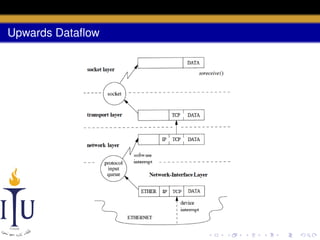
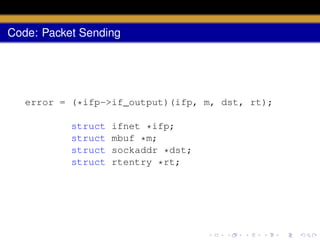
This document discusses network communication in Unix systems. It describes how the networking infrastructure abstracts different network architectures and consists of network protocols, address families, and additional facilities. It also summarizes the network subsystem layers, memory management using mbufs, data flow between sockets and the network, common network protocols, network interfaces, routing, and protocol control blocks.