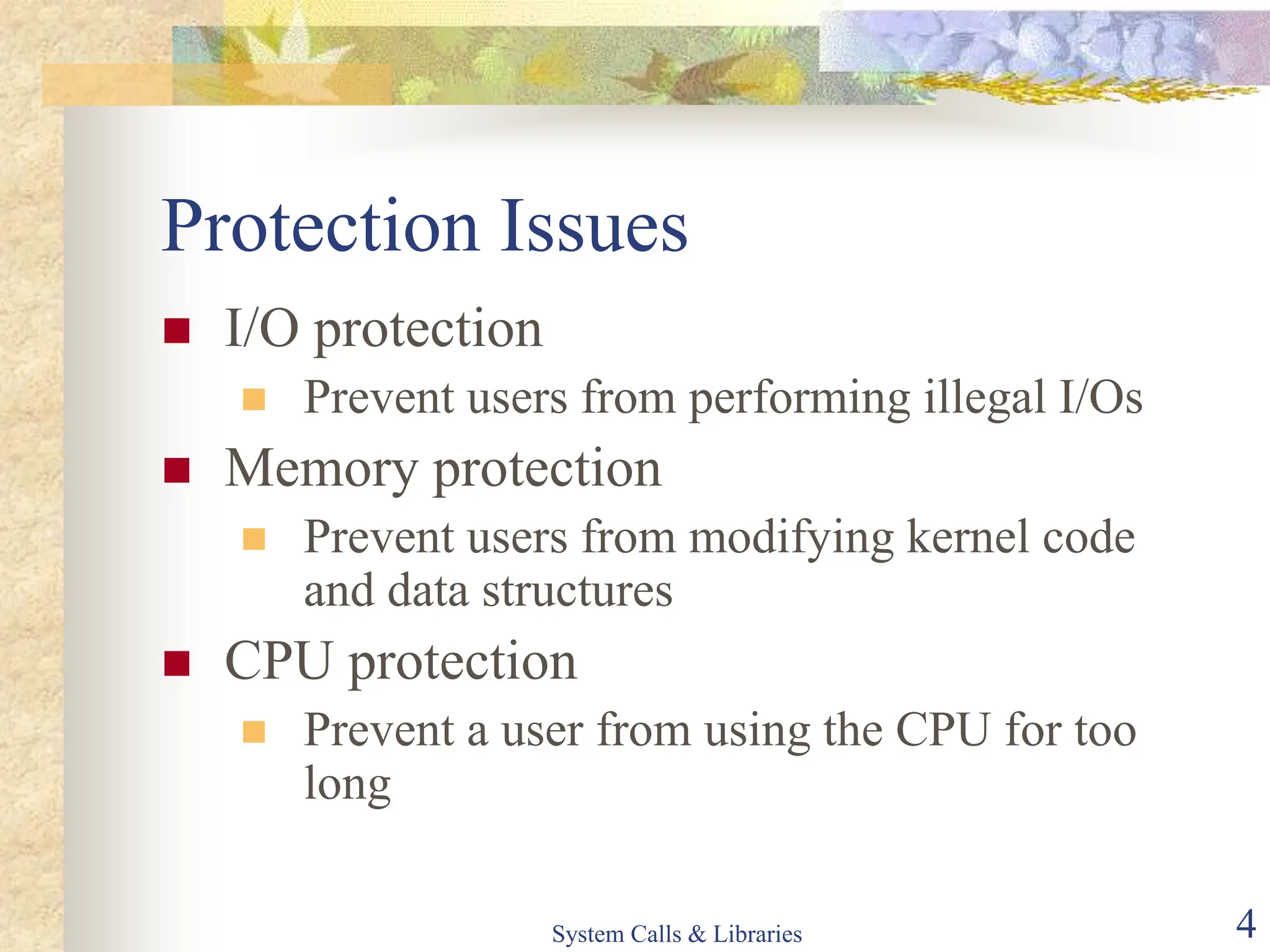
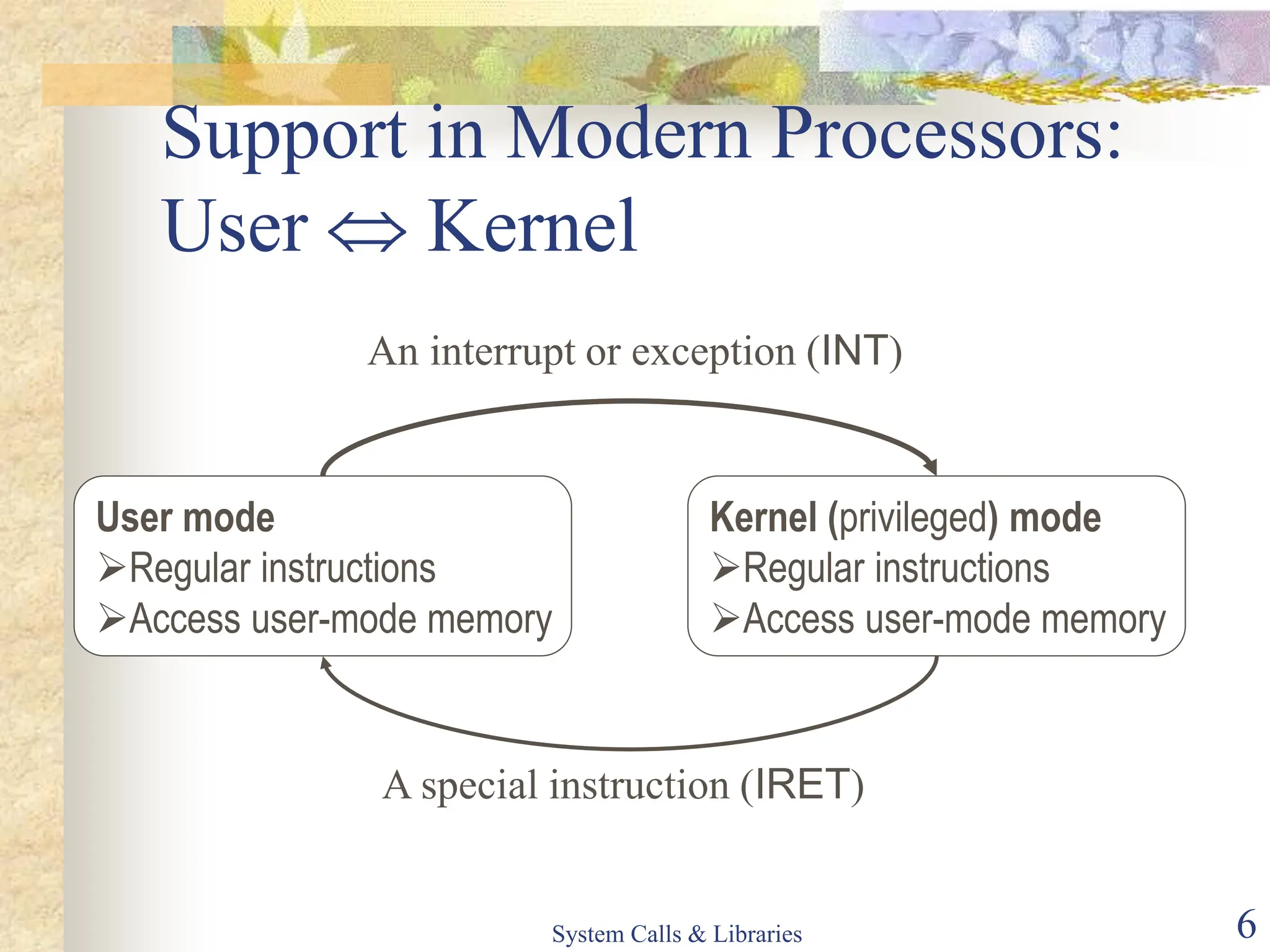
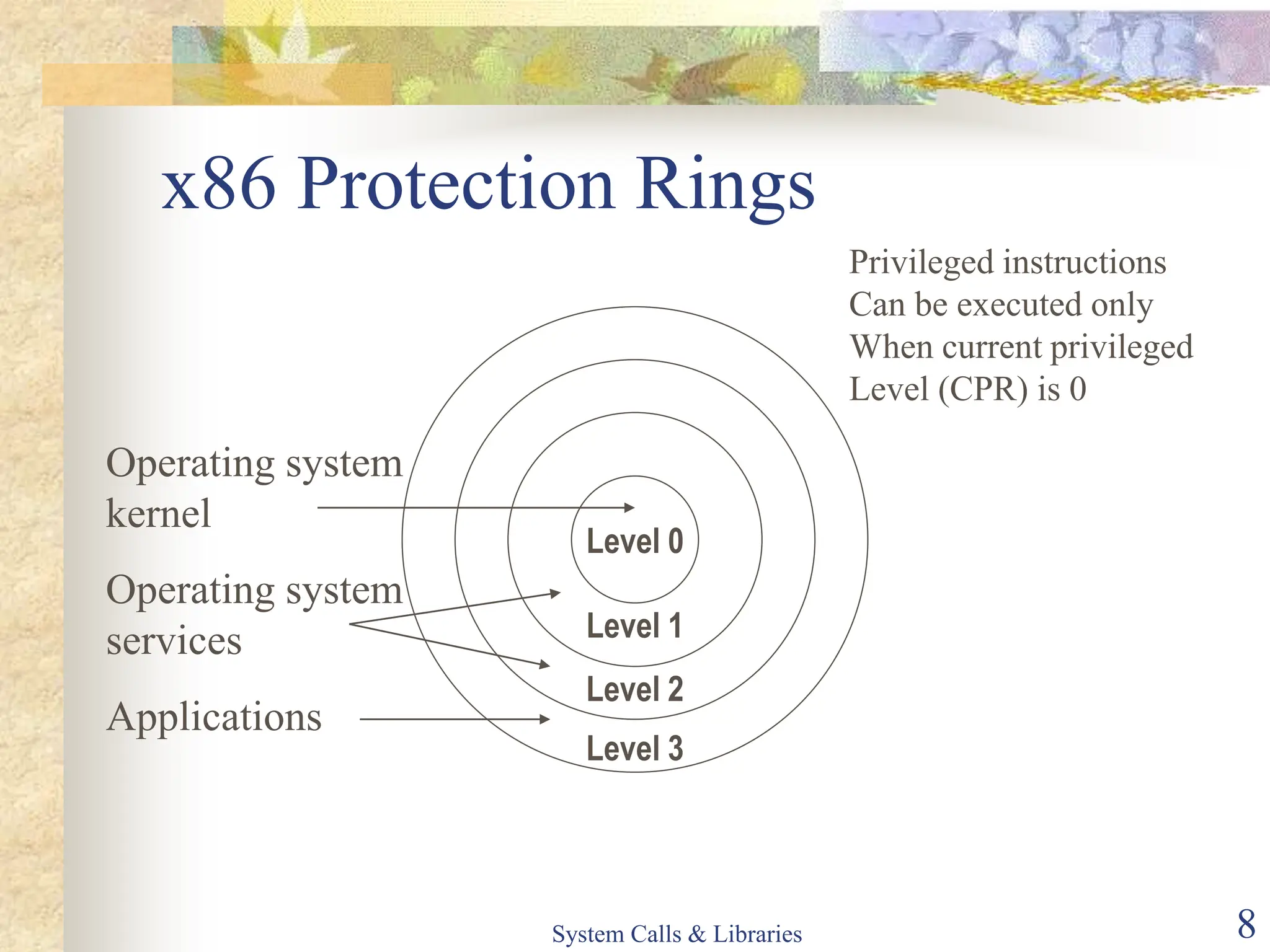
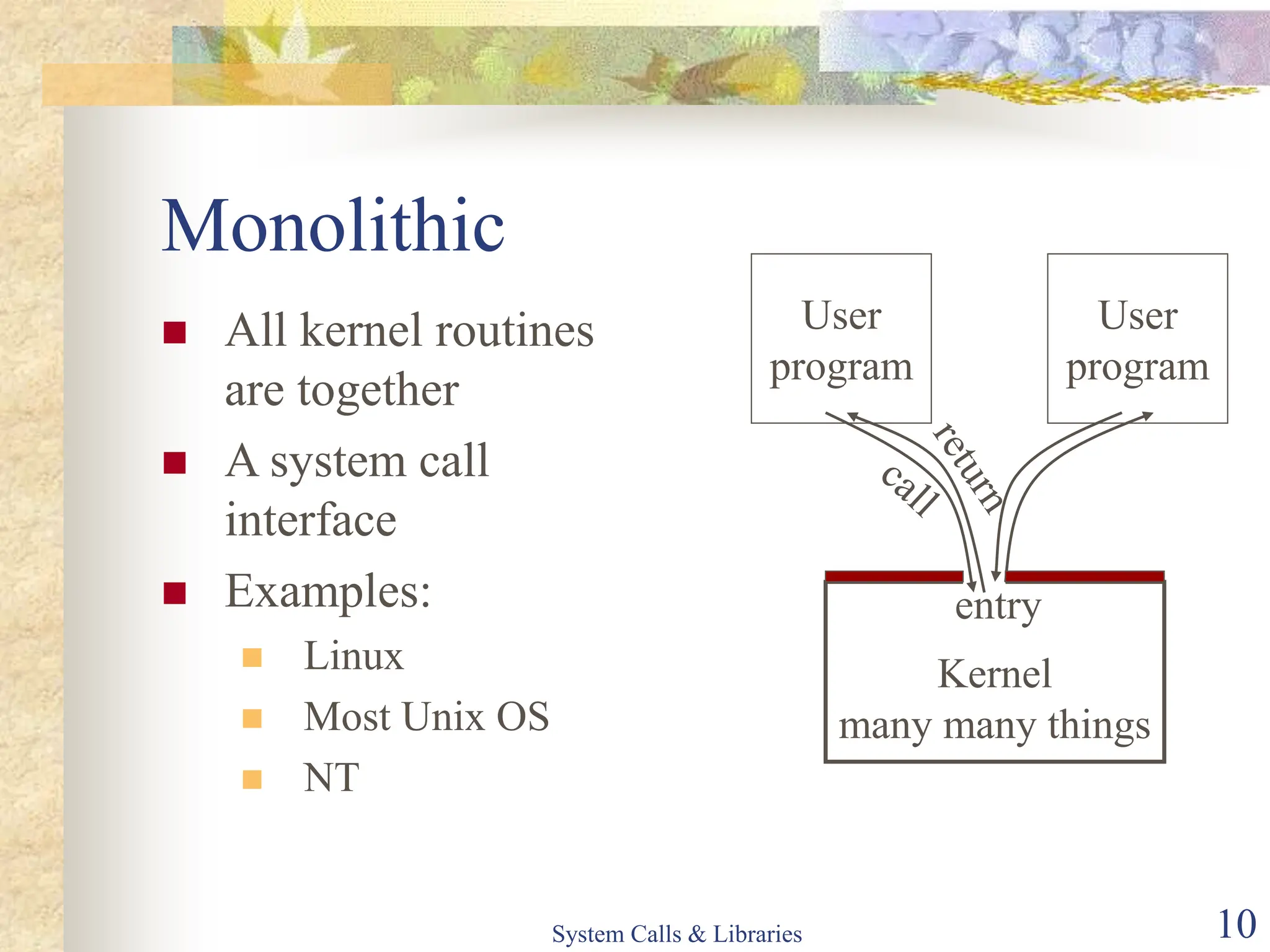
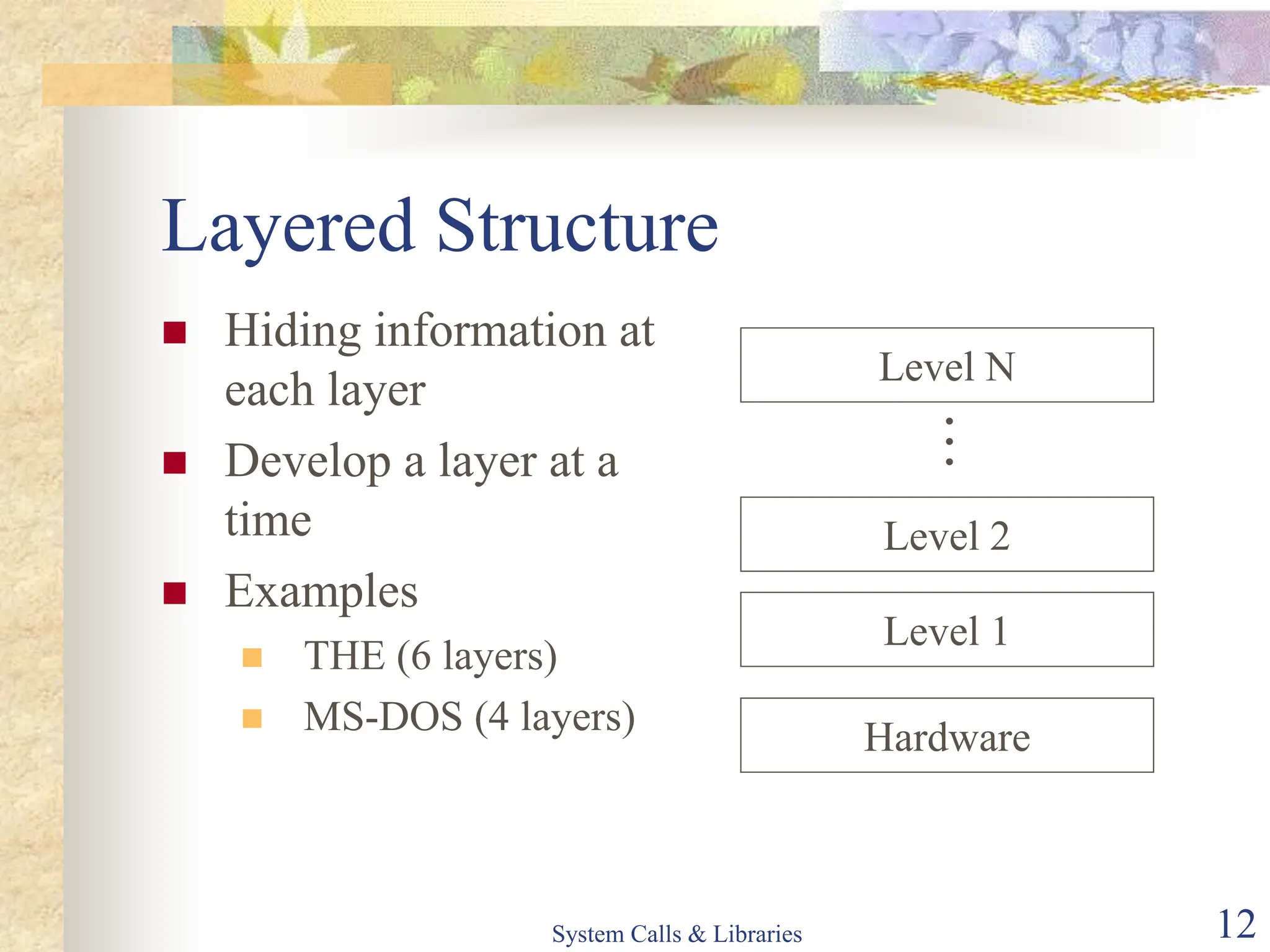
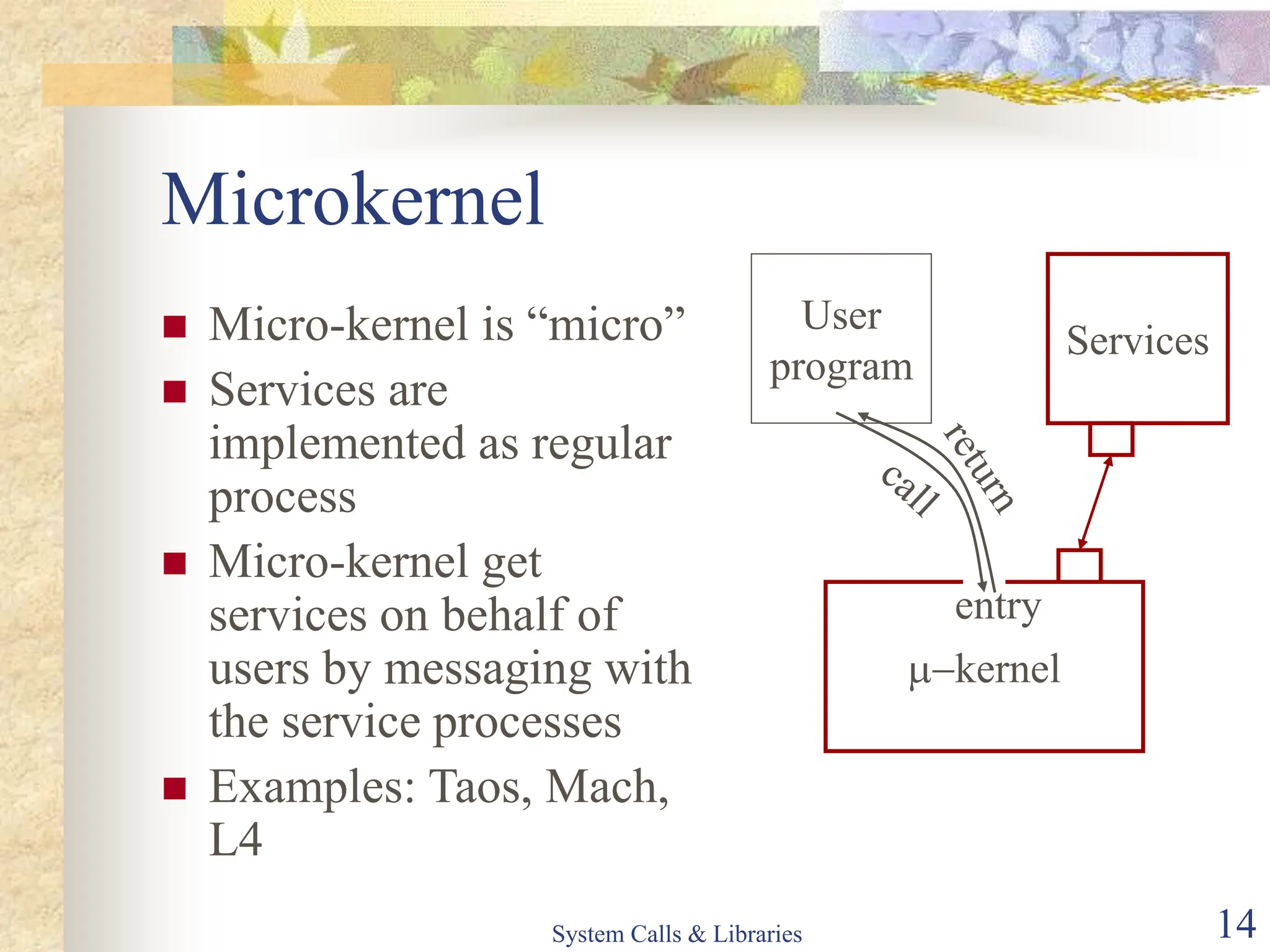
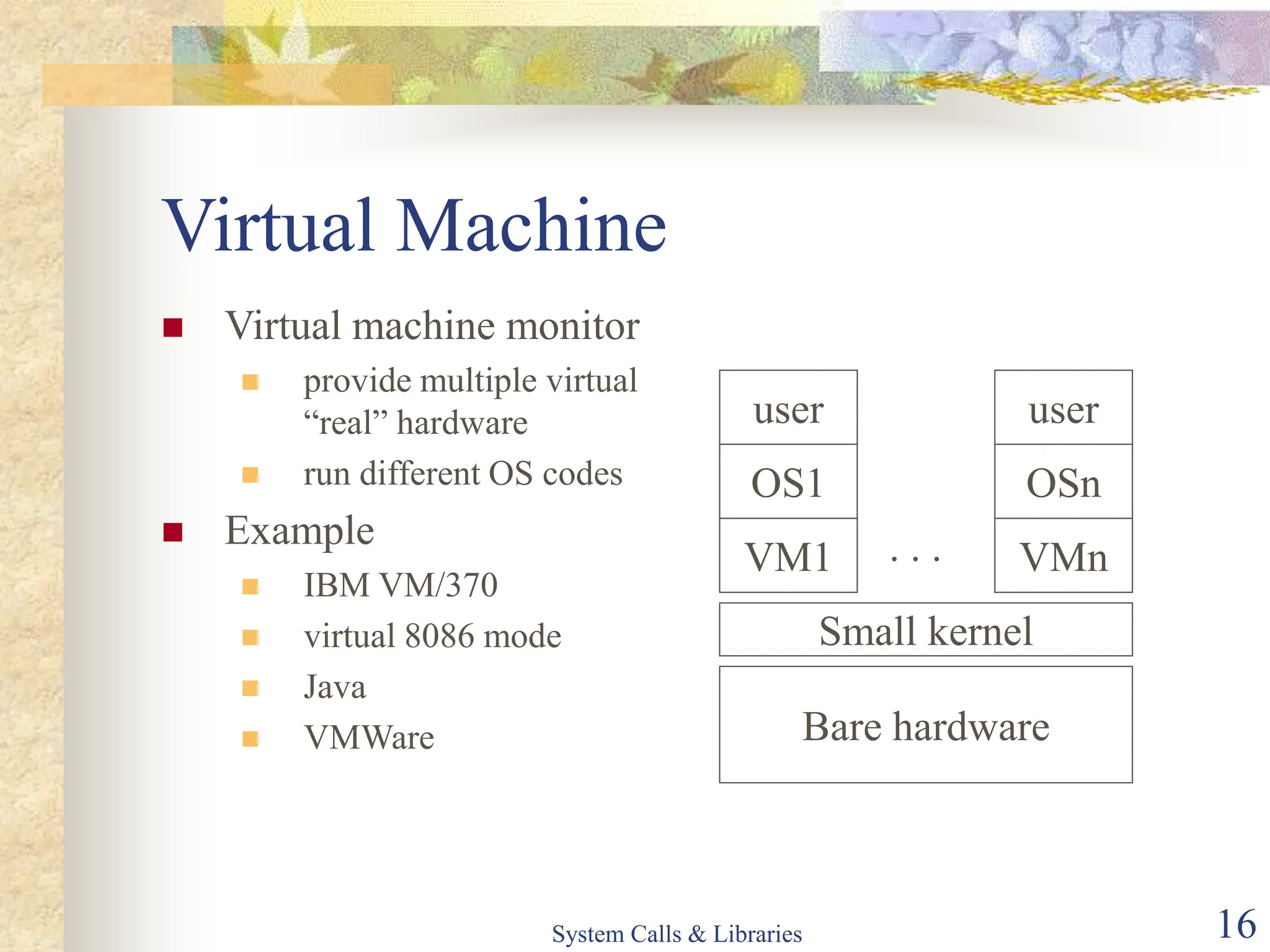
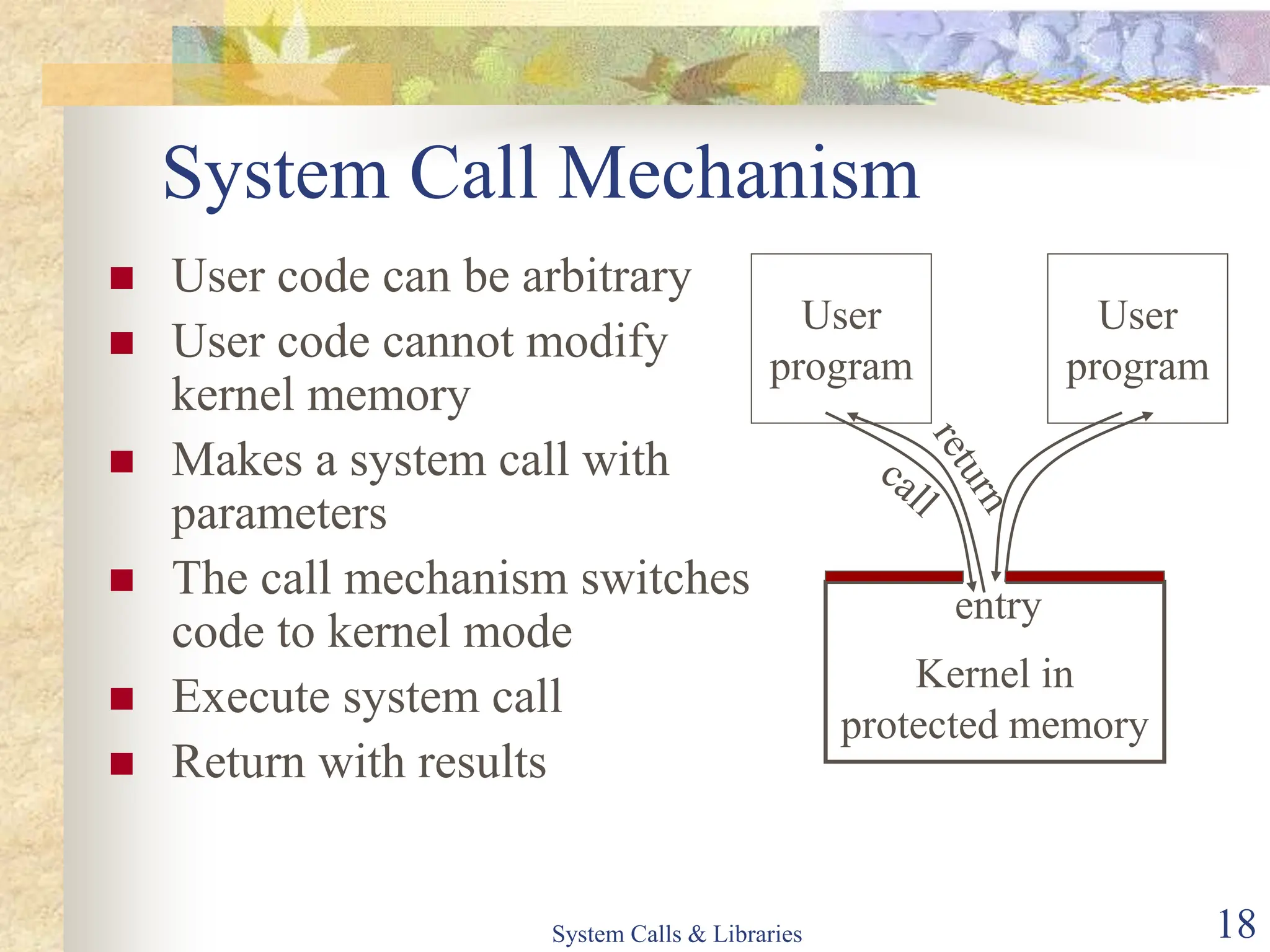
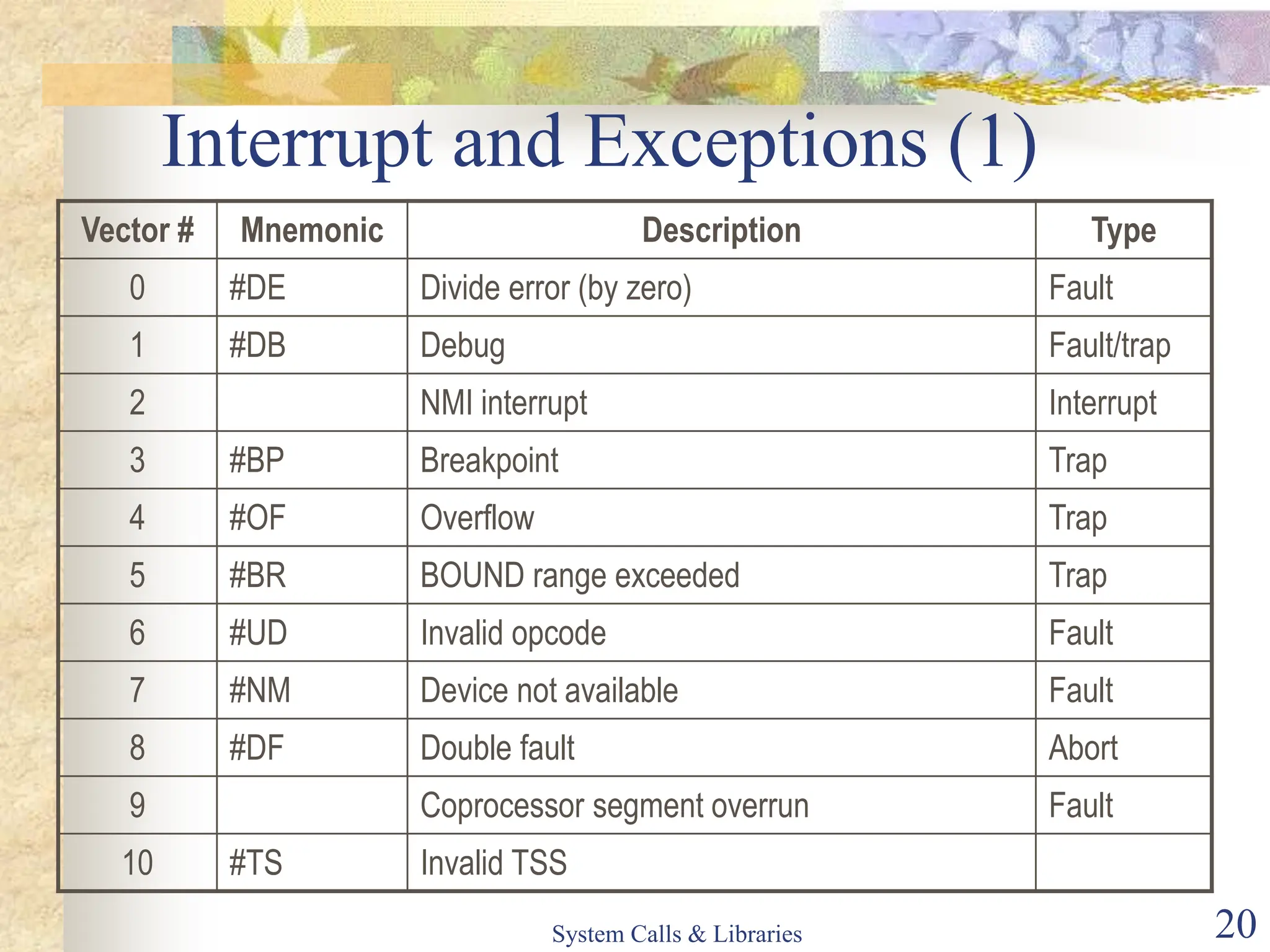
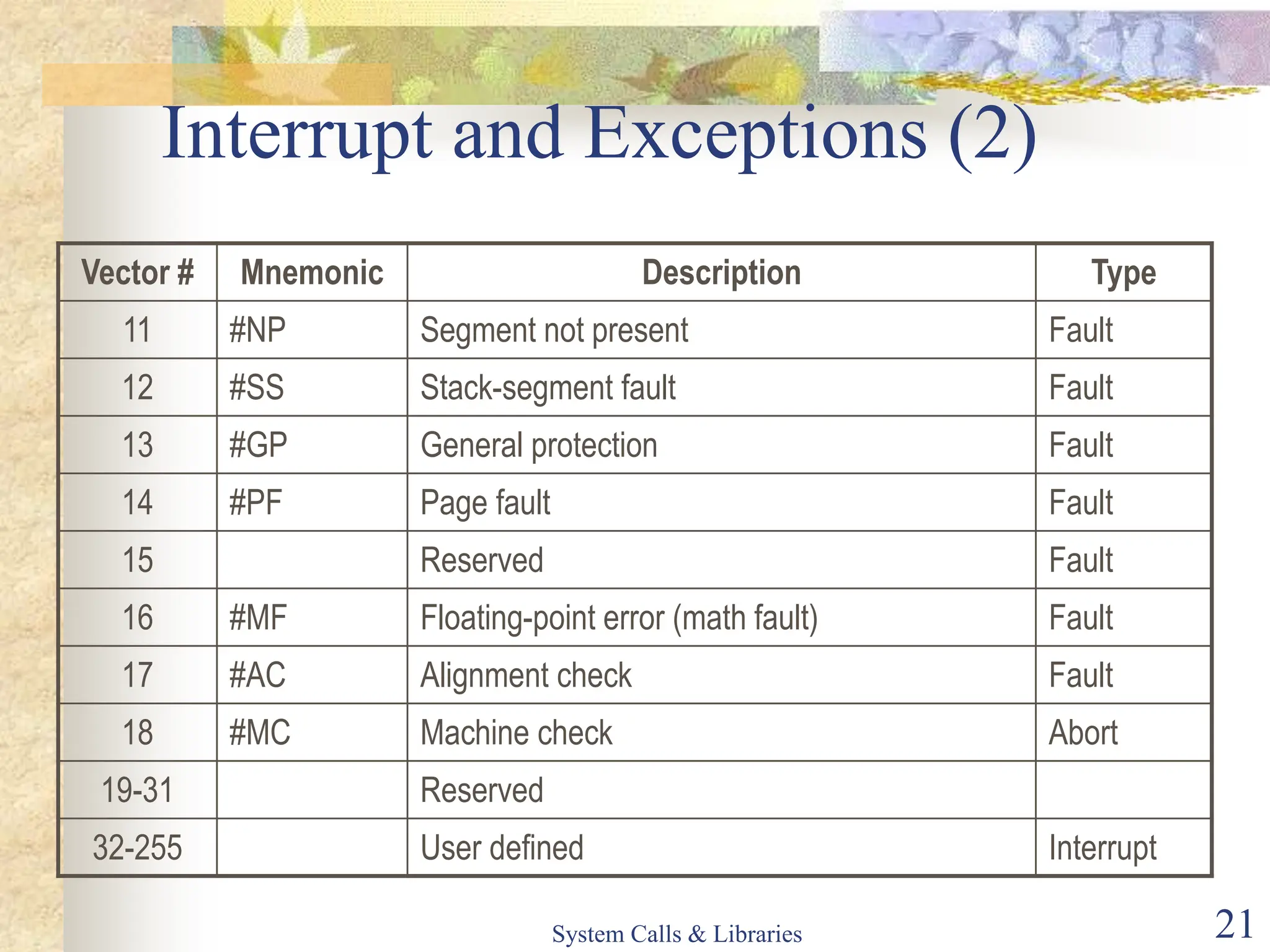
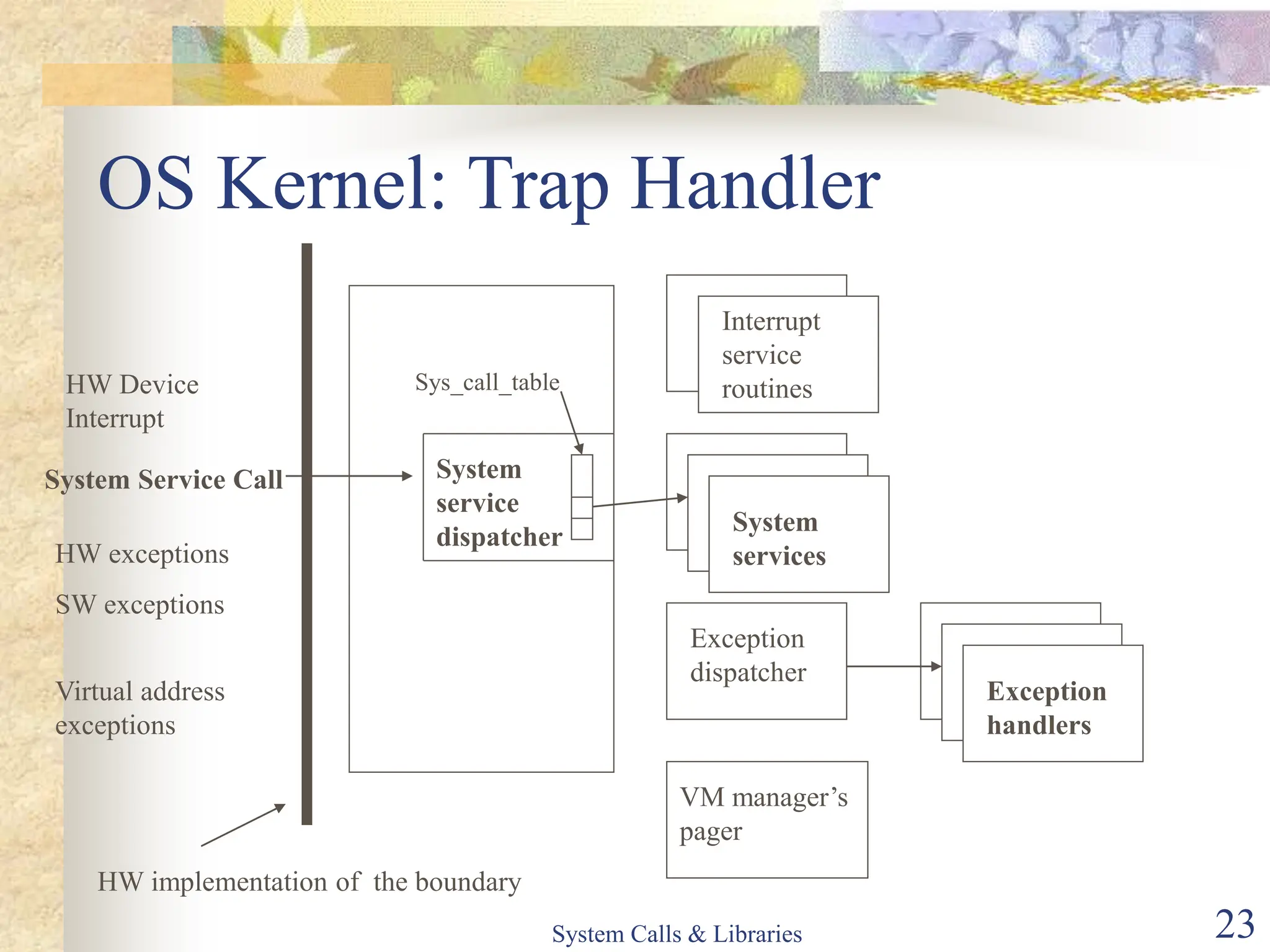
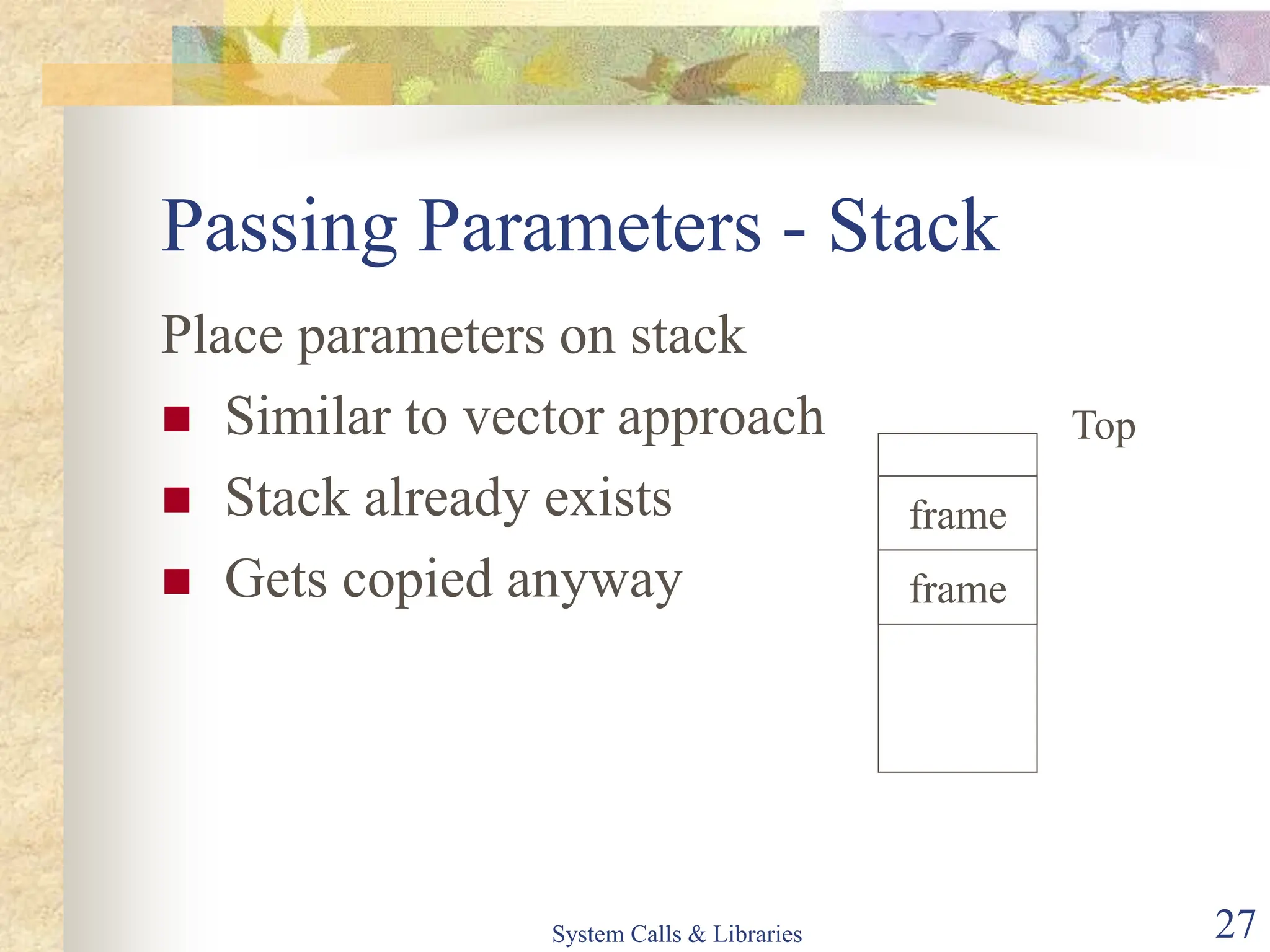
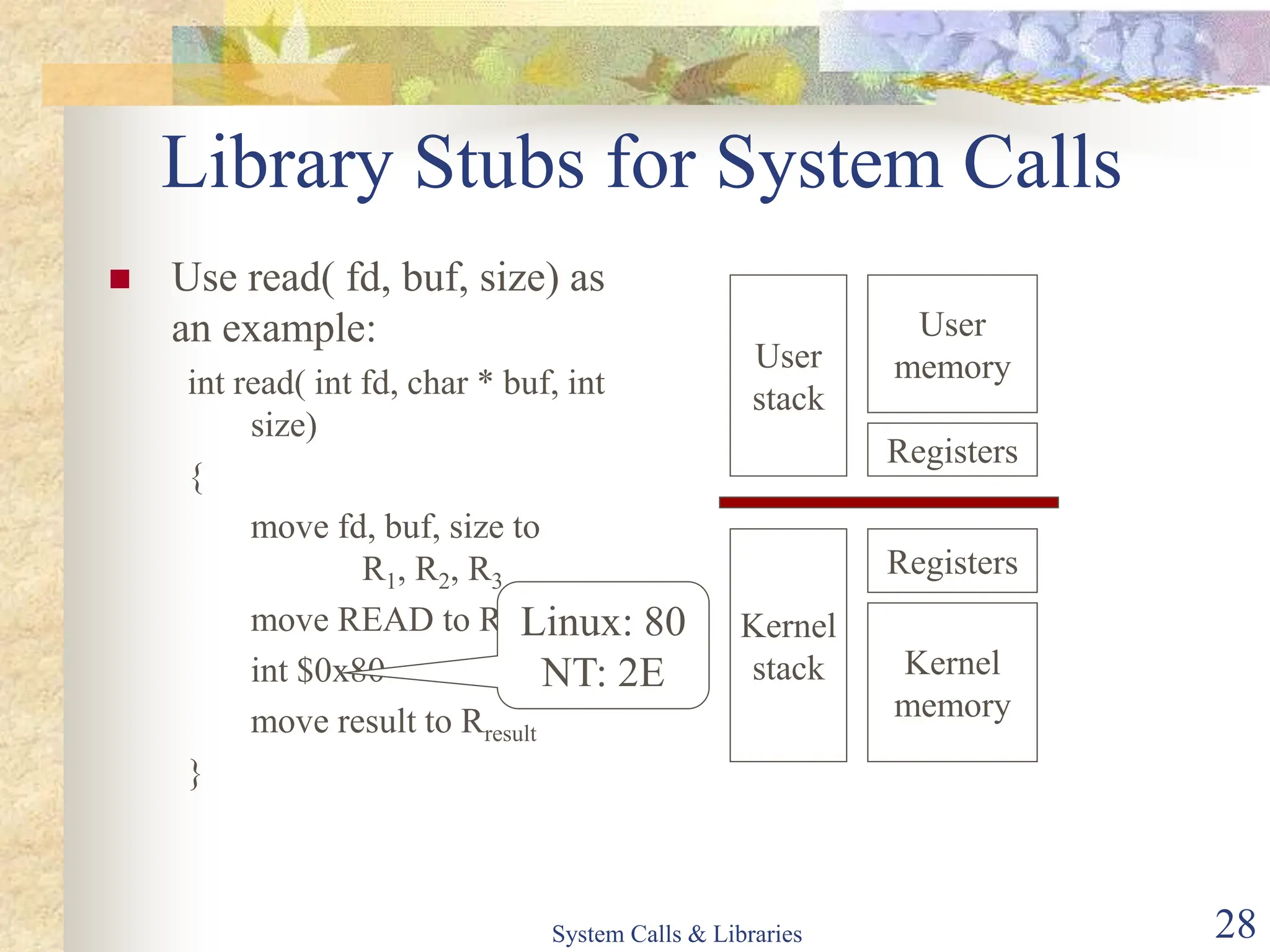
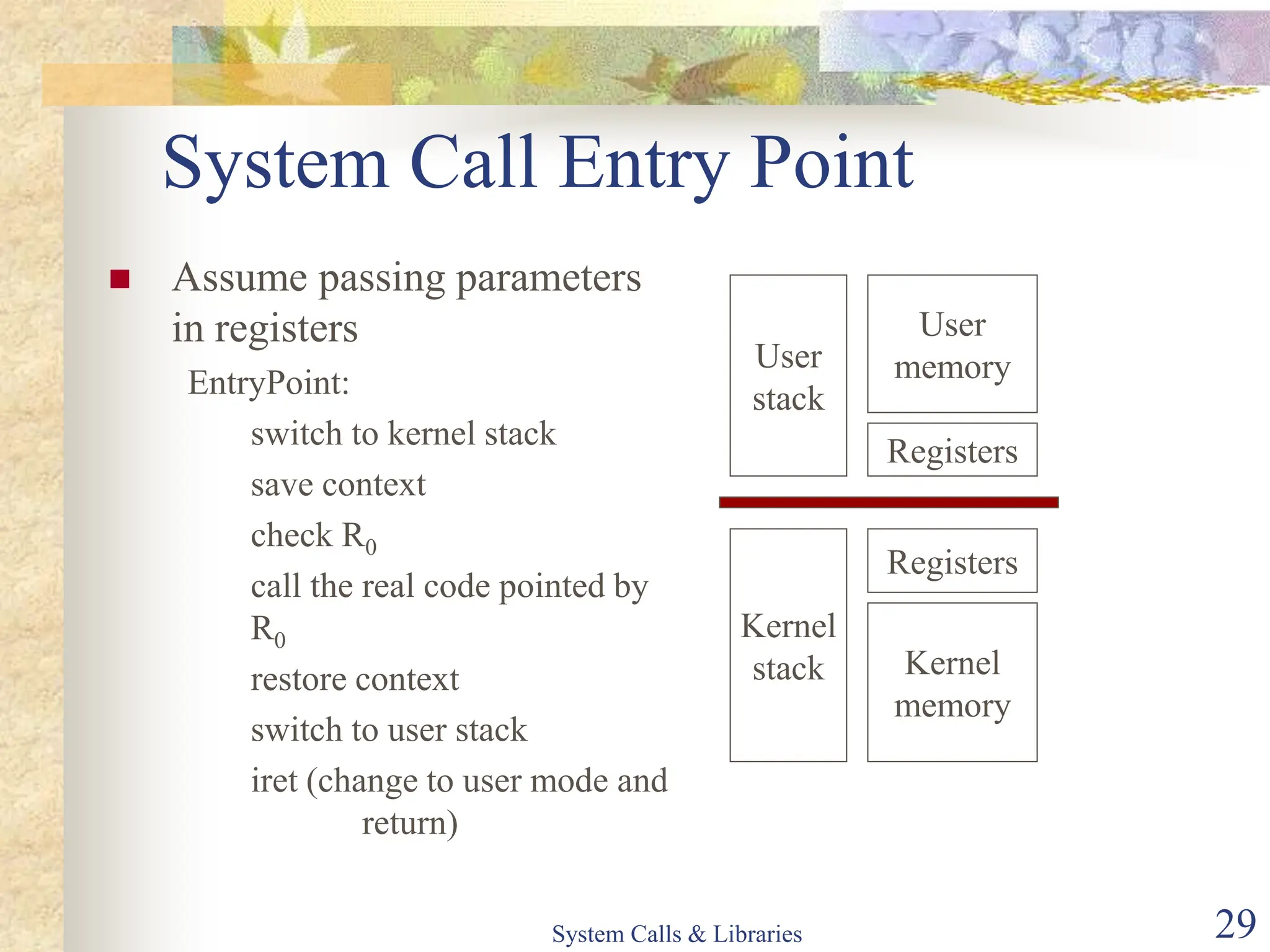
The document covers key concepts of system calls and libraries, focusing on protections, mechanisms, and types of system calls used in operating systems. It discusses different kernel architectures including monolithic, layered, and microkernel designs, alongside performance considerations and parameter passing methods. Additionally, it highlights the interactions between user processes and the OS kernel, as well as various exceptions and interrupts.