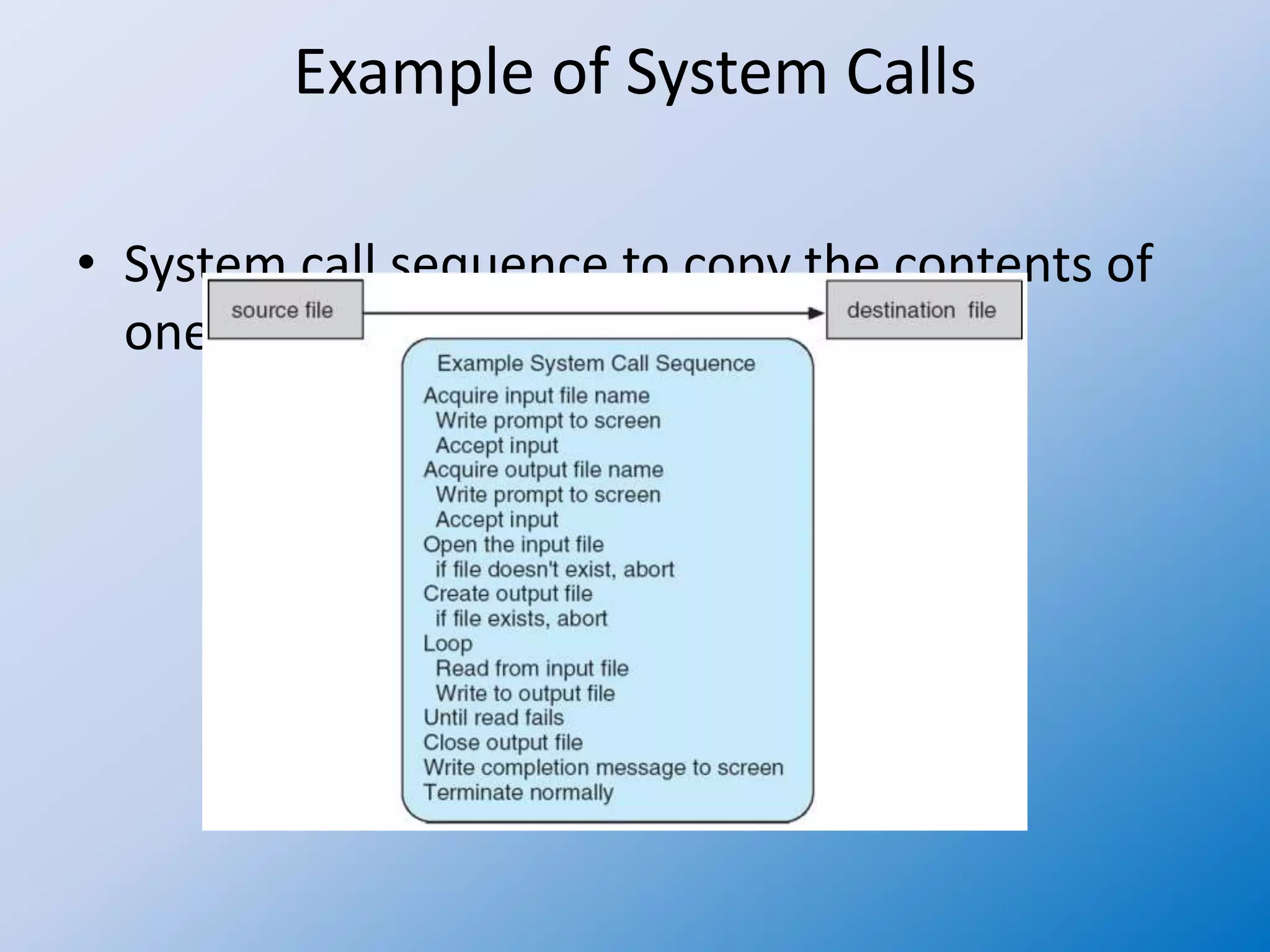
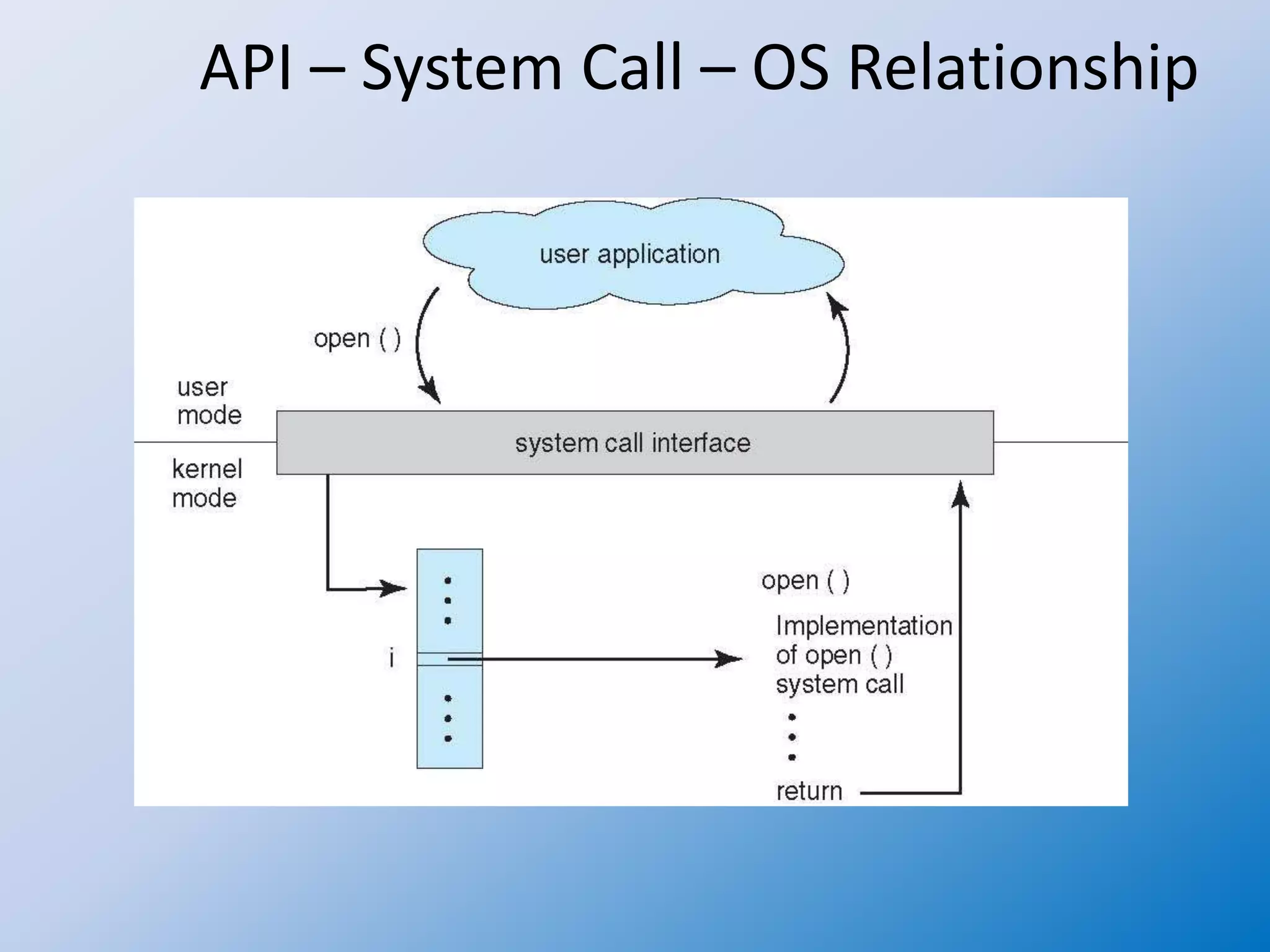
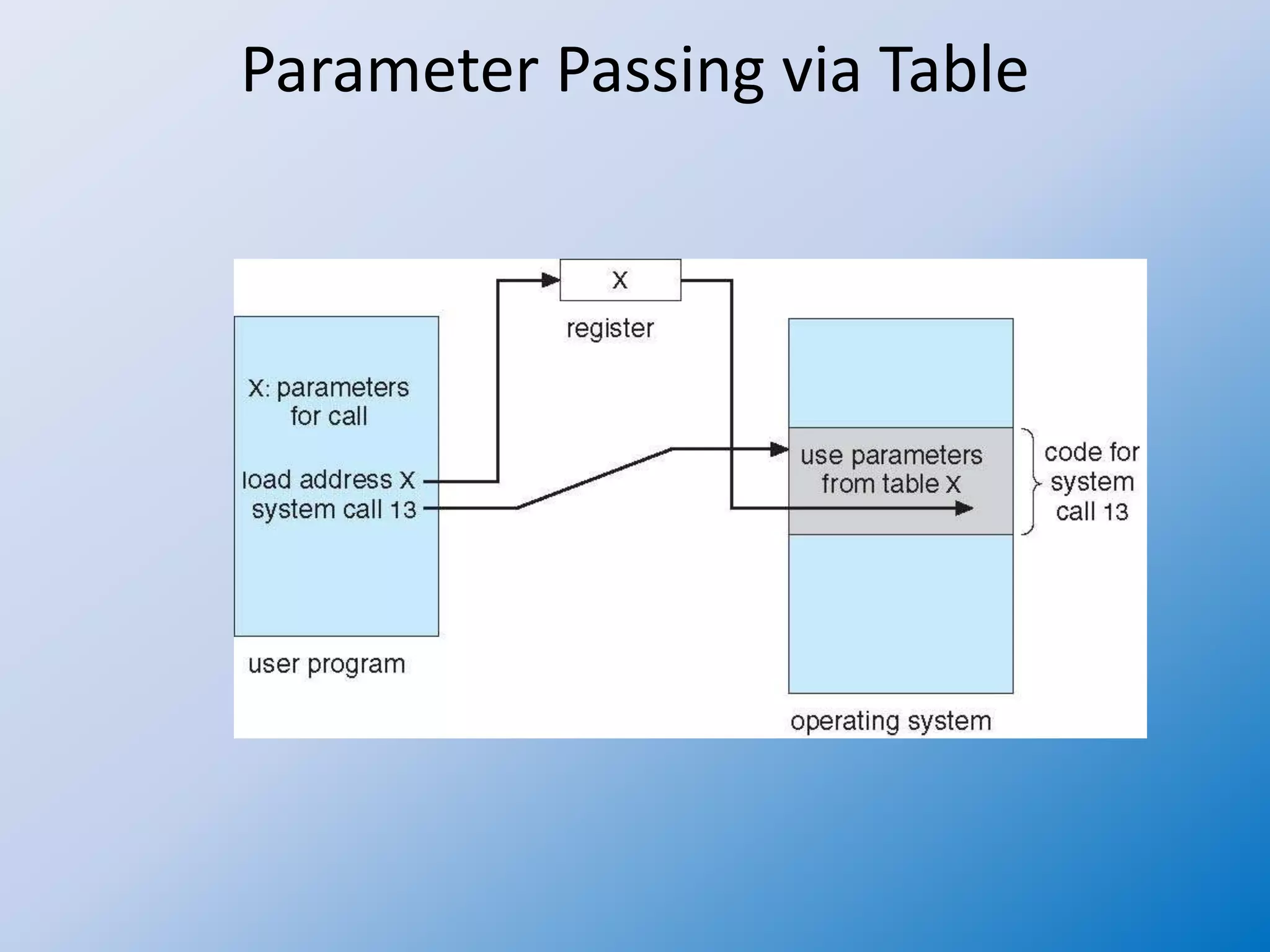
A system call is a standardized way for a computer program to request services from the operating system's kernel, enabling safe access to hardware and core services. System calls originate from user processes and are handled through various methods of parameter passing, essential for managing tasks like process control, file management, and communication. Different models exist for handling system calls in multithreaded processes, affecting how threads interact with the kernel and manage resources.