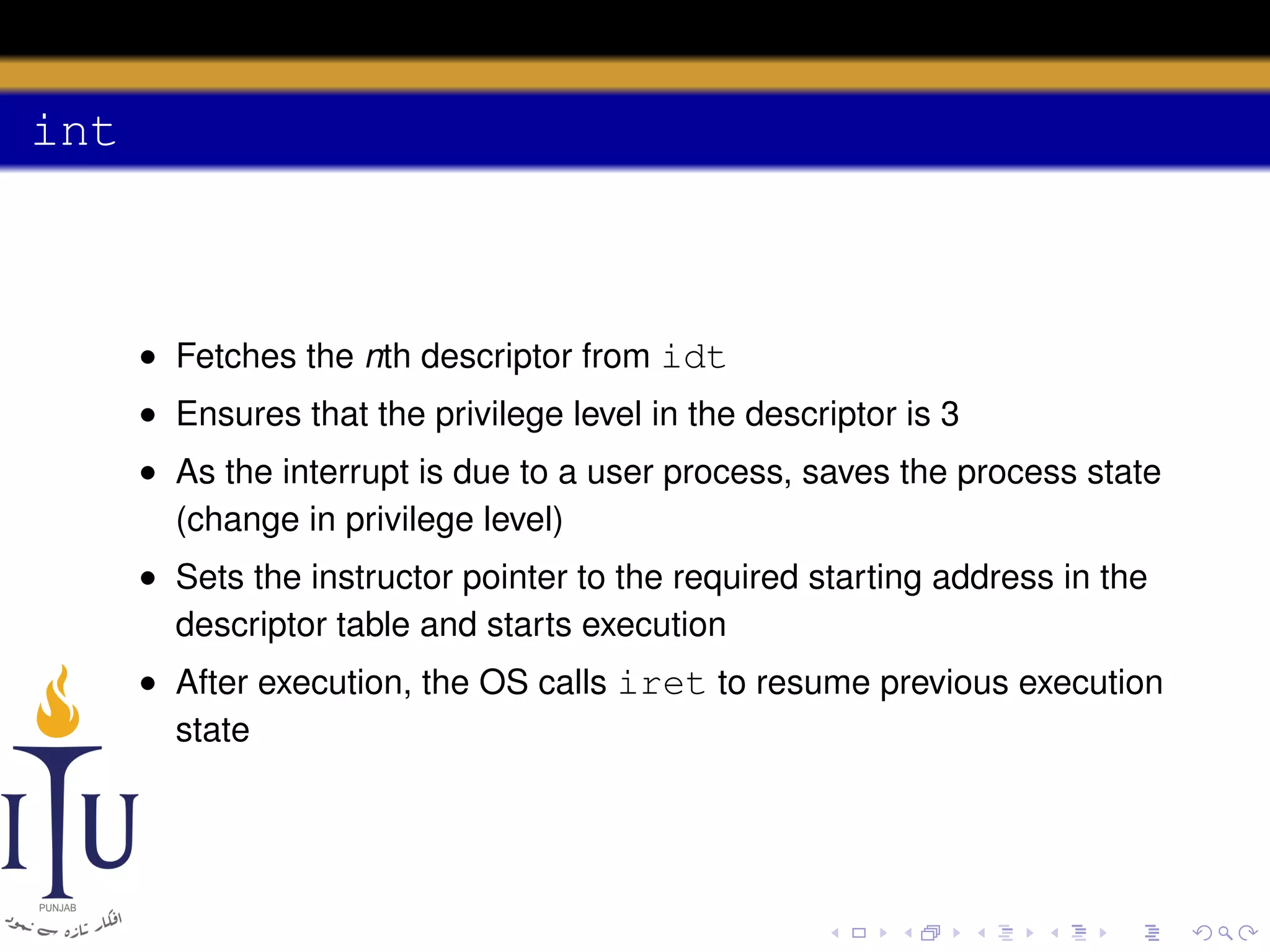
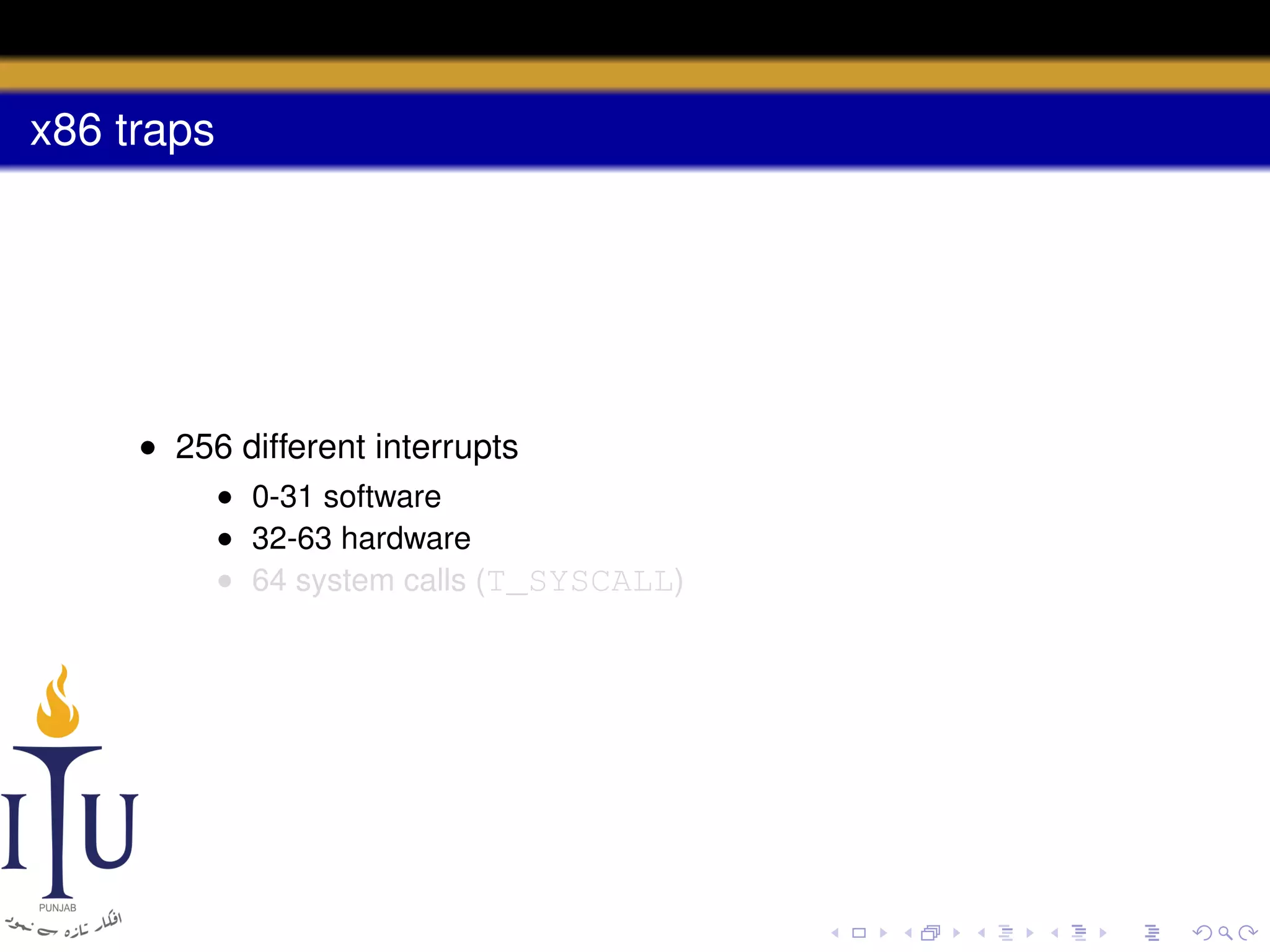
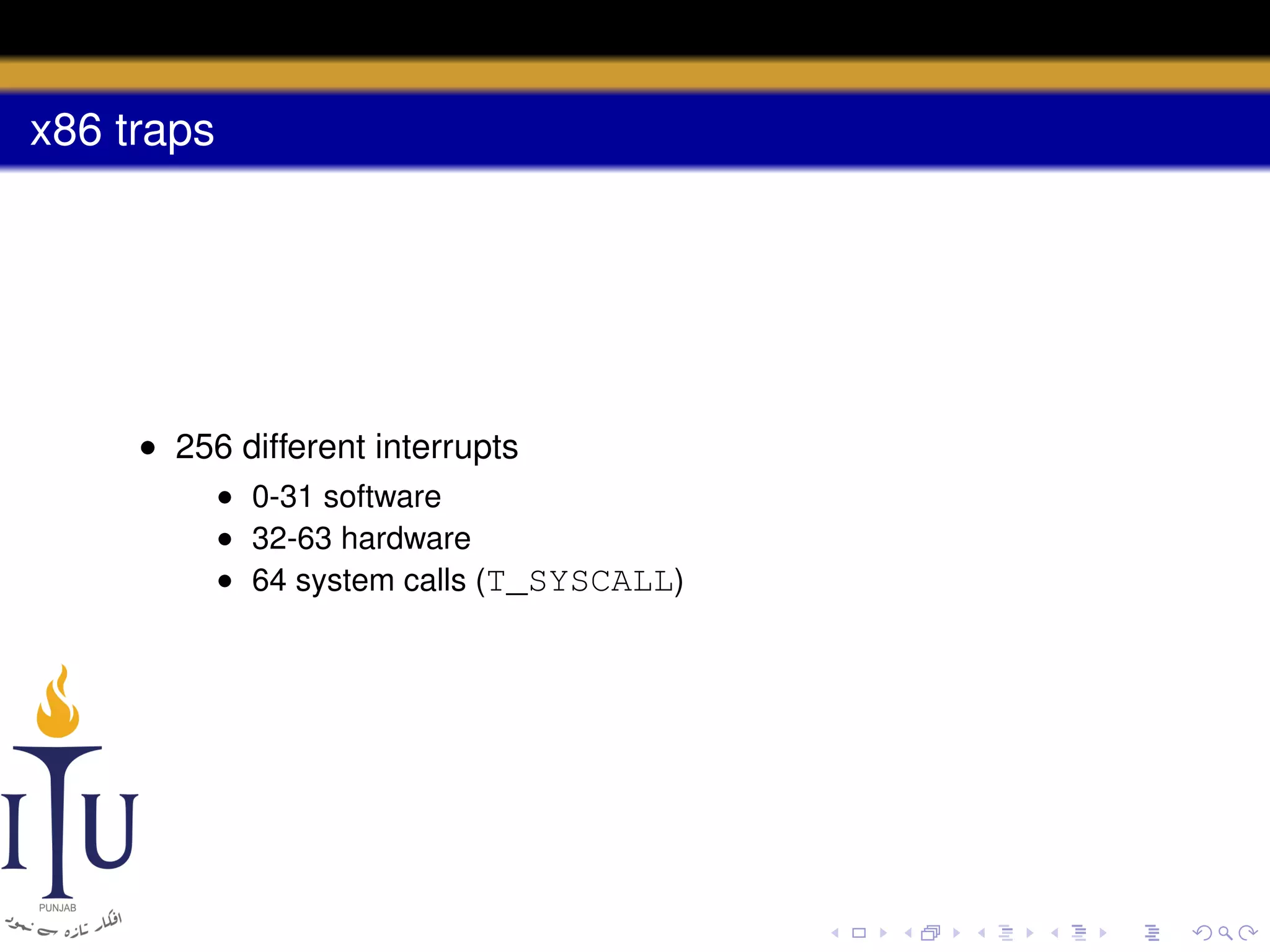
The document discusses system calls and how they are handled in operating systems. It explains that system calls allow user processes to request services from the kernel by generating an interrupt that switches the processor into kernel mode. On x86 processors, the interrupt handler saves process state and routes the call to the appropriate kernel code based on an interrupt descriptor table with 256 entries. The document provides details on how Linux/x86 implements system calls, exceptions, and interrupts using the IDT, and switches between user and kernel mode to maintain isolation.









![The first system call
• Recall that initcode.S started off by invoking an exec
system call to load the init process (/init)
• Flow:
1 Push the arguments and binary for exec on the process’s stack
2 Put the system call number (SYS_exec) in %eax (obviously this
number should already be present in the system call table,
*syscalls[])
3 Execute int T_SYSCALL](https://image.slidesharecdn.com/document-140110160523-phpapp02/75/AOS-Lab-5-System-calls-35-2048.jpg)
![The first system call
• Recall that initcode.S started off by invoking an exec
system call to load the init process (/init)
• Flow:
1 Push the arguments and binary for exec on the process’s stack
2 Put the system call number (SYS_exec) in %eax (obviously this
number should already be present in the system call table,
*syscalls[])
3 Execute int T_SYSCALL](https://image.slidesharecdn.com/document-140110160523-phpapp02/75/AOS-Lab-5-System-calls-36-2048.jpg)
![The first system call
• Recall that initcode.S started off by invoking an exec
system call to load the init process (/init)
• Flow:
1 Push the arguments and binary for exec on the process’s stack
2 Put the system call number (SYS_exec) in %eax (obviously this
number should already be present in the system call table,
*syscalls[])
3 Execute int T_SYSCALL](https://image.slidesharecdn.com/document-140110160523-phpapp02/75/AOS-Lab-5-System-calls-37-2048.jpg)
![The first system call
• Recall that initcode.S started off by invoking an exec
system call to load the init process (/init)
• Flow:
1 Push the arguments and binary for exec on the process’s stack
2 Put the system call number (SYS_exec) in %eax (obviously this
number should already be present in the system call table,
*syscalls[])
3 Execute int T_SYSCALL](https://image.slidesharecdn.com/document-140110160523-phpapp02/75/AOS-Lab-5-System-calls-38-2048.jpg)
![The first system call
• Recall that initcode.S started off by invoking an exec
system call to load the init process (/init)
• Flow:
1 Push the arguments and binary for exec on the process’s stack
2 Put the system call number (SYS_exec) in %eax (obviously this
number should already be present in the system call table,
*syscalls[])
3 Execute int T_SYSCALL](https://image.slidesharecdn.com/document-140110160523-phpapp02/75/AOS-Lab-5-System-calls-39-2048.jpg)
![Setting up idt
• tvinit, called from main, sets up the entries in idt
• The address of the handler for each interrupt in idt is present in
vectors[], i.e. Interrupt i is handled by vectors[i]
• T_SYSCALL is handled specially: it is distinguished as a trap
allowing multiple system calls to execute simultaneously](https://image.slidesharecdn.com/document-140110160523-phpapp02/75/AOS-Lab-5-System-calls-44-2048.jpg)
![Setting up idt
• tvinit, called from main, sets up the entries in idt
• The address of the handler for each interrupt in idt is present in
vectors[], i.e. Interrupt i is handled by vectors[i]
• T_SYSCALL is handled specially: it is distinguished as a trap
allowing multiple system calls to execute simultaneously](https://image.slidesharecdn.com/document-140110160523-phpapp02/75/AOS-Lab-5-System-calls-45-2048.jpg)
![Setting up idt
• tvinit, called from main, sets up the entries in idt
• The address of the handler for each interrupt in idt is present in
vectors[], i.e. Interrupt i is handled by vectors[i]
• T_SYSCALL is handled specially: it is distinguished as a trap
allowing multiple system calls to execute simultaneously](https://image.slidesharecdn.com/document-140110160523-phpapp02/75/AOS-Lab-5-System-calls-46-2048.jpg)
![tvinit
1
2
3
4
5
6
7
8
9
10
11
12
13
14
void tvinit (void) {
int i;
for(i = 0; i < 256; i++)
SETGATE (idt[i], 0, SEG_KCODE <<3, vectors [i], 0);
SETGATE (idt[ T_SYSCALL ], 1, SEG_KCODE <<3,
vectors [ T_SYSCALL ], DPL_USER );
/∗ SETGATE (gate , istrap , sel , off , d)
∗
∗
∗
∗
∗
gate: idt entry
istrap : 1 trap , 0 interrupt
sel: code segment
off: offset within code segment
d: privilege level
∗/
initlock (& tickslock , "time");
}](https://image.slidesharecdn.com/document-140110160523-phpapp02/75/AOS-Lab-5-System-calls-47-2048.jpg)
![Addresses of interrupt handlers
• xv6 uses a custom Perl script vectors.pl to generate
vectors.S which holds entry points of interrupt handlers in
vectors[]
• Each entry point:
Pushes an error code
Pushes the interrupt number
3 Jumps to alltraps
1
2](https://image.slidesharecdn.com/document-140110160523-phpapp02/75/AOS-Lab-5-System-calls-48-2048.jpg)
![Addresses of interrupt handlers
• xv6 uses a custom Perl script vectors.pl to generate
vectors.S which holds entry points of interrupt handlers in
vectors[]
• Each entry point:
Pushes an error code
Pushes the interrupt number
3 Jumps to alltraps
1
2](https://image.slidesharecdn.com/document-140110160523-phpapp02/75/AOS-Lab-5-System-calls-49-2048.jpg)
![Addresses of interrupt handlers
• xv6 uses a custom Perl script vectors.pl to generate
vectors.S which holds entry points of interrupt handlers in
vectors[]
• Each entry point:
Pushes an error code
Pushes the interrupt number
3 Jumps to alltraps
1
2](https://image.slidesharecdn.com/document-140110160523-phpapp02/75/AOS-Lab-5-System-calls-50-2048.jpg)
![Addresses of interrupt handlers
• xv6 uses a custom Perl script vectors.pl to generate
vectors.S which holds entry points of interrupt handlers in
vectors[]
• Each entry point:
Pushes an error code
Pushes the interrupt number
3 Jumps to alltraps
1
2](https://image.slidesharecdn.com/document-140110160523-phpapp02/75/AOS-Lab-5-System-calls-51-2048.jpg)