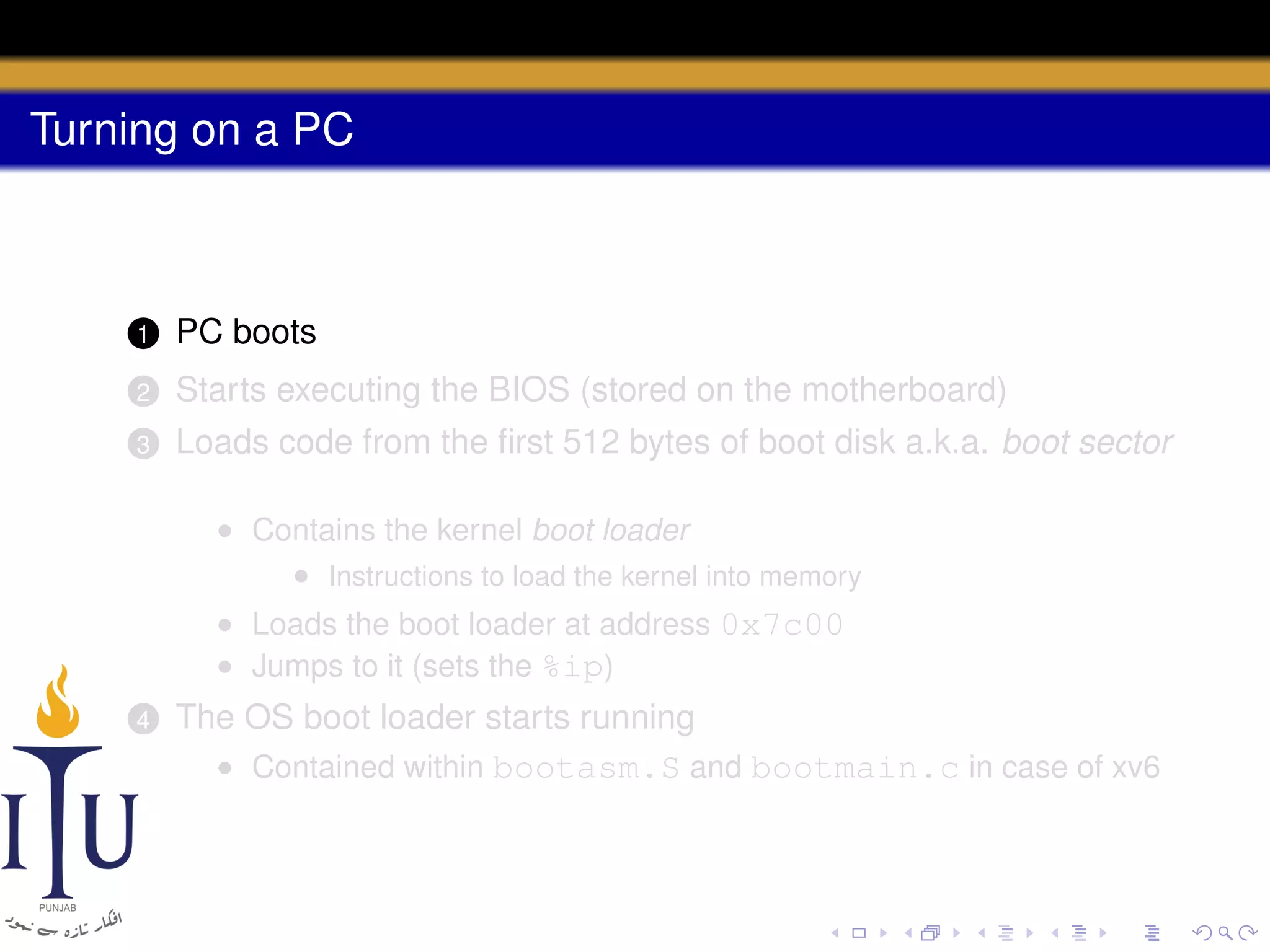
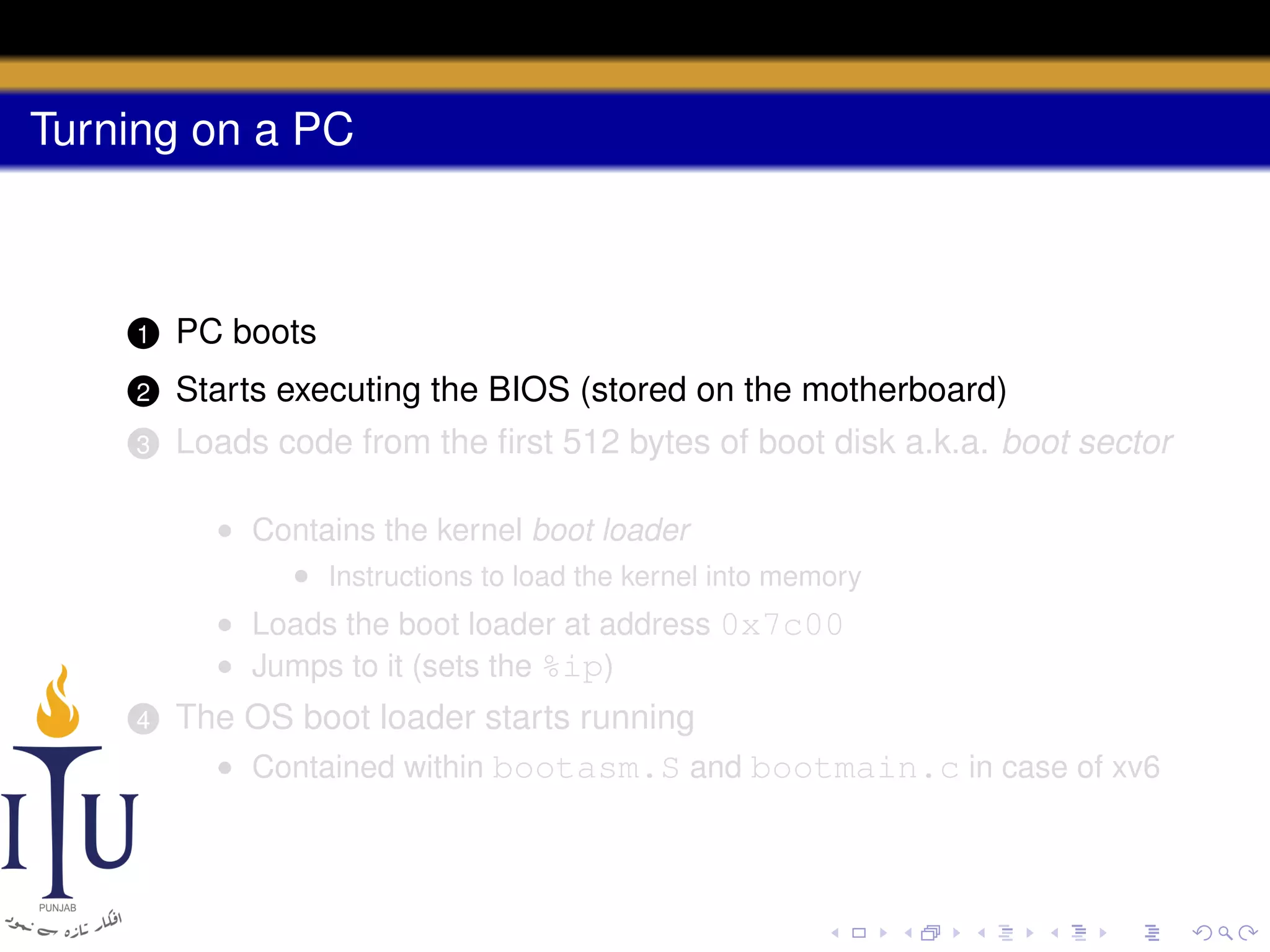
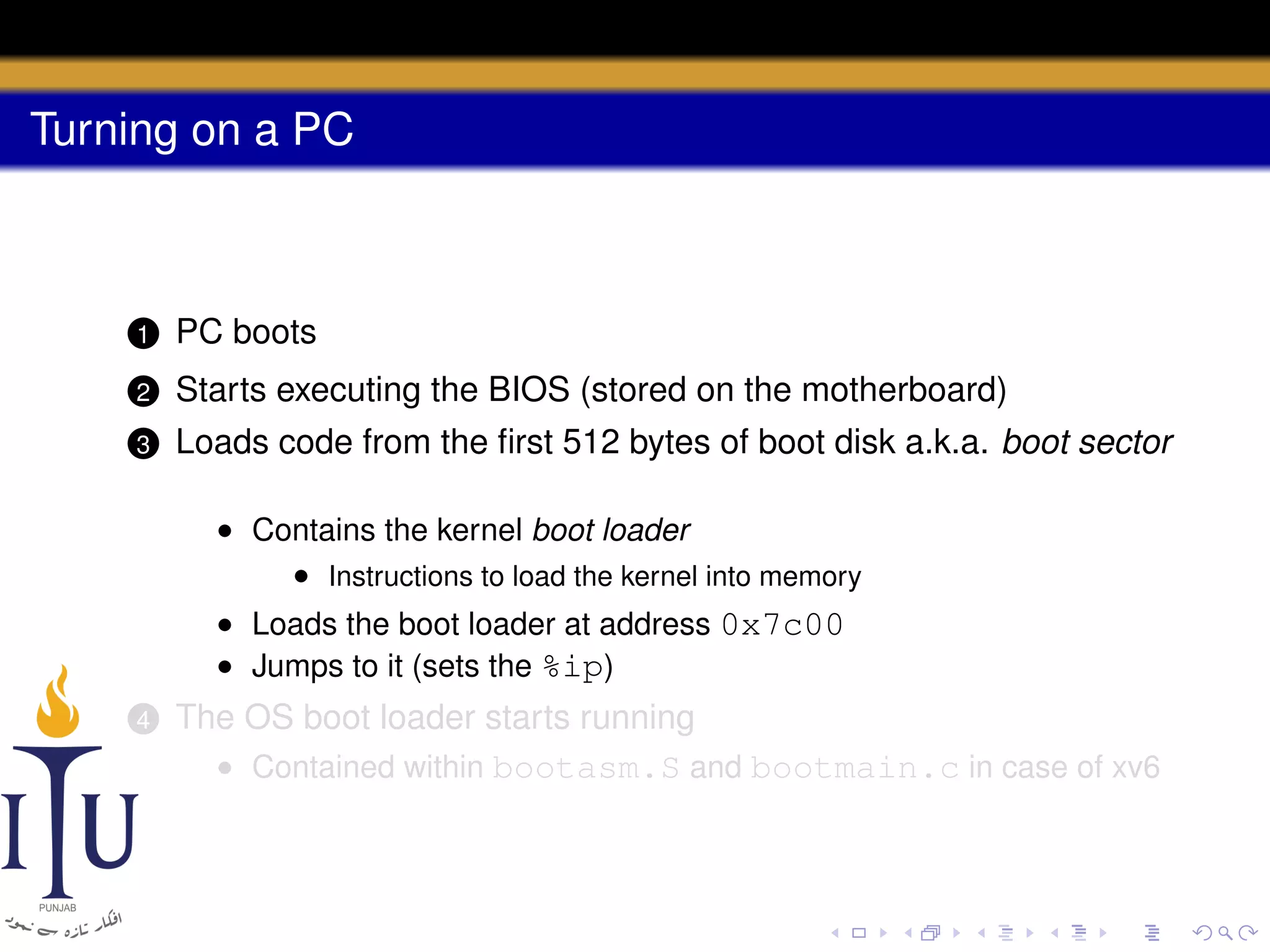
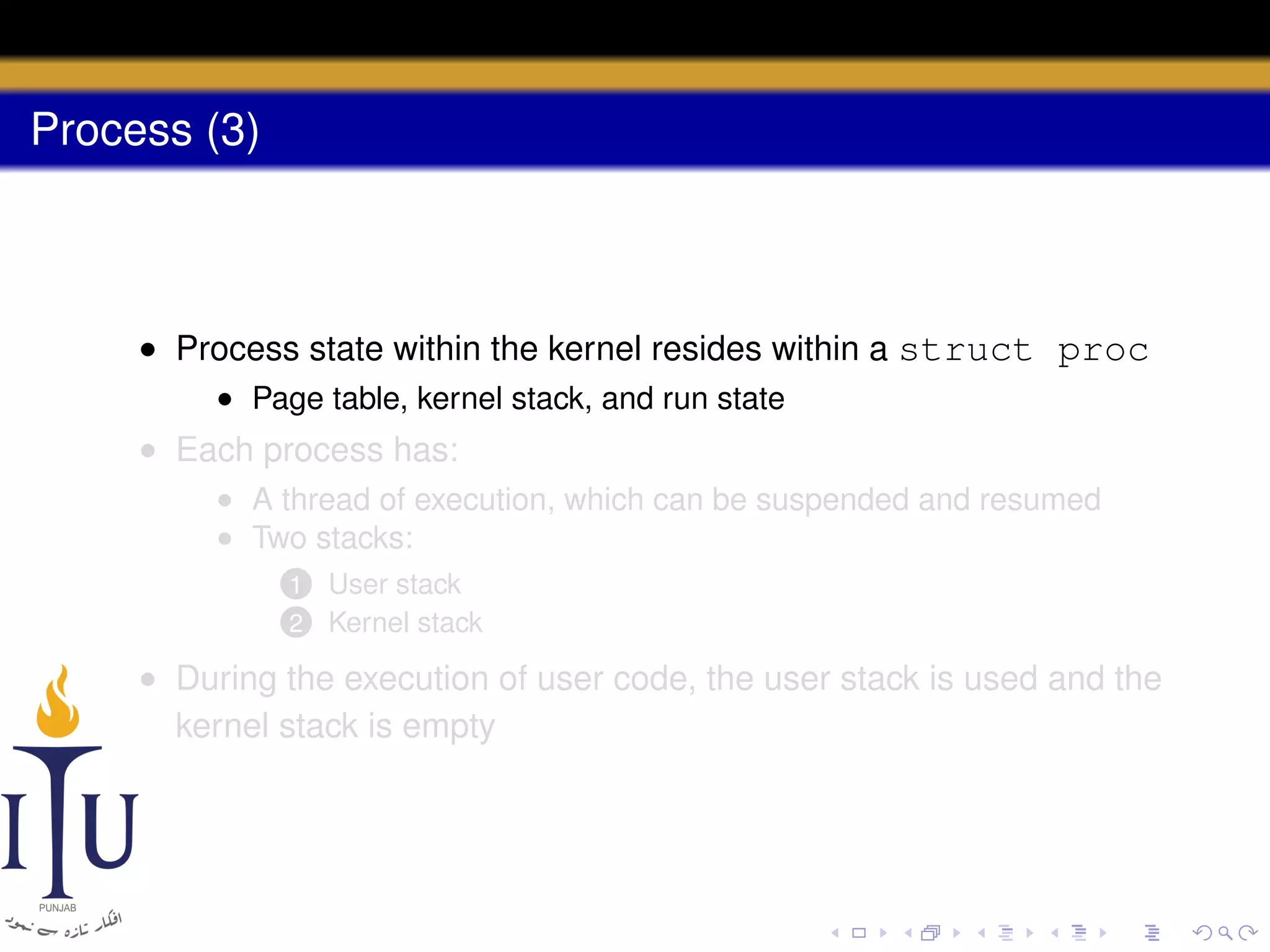
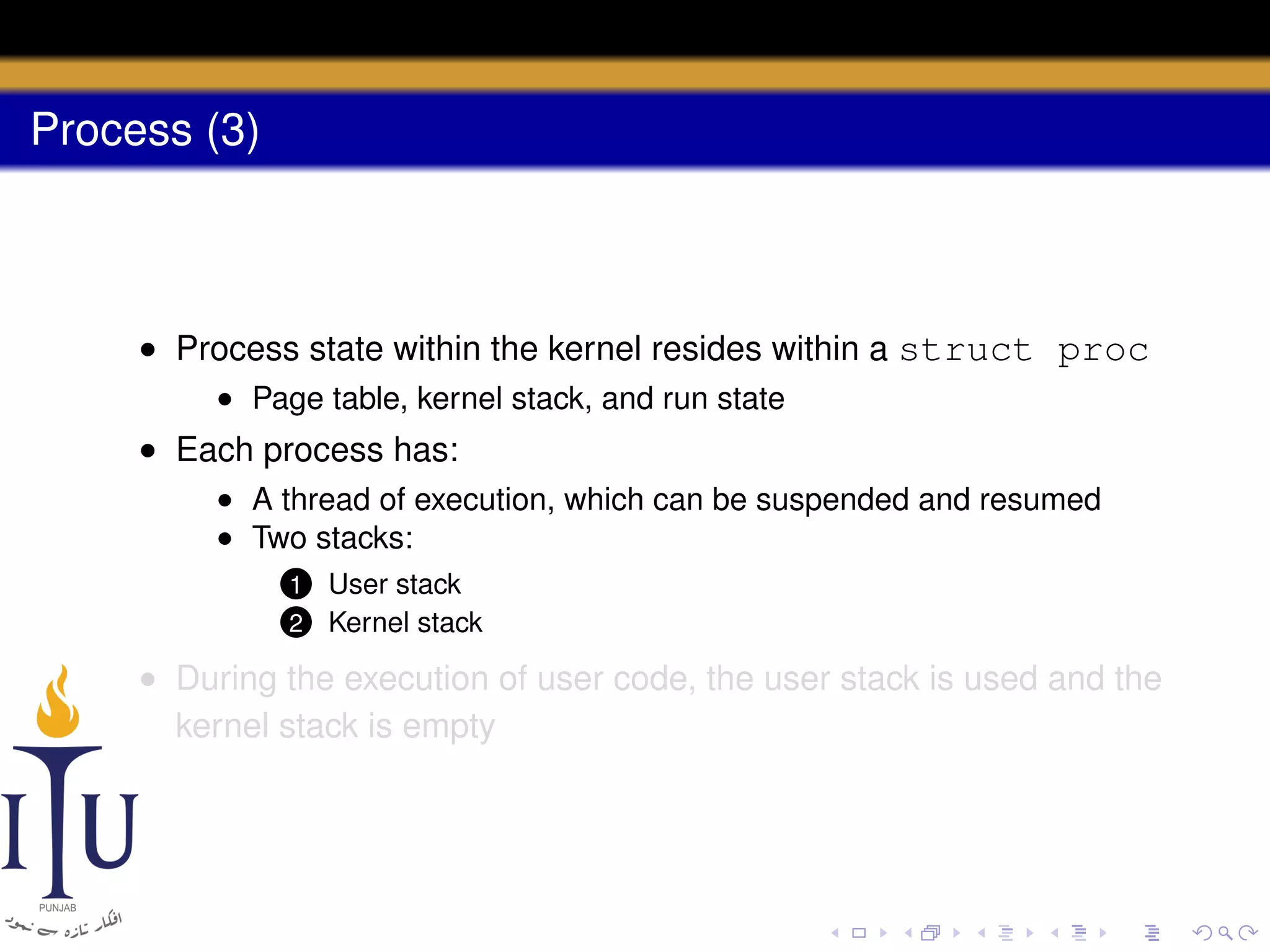
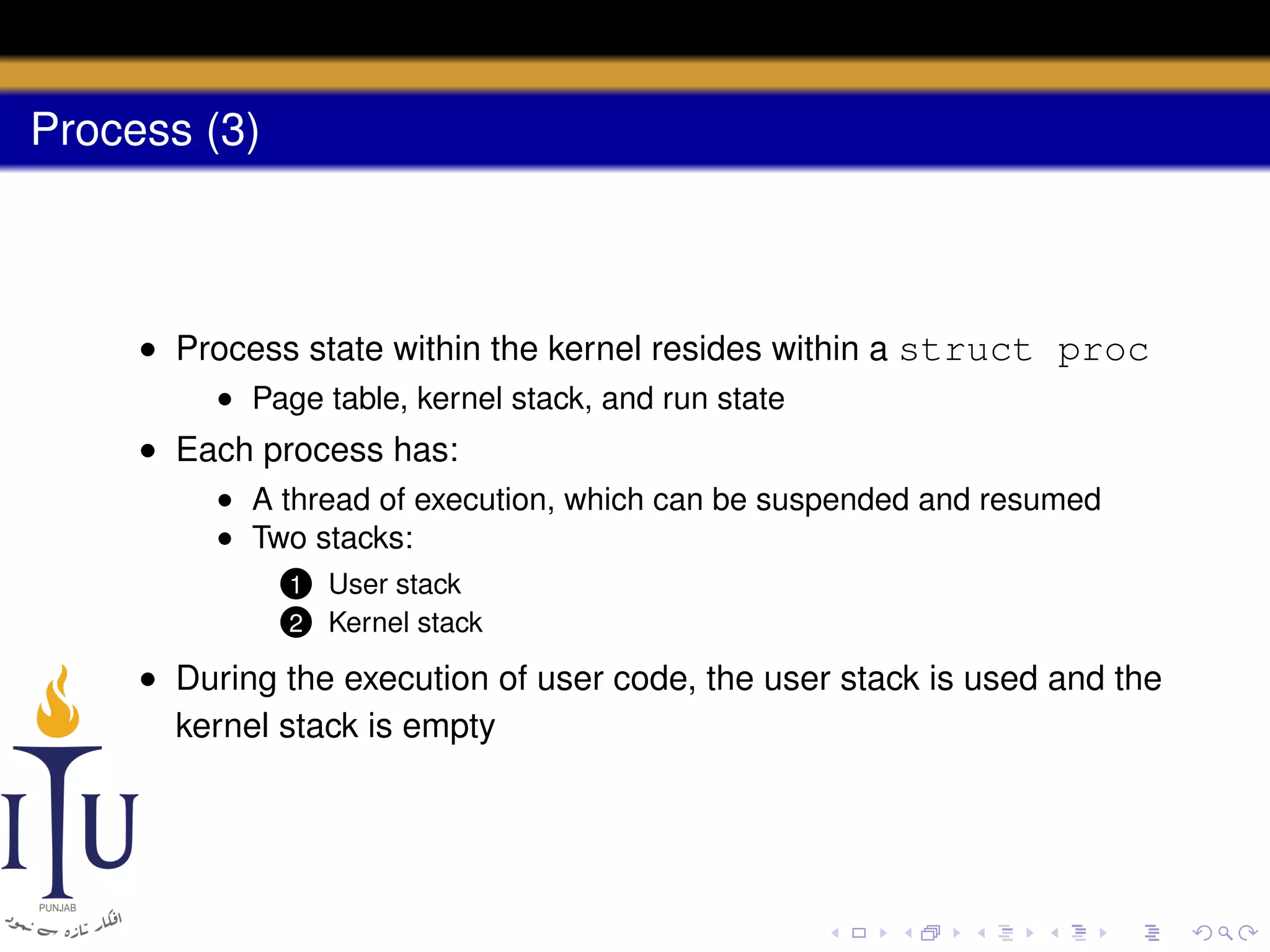
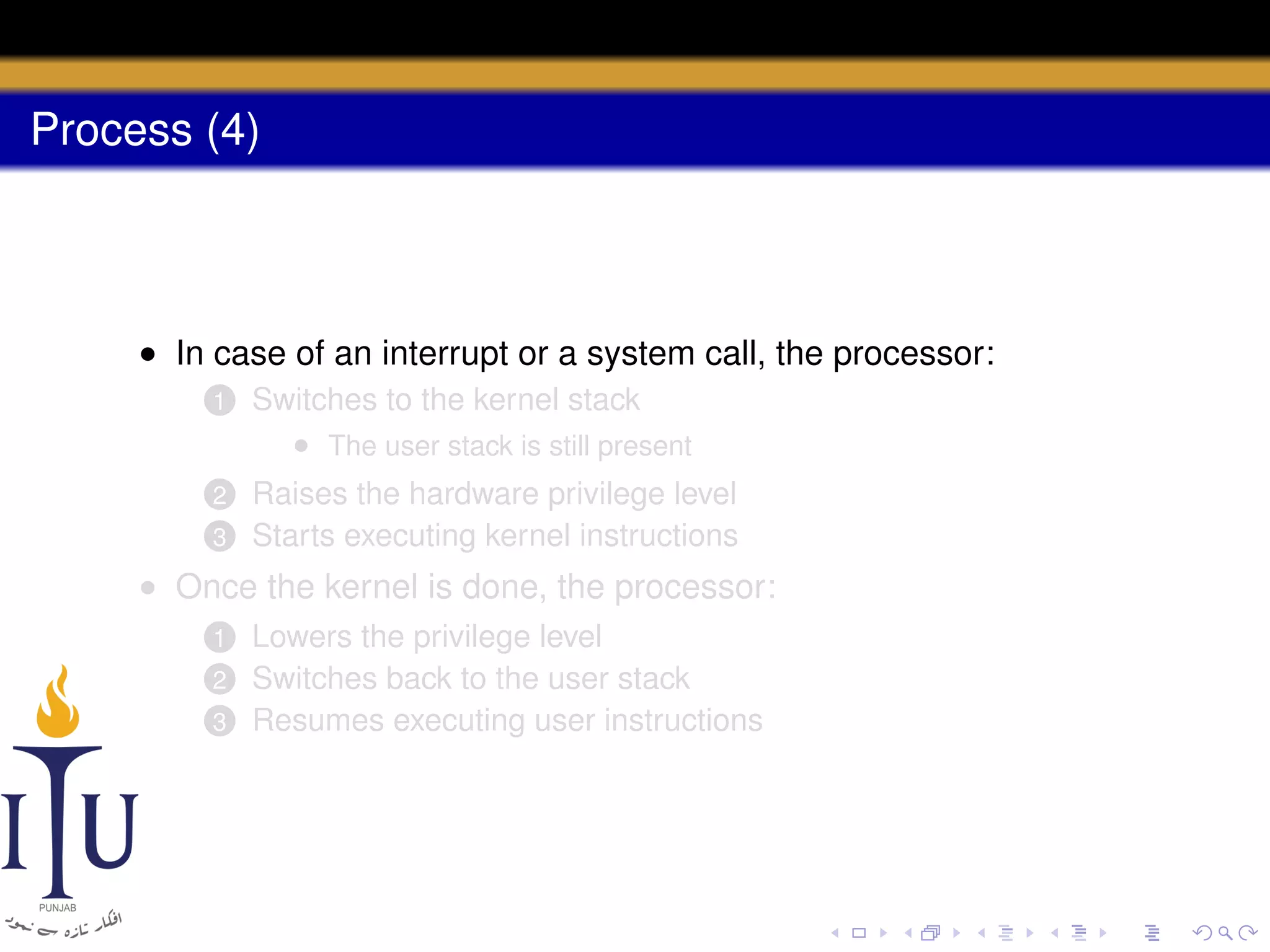
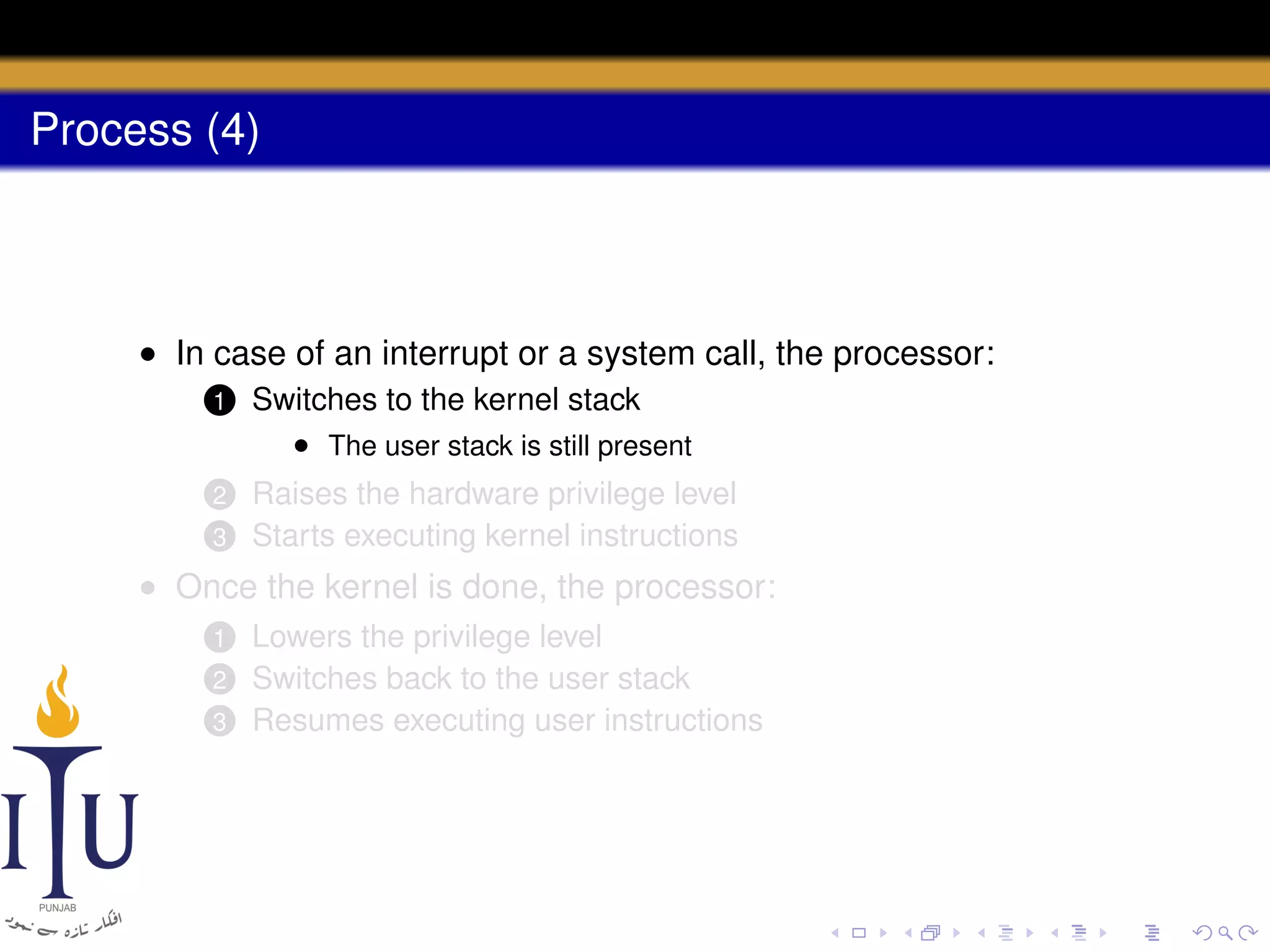
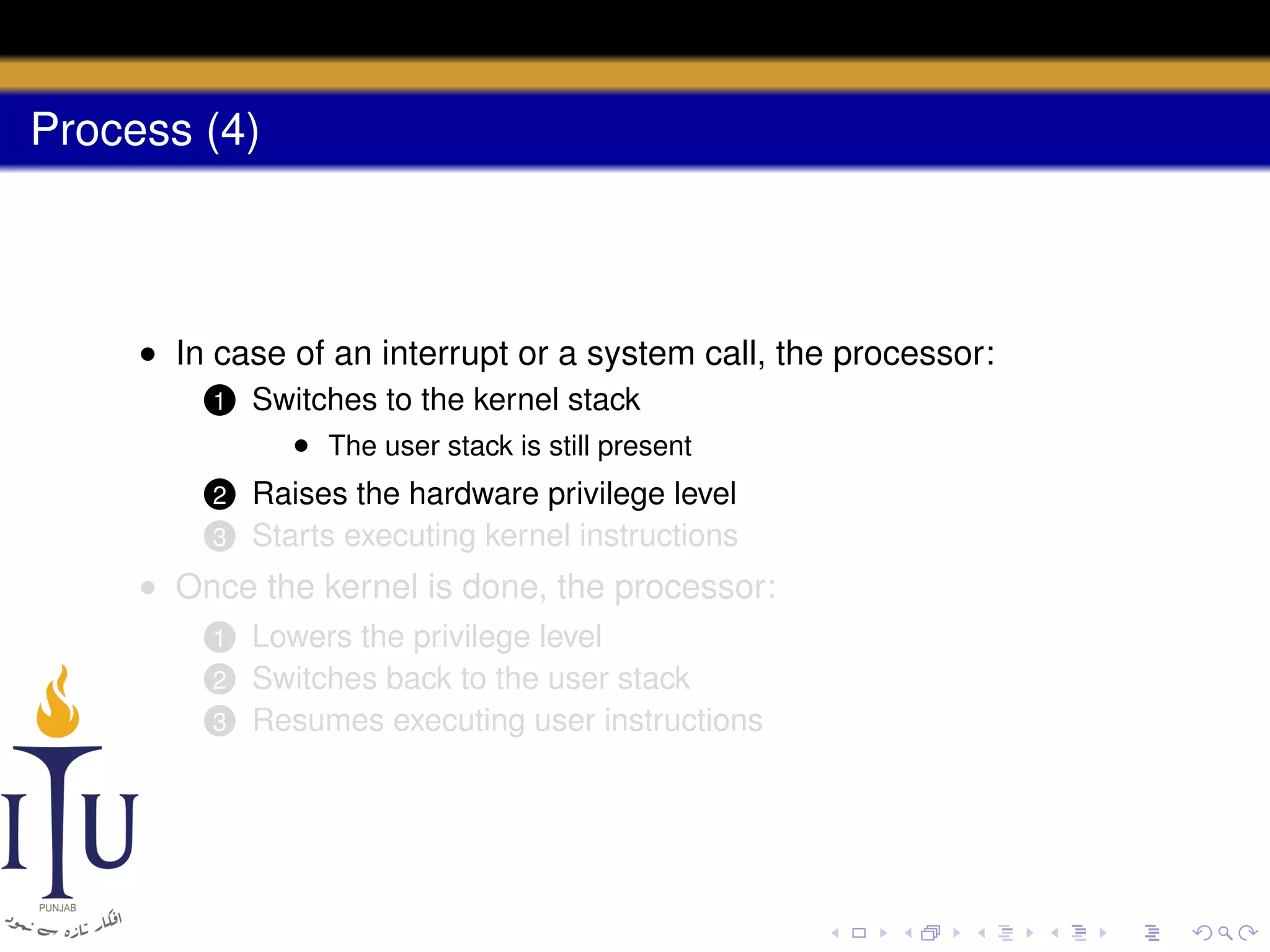
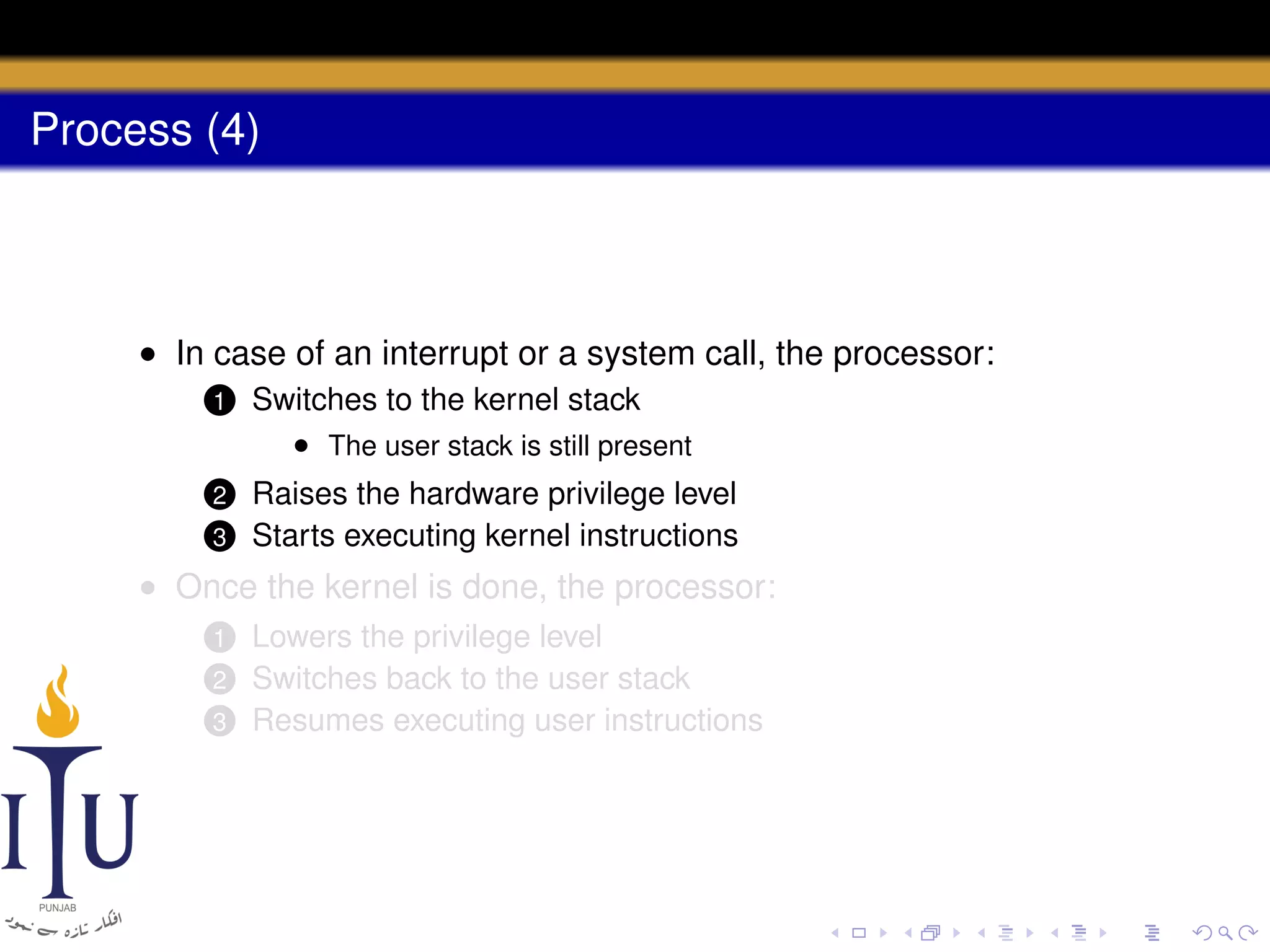
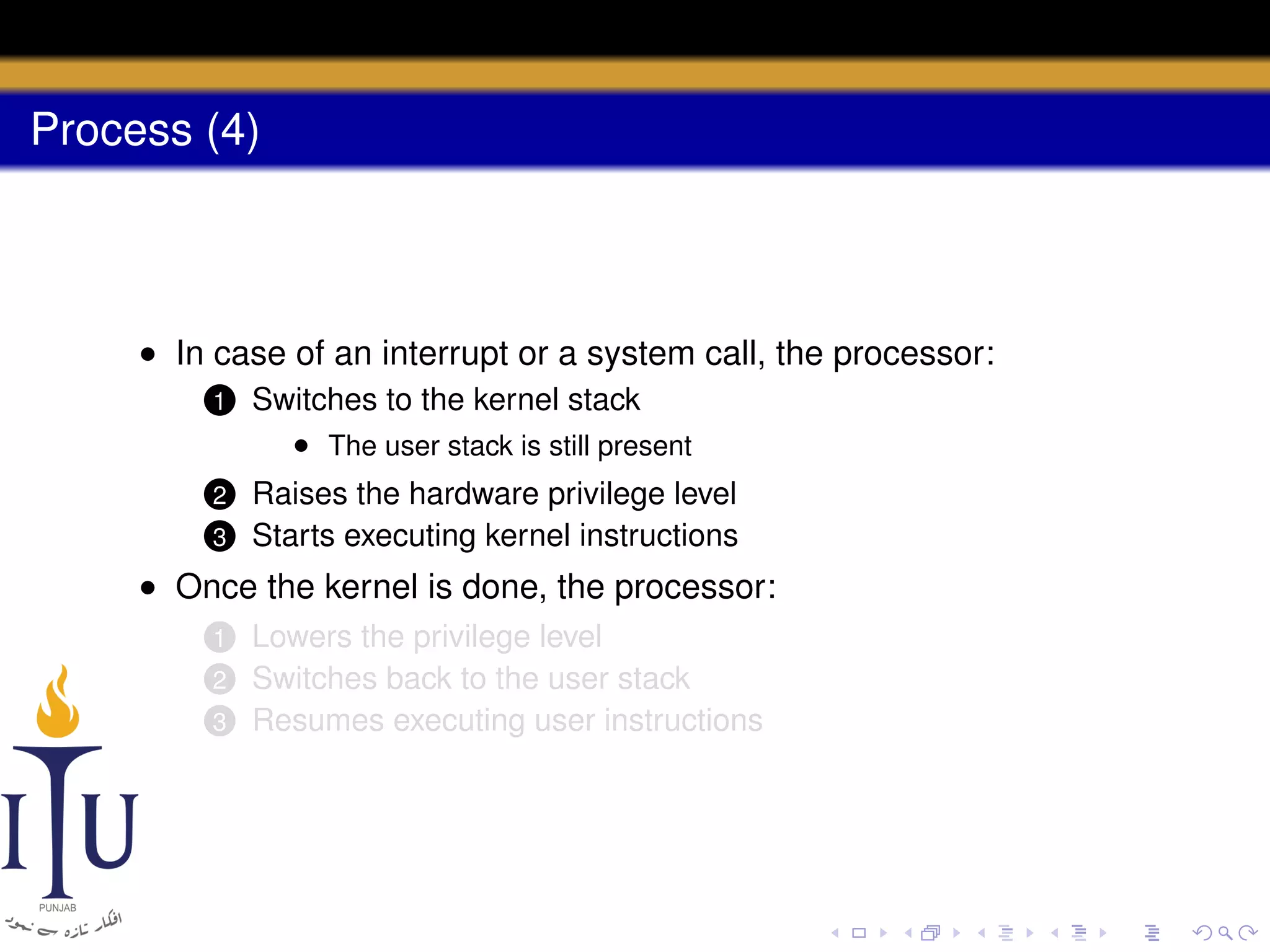
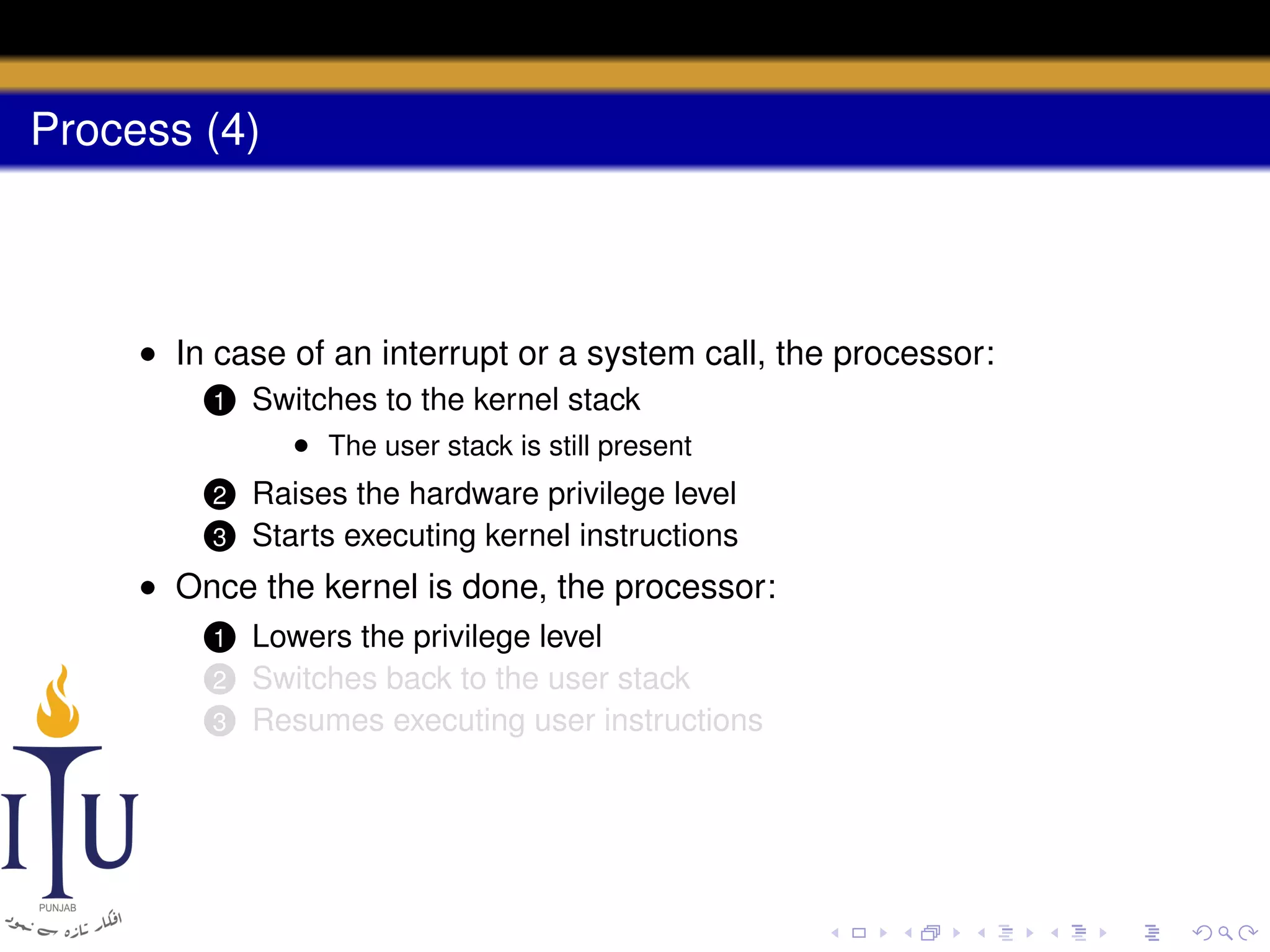
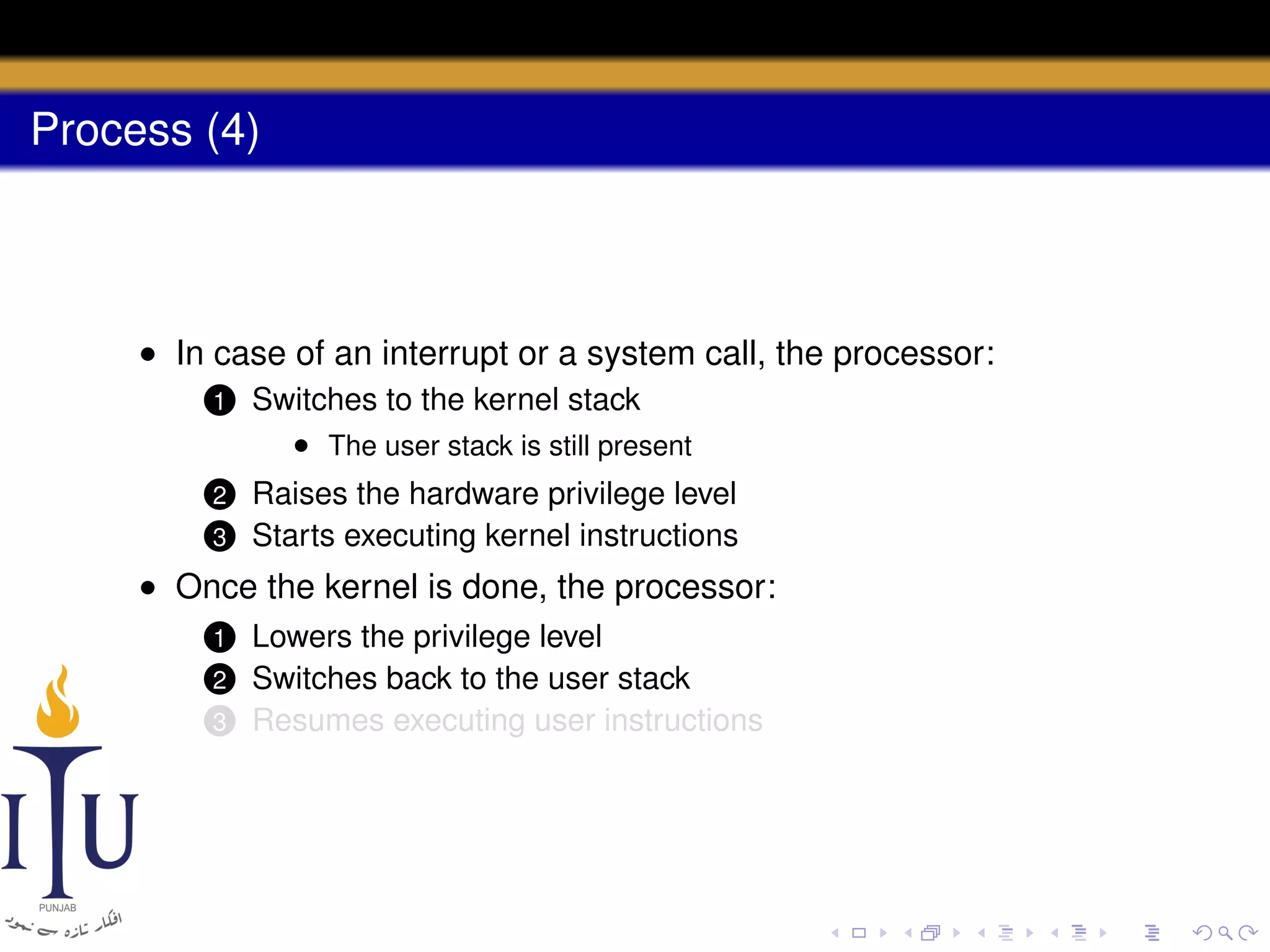
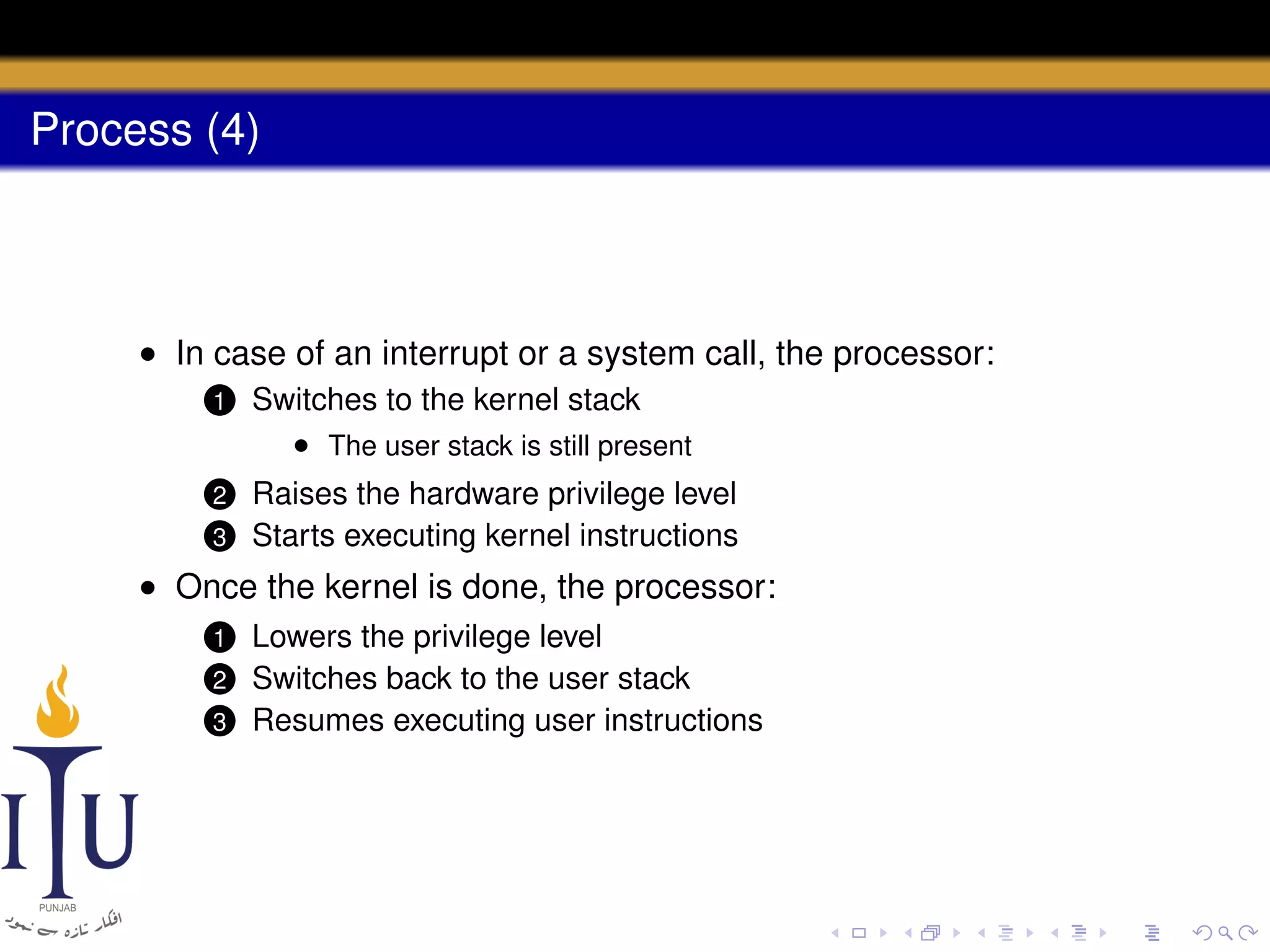
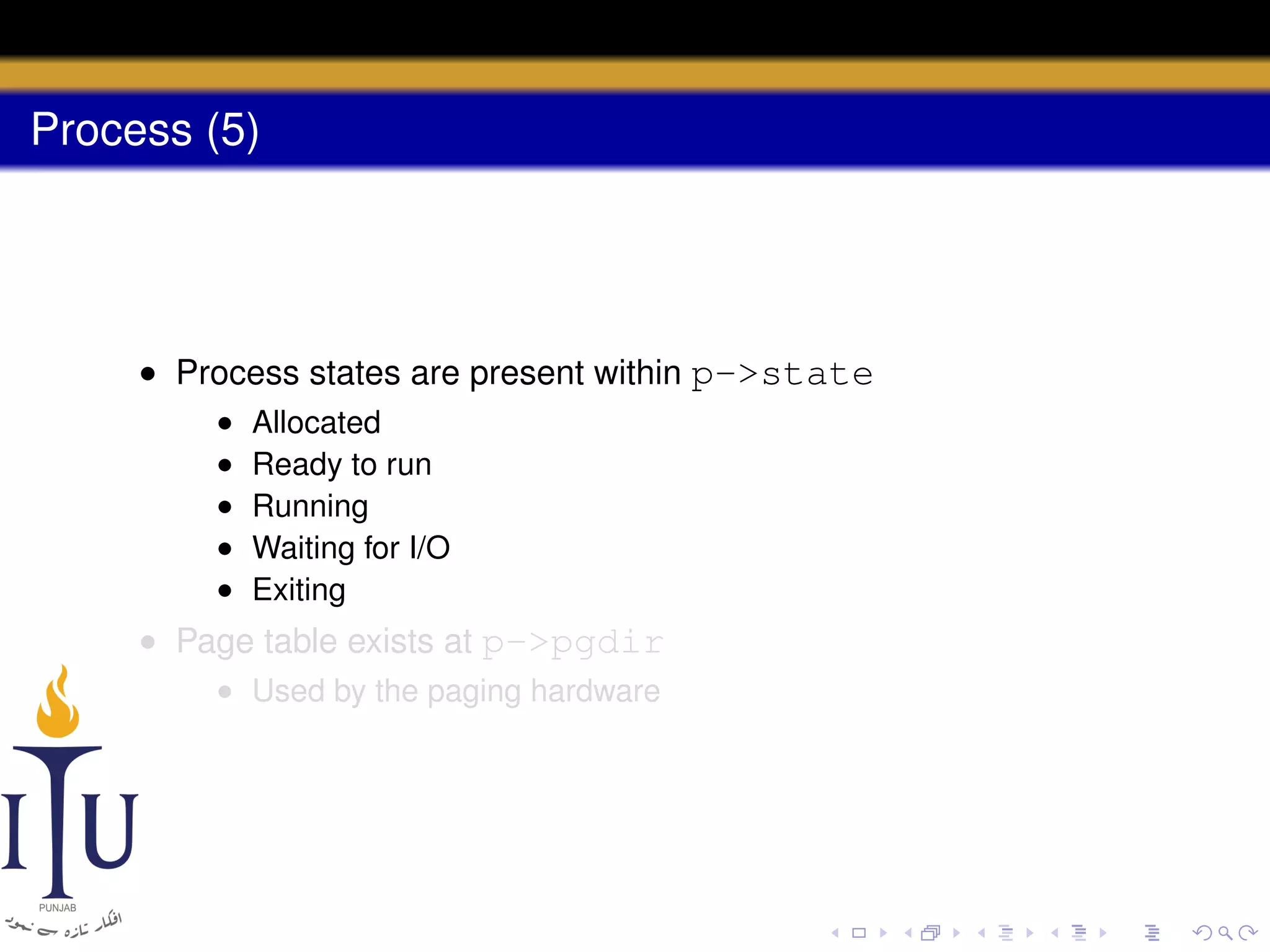
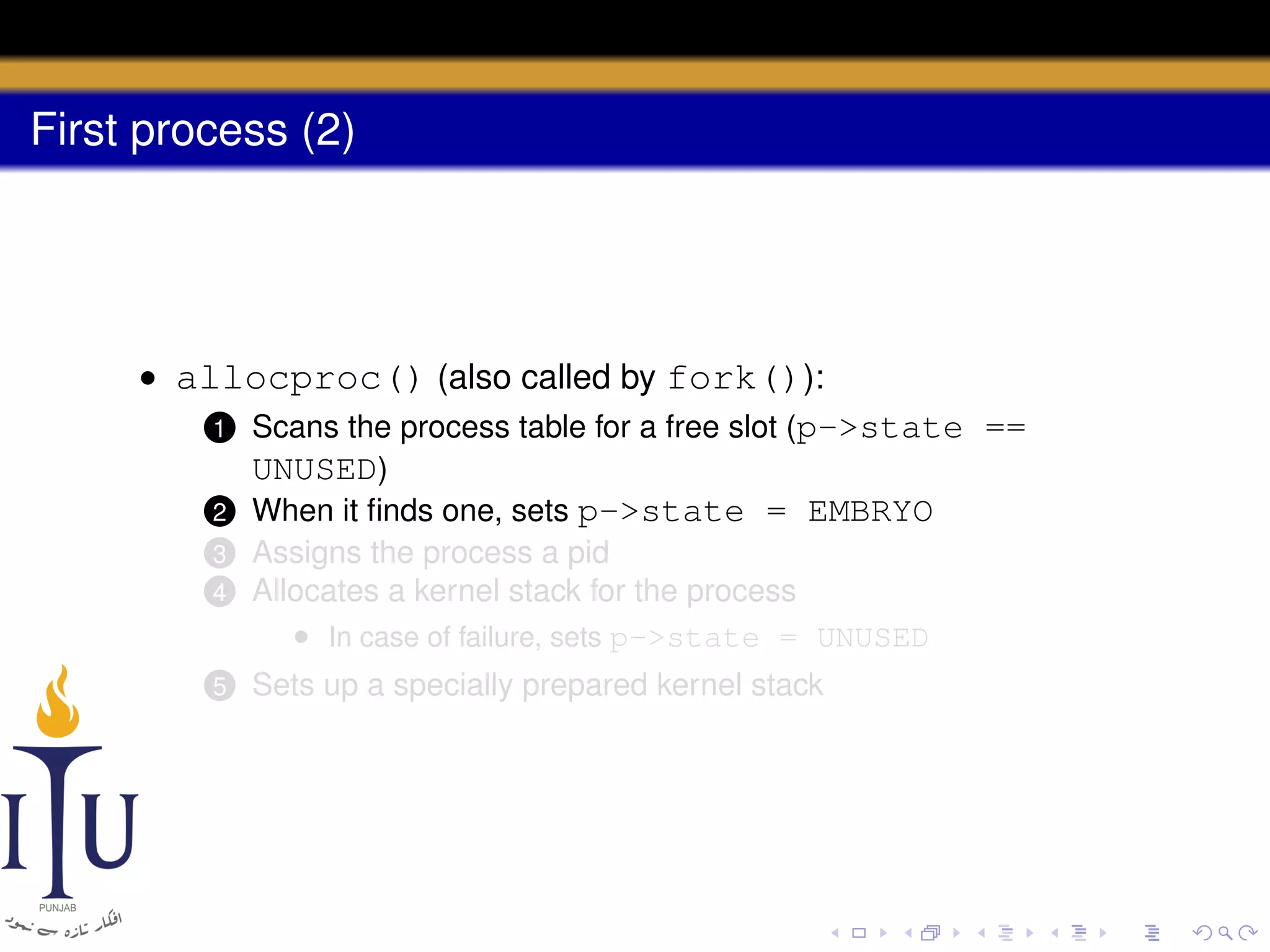
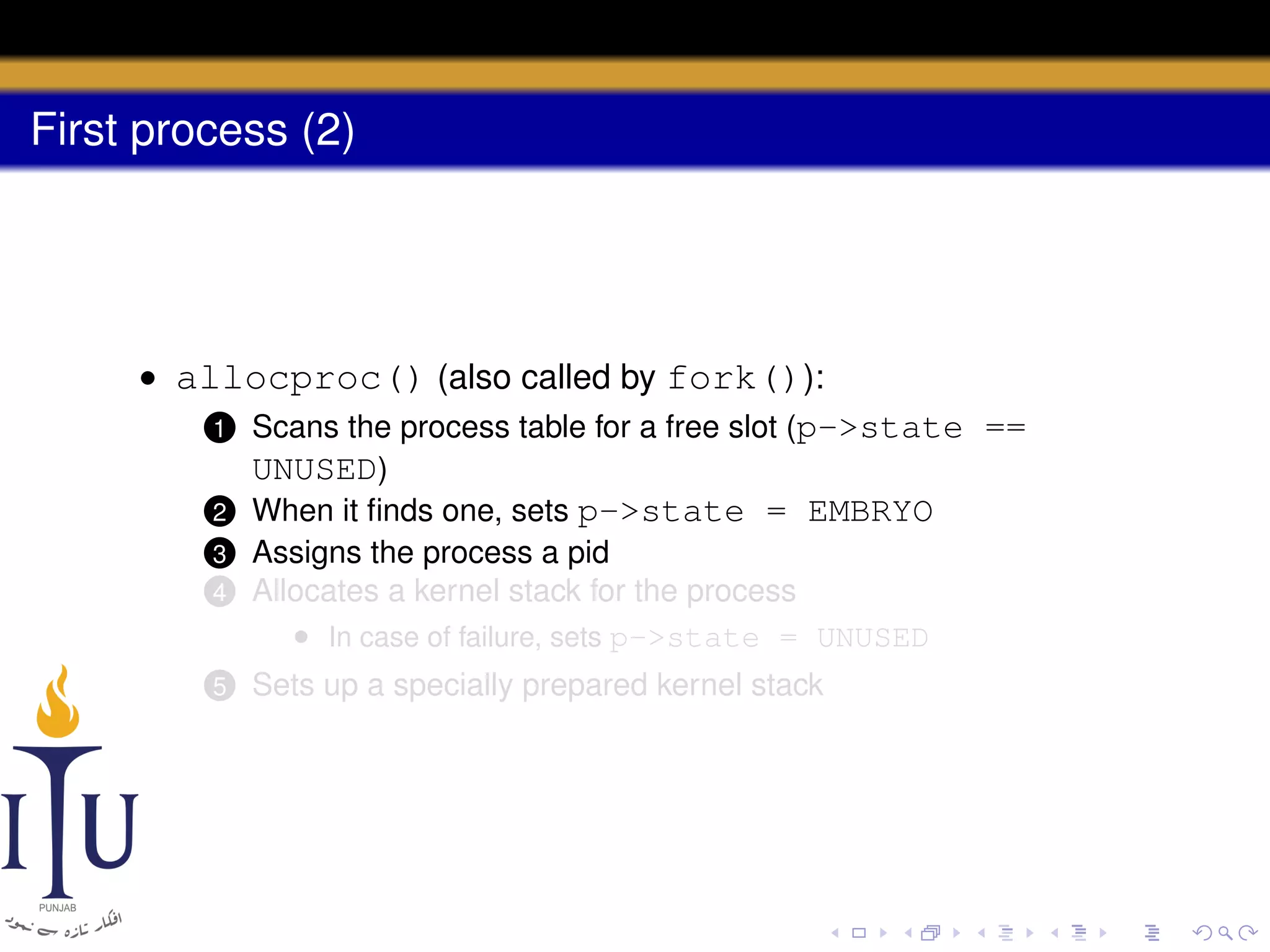
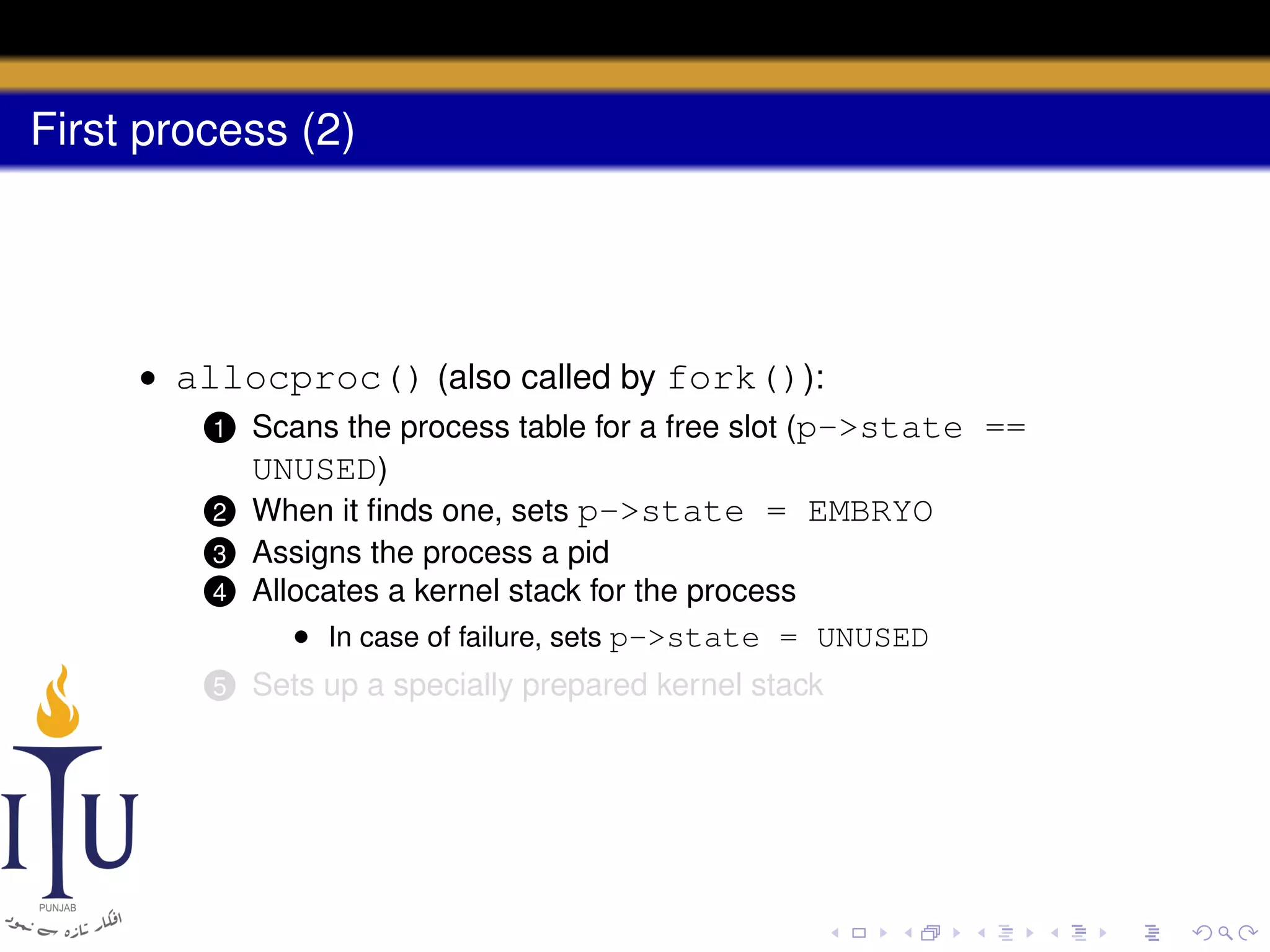
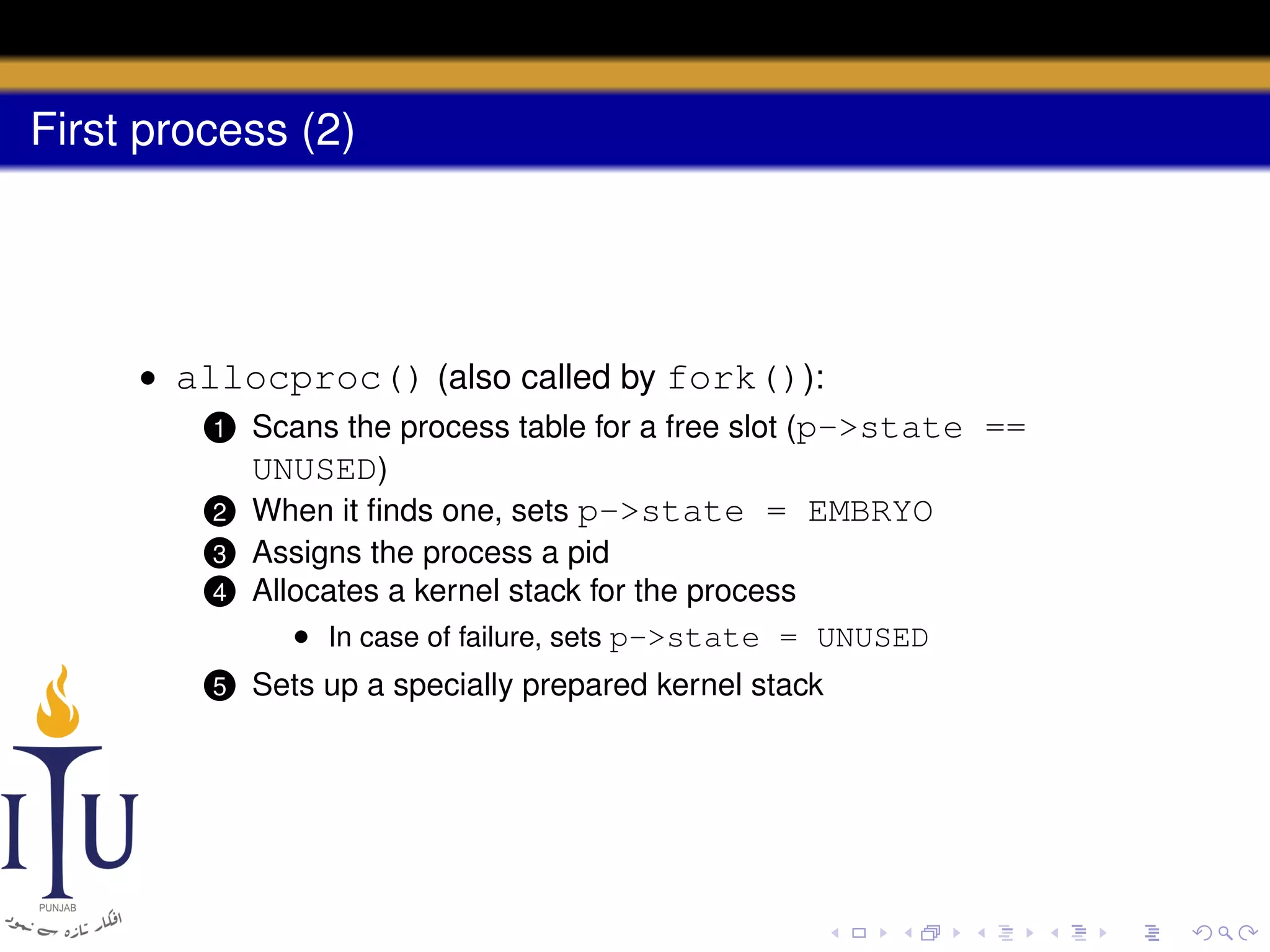
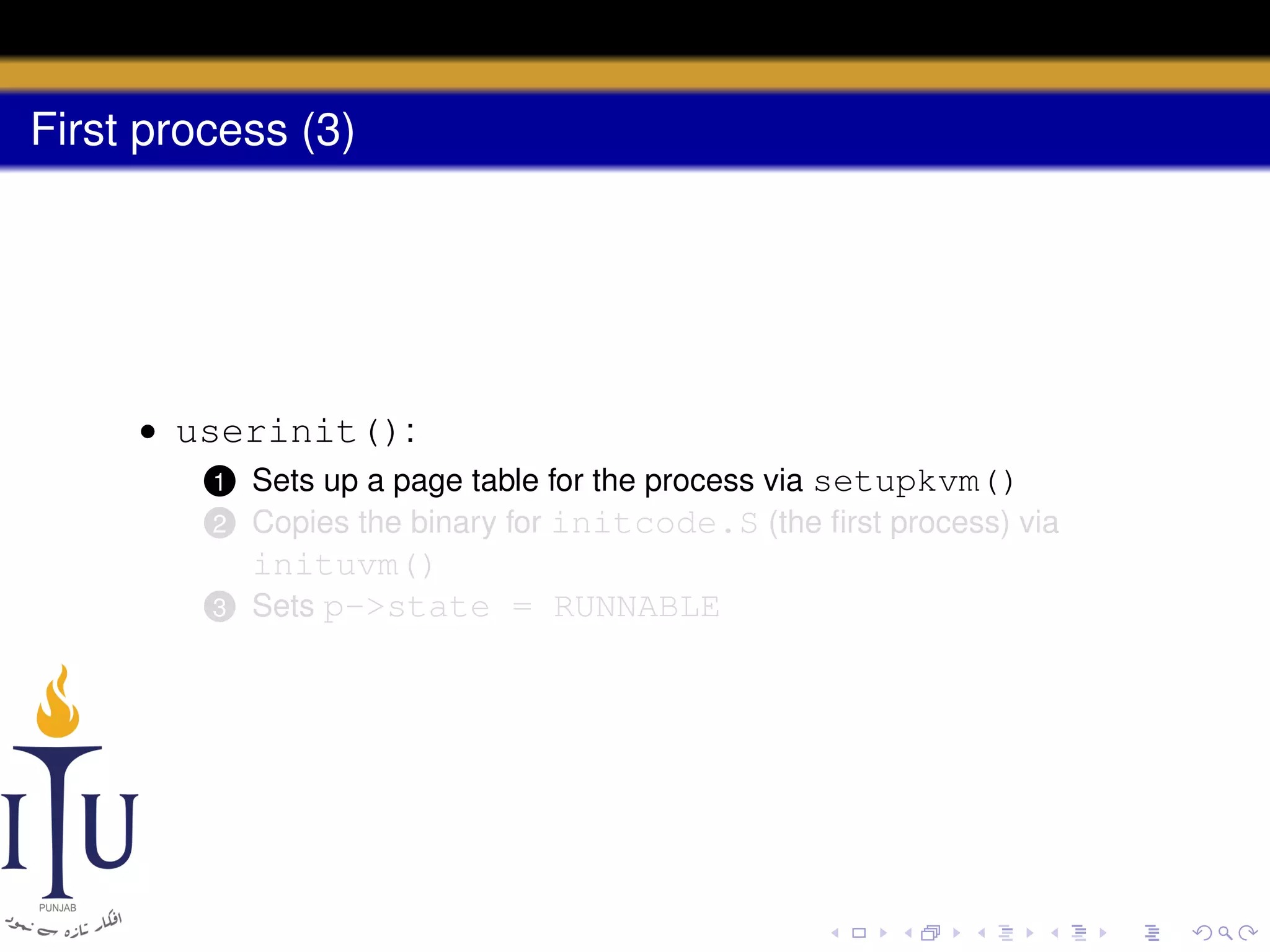
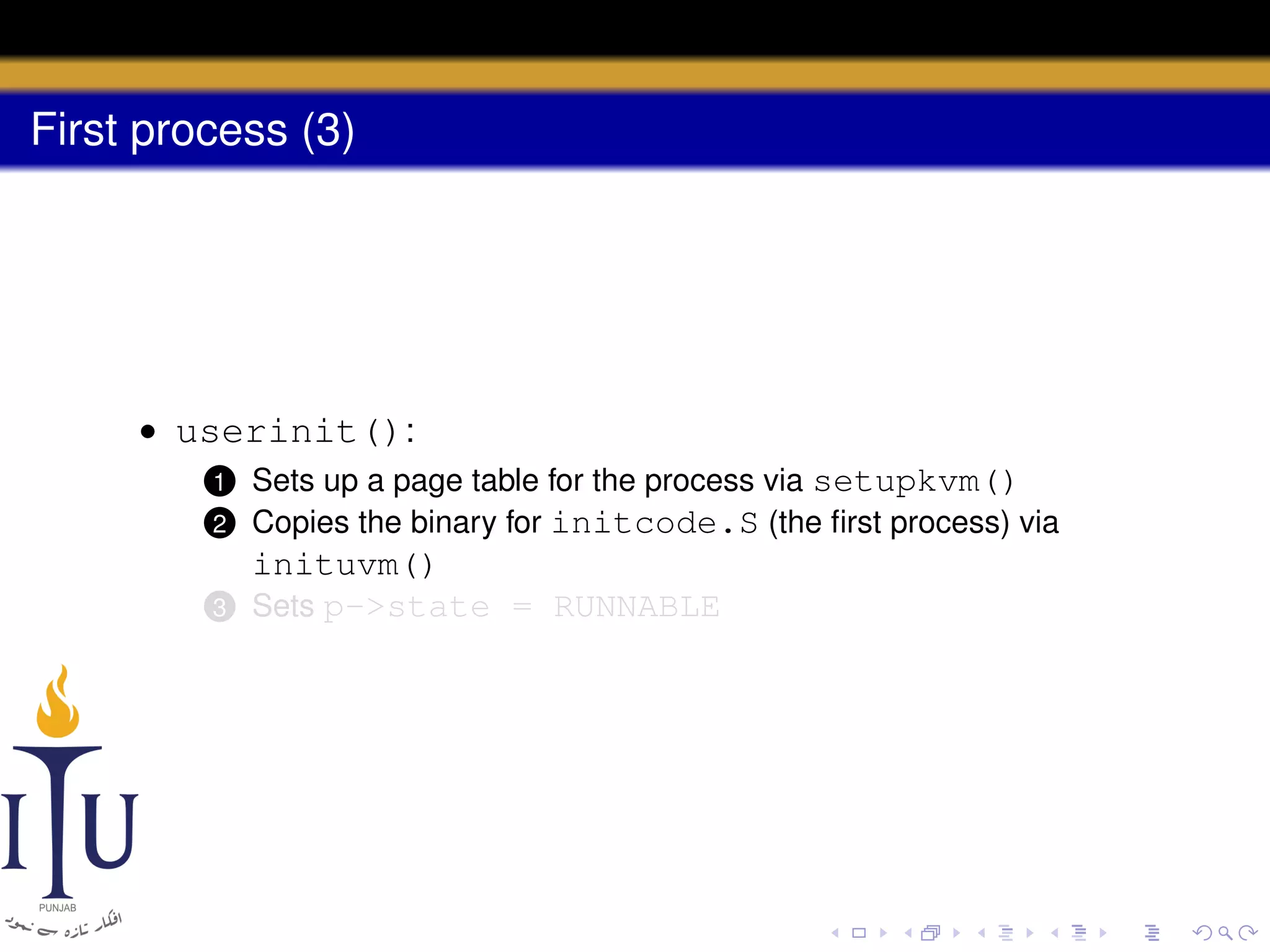
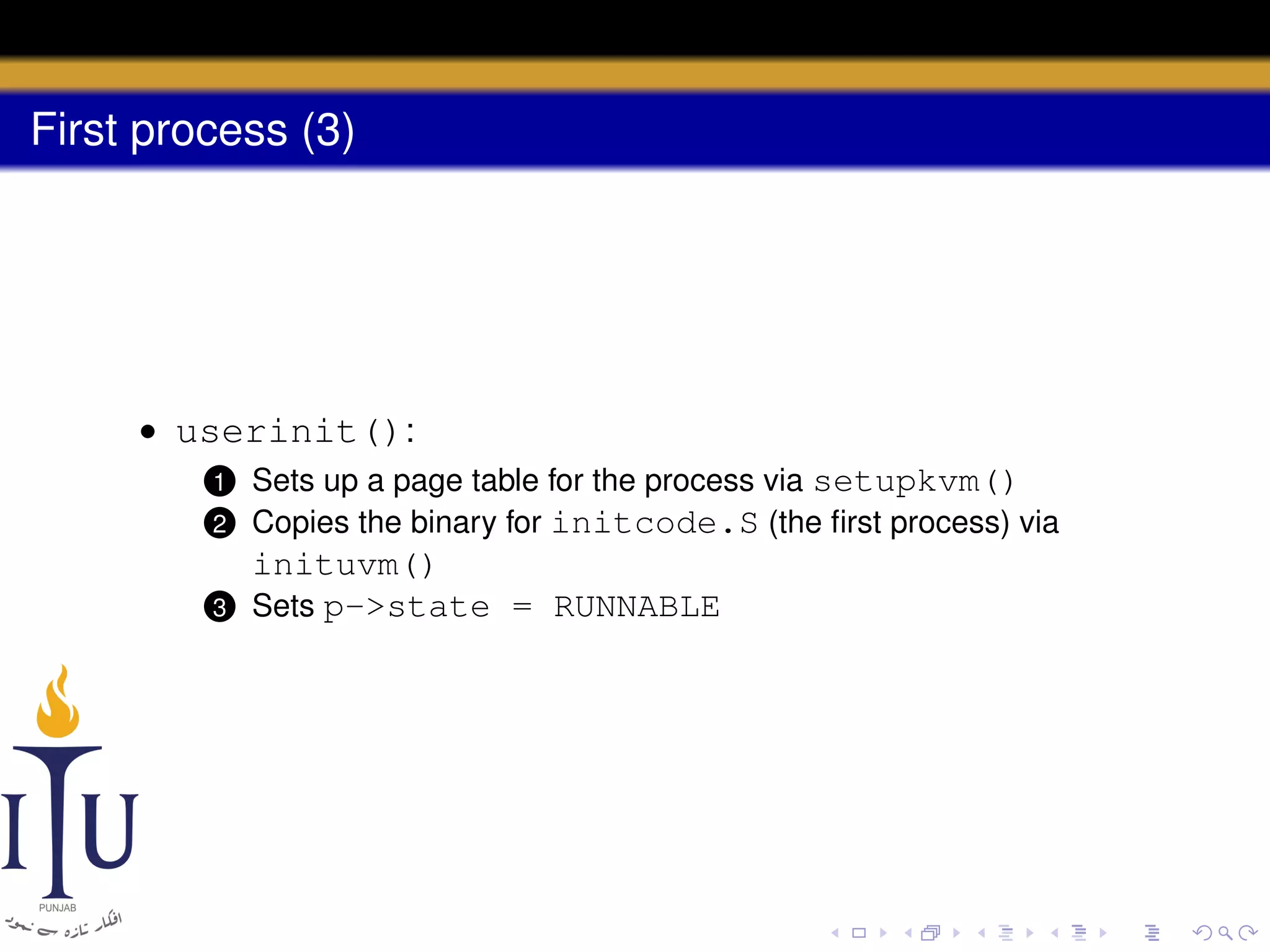
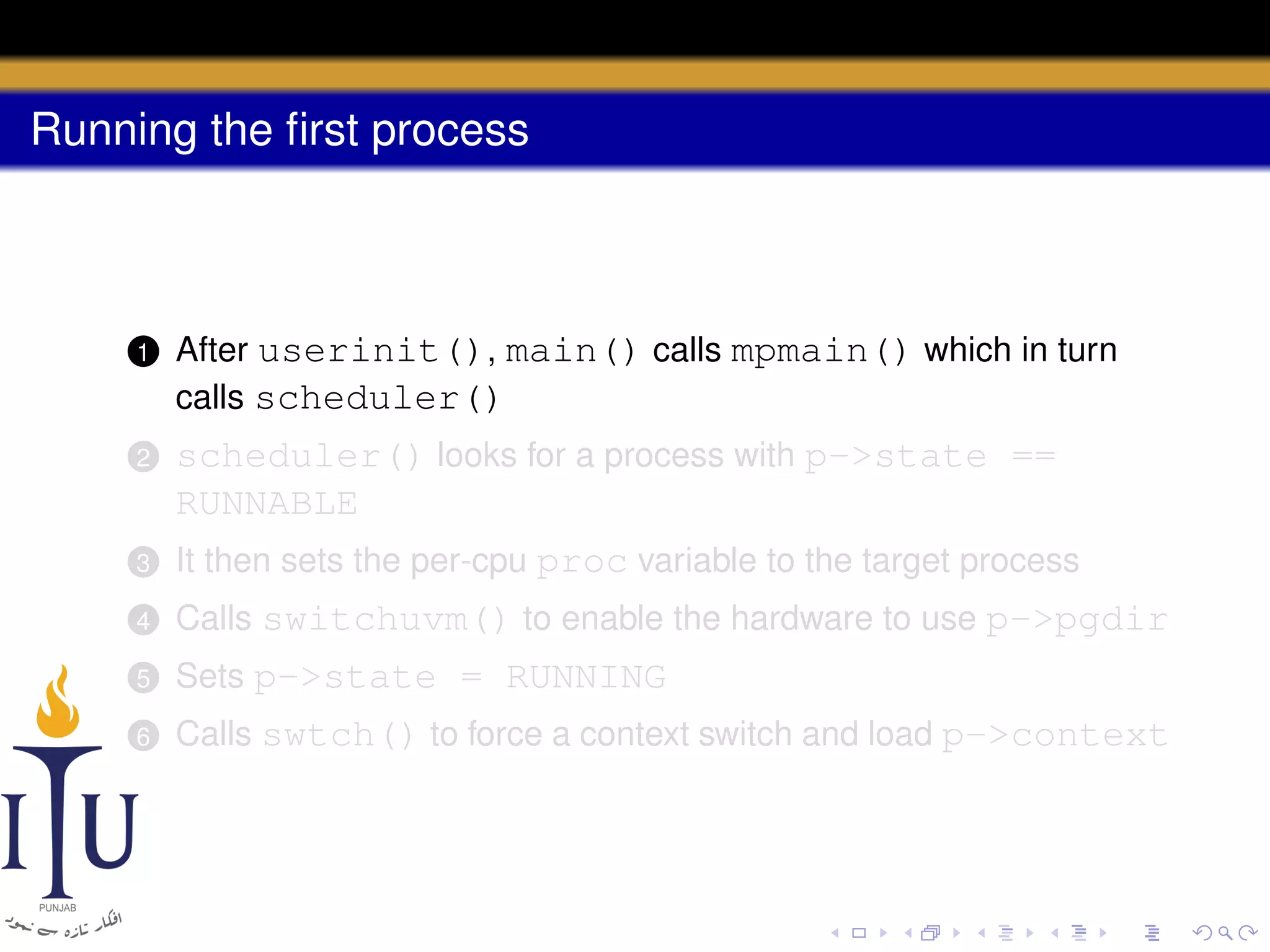
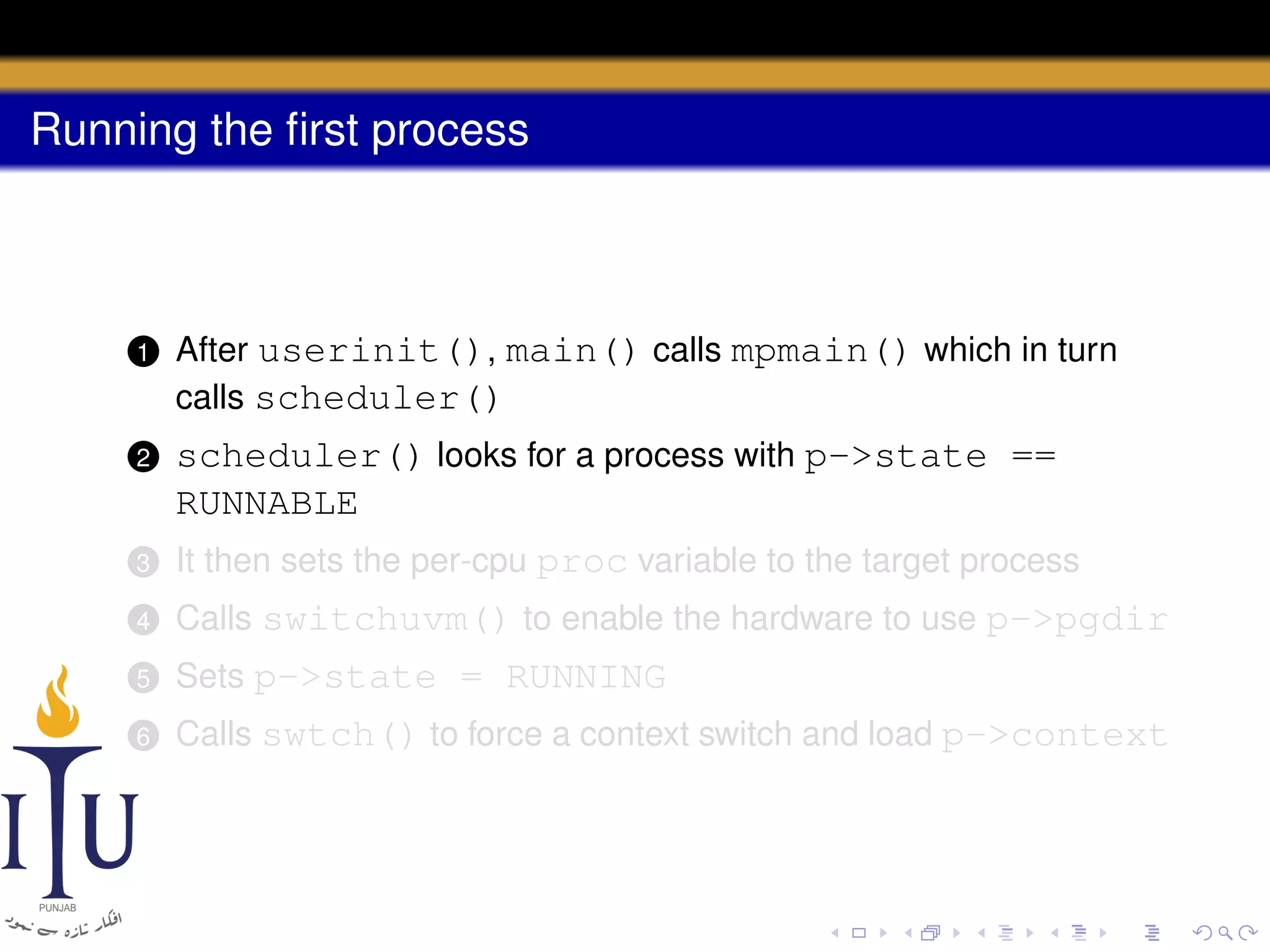
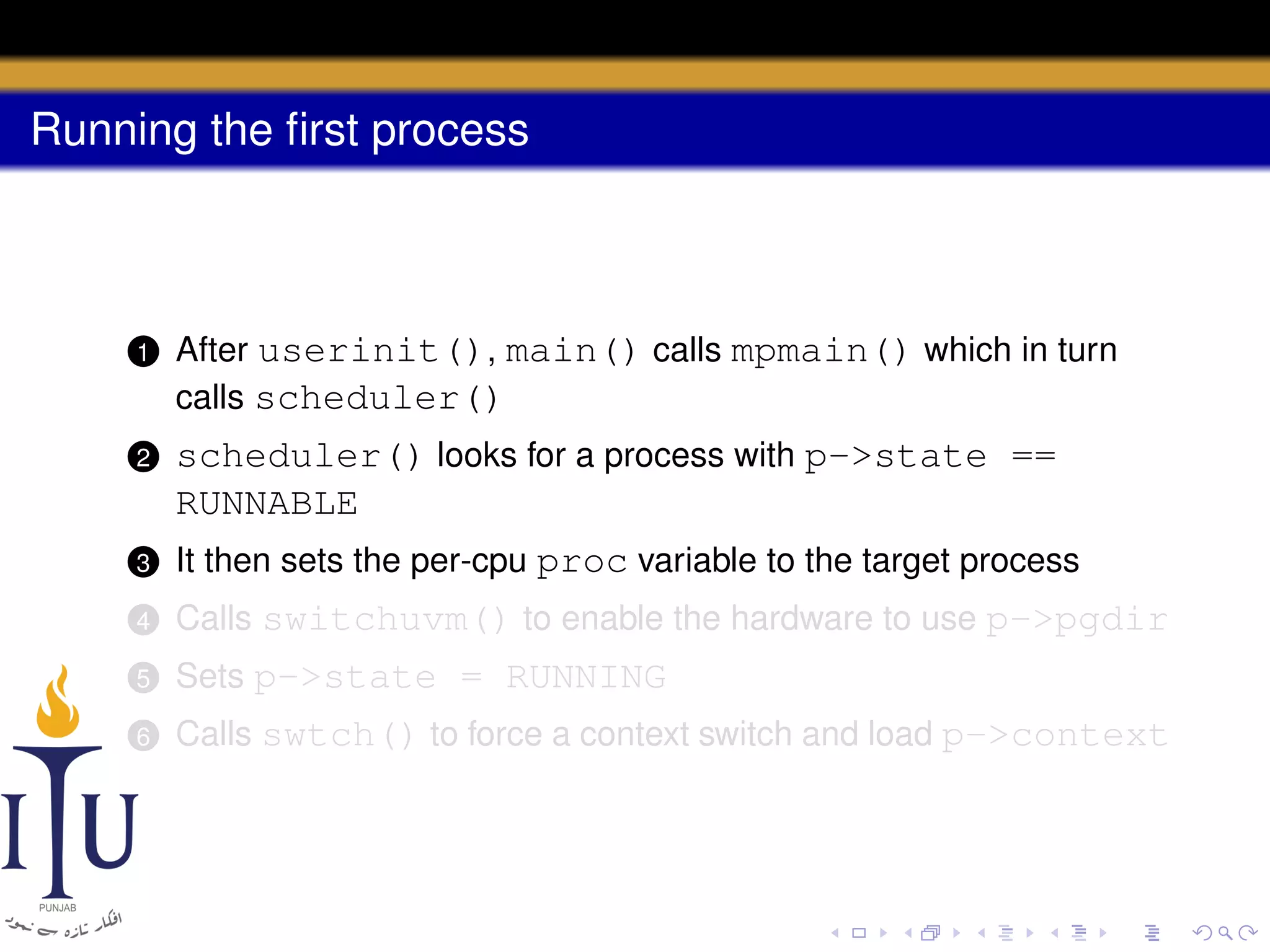
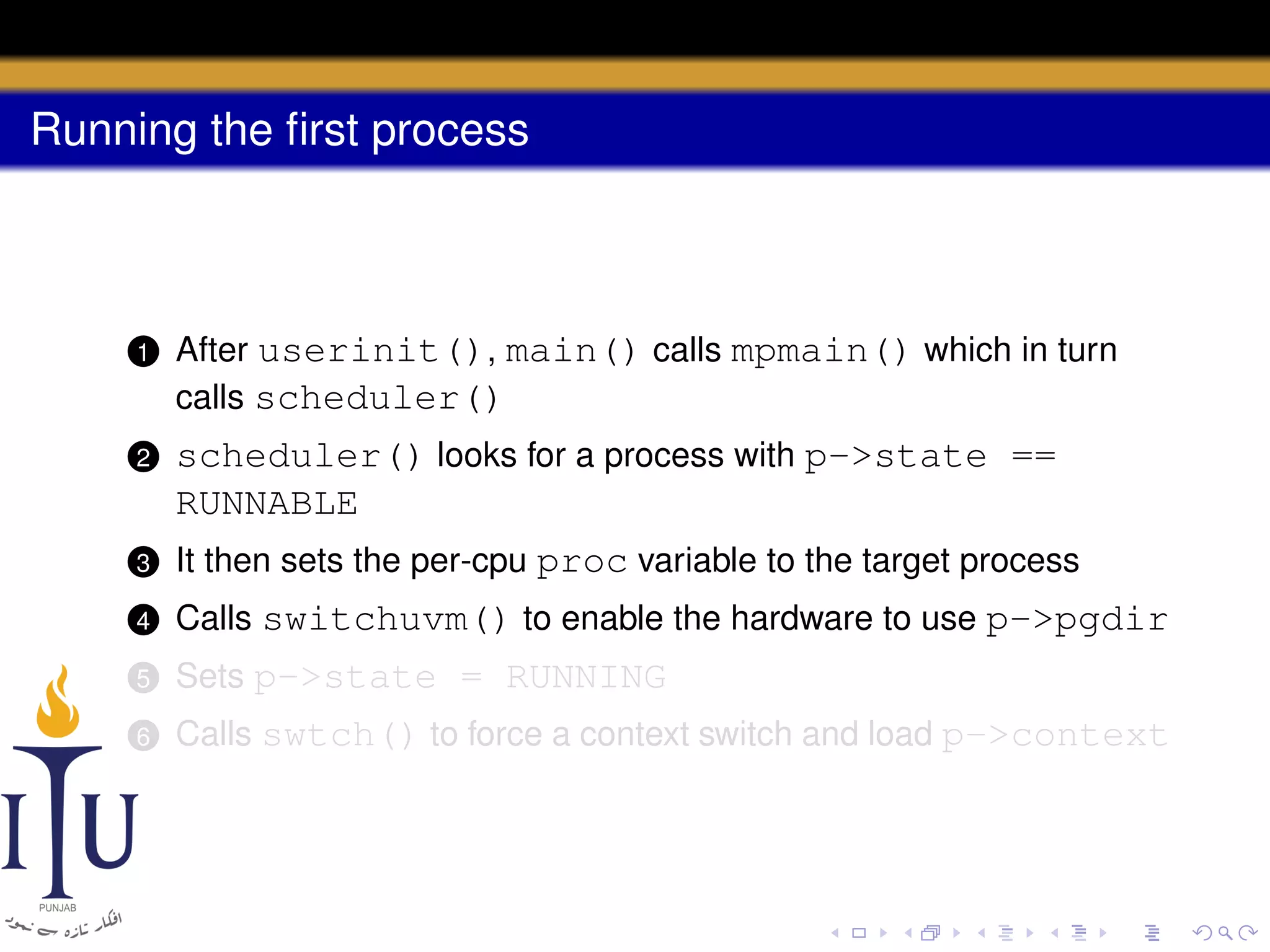
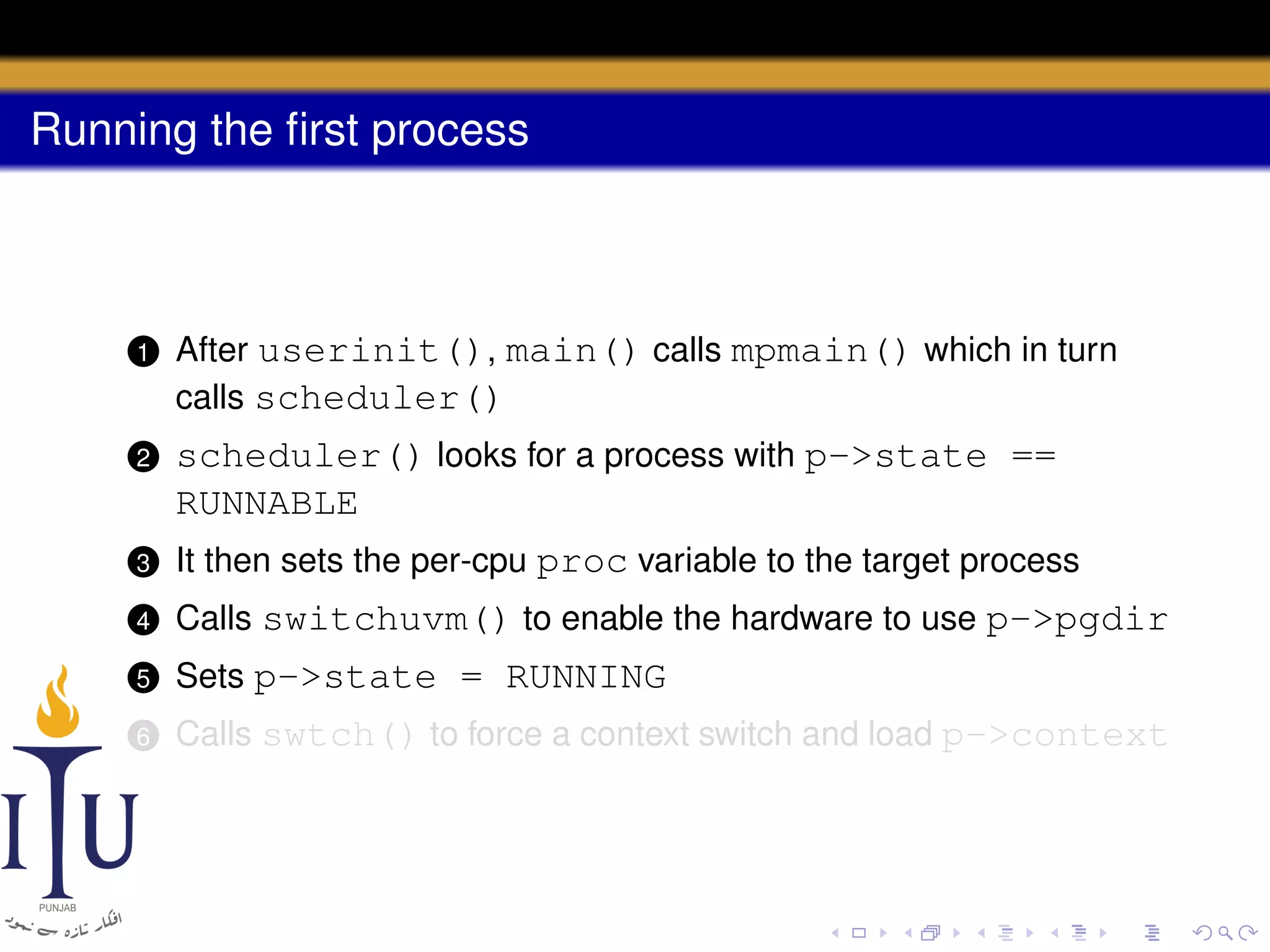
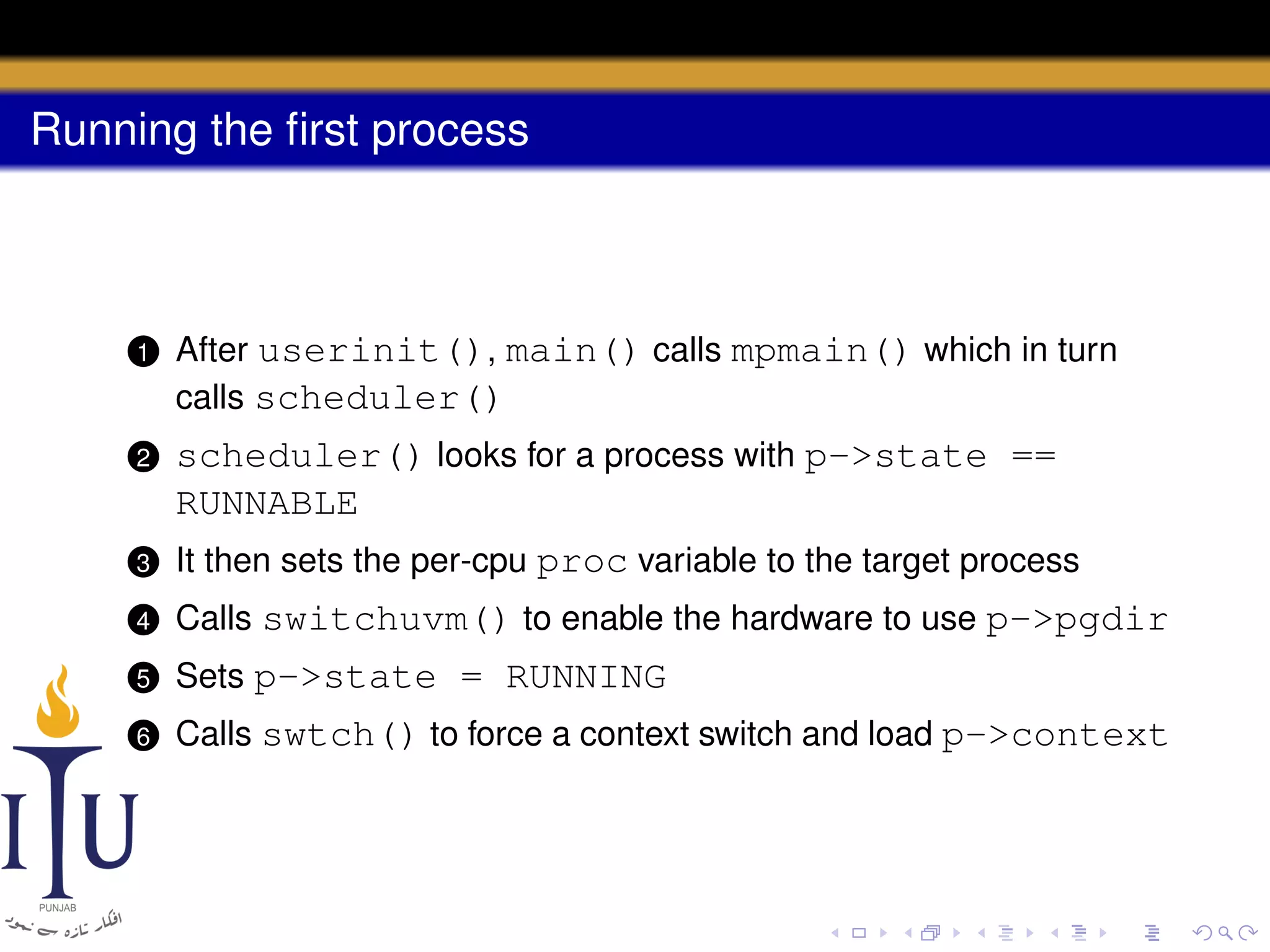
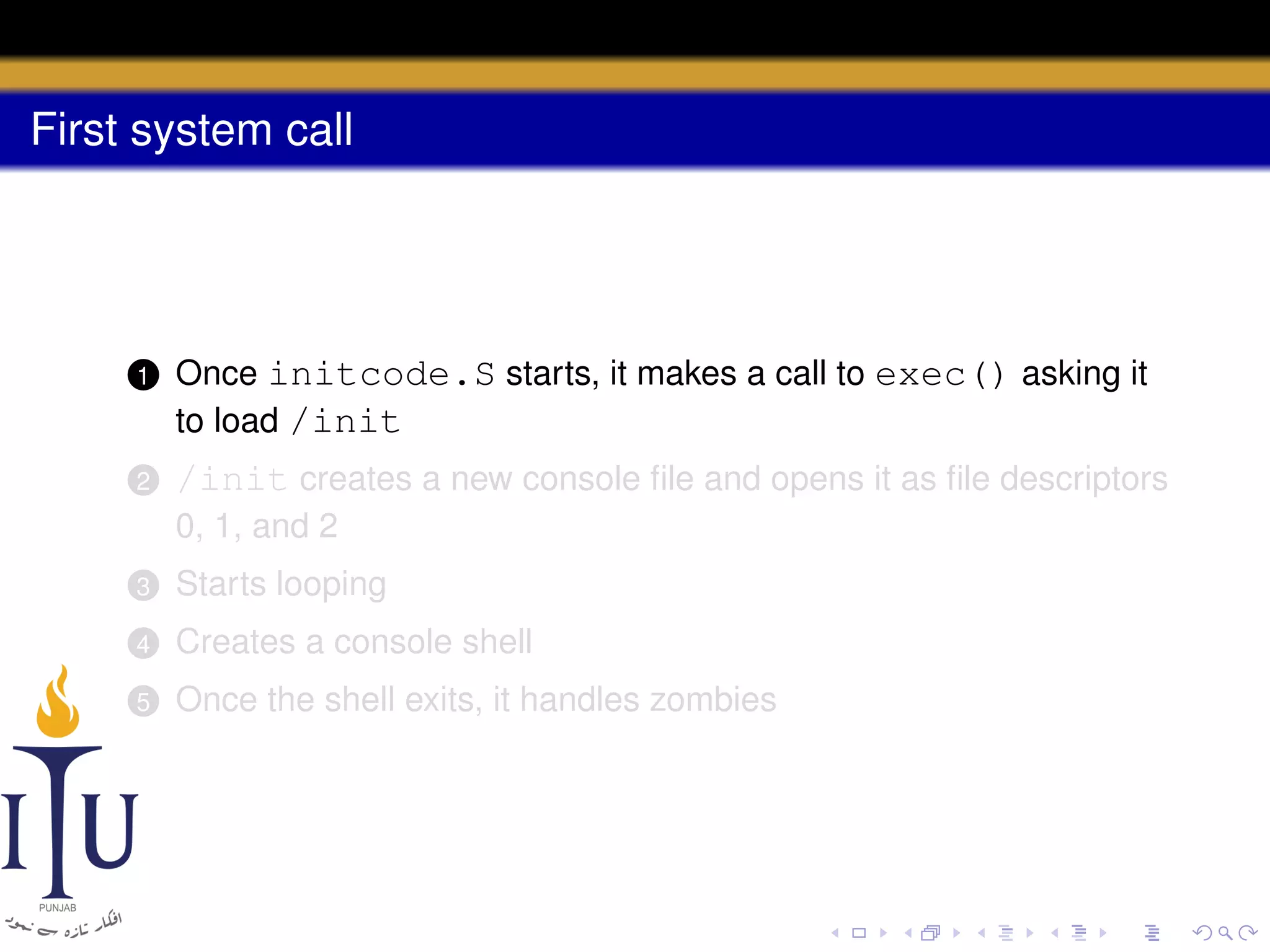
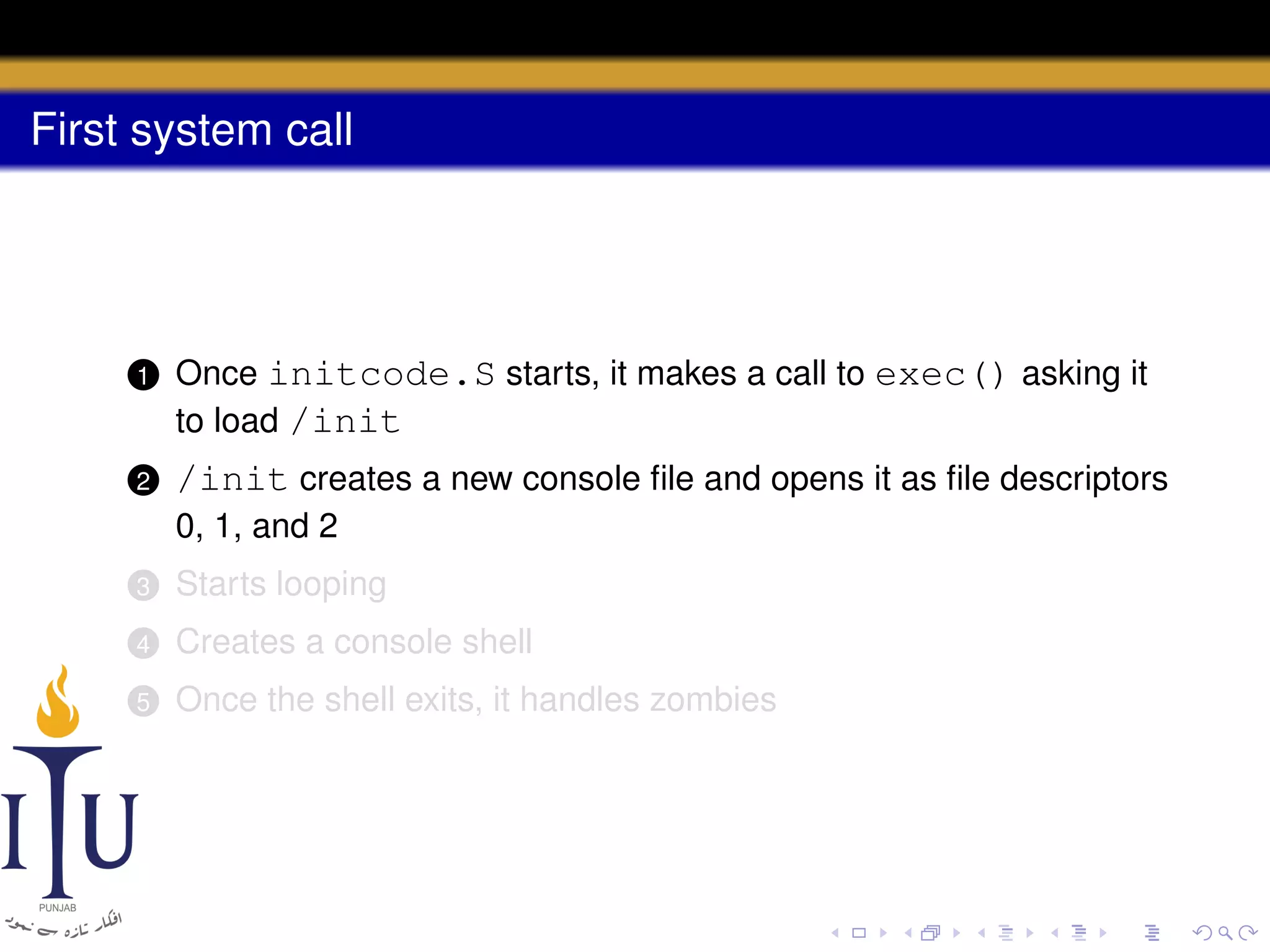
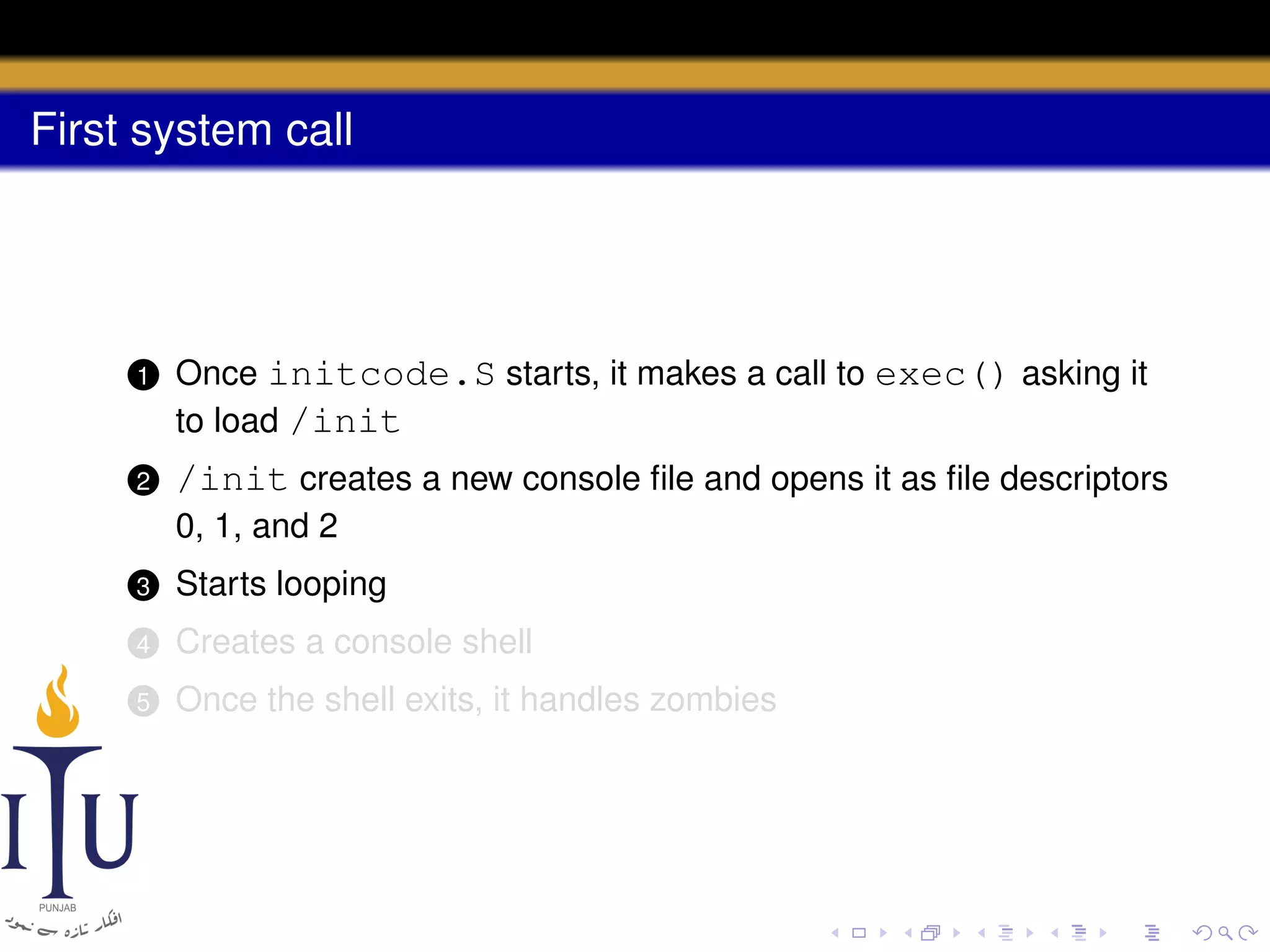
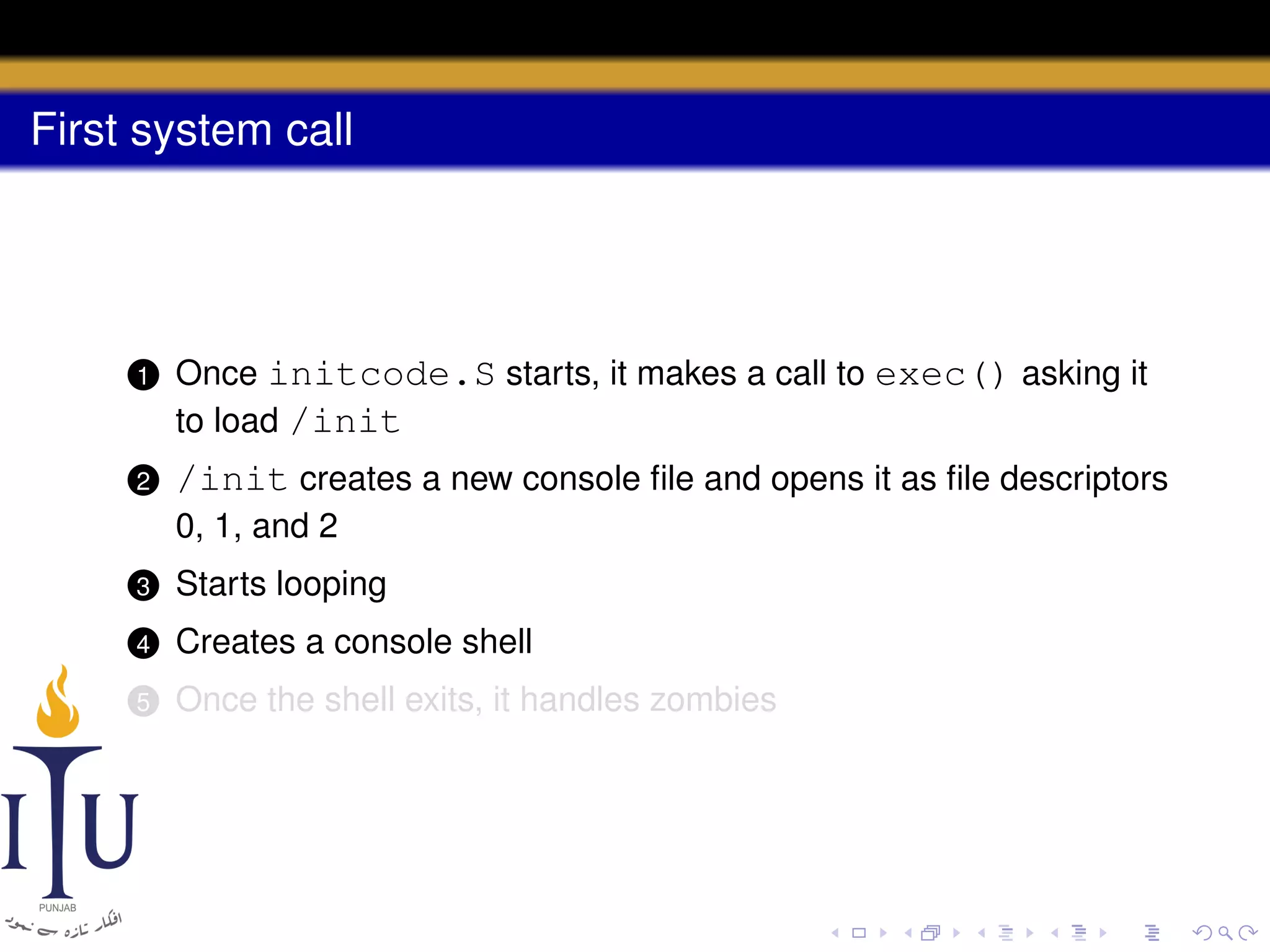
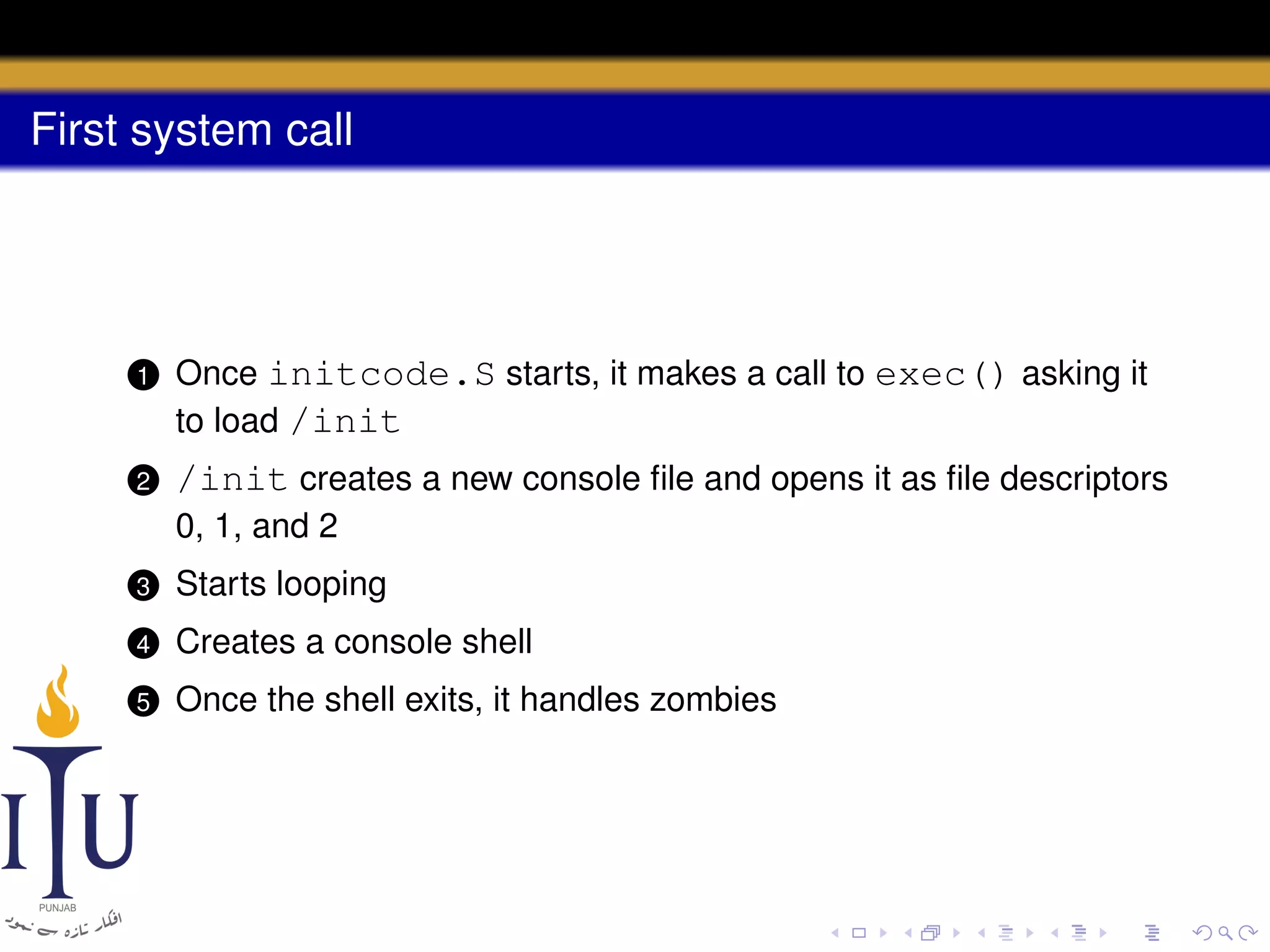
The document describes the process of starting a process on a PC. It explains that when a PC boots, the BIOS starts executing and loads the boot loader from the boot disk sector. The boot loader then loads the kernel into memory and jumps to it. The kernel boot loader then initializes devices and creates the first process by setting up its page table and memory space. The first process's state is set to runnable and the scheduler runs it, switching to its address space. The first process makes a system call to load the /init program, which creates the console and shell that runs as the main process.






![Today’s Task
• Write C code that implements a grep with two optional flags: -f
and -v and a wc with three optional flags: -b, -l, and -w
• Make two different source files: grep.c and wc.c
• Should be callable via ./grep -v -f foo for instance
• Boilerplate code:
void main(int argc, char *argv[]) {
// argc: number of arguments
// argv[]: array of string arguments
// your code goes here
}](https://image.slidesharecdn.com/document-140110160320-phpapp02/75/AOS-Lab-1-Hello-Linux-53-2048.jpg)